Welcome to the latest Veza product update! We’re excited to share the latest summary of new features, enhancements, and operational improvements introduced in our 2025.7 releases.
Veza 2025.7 extends our leadership in next-gen identity security by unifying access visibility, access intelligence, governance, and automation for all identities—human, non-human, and agent identities. With these new updates, organizations gain:
- Lower risk of identity-driven breaches through deeper monitoring and remediation.
- Reduced compliance costs with automation and pre-built audit evidence.
- Higher efficiency and scalability through workflow controls and expanded integrations.
This release enhances access monitoring capabilities, expands integration support with new vault-based credential management, and advances lifecycle management workflow controls and identity resolution capabilities, with highlights including:
Enhanced Access Monitoring and Intelligence
- Last Activity Time Filtering – Filter Query Builder results by last activity timestamps for AWS, Snowflake, Google Cloud BigQuery, SharePoint, and Okta to identify dormant and over-provisioned access.
- Query Builder Controls – Improved advanced queries supporting an optional “direction” parameter, for more precise and efficient search.
- Permission Summarization Across Resources – Automatic display of Effective and System permission summaries when showing source-destination relationships in Query Builder.
- Query Change History View – Before-and-after change history for any SoD and saved query, such as alterations to query conditions, name, or risk level.
- Dashboards Grouped by Security Scenario – Browse and act on organized collections of pre-built dashboards grouped by security scenarios, such as MFA analysis, NHI monitoring, ISPM, and cloud security frameworks.
Enhanced User Experience for Access Reviews
- Enhanced Access Review Configuration – Administrators can now enable default “Group By” settings in the Reviewer Interface (globally or for individual configurations) to customize the reviewer experience.
- Advanced Review Column Controls – Administrators can now remove specific columns from reviewer visibility, extending the existing option to hide certain columns by default.
- Improved Access Review Digest Notifications – Digest notifications now display destination data sources and include a customized digest summary for better reviewer context.
New and Enhanced Lifecycle Management Capabilities
- Custom Attribute Transformer Functions – Create reusable, custom transformation logic within policies to replace complex pipelines of built-in transformers with built-in macros.
- Random Integer Transformer – Generate random integer values within specified ranges for attributes such as unique identifiers in Lifecycle Management workflows.
- Enhanced Workflow Execution Controls – New delay trigger recheck controls and “Run Once” options for operations that should not be duplicated once successful.
- Azure Unique Identifier Support – Configurable unique identifier lookup for Azure AD users for more flexible user matching.
- Access Profile Name Transformers – Automatic naming rules for Access Profiles to standardize entitlements using organizational data or dynamic values.
NHI Security Enhancements
- Expanded Coverage – Extended support for 90+ NHI identities and secrets across major platforms.
- New NHI Landing Page – Enhanced visual clarity and navigation with expanded integration support and improved navigation.
- Improved NHI Classification – Salesforce API-only users are now marked as Nonhuman identities.
- Enhanced time range Filtering – Improved time range filtering for NHI Accounts.
Expanded Integration and Security Features
- Salesforce Guest User Profile Discovery – Discover Guest User Profiles providing public access to Salesforce sites and communities
- CSV Upload with Entity Owners – Set Entity Owners for custom applications using an owners column when importing your CSV
- Complete GCP IAM Role Permissions – Visibility into the full unfiltered set of GCP IAM role permissions, including custom & predefined roles in your environment
- Azure Secrets Vault Support – Use Azure integration credentials stored in external secret vaults, as an alternative to saving secrets in the integration configuration.
See each section below for more information on specific updates. Please reach out to the Veza support team with your valued questions or feedback.
Access Monitoring
New Features
Query Builder Last Activity Time Filtering
Query Builder now supports filtering results by last activity timestamps when audit log extraction is enabled for specific target systems such as AWS, Snowflake, Google Cloud BigQuery, SharePoint, and Okta. This enhancement enables the identification of dormant access and over-provisioned permissions through activity-based analysis.
