Elevate Cyber Insurability with Superior Identity Intelligence
Don’t let ransomware and identity-related threats impact your cyber insurability. Use Veza to visualize, manage, and control access everywhere. Easily meet evolving cyber insurance requirements and reduce premiums, while safeguarding sensitive data from breaches.
“Ransomware groups are using credentials obtained via phishing attacks or stolen in cyber-attacks, including those targeting IT suppliers, and sold on the dark net. Using credentials is easier than hacking. Once they get the ‘keys to the kingdom’ hackers can quickly access a system, elevate their access privileges and then move through the system.”
Tackle identity security challenges at scale
How Veza Improves Insurability
The Veza Access Platform connects your organization’s entire identity stack to deliver continuous authorization visibility, context and control, providing verifiable proof of your identity security posture to underwriters and insurance brokers.
Key Benefits
- Reduce identity risk leading to optimized premiums: Map your identity landscape to identify and prioritize the most critical identity risks, like human and non-human identities with overly broad access to critical resources, applications and data. Demonstrate a mature identity security posture leading to optimized cyber insurance terms and premiums.
- Quantify your identity risk posture: Provide underwriters with measurable, real-time data from Veza’s risk engine to prove your identity security strategy is robust and effective, with continuous visibility into access changes across your on-premises and hybrid environments.
- Demonstrate compliance and audit readiness: Realize complete audit trails of Separation of Duties (SoD) violations, history of alerts, reviews and remediations. Prove control over both internal and third-party/supply chain risks with certified vendor access reviews.
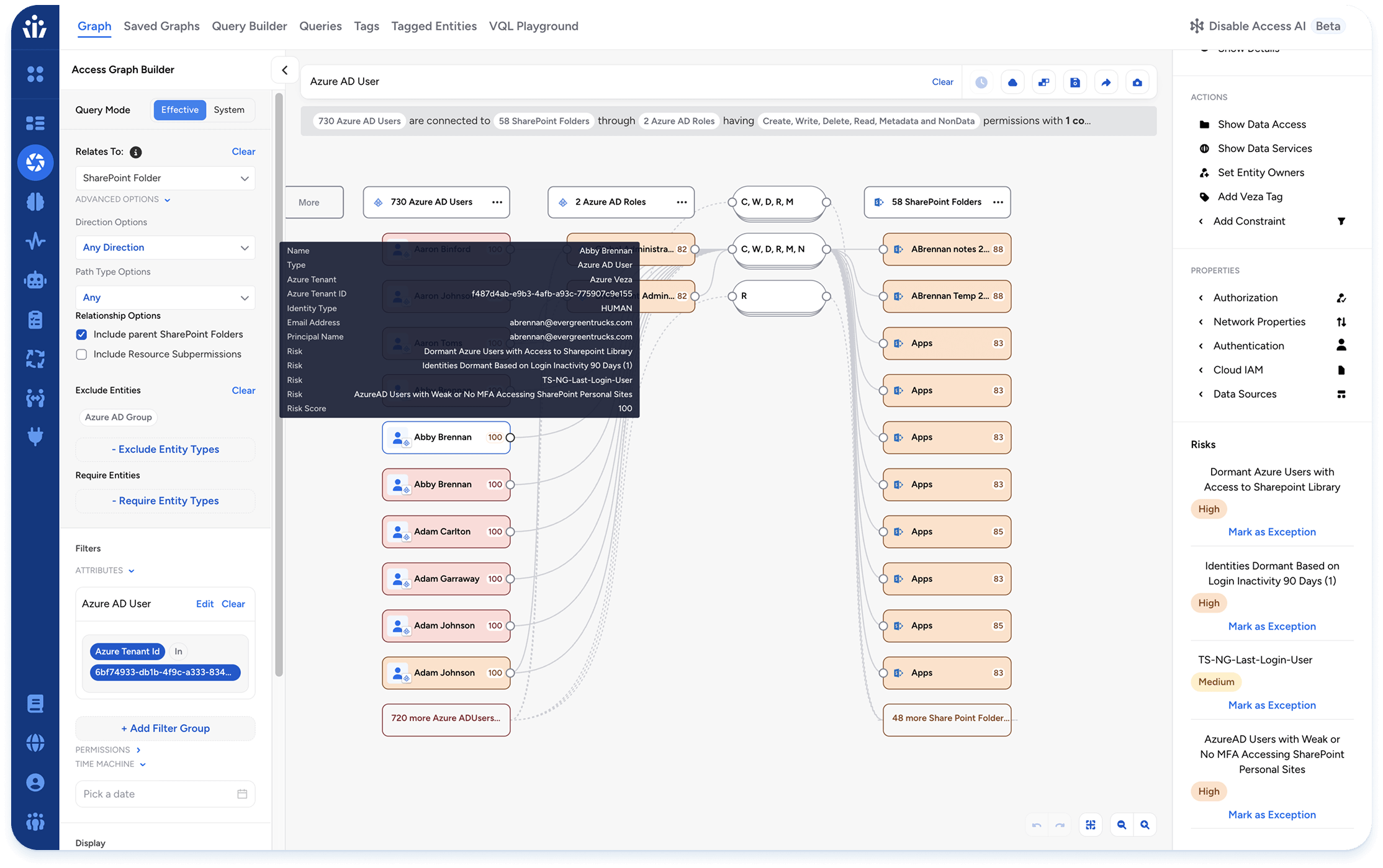
Key Features
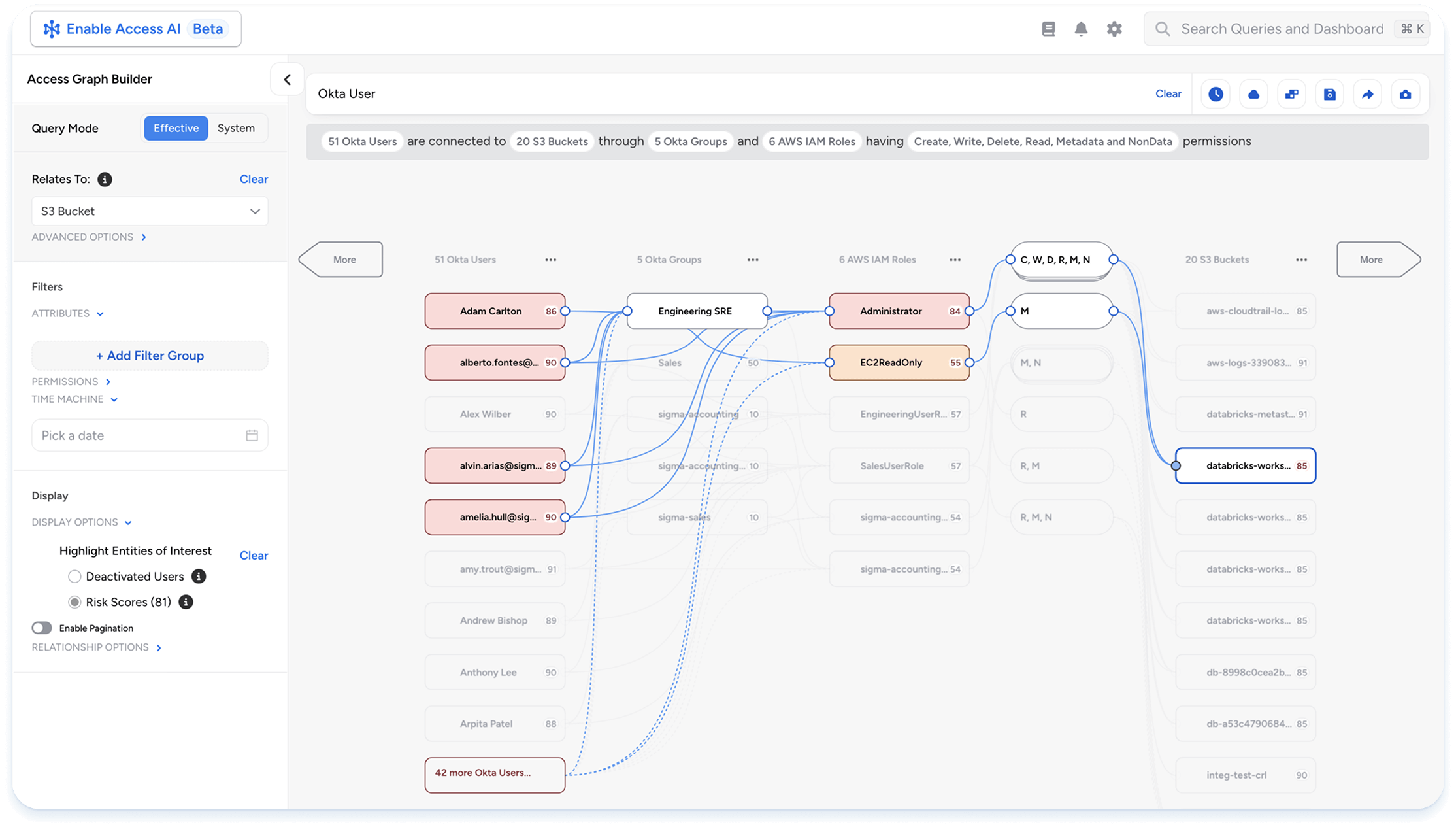
- Access Search: Empower your security teams to easily traverse complex relationships between identities (human and non-human), their permissions, and what they can access. Reveal true effective permissions by translating complex permissions into simple terms – create, read, update, delete – across all identities
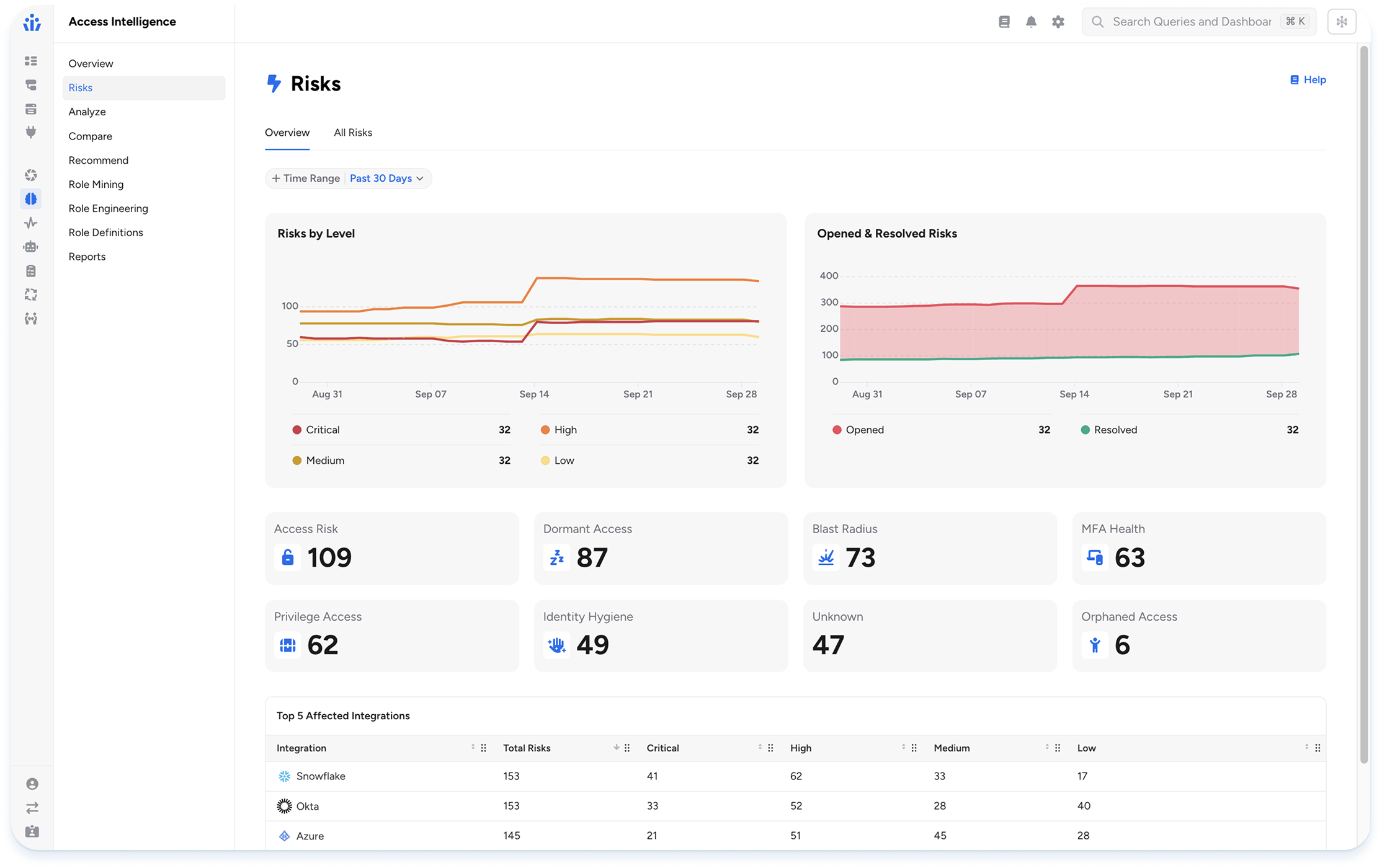
- Access Intelligence: With 500+ pre-built queries, continuously monitor your identities for policy violations and misconfigurations. Automatically trigger remediation workflows through your favorite ITSM tools that surface toxic combinations of permissions that violate SoD policies.
- Access Monitoring: Confidently achieve least privilege for all identities by understanding actual user activity, not just their entitlements. Instantly identify your most over-privileged accounts and groups, remove dormant account accesses, and right-size permissions based on business requirements.
Key Use Cases

