Data System Access
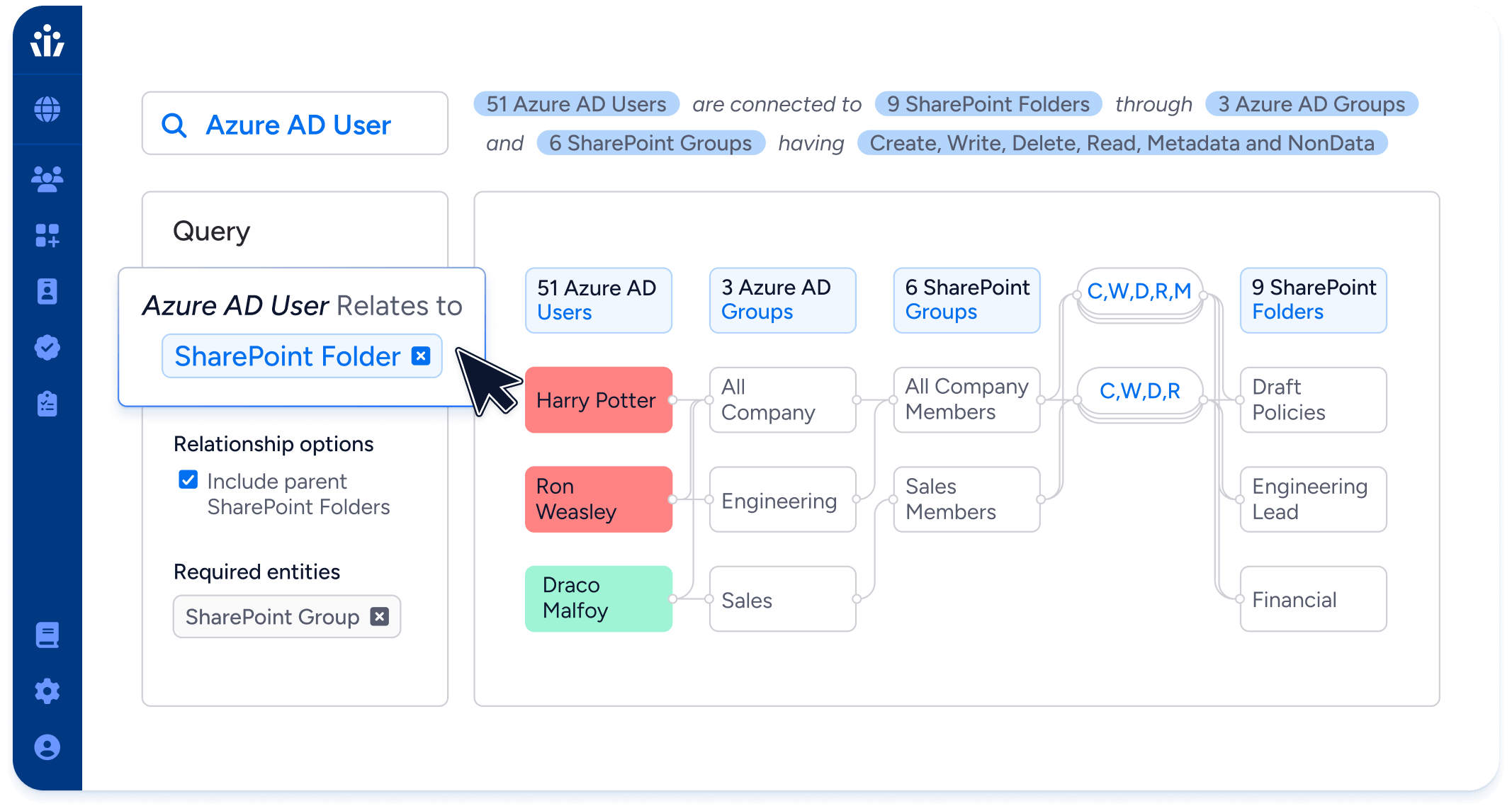
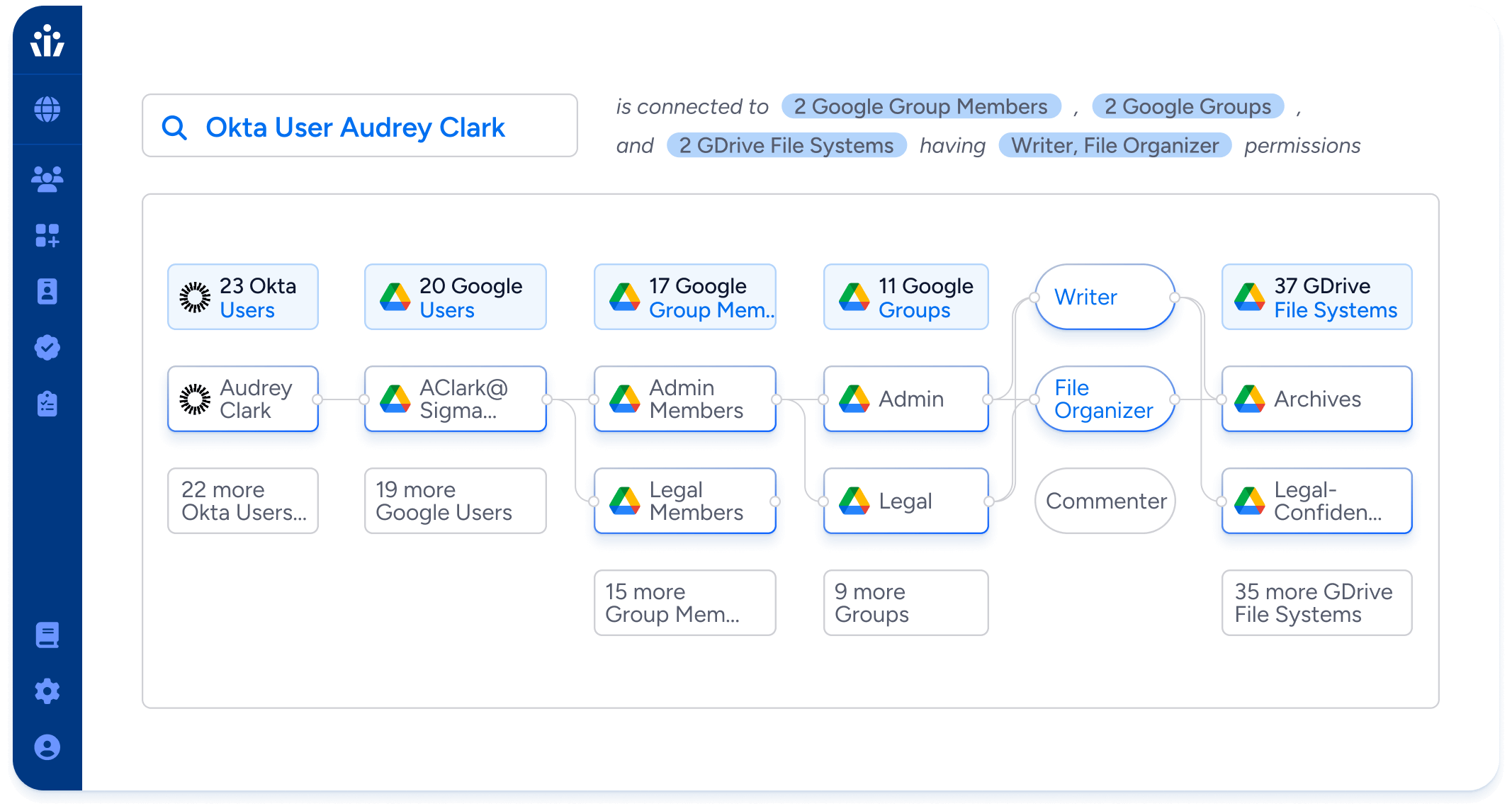
Your most sensitive data may not be neatly stored away in a SQL table, but spread across unstructured data stores beyond the reach of traditional IGA tools. With Veza, you can understand and control access to unstructured data in your data lakes, ML datasets, shared drives, and cloud storage.
Intelligent access for unstructured data
For all your identity security teams
Governance, Risk & Compliance (GRC)
Automatically compile and assign access reviews and certifications for sensitive data in cloud storage buckets or shared drives.
Track sensitive access by guest users, external contractors and third parties
Assign the least permissive role possible for ad hoc access requests to any resources.
Security and Risk Management (SRM)
Enforce detailed policies for restricting access to different types of unstructured data.
Identify and fix privilege drift and identities with overly broad access to fileshares.
Monitor for shared drive misconfigurations, such as drives that are accessible to the internet.
Learn More
-

Veza – The Enterprise Agent Identity Control Plane
Learn moreVeza’s 2026 State of Identity and Access Report found that in a typical enterprise, an average worker holds 96,000 entitlements, 38% of IdP accounts are dormant and only 55% of permissions are safe and compliant. The volume and complexity of identity-based attacks is exacerbated by the explosion of AI agents and non-human identities (NHIs). In […] -

Taming the M&A Chaos: How Veza Addresses Identity Security Risks During Mergers, Acquisitions, and Divestitures
Learn more