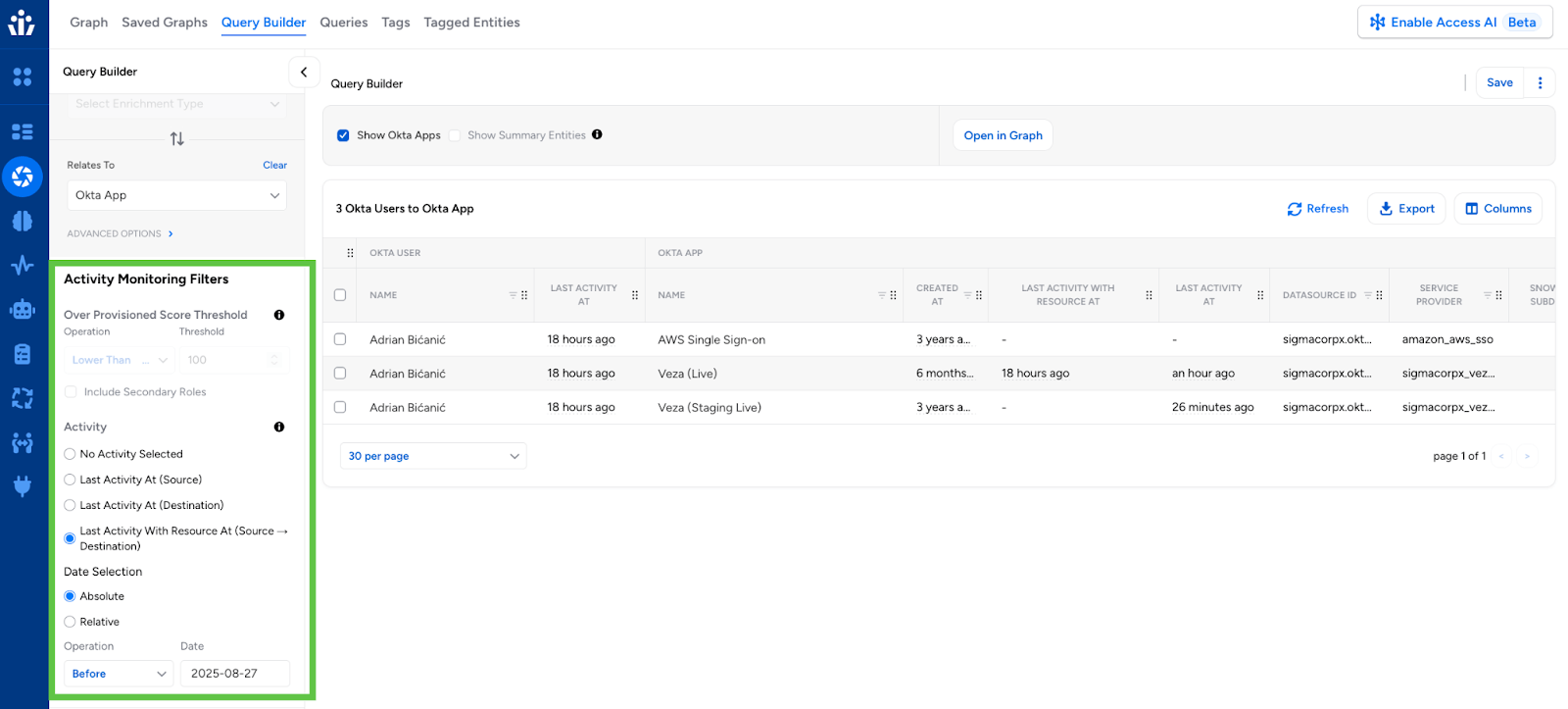
How to use it: Filters support both absolute timestamps and relative ranges like “activity within the last 30 days” for flexible access analysis. Note that “Show destination entities” must be enabled to display destination-related activity filters.
{% hint style=”info” %}This feature requires Access Monitoring to be enabled for the respective integrations and provides visibility into actual usage patterns to support access certification and cleanup initiatives. {% endhint %}
Access Intelligence
Enhancements
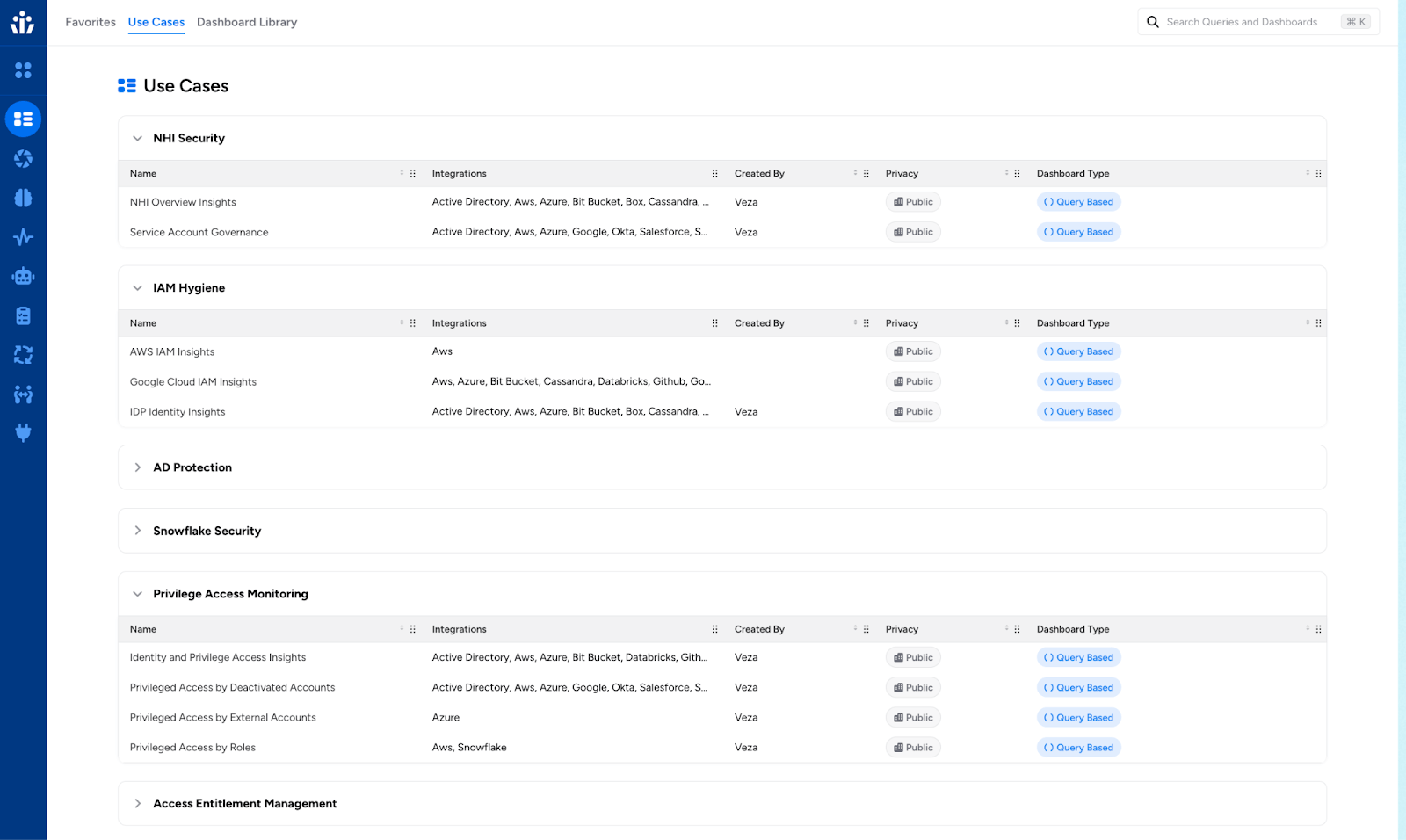
Security Scenario Dashboards
Access Intelligence now provides organized collections of pre-built dashboards grouped by security scenarios, including MFA analysis, NHI monitoring, ISPM, and cloud security frameworks. This feature is now generally available to help you quickly explore relevant dashboard collections based on your specific security needs.
Query Builder Direction Controls
Added direction options to Query Builder Advanced Options. You can now specify whether your query results will show incoming relationships (entities pointing toward the source), outgoing relationships (entities the source points to), or any direction (default).
Permission Summarization Across Resources
Query Builder now automatically displays columns summarizing Effective and System permissions when using the “Relates To” option to show results as source > destination pairs. This provides a better view into actual system permissions and effective access for each relationship.
