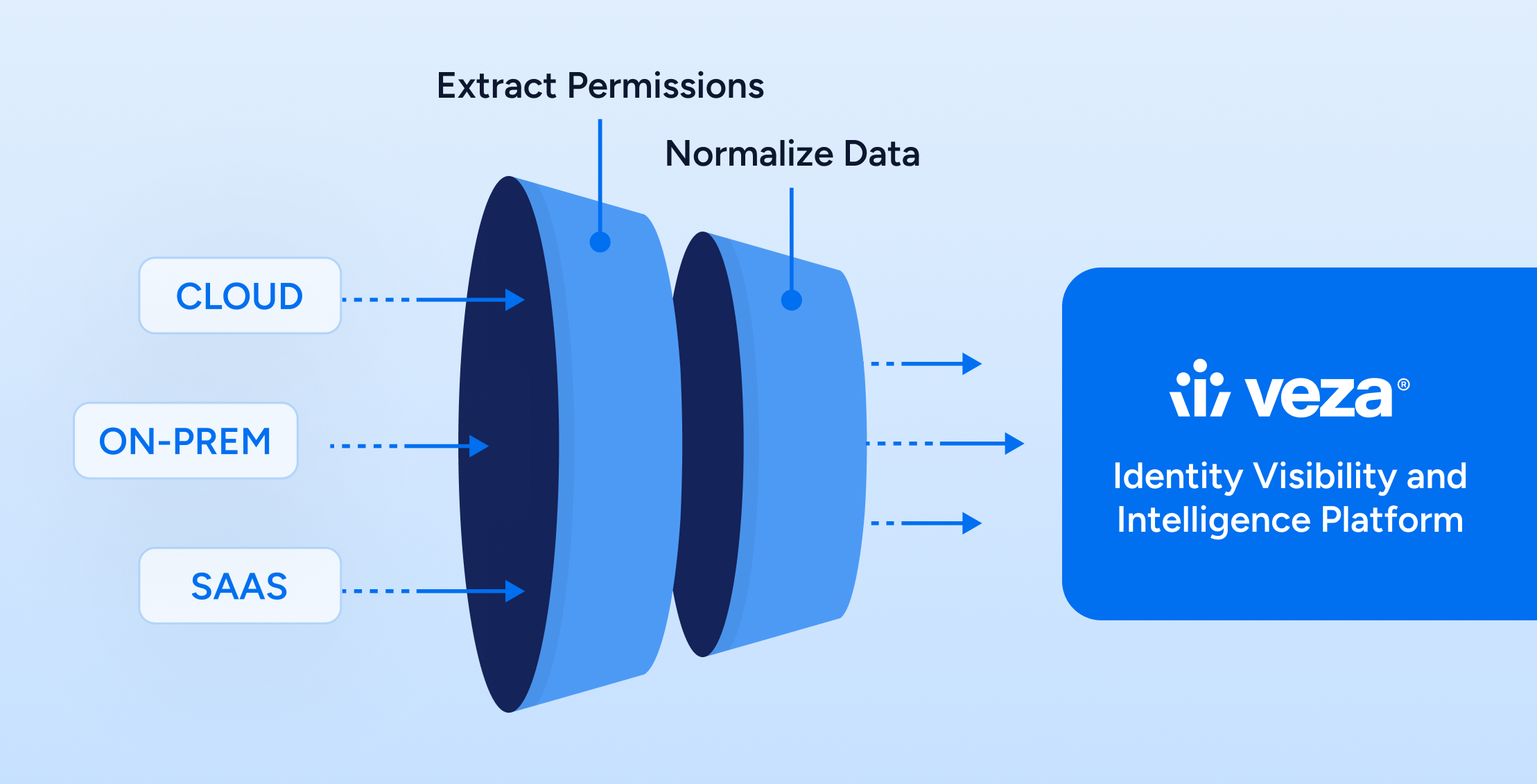
Modern identity security isn’t just about who you are. It’s about what you can do—and whether anyone knows it.
