Why Veza?
The scope, scale, and complexity of access control has skyrocketed, creating new surface area for identity-based cyber threats. And with the frequency and cost of data breaches also accelerating, the stakes have never been higher.
Old tools, built on old technology are no longer enough.































Why do you need Intelligent Access?
The increasing scale and complexity of managing access, along with the growing frequency and cost of identity-based attacks, demands a new approach to identity security. The old ways aren’t working any more.
1,295
Number of cloud services used by the average enterprise org. Plus an average of 364 SaaS apps.
17x
Machine identities outnumber human identities in the cloud by an average of 17 to 1.
75%
Share of breaches that occur through theft or misuse of identities.
$4.45mil
Global average cost of a data breach. In the US, it’s $9.48mil.
What is Intelligent Access?
“Intelligent Access” means that access is governed at the speed of business. Permissions are granted and revoked automatically and continuously, in accordance with security policies, for all identities and all systems.
Any company looking to govern access to data at scale should insist on the five key tenets of Intelligent Access.
To learn more about Intelligent Access, read our book or watch the book launch with authors Tarun Thakur and Phil Venables.
All systems
Sensitive access exists across all of your systems and controlling it demands a unified approach. You need one platform that can connect quickly to any enterprise system, whether it’s on-premise or in the cloud.
All identities
You won’t achieve least privilege trying to tackle federated identities, local accounts, and machine identities with different platforms. You need all identities, both human and non-human, managed in one place.
True permissions
You need to see beyond users and groups to understand each identity’s detailed permissions in apps and resources. Groups and roles change all the time, and they are often mislabeled. The only way to see the true reality of access is to look at permissions.
Standardized
Knowing permissions isn’t useful if you don’t understand them. Together, AWS, Azure, and GCP have over 21k permissions available. Security teams and stakeholders need standardized plain-English descriptions: who can create, read, update, and delete.
Automated
To tackle the scale of access in modern IAM, you must be able to automate decision-making, including continuously monitoring access permissions, checking against policies and best practices, and fixing violations.
Benefits of Intelligent Access
Veza is trusted by top financial institutions, healthcare organizations, retailers, security providers and other public companies. Join them to share in the benefits of Intelligent Access.
The Veza Advantage
Time to value
Veza connects to your systems in minutes, not months, and delivers immediate value in visibility and remediation, with out-of-the box intelligence on key risks and misconfigurations. Unlike traditional IGA solutions, Veza does not need long deployments with professional services building integrations to your systems.