Separation of Duties (SoD)
Enhancements
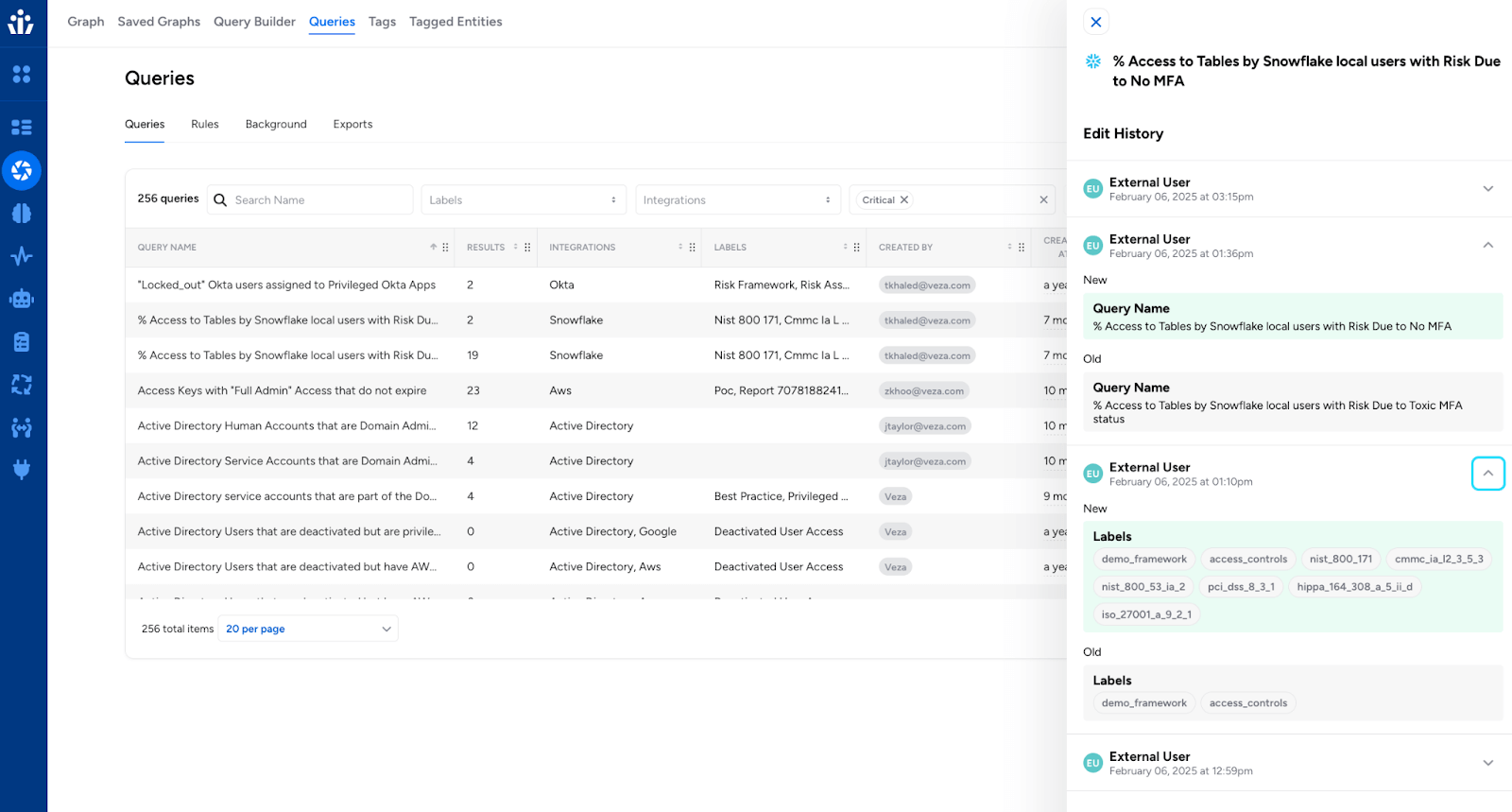
Query Change History View
You can now view a complete change history for Segregation of Duties (SoD) and other queries. The new sidebar provides a before-and-after view of the changes to query conditions and other metadata, such as modifications to query name, description, or risk level.
Access Reviews
Enhancements
Default “Group By” Configuration
Added both a global setting and a Review Configuration level setting to control the default “group by” column and specify collapse/expand behavior in the Reviewer Interface. When enabled, rows are automatically organized by column values such as resource name, identity name, or review status, making it easier to review related items together.
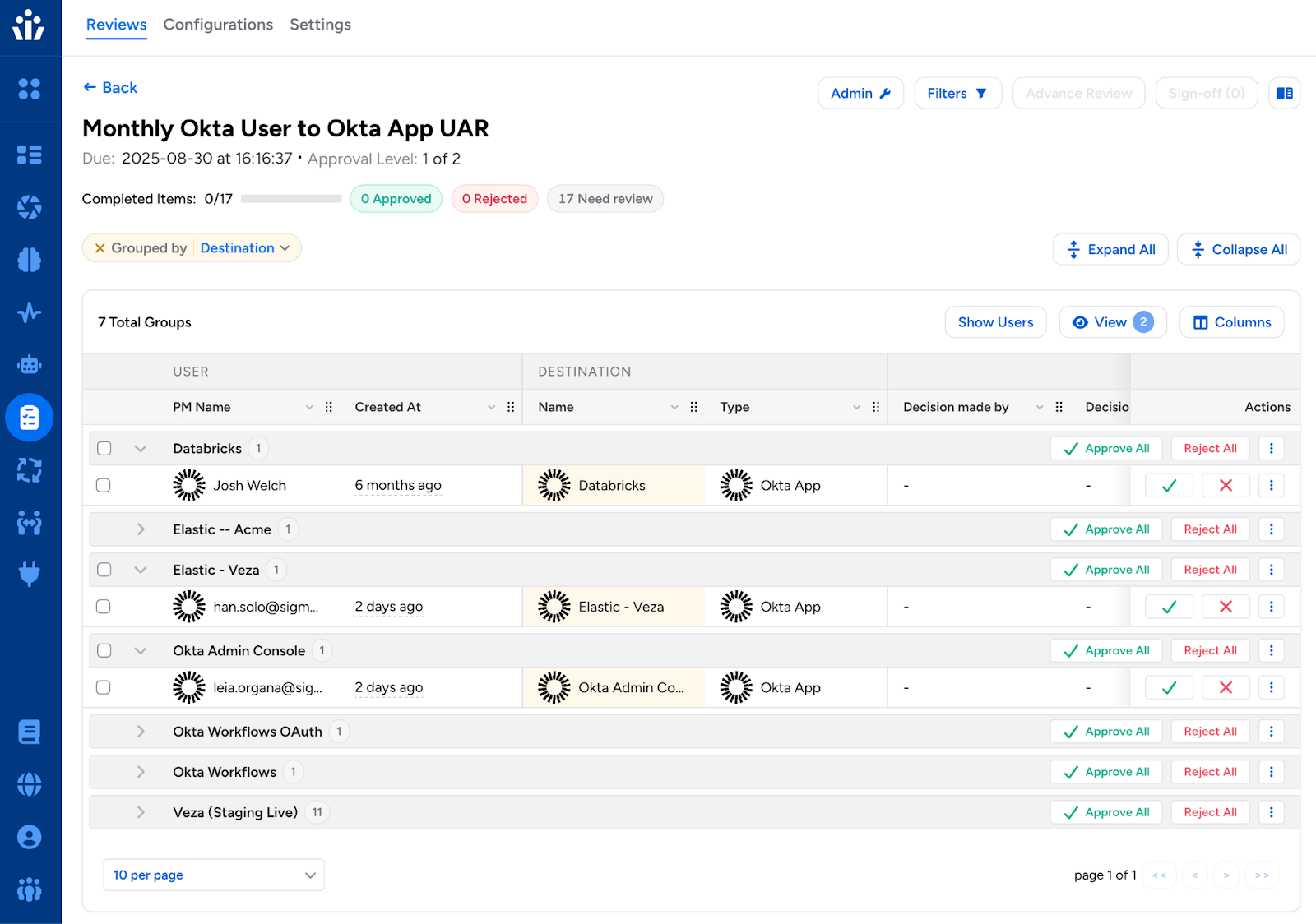
- Administrators can now set default “group by” columns (such as Source, Destination, or Risk Level) using the Access Review Settings API.
- Row grouping can be configured globally (establishing the default for all new reviews) or per Review Configuration (overriding the global default for specific review types).
Column Visibility Settings
Administrators can now use the Admin > Manage Columns option within specific Reviews to fully disable certain columns from being available for reviewers.
This will fully remove those columns from availability in the Reviewer Interface, as opposed to the existing option to hide visibility of specific columns by default.
Access Review Digest Notifications with Data Source Context
Digest notifications can now include information about specific destination data sources associated with their assigned reviews, helping reviewers better understand which applications, databases, or services each review applies to. This can be especially useful in environments with multiple applications of the same type.
