Introduction
Imagine giving a stranger your house keys just because they walked past your driveway. That’s effectively what many organizations still do—granting implicit trust to users or systems based on network location. Zero Trust flips this model on its head by treating every access request as untrusted until proven otherwise. This is why zero trust architecture has become the gold standard in cybersecurity. But what exactly is zero trust, and why is identity its cornerstone?
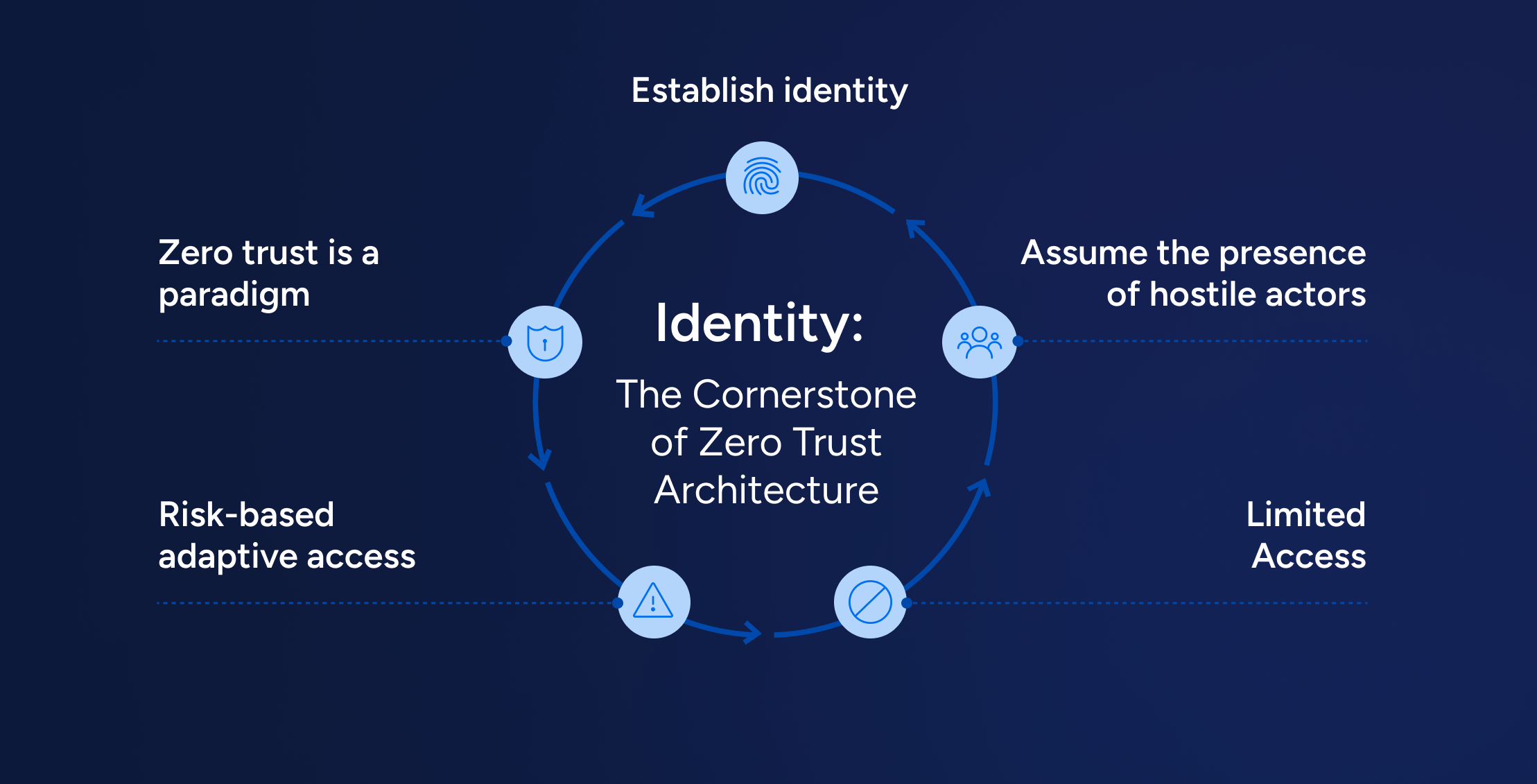
What Is Zero Trust, Really?