Veza delivers the execution layer for Gartner’s Identity Visibility and Intelligence Platform (IVIP) model. With real-time access intelligence, support for human and nonhuman identities, and visibility that cuts across your SaaS, cloud, and on-prem stack, Veza helps security teams go from identity data overload to access clarity.
Why Legacy IAM Stacks Can’t Deliver an Identity Visibility Platform
Even with IDPs, IGA, CIEM, and PAM tools in place, most organizations still can’t answer basic questions like:
- Who has access to customer data in production?
- Why does that account have privileged permissions?
- Is this service account even in use?
The problem isn’t identity management—it’s identity understanding.
IVIP is the framework Gartner introduced to solve this. And it’s what Veza has been building toward since day one.
Common Challenges an Identity Visibility and Intelligence Platform (IVIP) Solves
Siloed identity and permission data across cloud, SaaS, and legacy systems
Blind spots around machine identities, bots, and APIs
Overlapping tools that manage access, but don’t make it intelligible
Manual, reactive workflows for certifications, audit prep, and risk mitigation
Governance gaps that weaken Zero Trust, AI trust, and least privilege
What Is an Identity Visibility and Intelligence Platform (IVIP)?
IVIP is the intelligence layer missing from most identity security stacks. It doesn’t replace your IAM tools—it connects them, correlates their data, and makes access understandable.
According to Gartner, IVIP platforms help organizations:
