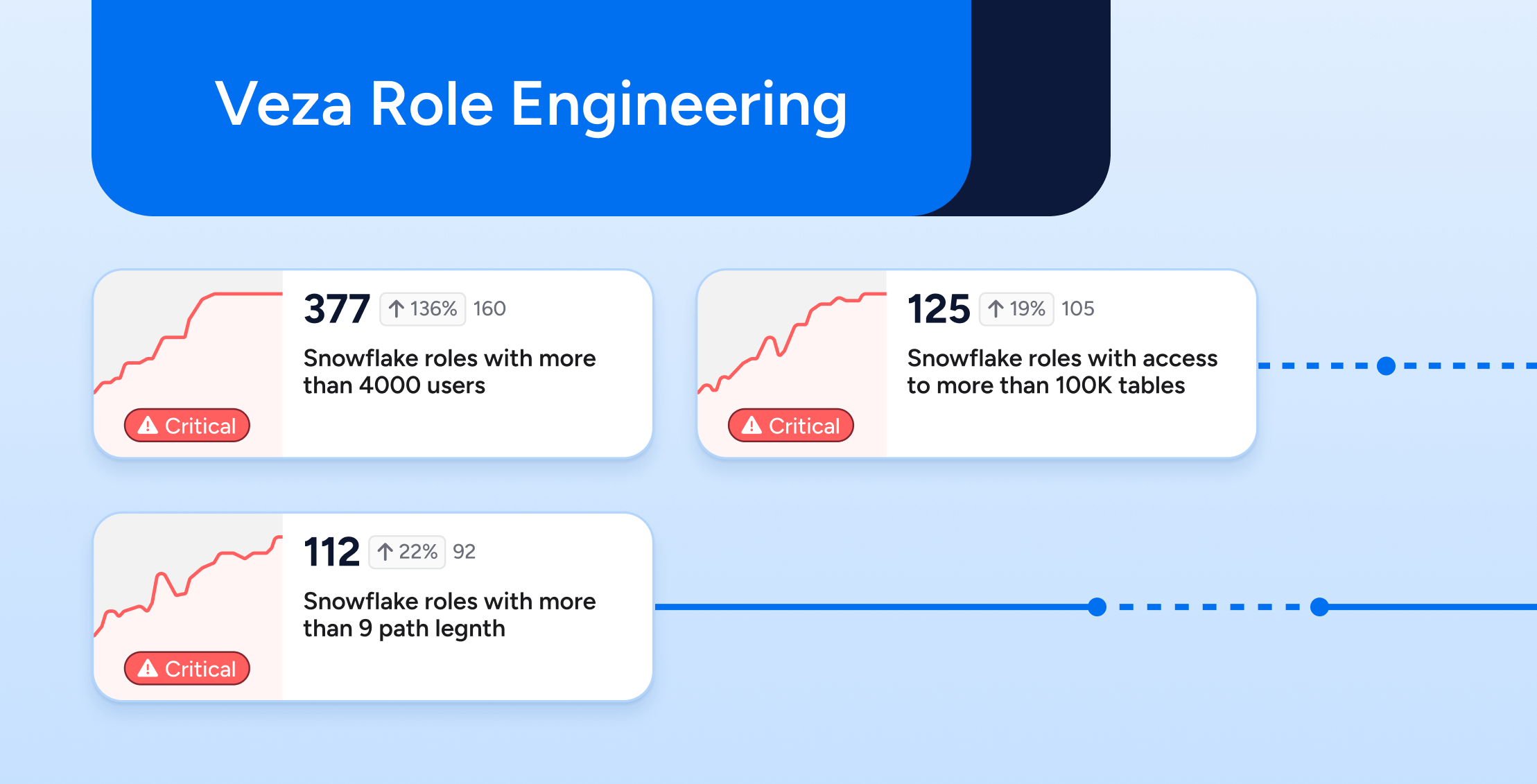
In theory, Role-Based Access Control (RBAC) is elegant. In practice, it’s often anything but.
