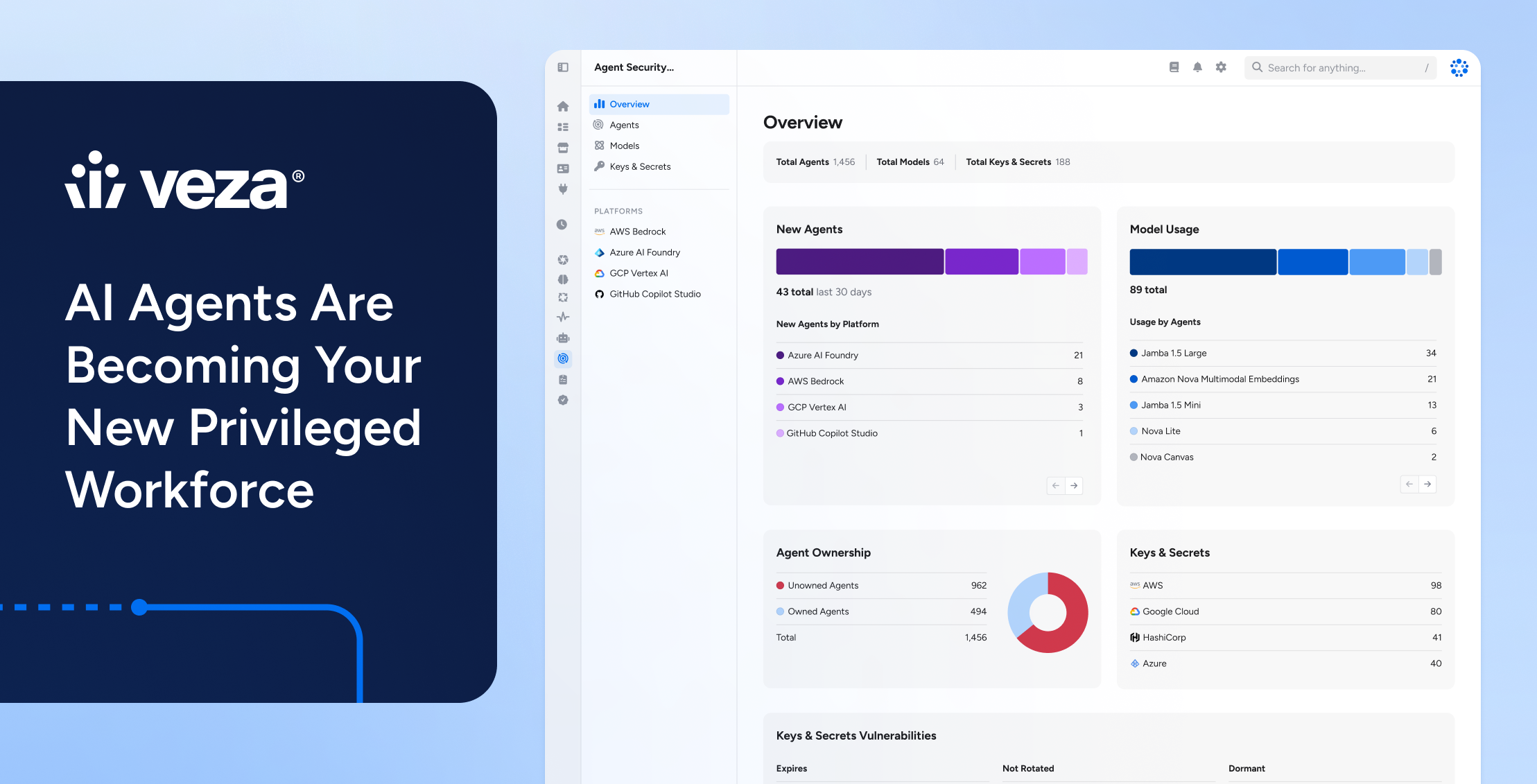
Access Is the New Perimeter—and It’s Fractured
The modern attacker’s mantra isn’t “break in” – it’s “log in.” Advanced groups, such as Volt Typhoon, demonstrate that SharePoint identity governance is now critical, as identities, not endpoints, are now the primary attack surface. By exploiting legitimate credentials, operational complexity, and now AI assistants, they stay hidden in plain sight.
For enterprise security teams, nowhere is this risk more apparent than in Microsoft SharePoint and Teams. These platforms power business collaboration, but their permissions sprawl faster than most teams can track. Files and sites get shared through nested groups, Microsoft 365 entities, and external links. What looks “secure” in an admin console can, in practice, be wide open.
Identity Governance and Administration (IGA) was supposed to prevent exactly this. But legacy IGA solutions—built for static, on-premises applications—weren’t designed for the messy reality of cloud collaboration.
The SharePoint Problem: Visibility Is an Illusion
Ask any security team to map who has access to their most sensitive SharePoint sites. The honest answer? They probably can’t—at least not with confidence.
Legacy IGA tools claim to track access through “users,” “roles,” and “groups.” But in modern Microsoft environments, Legacy IGA tools struggle with SharePoint identity governance, and effective permissions rarely map neatly to these categories:
- Nested group memberships cascade in unexpected ways
- Site inheritance and guest access blur ownership boundaries
- Microsoft 365 Groups introduces yet another layer of complexity
- Shared links bypass traditional control models entirely
The result? Quarterly access reviews become compliance theater. Business owners certify “groups” without understanding what SharePoint documents can actually be viewed, edited, or exfiltrated.
What your business leaders think they’re reviewing ≠ what’s actually accessible.