- Aggregate identity and access data from multiple sources
- Map effective permissions in real time
- Surface risky combinations and dormant entitlements
- Support access investigations and policy automation
- Integrate with IGA, CIEM, and ITSM workflows
Veza was named a Sample Vendor for IVIP in the Gartner Hype Cycle for Digital Identity, 2025—but we didn’t build for the quadrant. We built for the problem.
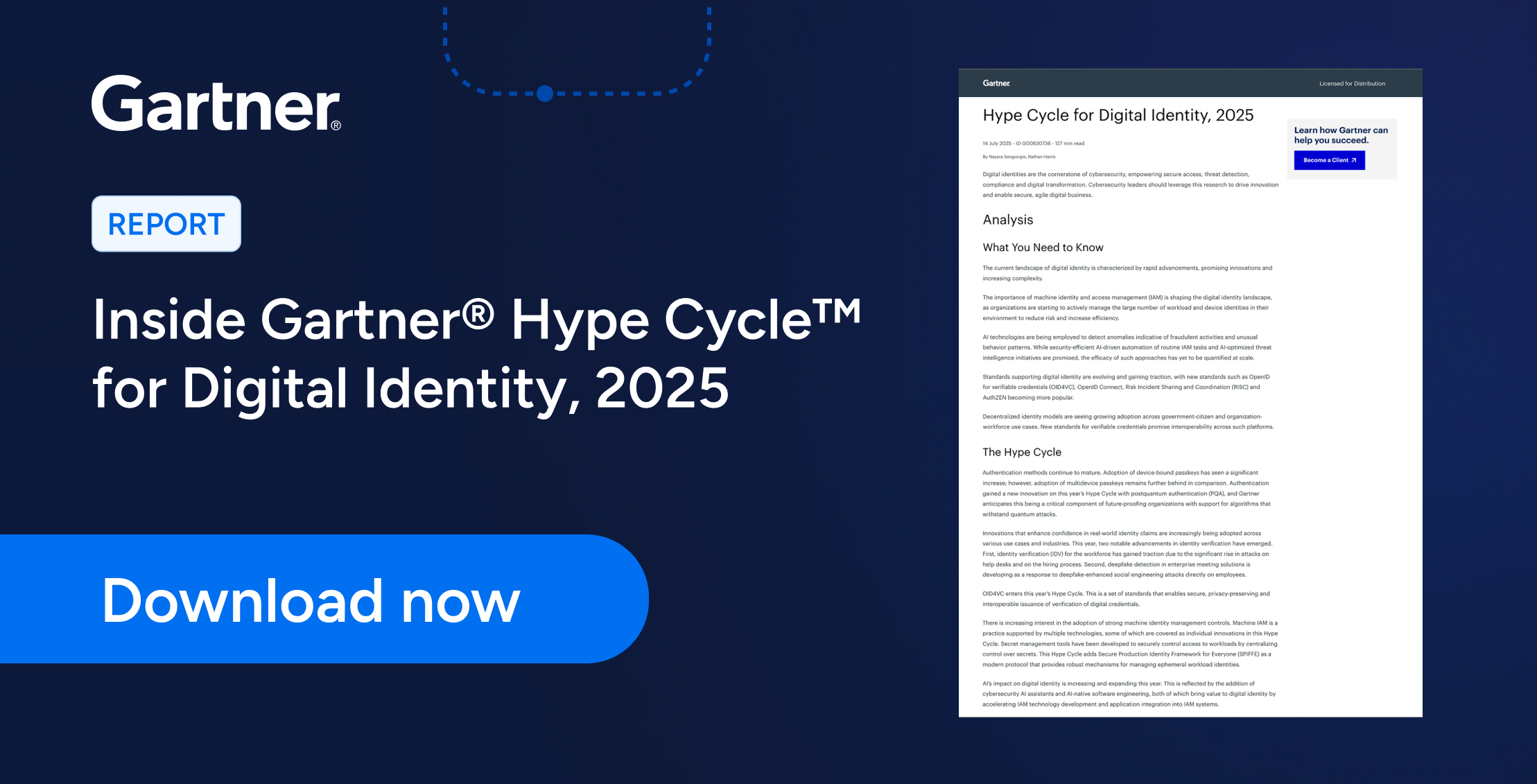
Core Capabilities of an Identity Visibility and Intelligence Platform (IVIP)
A true IVIP brings clarity to the chaos of identity and access sprawl. Veza enables that with:
Unified Access Visibility
Connect identity and permission data across hundreds of systems. Veza normalizes it into a unified, queryable Access Graph.
