Let’s Be Honest: IAM Was Never Built for This
Most of us spent the past two decades piling tools into our identity stack — IGA for access certification, PAM for privilege, CIEM for cloud roles, IDPs for login. Each solved a slice of the problem.
But ask the simplest question:
“Who has access to this data, and what can they do with it?” and if all you get back is a spreadsheet, three follow-ups, and a shrug. That’s a visibility gap.
Now, it finally has a name that’s starting to circulate among analysts and security leaders:
Identity Visibility and Intelligence Platform. Or just IVIP for short.
It’s not a product. It’s a framework your stack’s been missing.
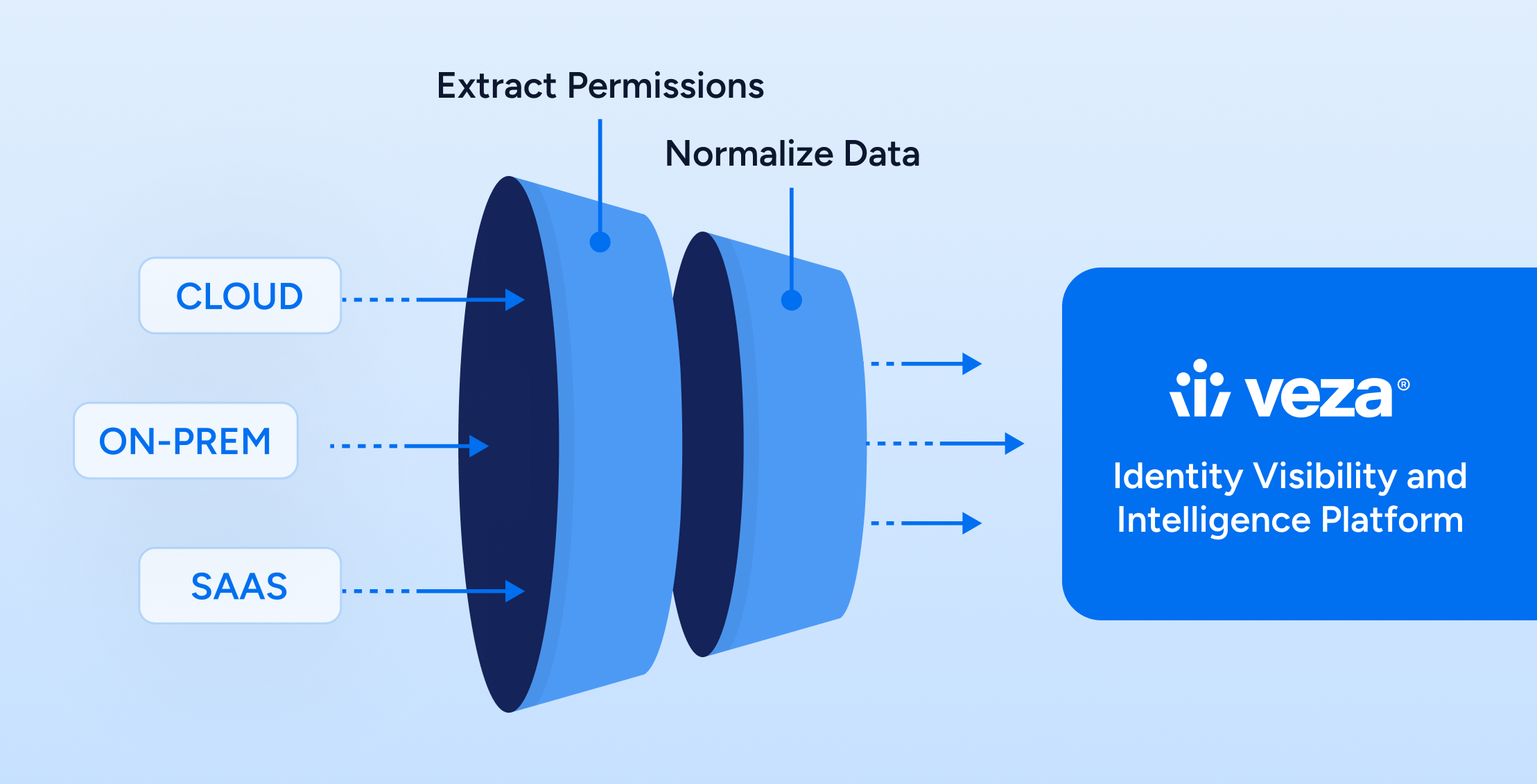
What Is an Identity Visibility and Intelligence Platform?