How to use it:
- A new template placeholder {{DIGEST_NOTIFICATION_WITH_SUMMARY_TABLE}} includes application names for each review in the table of the recipient’s assigned reviews.
- Administrators can create custom digest notification templates using Access Reviews > Settings > Notifications.
- Each Access Review workflow can include a custom digest summary text (configured via API) to identify specific names in the digest notification summary tables.
Enhanced Review Configuration Management
Added the “Schedule set” column to the Review Configurations table (under Access Reviews > Configurations), making it easier to see which review configurations have a recurring review schedule applied.
Access Lifecycle Management
Enhancements
New RANDOM_INTEGER Transformer
- Synced attributes can now use a RANDOM_INTEGER transformer to generate random integer values within a specified range (minimum and maximum values). This transformer is useful for creating unique identifiers, test data, or randomized values during provisioning workflows or Dry Runs. For example: Veza{| RANDOM_INTEGER, 1, 100} generates values like Veza42 or Veza87.
Enhanced Workflow Execution Controls
- Delay Trigger Recheck Control: Added a new toggle to control whether workflows recheck their trigger conditions when executing delayed or scheduled actions.
- The Don’t recheck trigger condition on delayed or scheduled tasks toggle is automatically disabled when no delay is configured and automatically enabled for “Mover” scenarios to prevent failed trigger rechecks.
- This option is available when editing the workflow trigger node in the Policy editor.