Over time, even the most disciplined identity programs fall prey to the usual culprits: role creep, stale entitlements, convoluted hierarchies, and a sprawling mess of redundant or overlapping roles. What started as a clean access control framework became a high-risk operational nightmare.
Veza Role Engineering functionality is how security teams take back control, transforming bloated, manual, and brittle RBAC models into streamlined, scalable access controls built for least privilege.
What Is Role Engineering?
Role Engineering is the process of designing, optimizing, and maintaining role structures that align user access with business needs while adhering to the principle of least privilege. It’s a critical part of identity security and access governance, especially as environments grow more complex across SaaS, IaaS, and hybrid infrastructure.
Why Traditional RBAC Fails in the Real World
Let’s call it like it is – static roles age poorly.
Over time, they decay—layer by layer—into brittle frameworks that can’t support today’s access needs.
What starts as a clean, least-privilege model gradually rots into an over-permissioned, unmanageable mess—fueling excessive access, audit headaches, and silent risk.
Common failure patterns in role-based access control:
- Privilege Creep & Over-Provisioned Users
Access is often assigned based on intuition, outdated templates, or copy-paste habits. The result? Privilege creep, excessive entitlements, manual review debt, and increasing risk. - Redundant & Overlapping Roles (Role Explosion)
Similar or identical roles stack up over time, creating complexity, confusion, and compliance gaps. - Stale Roles
Roles tied to legacy projects or outdated org structures remain active, creating complexity and silent vulnerabilities. - Multiple Access Paths
Users gain access – intentionally or unintentionally – through nested role hierarchies. Auditability suffers. So does accountability. - Over-Provisioned Roles
Even well-designed roles eventually bloat with unneeded permissions, violating the principle of least privilege. - Lack of Role Standardization
Inconsistent naming, scope, and purpose lead to downstream errors and security risks.
These symptoms aren’t random, nor are they limited to just a couple of applications—they’re systemic. And they all point to the same root cause: traditional RBAC can’t keep up with the speed and sprawl of modern access. Our Chief Security & Trust Officer, Mike Towers, breaks this down in more detail in a post where he explores why static roles are breaking under dynamic pressure and what a smarter, more adaptive approach looks like.
👉 Read the blog: “Why RBAC Is Not Enough”
Veza Role Engineering: A Modern Approach to Role Governance
Veza doesn’t just help you survive RBAC. We help you engineer smarter roles—with automated insights, data-driven recommendations, and a unified access graph across your cloud, on-prem, and SaaS environments.
Role Analytics: See the Full Picture
Use Veza’s Role Engineering capabilities to get the full story on your RBAC posture—from visualizing role sprawl to cleaning up stale, overprivileged access.
- Role Intelligence: Visualize your current role landscape; redundant roles, deep hierarchies, orphaned entitlements, and spot the inefficiencies dragging you down.
- Role Mining: Analyze usage patterns and permission overlaps across users and roles to identify candidates for cleanup, consolidation, or retirement.
- Role Comparison: Assess two or more roles side-by-side to highlight differences in permissions or attributes and reduce error-prone duplication.
- Redundancy Detection: Surface and eliminate duplicate or overlapping roles before they explode into a governance nightmare.
Role Recommendations: Automate Smart Access Decisions
Don’t guess—use data to guide access decisions.
- Entitlement Recommendations: Assign only what’s necessary—reduce access sprawl.
- Role Matching: Check if a suitable role already exists before creating a new one.
- Role Substitution: Swap overprivileged roles for least-privilege alternatives.
- Assignment: Auto-provision users with access tailored to their role, team, and responsibilities.
Role Definition: Build Smarter Role Structures
Use Veza to define and deploy efficient roles based on actual user entitlements, not outdated templates.
- Dynamic Role Modelling: Define optimized roles based on real-world access patterns—ready for review and deployment.
- Nested Role Flattening: Eliminate deep hierarchies that complicate visibility and increase the risk of overprivilege.
- Role Rationalization: Consolidate and reduce the total role count while improving precision.
The bottom line? Least privilege isn’t a one-time project—it’s a continuous discipline. And role engineering is your foundation. For a deeper dive into how Intelligent Access transforms enterprise access control, check out our eBook, co-authored by Veza CEO Tarun Thakur and renowned security exec Phil Venables.