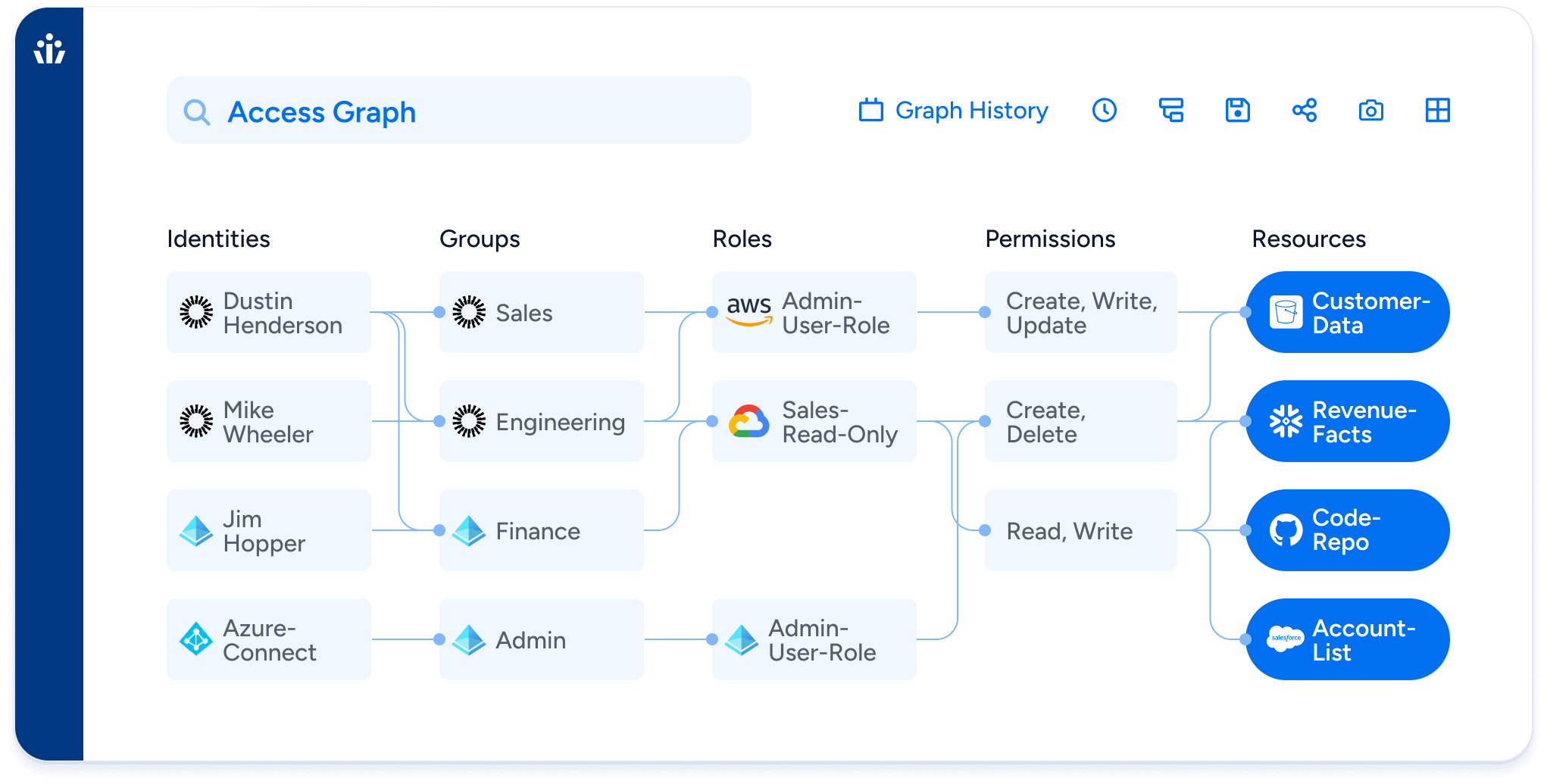
Real-Time Permission Intelligence
See effective access—not just assigned roles—across cloud, SaaS, and on-prem systems. Automatically detect anomalies, overprivilege, and risky access paths.
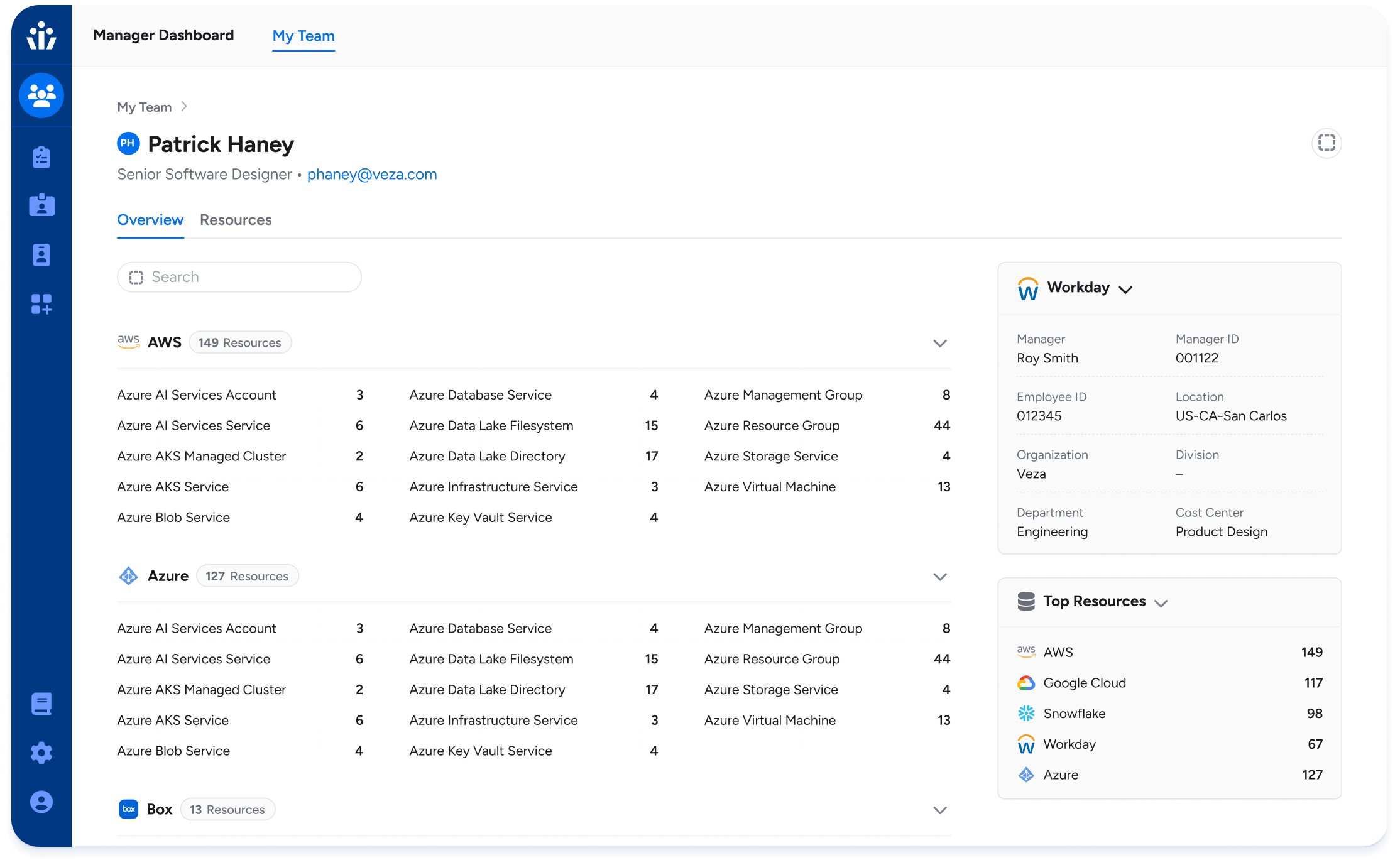
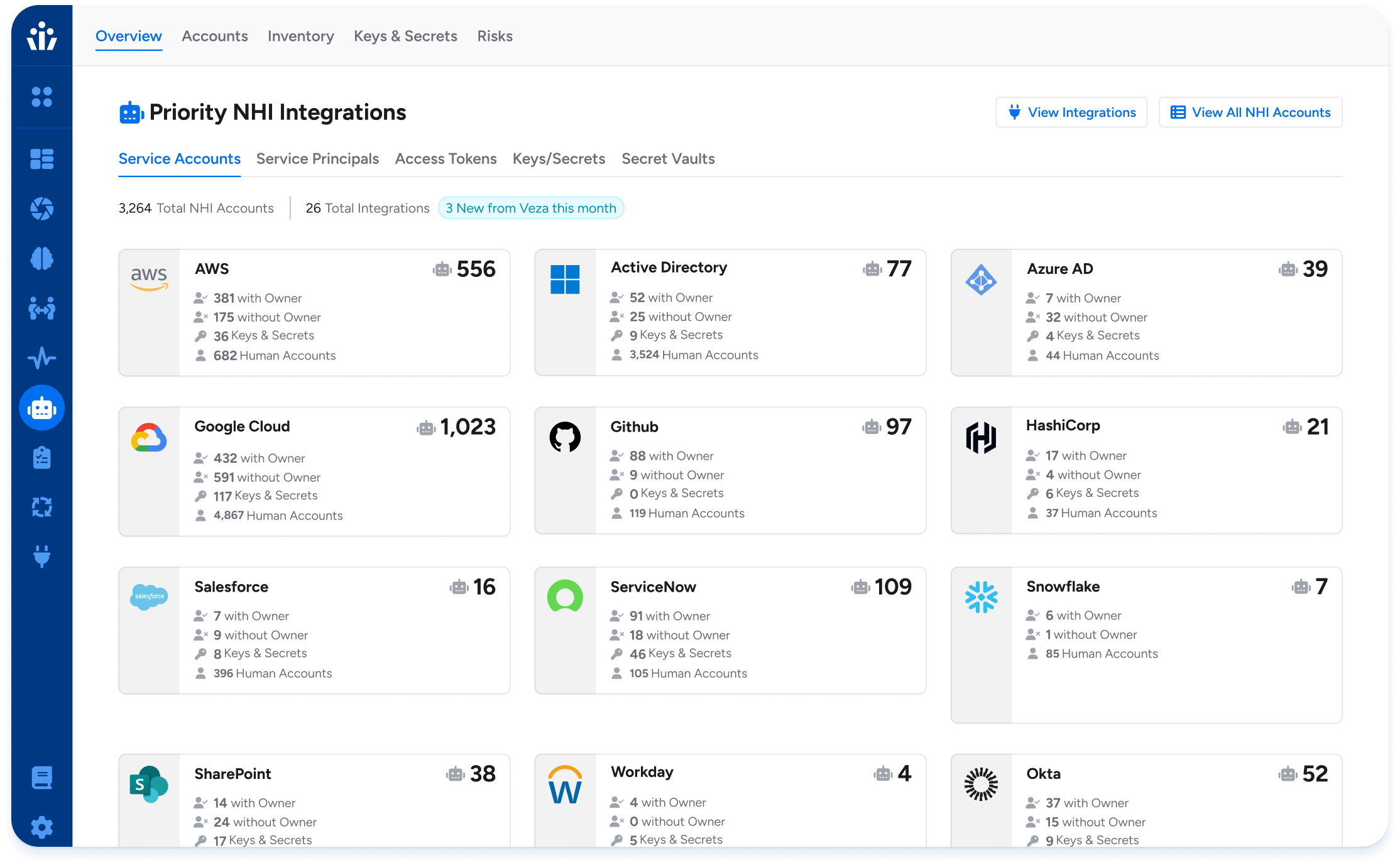
Machine Identity Governance
Discover, monitor, and govern access for service accounts, API keys, and bots. Flag dormant access, escalate based on blast radius, and enforce least privilege.
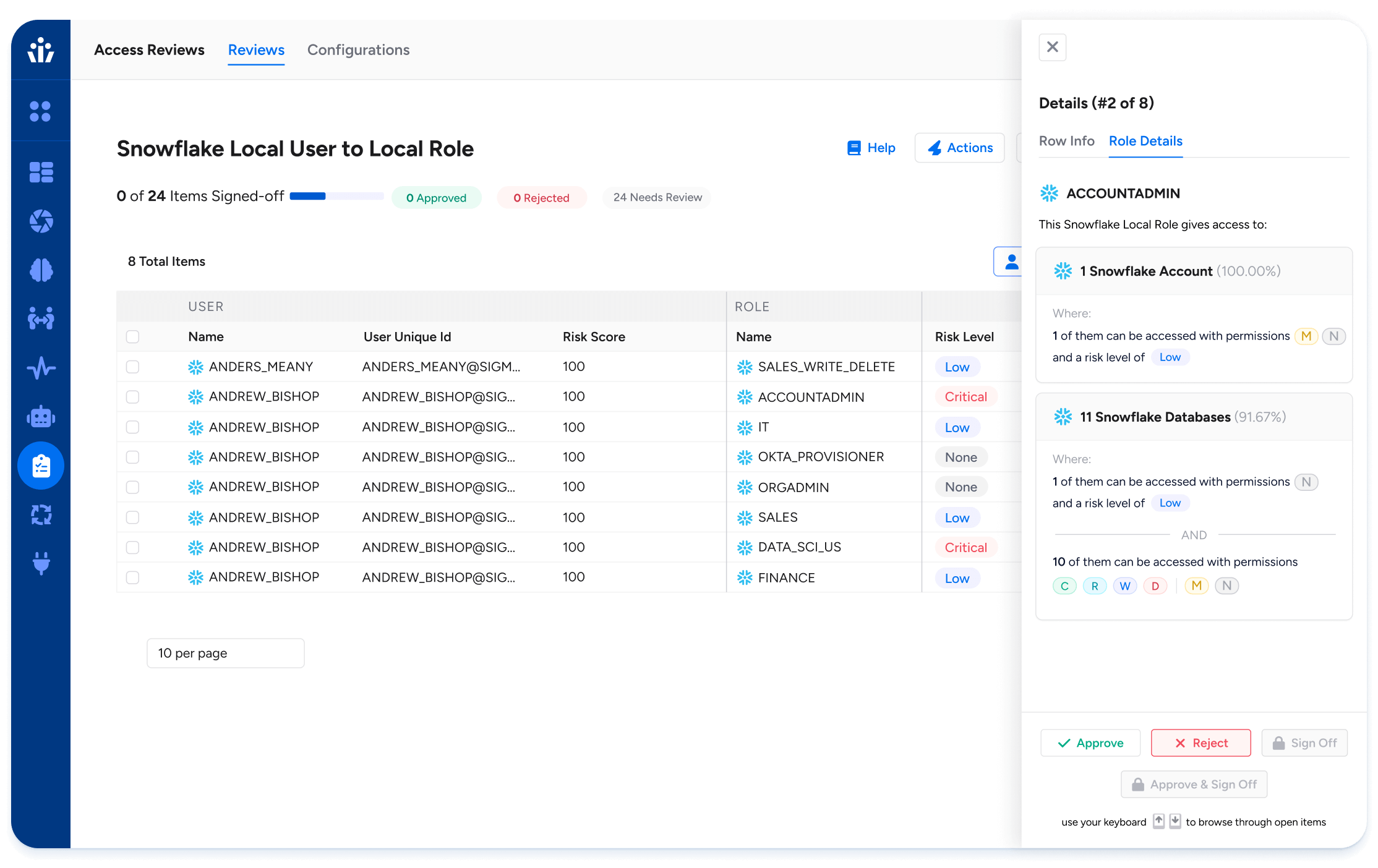
Context-Aware Access Reviews
Transform certification campaigns with access context, peer comparison, and policy logic. No more rubber-stamping.
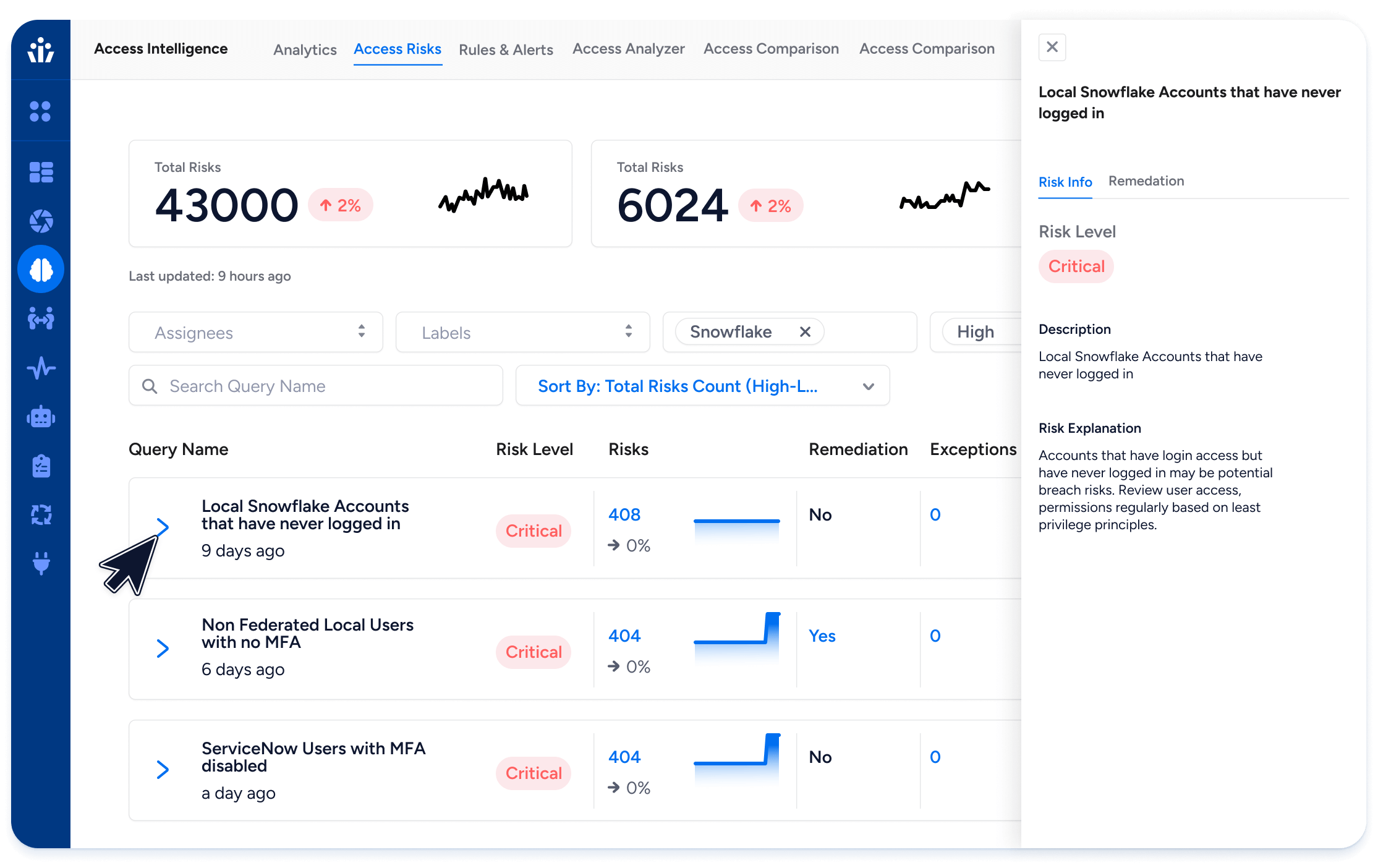