- “Run Once” Option for All Actions: For improved control over sensitive operations that should not be repeated, actions now support a “Run Once” option to skip execution if the action has already been completed for the same identity. This provides a safety mechanism that prevents the same action from executing multiple times for the same identity when the workflow is re-triggered.
- Only a previous successful completion prevents re-execution. Failed actions will retry. Skipping a “run once” action won’t interrupt the rest of the workflow.
- “Run Once” should be enabled to prevent duplication of email accounts, welcome emails, or password reset actions. It should also be enabled for one-time provisioning actions that create resources that should not be duplicated.
- Custom Attribute Transformer functions within Lifecycle Management Policies: This enables administrators to create reusable, custom transformation logic that can replace complex pipelines of built-in transformers. For example, a custom transformer named $CLEAN can be defined within a policy version and used as {first_name | $CLEAN}.
- In this example, $CLEAN might resolve to a series of pipelined transformer functions, such as | ASCII | LOWER | REMOVE_CHAR, “.@,”.
- Note that custom Attribute Transformers may not include transformer functions with parameters (e.g., REMOVE_CHARS “abc”, SUB_STRING 0,5) and nested transformer functions (custom transformers cannot reference other custom transformers).
Improved Identity Resolution
- Azure Unique Identifier Support: Lifecycle Management now supports configurable unique identifier lookup for Azure AD users, enabling alternative user identification methods during lifecycle operations. This addresses scenarios where User Principal Names (UPN) change during employee transitions.
- Enhanced Identity Properties: Identity attributes shown in Dry Run previews and Identity view are now sourced directly from the Identities metadata store, including Lifecycle Management-specific attributes and overridden attribute values. Previously, Dry Run used Graph as the source of identity metadata.
- Sync Identities Write-back Mode: The write-back mode for Sync Identities actions now activates automatically when selecting a Source of Identity integration as the target. The action configuration clearly shows “writing back to identity source” status and hides unnecessary options for SOI integrations. This change ensures that Sync Identities actions only update existing identities in the Source of Identity (SOI) system, preventing the creation of new records.
Advanced Action Configuration
- Policy Identity Overrides: You can now apply override values to individual identity properties (such as name, email, active status, department, and other fields) in the Identities tab, with support for Dry Run simulation of override values.
- Sync Identity Selection for Deprovision Actions: You can now choose which Sync Identity actions to match when configuring Deprovision Identity actions, for precise selection when policies sync multiple entities to the same target application.
- Reset Password Action Unique Identifier: Reset Password actions now support Action Unique Identifiers for consistent identity resolution across all action types, improving the reliability of password reset operations.
Non-Human Identity (NHI) Security
Enhancements
Expanded Integration Support
Veza now provides coverage for 90+ NHI identities and secrets, including AWS, GCP, Active Directory, Azure AD (including relationships between Service Principals and Azure AD Roles), Okta, SharePoint, Snowflake, GitHub, Salesforce, HashiCorp, and CyberArk.
Improved Classification Logic
- Okta App User classification now inherits the identity type from the Okta App User’s corresponding Okta User account. When an associated Okta User exists, the App User now automatically adopts the same identity type classification (human or non-human). App Users without corresponding Okta User accounts are marked by default as human identities.
- Salesforce Users assigned built-in “API-only” Integration Profiles are now automatically marked with the Nonhuman Identity Type. API-only profiles include: Salesforce API Only System Integrations, Minimum Access – API Only Integrations.
