Least privilege is not a quarterly project. It is an operating model. Identities change, systems change, and rules change. The only stable path is one built on visibility and control that can keep pace with that change. That is the purpose of Intelligent Access. Start with a true picture of who can do what on what data. Standardize the meaning of those permissions so people can reason about them. Then automate decisions so policy is enforced in the flow of work, not after the fact.
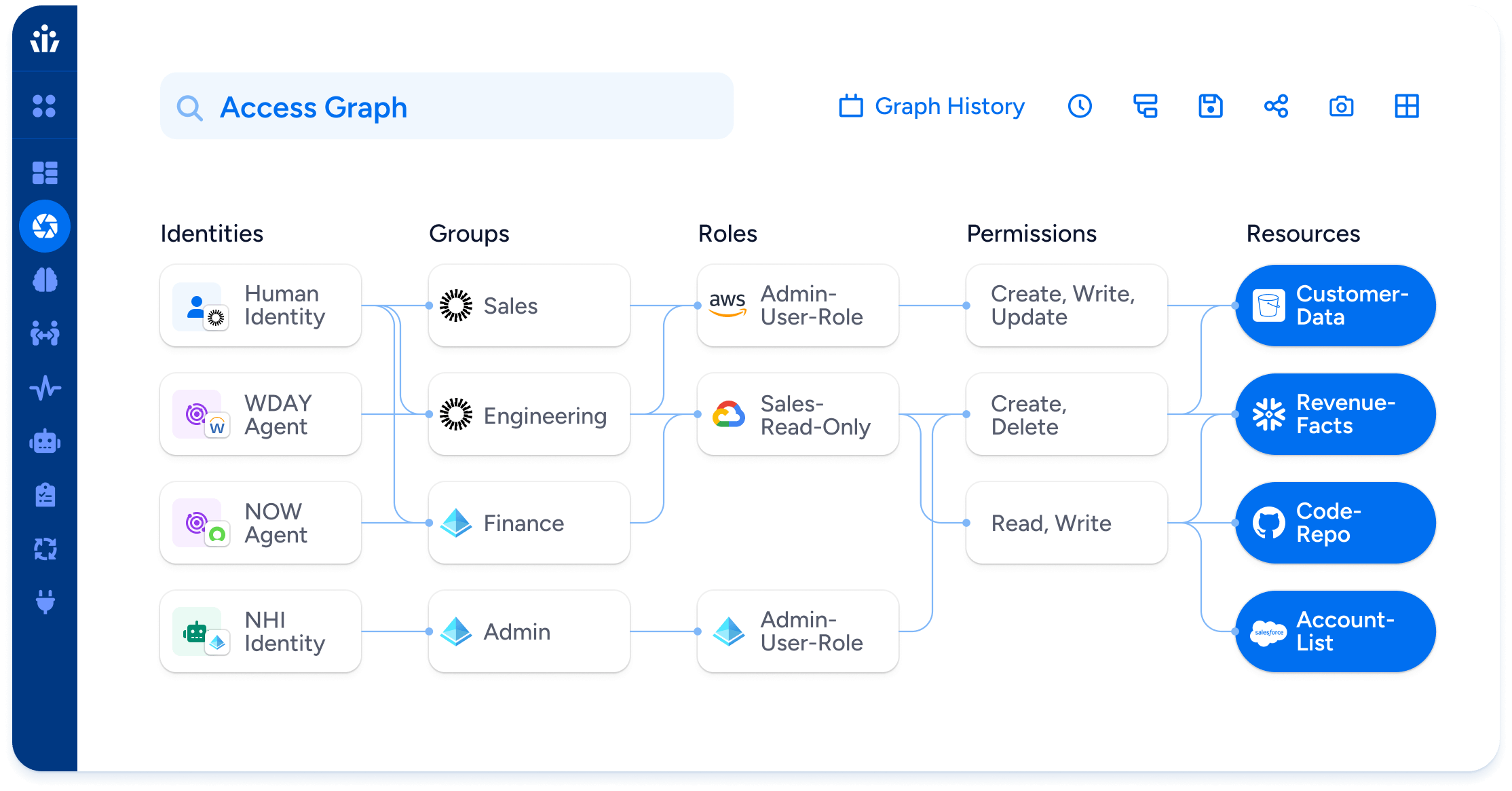
We built the Access Graph to make that possible. It unifies identities, permissions, and resources across cloud, SaaS, data, and on-prem systems into one model you can search, trust, and act on. When you ask a hard question, you get an answer with evidence, not a guess. When the environment shifts, the model stays fresh, so decisions reflect reality.