Risk Insights and Enforcement
Detect toxic combinations, stale access, and privilege escalation paths. Integrate with ITSM workflows to trigger revocation or review.
Seamless Integration with IAM
Veza complements your existing stack: Entra ID, Okta, SailPoint, Saviynt, CyberArk, AWS IAM, ServiceNow, and more.
Veza Patents: The Architecture Behind IVIP
IVIP isn’t a bolt-on for Veza. It’s embedded in the platform’s DNA.
Our architecture was patented before the framework had a name. From graph-based privilege modeling to policy simulation, near real-time access visibility, and anomaly detection, Veza’s portfolio includes 13+ patents aligned with the IVIP model.
Key patented innovations include:
- US20220067186A1: Unified access graph. See who can do what across systems in one place.
- US20220286466A1: Entitlement truth. Trust the answer for audits, incidents, and reviews.
- US20250097233A1 (continuation): Effective permissions. Know the exact rights every identity has.
- US20220358233A1: Fresh signals. Keep the access graph current with event-driven push updates from source systems.
- US20240095279A1: High-speed queries. Get those answers fast at enterprise scale.
These aren’t theoretical. They’re foundational to how Veza delivers visibility, intelligence, and control across hybrid and multicloud environments.
Real-World Use Cases
Access Investigations
Trace the blast radius of a compromised account in minutes.Compliance Reporting
Generate audit-ready reports with real-time access context.Role Rationalization
Model access profiles using usage patterns, not guesswork.Machine Identity Oversight
Detect and remediate dormant service accounts and zombie credentials.Access Governance at Scale
Drive certifications and access reviews with context and confidence.
Case Study: Global Bank, Real-World Results
A Fortune 100 bank deployed Veza to analyze machine identities. What surfaced? Over 120 dormant service accounts with direct access to production data—some untouched for more than a year.
With Veza, they moved from blind spots to full remediation in days, not quarters.
Get Started: No Forklift Required
Veza deploys alongside your existing IAM systems. Most customers start with a specific challenge—like failed audits, SaaS overprovisioning, or machine identity sprawl—and expand as they see results.