An IVIP pulls together identity and access metadata from all over your environment: SaaS, cloud, on-prem, even that old HR system nobody wants to touch, and maps it in a way that makes sense.
It’s not another source of truth. It’s the thing that makes sense of all your truths.
Here’s what a true IVIP brings to the table:
- Pulls in identity and access data from every system, human, and machine
- Translates different permission models into a common language
- Maps how identities connect to systems, data, and roles
- Surface access anomalies, toxic combos, unused permissions
- Let’s you ask questions like “Who can touch this?” and “Why does that account still exist?”
It doesn’t hand out access.
It shows you what your stack already allows, and whether that still makes sense.
Why Is IVIP Emerging Now?
Security teams are tired of taping together identity data from 15 tools and hoping for the best.
In Gartner’s recent report, IAM — Taxonomy, Domains and Tooling, analyst Erik Wahlstrom writes:
There is also an emerging concept of “identity visibility and intelligence platforms” that is forming. This is distinct from a traditional user or metadirectory. It gathers, categorizes, and visualizes identity data across directories, tools, and multiple IAM domains. Ultimately, it enhances visibility, governance, and improves IAM hygiene, enabling centralized control in a decentralized environment.
Here’s why this is a critical part of an identity security strategy:
1. The Machines Have Taken Over
Machine identities now outnumber humans by a factor of 40 to 1, according to Veza’s 2024 State of Access Report. API keys, service accounts, containers, and AI agents are constantly requesting access—often with excessive privileges—and then disappearing, leaving behind unmanaged risk.
2. IAM Tools Don’t Talk to Each Other
Entra ID uses “groups,” AWS IAM uses “roles,” and Workday uses “permission sets.” Trying to correlate these across hybrid environments, especially when legacy systems or manual overrides are involved, is where visibility breaks down. Without a unified view, effective access remains buried.
3. Zero Trust Isn’t Possible Without Context
Frameworks like NIST’s Zero Trust Architecture and CrowdStrike’s Zero Trust model stress that visibility and analytics are foundational. If you don’t know what an identity can do, you can’t verify anything. Real-time permission intelligence isn’t optional—it’s how Zero Trust gets enforced.
4. The Board Wants Numbers, Not Excuses
Audit teams need defensible reporting. CISOs need accurate, real-time context. Boards want to understand risk exposure without a glossary. IVIPs provide the clarity to answer critical questions like “Who has access?”, “Why do they have it?”, and “What happens if this account is compromised?”
IAM vs IVIP: Why You Need Both
After years of IAM investments, most organizations already have tools for provisioning, authentication, and privileged access. These tools are essential, but they weren’t built to provide a unified, real-time view of what identities can actually do across hybrid environments.
That’s where Identity Visibility and Intelligence Platforms (IVIPs) come in. IVIPs are not replacements for IAM tools. They’re purpose-built platforms that sit across existing IAM systems and enterprise resources, bringing context, correlation, and clarity to fragmented access data.
Here’s how the two categories compare:
Comparison Table
| Need | Traditional IAM Tools | Identity Visibility & Intelligence Platforms |
|---|---|---|
| Provision and deprovision users | IGA | Not designed for this |
| Manage passwords, secrets, and keys | PAM, Secrets Manager | Not designed for this |
| Authenticate users | IDP (e.g., Okta, Entra ID) | Not designed for this |
| Understand what a service account can access | CIEM, PAM (limited scope) | Full-context visibility across environments |
| Visualize access across SaaS, cloud, and on-prem | IGA, CIEM (siloed views) | Unified, normalized permissions map |
| Detect unused or toxic access patterns | IGA, PAM (manual or reactive) | Automated insight based on real-time data |
| Run real-time queries like “Who can access this system or dataset?” | Requires manual correlation across tools | Built-in, queryable intelligence layer |
- IGA (Identity Governance and Administration): Manages user lifecycle, provisioning, and certification
- PAM (Privileged Access Management): Manages secrets, credentials, and elevated access
- IDP (Identity Providers): Authenticate users, manage federation, and SSO
- CIEM (Cloud Infrastructure Entitlement Management): Manages cloud-specific entitlements
- IVIP: Normalizes and correlates access data across all of these to answer: Who can take what action on what data, and should they?
Traditional IAM tools are essential for access control and operations.
IVIPs are critical for access intelligence and governance at scale.
Together, they enable organizations to move beyond simply granting access to understanding and governing it intelligently. That’s the difference between surviving an audit and preventing the next breach.
