Blog
-
 Identity Security
Identity SecurityUnderstanding ISPM: Closing the Identity Gap with Identity Security Posture Management
ISPM is a new category of identity security designed to help organizations continuously monitor and manage identity risk across cloud, SaaS, and hybrid environments. Learn how Identity Security Posture Management works, why it matters, and how Veza enables it. -
 AI
AIVeza Access AI – Applications of Gen AI for Identity Security Use Cases
Veza Access AI transforms identity security by enabling natural language queries to navigate complex access landscapes, empowering organizations to achieve least privilege effectively.
Explore our posts
-

Taming the M&A Chaos: How Veza Addresses Identity Security Risks During Mergers, Acquisitions, and Divestitures
Learn more -

Automating Veza Access Requests for the Enterprise: Integrating Veza with ServiceNow
Learn more -

Forrester Recognizes Veza for IGA, ISPM, and NHI/AI Identity Management
Learn more -
2025: The Year of Product Innovation
Learn more
-

When Logging In Is the New Hacking: Nicole Perlroth on the Evolving Cyber Threat Landscape
Learn more -

Simplifying CMMC 2.0 Compliance: Modern Access Control Strategies for Government Contractors
Learn more -

Achieving DORA Compliance: A Practical Guide for Financial Organizations
Learn more -