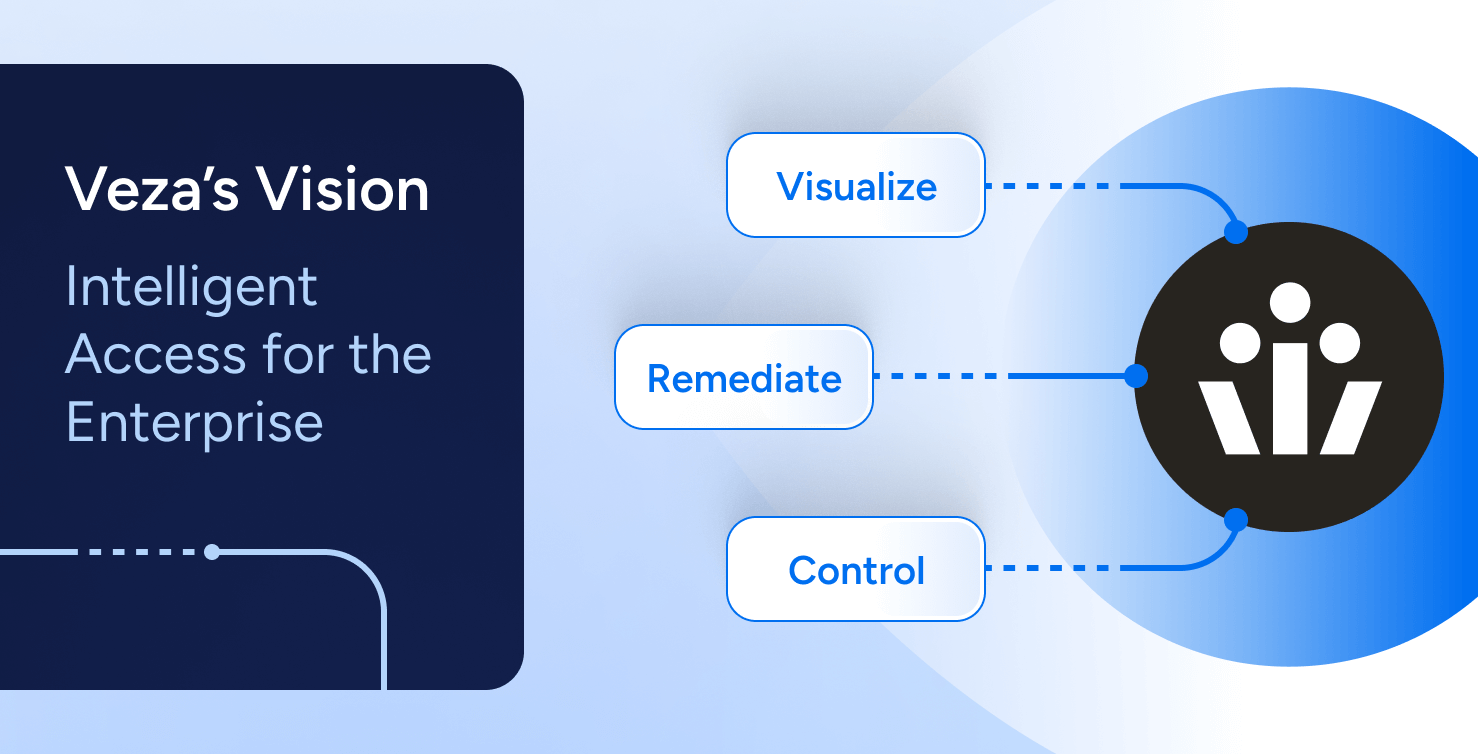
This vision moves in three acts that reinforce one another.