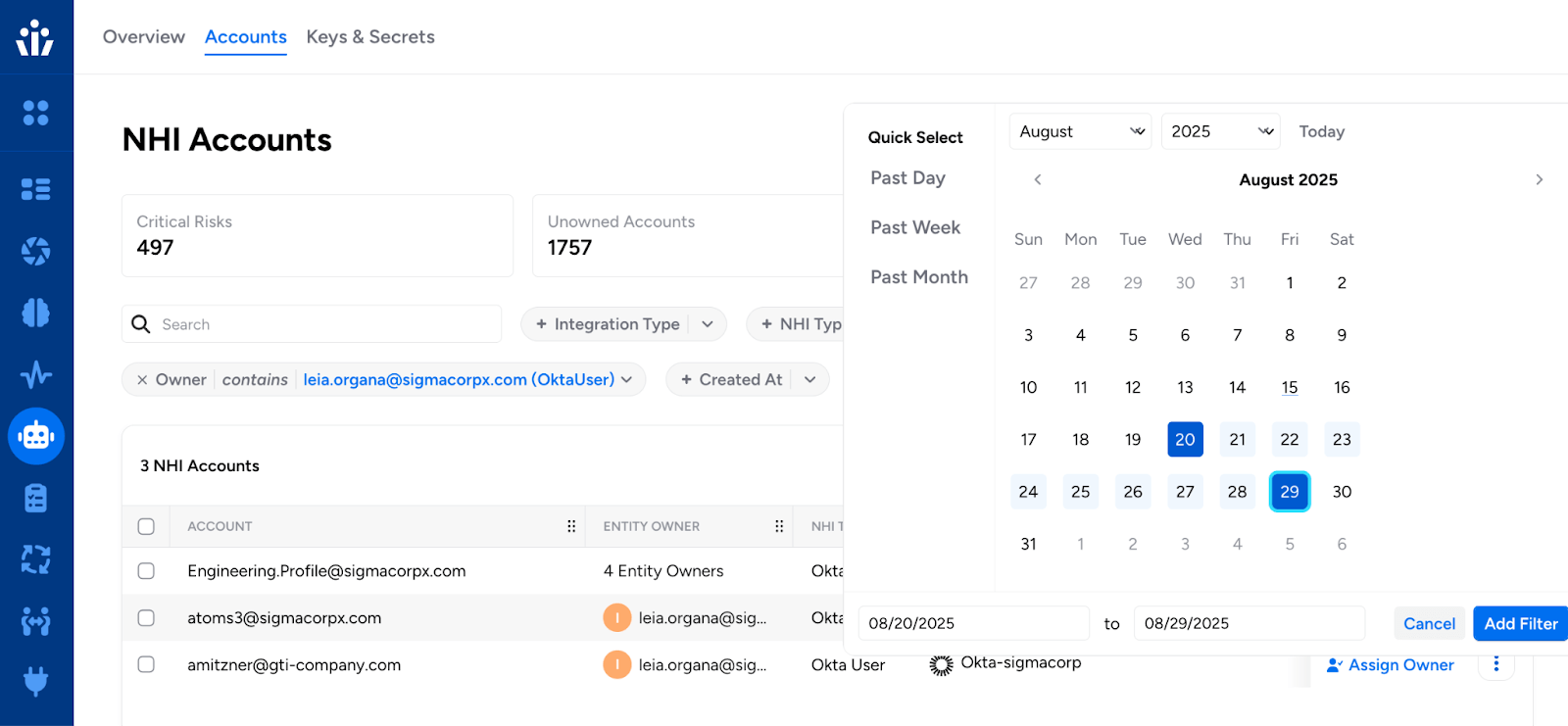
Enhanced NHI Account Filtering
The NHI Security > Accounts view now supports filtering to focus on identities created within a specific date range, improving the ability to track and manage recently created non-human identities.
Redesigned NHI Landing Page
The NHI Overview page has been redesigned for visual clarity and improved usability. This landing page now provides a summary of NHI accounts across your top integrations, with the option to drill down to specific integrations for detailed insights about accounts, keys, and secrets within that integration.
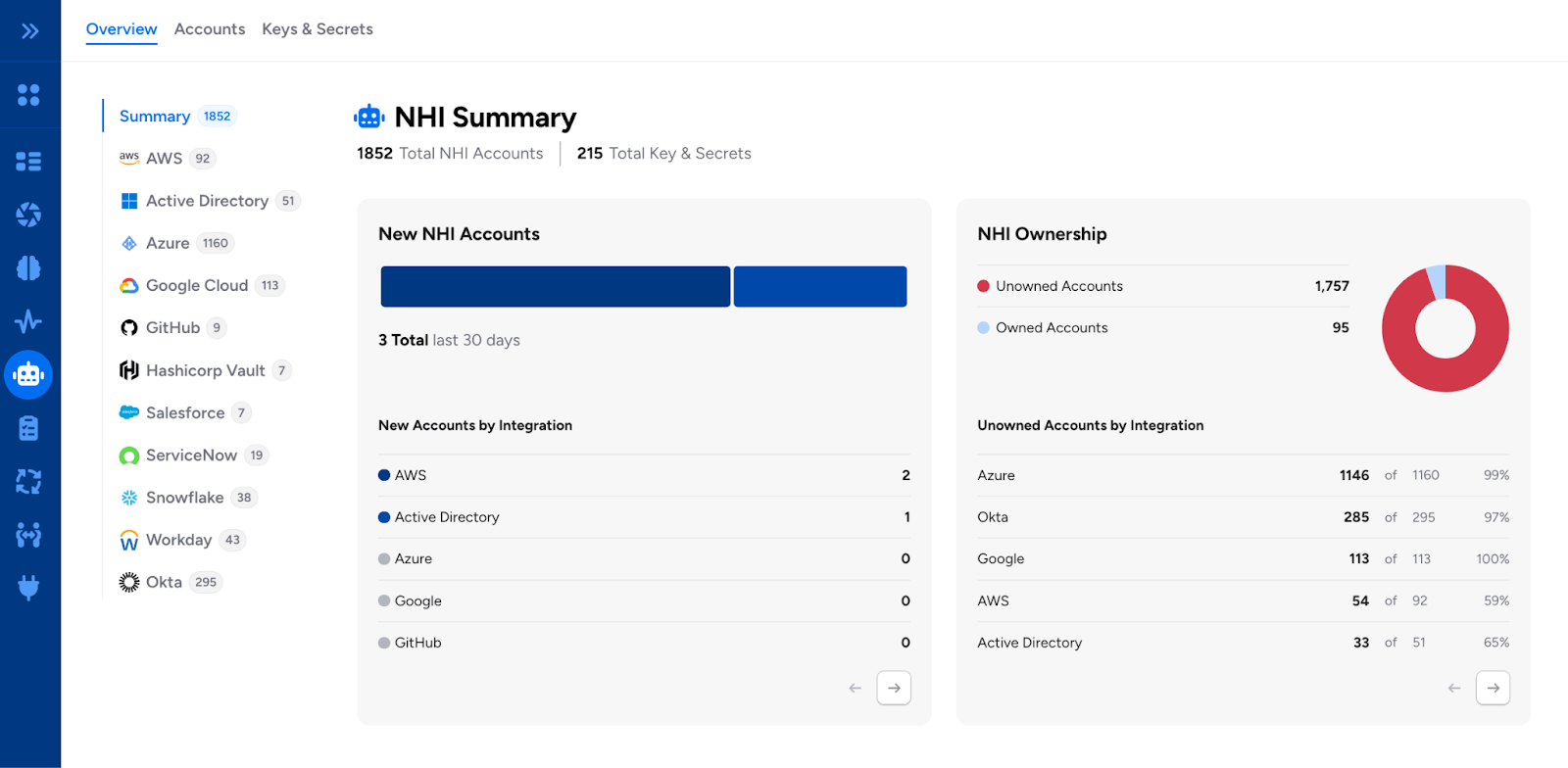
Clicking any NHI entity opens the Accounts or Keys & Secrets view for more information about specific entities, with support for:
- Owner assignment for human accountability
- Blast radius inspection using Graph search
- Review Risk Scores to prioritize security risks
- Launch Veza Actions for access reviews and remediation
NHI Entity Information in Integrations
A new section, NHI Entity Types and Entities, has been added to the integrations page. This dedicated section now offers granular information for the chosen NHI integration, providing better visibility into non-human identities across different systems.
Veza Integrations
Enhancements Across Enterprise Integrations
- Assign Entity Owners for CSV Upload: The CSV Upload integration now supports setting Entity Owners for custom applications, with configurable owner ID columns for Users, Groups, Roles, and Resources. This enables direct import of ownership metadata for improved governance and automatic reviewer assignment.
- Azure Secrets Vaulting (Early Access): When configuring an Azure integration, you can now use Azure integration credentials (client ID, client secret, certificates) stored in external secret vaults instead of securely storing secrets in the Veza integration configuration. This option requires a configured Insight Point with vault access and secrets stored in JSON format containing all required Azure authentication fields.