Case in Point: Volt Typhoon’s Enterprise Lessons
While Volt Typhoon targeted critical infrastructure, their techniques mirror what we see in enterprise breaches daily. As detailed in my previous analysis, they didn’t deploy sophisticated malware—they used valid credentials and native tools to maintain persistence.
Consider how this plays out in enterprise environments: An attacker compromises one account through phishing. Using that foothold, they discover SharePoint sites containing M&A documents, customer data, or intellectual property. Through poorly governed permissions—that external vendor who still has access, those nested groups no one understands—they move laterally without triggering alerts.
The SOC sees normal SharePoint activity. The SIEM shows authorized access. But competitive advantage walks out the door.
If SharePoint access isn’t governed, it’s not just a compliance gap—it’s the next breach waiting to happen.
Where Legacy IGA Falls Short for Modern Enterprises
The gap isn’t in team effort—it’s in tooling built for yesterday’s IT environment. Legacy IGA was designed when:
- Applications lived in data centers
- Active Directory defines the perimeter
- Quarterly reviews met compliance requirements
But businesses don’t operate that way anymore. Legacy IGA simply:
- Cannot resolve who actually has access to specific SharePoint content
- Lacks the business context teams need for intelligent decisions
- Provides yesterday’s snapshot of today’s dynamic environment
- Misses the permission chains that lead to data exfiltration
The AI Amplifier: When Copilot Meets Ungoverned SharePoint
The SharePoint identity governance challenge becomes exponentially more complex with the introduction of AI assistants. Microsoft Copilot for SharePoint exemplifies this new risk dimension—it’s not just another user, it’s a non-human identity (NHI) with the ability to search, interpret, and surface data at unprecedented scale.
Consider what happens when Copilot encounters typical SharePoint environments:
- Those forgotten project folders with embedded passwords? Copilot can find them with a simple query
- The M&A documents over-shared three reorganizations ago? Now searchable through natural language
- Legacy runbooks with API keys that “everyone knows about”? Copilot just made them discoverable to anyone with basic access
Recent security research reveals consistently that attackers can use Copilot to exfiltrate sensitive content without triggering traditional security alerts. The AI assistant operates within existing permissions, making these activities appear legitimate. When asked to “find documents with passwords,” Copilot dutifully complies—no malware required.
This represents a fundamental shift in the threat landscape. Organizations aren’t just dealing with human users anymore—they’re managing AI agents that:
- Inherit permissions from users but operate at machine speed
- Can parallel-process queries across thousands of documents simultaneously
- Often bypass traditional audit trails and monitoring systems
- Come enabled by default in many Microsoft 365 environments
The multiplication effect is real. One over-privileged user account becomes an over-privileged AI assistant with the ability to surface every piece of sensitive data that the account can theoretically access—including content the human user never knew existed.
For organizations already struggling with SharePoint permission sprawl, AI assistants transform a governance challenge into a potential crisis. Legacy IGA tools, already blind to effective permissions in SharePoint, have no concept of these AI agents as distinct identities requiring their own governance.
The Way Forward: Practical Identity Governance for Real-World SharePoint
Solving this isn’t about restricting collaboration—businesses depend on it. It’s about giving security teams the visibility and control they need. Modern identity security platforms address the SharePoint challenge by:
- Showing Real Access: Mapping actual permissions across all those nested groups, shared links, and external users—not just what AD says
- Making Reviews Meaningful: Automating certification with context, business owners understand: “This contractor has access to these 47 confidential files last accessed 6 months ago”
- Enabling Smart Decisions: Providing the confidence to revoke access without breaking critical projects—because the impact is clear
- Maintaining Continuous Visibility: Alerting on permission changes that matter, not drowning teams in noise
- Governing Non-Human Identities: Discovering and managing AI agents like Copilot as distinct identities, tracking what they can access across SharePoint sites, and implementing controls before these powerful NHIs become the next insider threat vector
Every SharePoint Environment Tells a Story
SharePoint sprawl reflects a larger truth about identity debt in organizations. Every merger leaves behind access. Every project creates new shares. Every departure leaves orphaned permissions.
If sophisticated attackers can navigate SharePoint permissions better than internal teams, organizations operate at a disadvantage. Attackers see the accumulated access, the forgotten external shares, the permission paths that tools miss.
The techniques Volt Typhoon used against infrastructure work just as well against enterprises. The difference? When nation-states target infrastructure, it makes headlines. When they target intellectual property, companies might never know.
For enterprise security leaders, the message is clear: Identity governance isn’t a compliance checkbox—it’s operational resilience. And SharePoint might be where that resilience is tested first.
Is SharePoint becoming your blind spot, too?
Legacy IGA didn’t plan for nested permissions, link sprawl, or AI assistants like Copilot. Veza has.
Learn: Download our Comprehensive SharePoint Security Checklist, packed with best practices to mitigate permission sprawl, AI access risks, and compliance blind spots in SharePoint Online.
Explore: Dig into the Solution Brief — Veza for SharePoint Online to see how Veza’s Access Graph visualizes identity-to-data relationships, automates alerts, and enables real-time governance you can’t get from legacy tools.
Engage: Want to see how Veza tracks access across nested groups, guests, and AI agents and surfaces real risks? Request a Demo
This article builds on my previous analysis of Volt Typhoon’s identity-centric attack patterns. For a comprehensive examination of their techniques and defensive strategies, see https://securityboulevard.com/2025/05/an-enterprise-playbook-to-defending-against-volt-typhoon/.