At its core, zero trust means that we don’t assume any connection between a person or device is secure. Every user or system must be authenticated before being given access to a system. We essentially never trust, and we always verify connections.
Zero Trust is not a single product or feature—it’s a security framework rooted in the principle of “never trust, always verify.” It requires organizations to rethink access: verifying users and systems every time they request access, regardless of whether they’re inside or outside the network. It is more of a philosophy than a silver bullet. So, when an organization has a zero-trust initiative, it will consist of multiple tools. When considering zero trust tools, one of the core components of a zero trust philosophy has to include identity.
When running security programs or advising customers, it’s important to reference common frameworks like NIST. These standards are well-researched and carry weight in conversations with executives and board members. According to NIST 800-207, the definitive Zero Trust Architecture framework, Zero Trust is built on multiple pillars, but identity is the cornerstone.
Every access decision hinges on a single critical question: who (or what) is trying to gain access—and should they be allowed? Identity plays such a vital role in Zero Trust that it maps directly to each of NIST’s seven core tenets. Without strong identity controls, the entire model falls apart.
Resource Management and Access Control
Understanding Your Assets
In a Zero Trust model, every data source, system, or service is considered a “resource”—and identity is what determines whether it should be accessed at all.
When we talk about identity in cybersecurity, we’re not just talking referring to usernames and passwords. Identity is the cornerstone of access: it defines who or what can touch your environment, and under what conditions.
Think about the identities you use every day: a work login, social media accounts, or online banking credentials. These are examples of human identities, and they’re fairly straightforward. But there’s another category that’s often overlooked—and increasingly critical: non-human identities.
Non-human identities include service accounts, cloud workloads, and API keys—virtual entities that operate behind the scenes to keep modern IT environments running. Picture a cloud server that needs specific permissions to do its job, or an API key that acts as a digital passport for different services to communicate with each other. In many organizations, non-human identities now outnumber human ones, and they can be just as easily exploited if left unmanaged.
Here’s what makes this really interesting: whether we’re talking about a person logging into their email or a cloud instance accessing a database, identity is the critical first step in implementing Zero Trust security. You simply can’t build a solid security foundation without first knowing who—or what—is trying to access your resources.
But Zero Trust access control doesn’t stop there. It goes beyond static permissions and hardcoded roles. Instead, access decisions are driven by dynamic policy, which evaluates not only the identity but also the observable state of the client, the requesting asset, and the environment around the request.
This is where identity attributes come into play—characteristics like location, device posture, business unit, and MFA status. These provide real-time context and are key to making smart, conditional access decisions. Whether an identity is human or non-human, these contextual signals help determine if access should be granted right now, under these conditions.
A strong identity strategy—one built on visibility, context, and control—is what turns Zero Trust from theory into action. It’s how organizations prevent security incidents, reduce risk from compromised credentials, and enable secure access without slowing down the business.
Continuous Monitoring and Assessment
The enterprise monitors and measures the integrity and security posture of all owned and associated assets.
Zero Trust programs need a way to monitor not just the perimeter, but the identities and resources inside it—continuously. A modern identity management approach under Zero Trust principles includes monitoring identity-related metrics to ensure devices and users comply with security policies, even as conditions change.
This goes beyond provisioning and de-provisioning. It’s about observing how identities behave over time. Compliance dashboards, access reviews, and usage-based analysis are critical tools that help organizations answer key questions:
- Are our identities doing what we expect?
- Are they over-permissioned?
- Are they being misused?
With so many breaches tied back to identity, this level of monitoring isn’t optional—it’s foundational.
The enterprise collects as much information as possible about the current state of assets, network infrastructure, and communications, and uses that to improve its security posture.
Too often, the focus is on prevention at build time, not what’s happening at runtime. But true Zero Trust security requires a continuous feedback loop. Identity data should feed into your security telemetry—just like endpoint and network data. This helps ensure identities are being used as expected (not compromised) and have only the permissions they need (not over-permissioned).