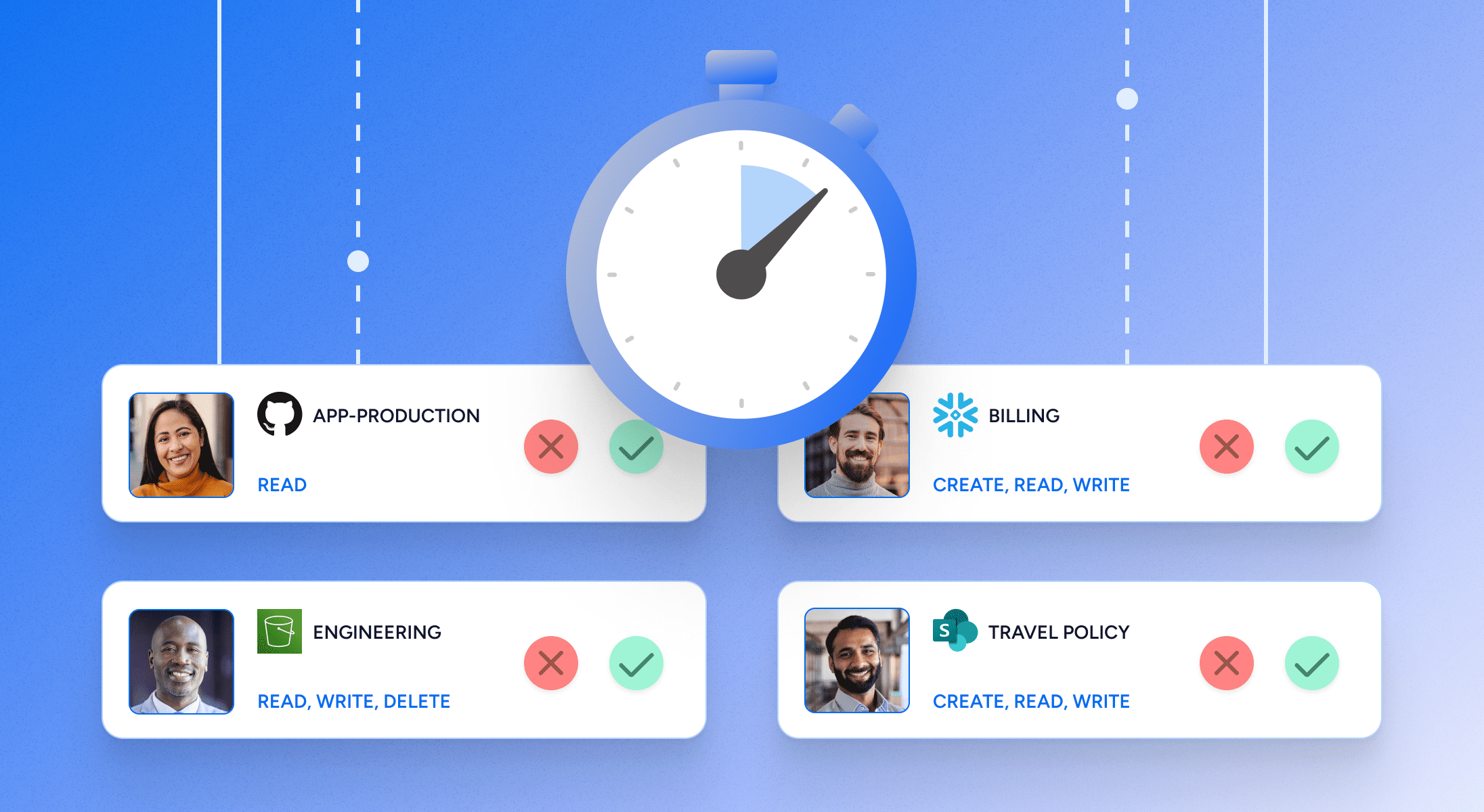

Coverage
Only Veza can cover all your systems. Veza has hundreds of native integrations covering on-prem apps, cloud services, SaaS apps, and data lakes. To fill any gaps, Veza’s Open Authorization API (OAA) allows for building quick custom integrations to your own apps.
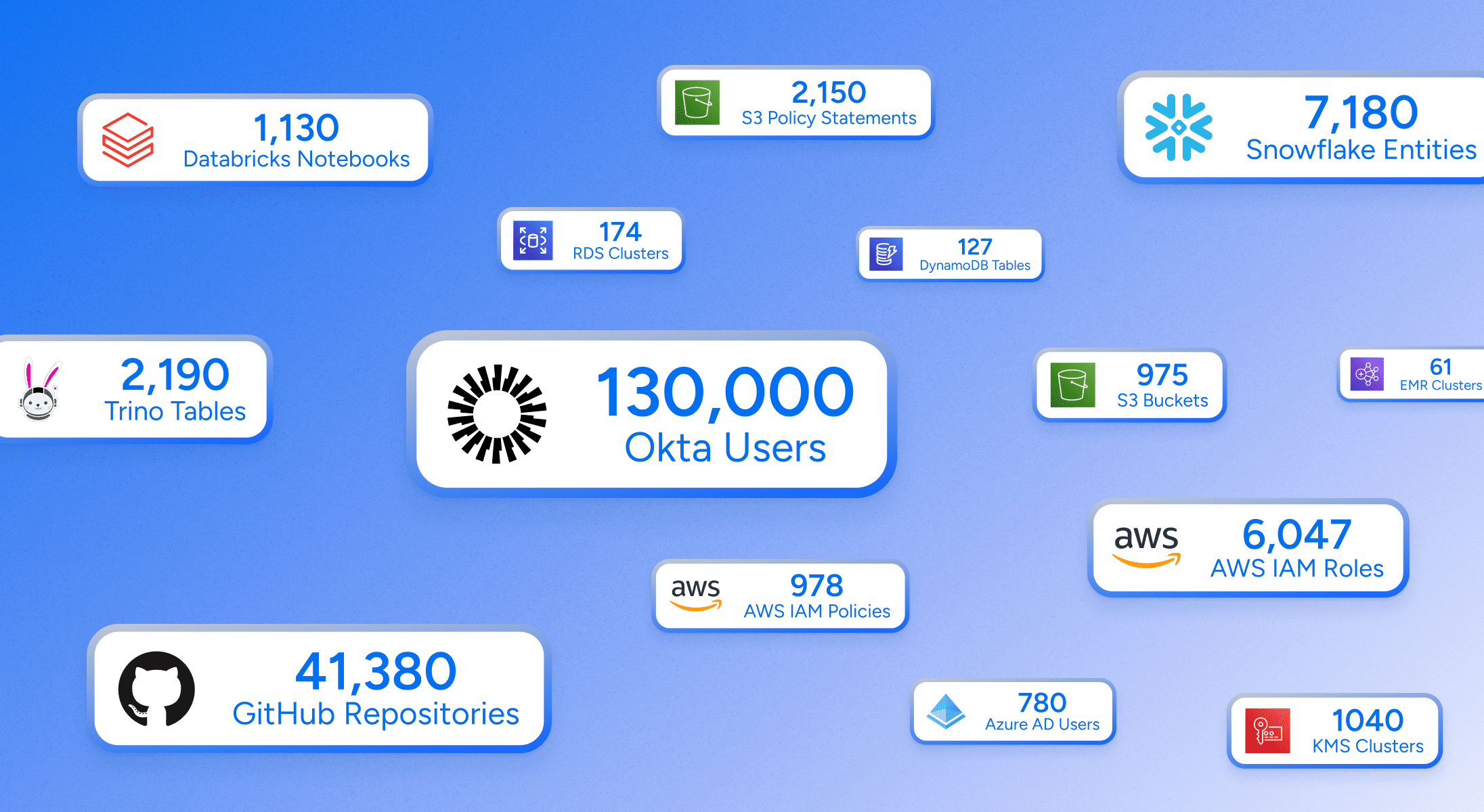
Proven Scale
Veza’s purpose-built graph infrastructure—already protecting over 30 million identities and 500 million permissions—is engineered to handle the scale and complexity required by large enterprise customers. We built the Veza platform to seamlessly support massive AI/ML-based capabilities, from access recommendations to universal search and more
Born in the cloud
Veza is a modern, cloud-native SaaS platform that introduces no admin overhead when deploying new updates. It also takes an API-first approach, which means that customers can build the power of Veza’s Access Graph into their own security apps.
Secure
No agents, installers, ports, or firewalls. This out-of-band approach means no risk of downtime. Veza embraces industry best practices including independent penetration testing, data encryption at rest and inflight, strict role-based access controls, complete tenant isolation and zero external access by design. Veza is SOC 2 Type II, and ISO 27001 certified, demonstrating our dedication to security and compliance.