Prove control over privileged access
Go beyond basic PAM to satisfy underwriters with data-driven proof of least privilege, with a complete inventory of every privileged identity and auditable reports to justify a lower-risk profile.
Eliminate non-human identity risk
Close a critical blind spot for insurers by governing all service accounts, API keys, and identities powering AI agents, and prove that you are managing the chaotic, high-risk world of machine identities.

Secure your supply chain and vendor access
Satisfy a key insurer concern by demonstrating robust governance over third-party risk with a complete audit trail of vendor accesses, showcasing proactive management of supply chain threats.

Prevent insider threats and data misuse
Prove you have strong internal controls by automatically detecting toxic, cross-application SoD violations, with an auditable history of alerts and remediation actions, and stop breaches before they result in a claim.
Learn More
-

How to Secure Non-Human Identities: Best Practices to Manage Bots, Tokens, and API Keys
Learn more -

Veza + ServiceNow: The Enterprise Agent Identity Control Plane
Learn more -

Veza – The Enterprise Agent Identity Control Plane
Learn moreVeza’s 2026 State of Identity and Access Report found that in a typical enterprise, an average worker holds 96,000 entitlements, 38% of IdP accounts are dormant and only 55% of permissions are safe and compliant. The volume and complexity of identity-based attacks is exacerbated by the explosion of AI agents and non-human identities (NHIs). In […]