This feedback loop is what allows security teams to adapt to new threats and reduce the blast radius when something goes wrong. Because in Zero Trust, it’s not just about setting policies—it’s about making sure they still make sense tomorrow.
Secure Communication and Session Management
Network-Independent Security
All communication is secured regardless of network location.
Whether access happens in a corporate office, at home, or from a hotel Wi-Fi, secure communication must be independent of network location. That’s the network-agnostic principle at the heart of Zero Trust.
Proper access control is at the center of securing that communication. It doesn’t matter where the connection is coming from—the access between systems must be protected by strong identity verification and access policies.
Access to Resources is Granted on a Per-Session Basis
Each session’s access is tied to the validation of identity at the time of the request, not before, and not assumed. Once the session is established, permissions are checked to ensure the resource only gets the access it truly needs.
Whether it’s a human user logging in or a non-human service account spinning up in a cloud environment, access must be explicitly granted and continuously verified. That means roles and permissions need to be right-sized at the time of access—not just statically assigned up front.
The same rule applies when trust is established between machines or platforms. Session-level authentication depends on knowing exactly who—or what—is making the request, and what they should be allowed to do. Without that, Zero Trust breaks down.
Dynamic Authentication and Authorization
All resource authentication and authorization are dynamic and strictly enforced before access is allowed.
Many of us remember the days when VPNs were the backbone of remote access. Always-on connections were the norm—once you were in, you were in. The problem was, these connections weren’t dynamic. Updating permissions or roles often meant re-establishing a connection or waiting for policy changes to catch up. It worked back then, but let’s be honest—it wasn’t built for today’s world.
That old model relied on persistent trust. In a modern Zero Trust architecture, we’ve thrown that out the window.
Today, identity must be continuously verified and dynamically authorized. Access is no longer a one-time gate check—it’s a living, breathing process that evaluates each session based on real-time context.
Whether it’s a login from an unusual location or a service acting outside its normal behavior, permissions need to adjust automatically. That means identity infrastructure has to be more than just a static directory—it needs to respond in real time to changing risk signals.
The only way to enforce Zero Trust is to treat access as temporary, contextual, and revocable—every time. And that starts with making identity dynamic by design.
Conclusion
Identity serves as the thread that connects every aspect of Zero Trust. Without strong identity management, the rest of the framework—no matter how advanced—simply doesn’t hold.
NIST 800-207 lays out a solid blueprint, but whether you’re aligning to that framework or charting your own course, one thing remains consistent: Zero Trust starts with identity and ends with how well you manage, secure, and monitor those identities.
It’s not just about authentication anymore. It’s about control. That means building your strategy around:
- Unified identity stores that give you visibility into who (or what) exists in your environment
- Attribute-based policies that adapt in real-time
- Continuous monitoring of identity behaviour
- Regular reviews of roles and entitlements to prevent privilege creep
Firewalls, policy engines, and access brokers all have their place—but none of it works without a solid identity foundation.
The organizations that recognize identity as the control plane—not just a login step—are the ones who will make Zero Trust work in the real world.
Next Steps: Putting Identity at the Center of Your Zero Trust Strategy
Zero Trust isn’t achieved through a patchwork of tools—it’s built on the foundation of identity. If this blog resonated, here are a few logical next steps to help you move from strategy to execution:
- Understand the Landscape
Download the Veza Product Whitepaper to see how Veza enables identity-first security across hybrid, SaaS, and multi-cloud environments. - Deepen Your Knowledge
Read the Critical Role of Identity Security in Enabling Zero Trust to explore how real organizations are operationalizing identity as the control plane. - Take the Next Step
Ready to see it in action? Schedule a demo with our team to discuss how Veza can help you enforce dynamic access, monitor permissions, and strengthen your Zero Trust posture.
About the Authors
This piece was developed by Tim Chase, Solutions Architect at Veza, in collaboration with Matthew Romero, Technical Product Marketing Manager at Veza.
Tim brings over two decades of hands-on cybersecurity leadership to the table, with a focus on identity, data protection, and product security. Matthew partnered closely on this piece to help shape the narrative and ensure it speaks clearly to today’s enterprise security challenges.