The Evolution of Identity and Security at Workday: Insights from CISO Josh DeFigueiredo
Learn more
-
Privilege Creep: What It Is and How To Prevent It
Learn more -
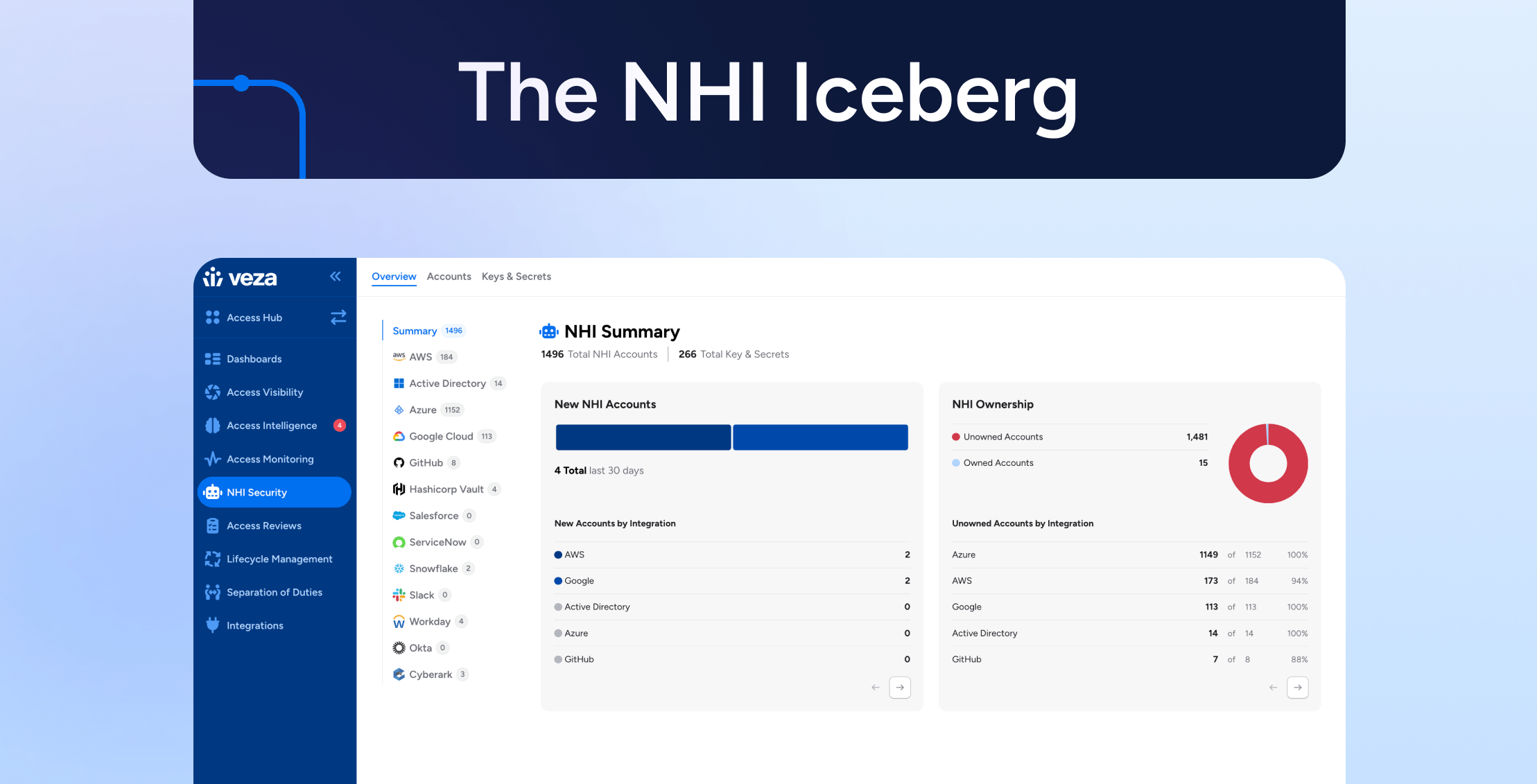
The NHI Iceberg: Veza NHI Security brings visibility and actionability of the hidden risks across the enterprise
Learn more -
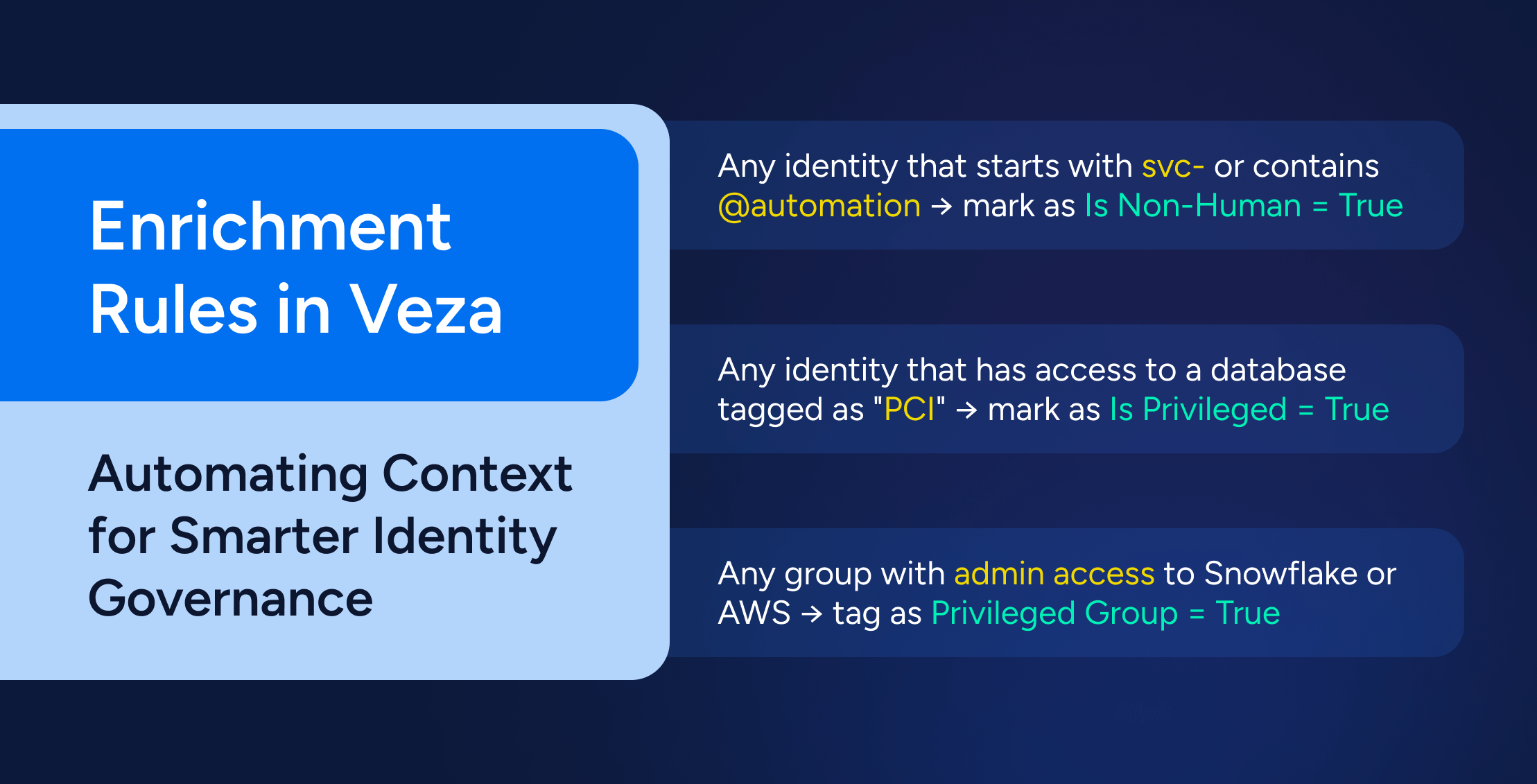
Enrichment Rules in Veza: Automating Context for Smarter Identity Governance
Learn more -
What is Cloud Identity Security? Key Considerations
Learn more -
How AI is impacting identity security and privileged access management in 2025
Learn more