📘 Download the eBook: A Practitioner’s Guide to Intelligent Access
Role Engineering in Action: Use Cases & Outcomes That Matter
Strategic Gains: Identity Security That Sticks
Veza helps identity teams move beyond role explosion and static templates—toward access governance that’s intelligent, automated, and continuously adaptive.
- Enforce Least Privilege at Scale – Eliminate excessive access by aligning roles to how work actually gets done.
- Boost Audit Readiness – Real-time visibility into entitlements makes compliance simple, even in complex environments.
- Modernize Role Modelling – Replace spreadsheets and legacy modelling tools with automated insights from a unified access graph with permission-level visibility.
- Go Hybrid with Confidence – Manage roles consistently across SaaS, cloud, and on-prem systems.
Operational Efficiency: Fewer Tickets, Faster Decisions
Automated insights and role-aware workflows reduce overhead across security, IT, and application teams.
- Simplify Reviews – Simplify Reviews – Use cohort-based insights to define consistent birthright access, reducing review scope and manual effort.
- Clean Up Role Sprawl – Spot duplicates, compare roles side-by-side, and remove the noise.
- Cut the Service Desk Churn – Streamline access requests and reduce downstream IAM bottlenecks.
- Empower App Owners – Let business teams review and manage access using plain-language roles tied to their applications. No IAM expertise required.
- Grant Access Just-In-Time – Minimize standing privileges by delivering temporary access only when it’s needed.
Real-World Results: How Identity Teams Are Winning with Veza
Customer X: Cleaning Up the RBAC Jungle
- Challenge: Role sprawl with deep, nested hierarchies that bred complexity.
- Impact: 30% of access management spend was tied up in internal tools and manual scripting.
- Solution: Role Mining and Role Analytics drove consolidation and eliminated redundant tooling.
Customer Y: Smart Access from Day One
- Challenge: Access was assigned based on informal rules and assumptions, resulting in excessive privileges and onboarding delays..
- Impact: Elevated risk posture, audit gaps, and increased time-to-productivity for new hires, creating operational friction.
- Solution: Veza’s Role Recommendations and OPAS (Over-Provisioned Access Score) insights identified unused permissions early, enabling faster onboarding and proactive access right-sizing from day one.
Role Mining to Role Engineering: A Smarter Path Forward
Every successful role engineering journey starts with one critical step: visibility. You can’t engineer what you can’t see.
That’s why Veza starts with role mining—analyzing actual access patterns, permission overlaps, and entitlement usage to reveal the true state of access in your environment. From there, teams can confidently rationalize roles, define least-privilege baselines, and automate enforcement.
👉 Want to see how this works in the real world? Read our deep dive on Role Mining and Access Intelligence
How Veza Role Engineering Works
Input:
Direct ingestion from your identity provider or cloud, or a simple CSV mapping users to entitlements when needed.
Output:
- Efficient Role Definitions
- User-to-Role Assignments
- Visual Role Comparisons
- Cohort-Based Access Recommendations
- Role Rationalization Suggestions
All powered by Veza’s Access Graph: a unified permission intelligence layer across systems, apps, identities, and data.
Bonus Capabilities That Set Veza Apart
- Cohort-Based Role Recommendations – Identify common access granted across similar users to inform role design and access decisions.
- Visual Role Diffing: Compare any two roles or groups instantly.
- Role Substitution (Upcoming): Automatically suggest safer alternatives for overprivileged roles, based on your custom definitions.
Fix RBAC. For Real This Time.
RBAC has a reputation problem—but that doesn’t mean we should abandon it. The truth is, RBAC can work—if you engineer it right.
Veza’s Role Engineering brings visibility, automation, and data science to an area long dominated by guesswork and gut feel. No more brittle access control frameworks. No more over-provisioned zombie roles. No more spreadsheets and duct tape..
See Veza in Action
If you’re ready to put role engineering into practice, schedule a demo with our team. We’ll show you how to answer, once and for all: Who can take what action on what data?
🔍 Schedule a Demo