Unified
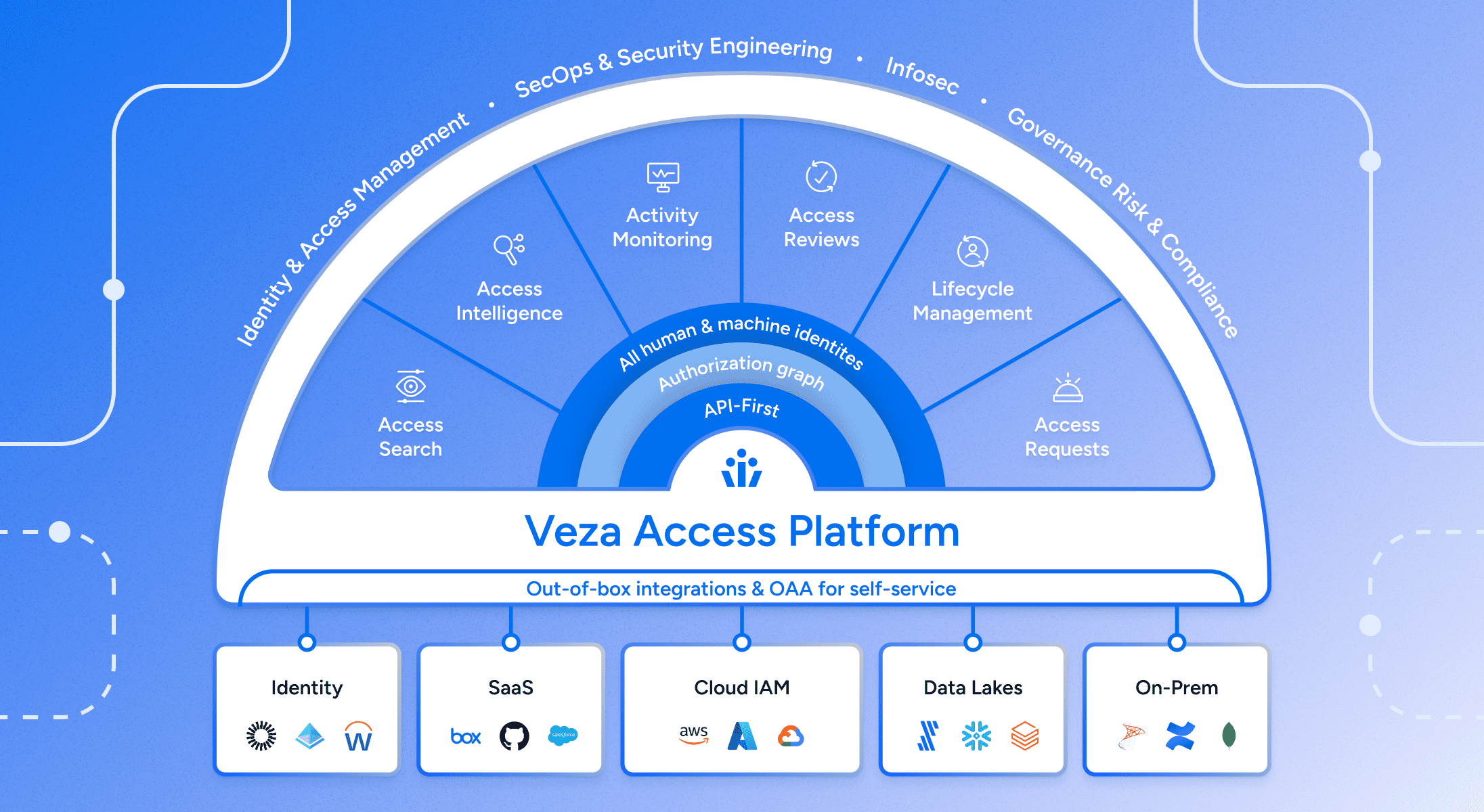
Veza provides a unified Access Platform, with native products offering access search, access intelligence, access monitoring, access workflows, lifecycle management, and access requests. API-first design enables a unified ecosystem experience with tooling like ServiceNow, Snowflake, AWS, and more. A unified experience helps organizations realize fast time to value, hard savings, and operational savings.

Veza’s Vison
Join Veza’s Co-Founder and CEO Tarun Thakur to explore Veza’s vision for Intelligent Access.