Act I: Visualize
Tell the truth about access. Put people and machines on the same map. Treat workforce accounts, service accounts, tokens, workloads, pipelines, and AI agents as first-class identities. Pull their names, roles, policies, and resources into one coherent picture, resolve duplicates, and keep it current as source systems change. When you ask who can delete data in a bucket or who can read a warehouse table, you follow the path that grants the permission, and you see the blast radius if that identity is compromised.
Act II: Remediate
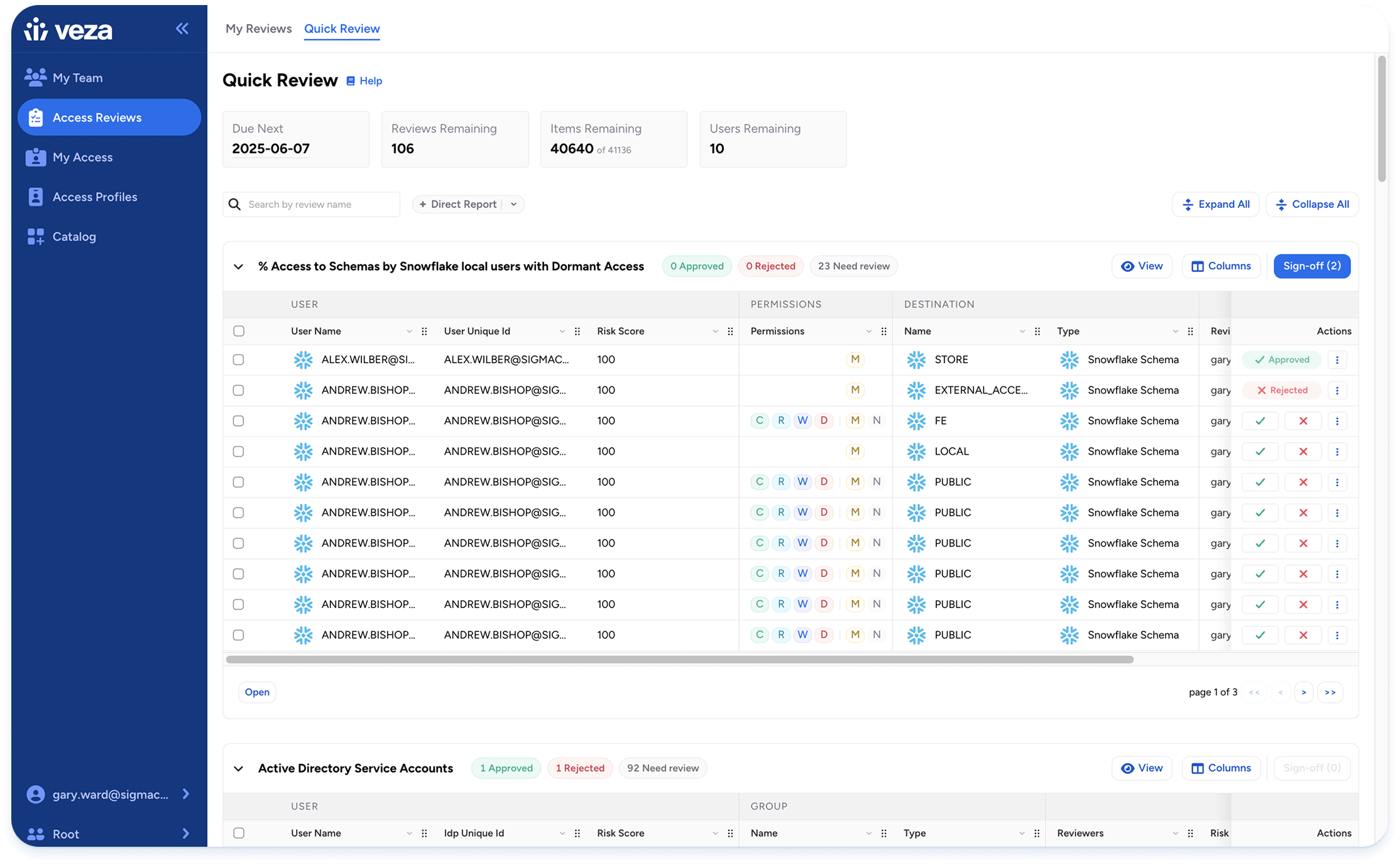
Turn visibility into change that lasts. Compute what access really allows by evaluating identity policies, resource policies, denies, and inheritance, then express the outcome in plain create, read, update, and delete. Compare intent with reality. Remove dormant entitlements. Right-sized roles that carry more history than purpose. Validate that revocations landed. Make remediation a rhythm, not a campaign.