- Open Authorization API (OAA) Entity Owner Support: You can now assign entity owners directly in Open Authorization API Custom Application payloads, eliminating separate API calls after entity creation. Owner assignments integrate with Access Reviews auto-assignment, NHI Security governance, and Query Builder filtering.
- Complete GCP IAM Role Permissions: The Google Cloud Platform integration now shows the complete, unfiltered set of GCP IAM role permissions, including custom and predefined roles across project, organization, and folder levels.
- Azure Sensitivity Label Support: The Azure integration now extracts and displays Microsoft Purview Information Protection sensitivity labels applied to Azure AD groups and SharePoint Online sites. This provides visibility into data classification policies across Microsoft 365 environments, including metadata such as description, color coding, and protection settings.
- Enhanced LDAP Compatibility: The generic LDAP integration now supports configurable group object classes and member attributes, for greater compatibility with LDAP implementations that do not implement the default `groupOfUniqueNames` standard (such as Red Hat Identity Manager).
- SharePoint Term Store Admins: Added support for extracting SharePoint Term Store Administrators for visibility and governance of the highest level of management permissions across SharePoint tenants.
- Transformations for CSV Upload: The CSV Upload integration now supports transformations on imported columns for better flexibility and data quality. When uploading a CSV, you can now define templates using Lifecycle Management Transformers to combine multiple columns into one, process data formats, case transformations, insert static values, and more.