You’ve already got a stack. IVIP makes it smarter.
Where IVIP Helps the Most
Many of the challenges IVIP solves today didn’t exist when IAM first emerged. That’s why Identity Visibility and Intelligence Platforms (IVIP) have become essential: they address modern use cases that traditional IAM was never built for.
- Incident Response: Find the blast radius before the next meeting starts.
- Access Reviews: Certify access with actual context, not just a list of usernames.
- Zero Trust Initiatives: Enforce least privilege based on real data, not assumptions.
- Audit and Compliance: When the regulators ask questions, IVIP gives you answers you can stand behind.
- AI Security: Non-human identities are exploding. IVIP keeps them in check.
What to Look for in an IVIP Platform
Not all “visibility tools” are created equal. Here’s what to ask:
- Can it connect to SaaS, cloud, on-prem, and IDPs?
- Does it support service accounts, secrets, and machine identities?
- Can it show effective permissions in business language?
- Is the data real-time, not stale exports?
- Does it help you act — or just observe?
If it just gives you dashboards and another place to click around, it’s not an IVIP. It’s a report.
FAQ: Common Questions About Identity Visibility and Intelligence Platforms
What is an Identity Visibility and Intelligence Platform?
An IVIP is a framework that pulls together identity and access data from across your environment—cloud, SaaS, on-prem, and more—and normalizes it into a unified, real-time view. Unlike IAM tools that hold individual pieces of the puzzle, IVIPs focus on what identities can do. For an overview and vendor comparisons, see Forrester’s Customer Identity and Access Management Solutions Landscape Q3 2024.
How does an IVIP differ from traditional IAM tools?
Traditional IAM tools like IGA, PAM, and IDPs manage specific parts of the identity lifecycle, authentication, and privileged access. But they typically operate in isolated silos. IVIPs layer on top to connect these pieces, providing visibility into effective permissions and access risk across the entire stack. The NIST Digital Identity Guidelines (SP 800-63) provide foundational context for these identity management functions.
Why is real-time identity visibility important for Zero Trust security?
Zero Trust demands continuous verification of every identity and its permissions. Without up-to-date visibility into what users and machines can access, enforcement is guesswork. IVIPs provide the ongoing intelligence needed to make Zero Trust policies actionable. Read more on the principles in the NIST Zero Trust Architecture (SP 800-207).
What role do machine identities play in identity security?
Machine identities—including API keys, service accounts, and AI agents—now outnumber human users by a wide margin. They often accumulate excessive privileges and can disappear without notice. Managing these non-human identities is critical to reducing the attack surface and preventing breaches. Learn more in Veza’s blog on What is a Machine Identity?.
Can IVIPs help with audit and compliance requirements?
Yes. IVIPs provide context-rich access reports that answer vital questions like “Who has access? Why? Is it still justified?” That clarity is essential when preparing for audits, explaining risk to boards, or enforcing governance policies. For example, see how Conifer Retail moved from reactive cleanup to automated compliance with PCI DSS 4.0 using access reviews and audit-ready controls powered by Veza. (From Crisis to Compliance: How Conifer Retail Rebuilt Trust)
Bottom Line: Know Who Can Do What – Everywhere
Identity and security teams don’t need another acronym. They need answers to basic, high-stakes questions about identity and access. Threat actors like Volt Typhoon have made identity attacks their hallmark. With no malware to detect, visibility into permissions and access has become a pillar of security.
IVIPs give you that. They’re not here to reinvent your stack. They’re here to help you understand what that stack has already created. And in a world of AI agents, distributed apps, and machine-speed risk? That understanding isn’t optional.
Keep Going: Build on Your IVIP Strategy
If the idea of an Identity Visibility and Intelligence Platform resonates, you’re not alone. Many teams are already asking what comes next once the limits of traditional IAM tools are exposed. Below are a few places to keep the momentum going.
Start with the foundation
Learn how Identity Security Posture Management helps close visibility gaps that legacy IAM tools leave behind. It’s the first step toward understanding not just who has access, but what that access actually allows.
Read the blog → https://veza.com/blog/identity-security-posture-management/
See it applied in the real world
Explore how organizations are using Veza to secure SaaS environments by mapping access, identifying risky permissions, and enforcing least privilege across apps like Salesforce, GitHub, and Workday.
View the SaaS Access Use Case → https://veza.com/use-cases/saas-access-security/
Want to see it live?
Schedule a personalized demo to see how Veza brings IVIP to life across your actual environment – cloud, SaaS, and on-prem.
Schedule a demo