Act III – Control
Make least privilege durable in the flow of work. Requests follow policy. Approvals carry context. Temporary access ends on time. Ownership is assigned and enforced for human and non-human identities. Lifecycle changes run as rules, not reminders. When something looks risky, the system explains why, recommends the smallest safe choice, and lets teams move without opening new doors.
That is Intelligent Access. Not a feature list. An architecture that turns visibility into action and keeps the loop closed as your enterprise evolves.
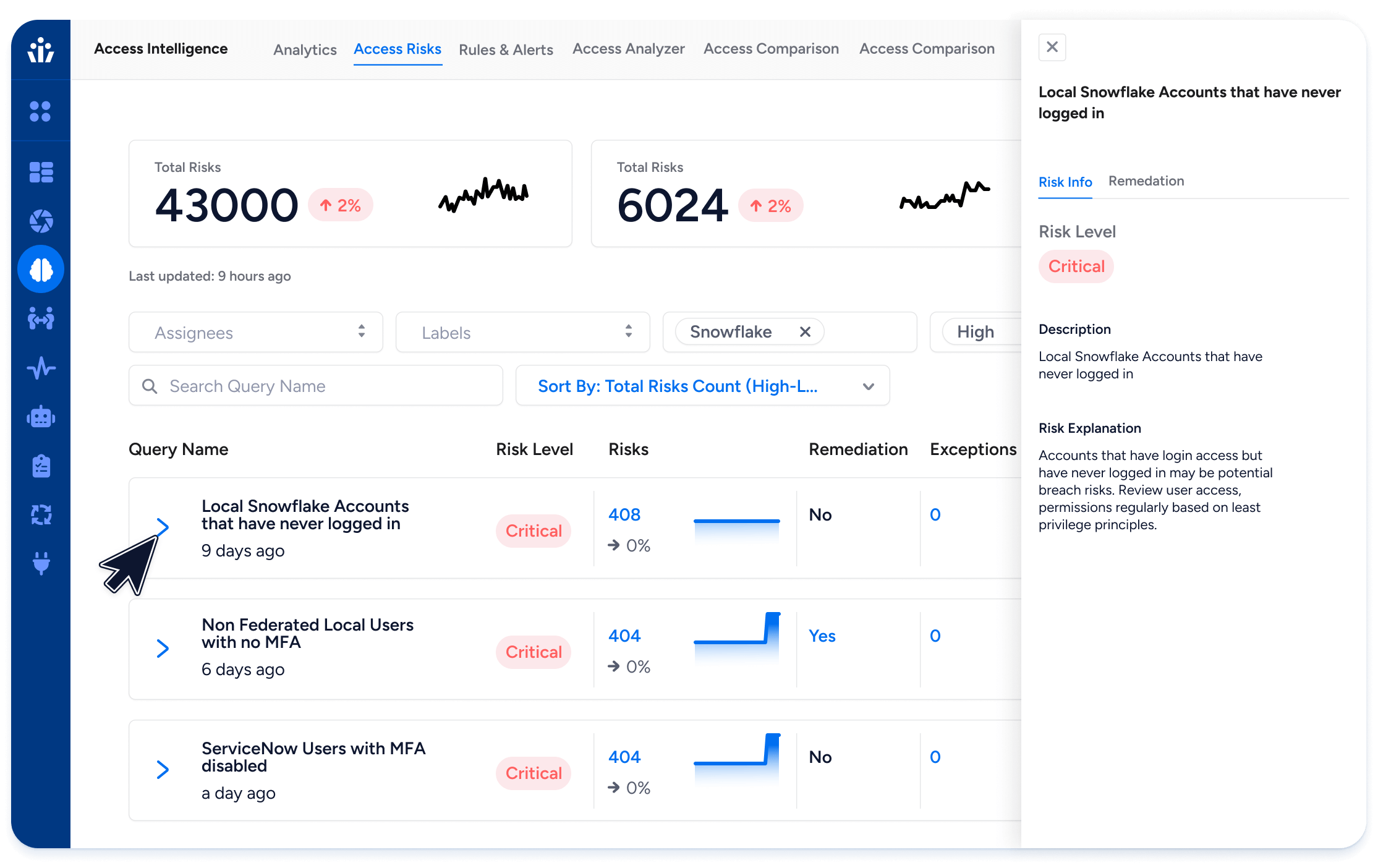
Postlude: From vision to practice
The three acts give you the pattern. You now have a map you can trust, a language you can share, and a motion you can sustain. The rest is focus. Start where risk is largest, prove it with evidence, and let policy take over the repetitive work.
We have built a comprehensive access mapping system, proven in real customer environments at enterprise scale. The model is not theoretical. It has been tested against hybrid estates, millions of permissions, and the full mix of human and non-human identities. Our goal is simple and repeatable. Enable every customer to define and control access across the enterprise, and to trust that definition because it is consistent, explainable, and enforced.
This is the foundation of Veza’s vision. Make least privilege not just a principle, but an operational reality. The Access Graph provides the truth about who can access what data. Standardization gives that truth meaning. Automation keeps it in motion as the environment changes. With these pieces in place, Intelligent Access moves from aspiration to practice.
What follows is the natural next step. Bring the architecture to your environment. Start with visibility, remove excess, and let policy drive the daily workflow. In the conclusion, we will distill how to begin and how to measure progress so that least privilege endures.
Conclusion
This paper has covered a wide field because the field itself has widened. Identities are no longer confined to a directory or a single cloud tenant. They live across SaaS, data platforms, multiple clouds, custom applications, and the automations that tie them together. The consequence is clear. Excess privilege accumulates wherever visibility is fragmented and control is manual. The answer is also clear. Least privilege needs a model that can keep pace with change. That is what we mean by Intelligent Access.
The throughline is consistent. Begin with a true picture of who can do what on what data. Give that picture a shared language so teams can reason about it without translation. Then place policy where work actually happens so decisions are enforced as part of the flow, not as an afterthought. The five pillars set the frame for that progression. All systems. All identities. True permissions. Standardization. Automation. Each pillar matters on its own, and together they make least privilege sustainable.
Architecture turns those pillars into practice. The Access Graph unifies identities, permissions, and resources across cloud, SaaS, data, and on-prem into a coherent model. It resolves duplicates, traces inheritance, and keeps state fresh as source systems change. It computes effective permissions in plain terms like create, read, update, and delete, so risk is explained, not implied. With that foundation, visibility becomes something people can trust, and trust becomes the basis for action.
Products carry the architecture into daily work. Search answers hard questions in plain language and returns evidence, not guesswork. Intelligence scores risk, explains why it matters, and validates that remediation lands. Monitoring shows what access is actually used, so roles can be right-sized and dormant rights can be removed. Reviews become focused and auditable, with verification that rejected entitlements truly disappear. Lifecycle and Requests make policy tangible by granting, adjusting, and revoking access on time for both human and non-human identities. NHI Security closes a gap that has grown faster than most teams could track. Access AI brings context to every step so people can move faster with a smaller blast radius.
Use cases show the outcomes. Privileged access becomes governable instead of brittle. Non-human identities gain owners, hygiene, and scope. Data systems and SaaS estates are no longer blind spots. Role engineering sheds history and keeps intent. Posture is measured and improved in a continuous loop. AI agents join the model as first-class identities with the same boundaries and accountability as people. None of this is a side project. It is the operating model that holds as the enterprise evolves.
The vision endures because it moves in a rhythm you can sustain. Visualize the truth of access. Remediate with evidence. Control in the flow of work. That rhythm does not require a wholesale reset. It invites a practical start. Pick one high-value system. Use the Access Graph to see what access really allows. Remove what no one uses. Let policy carry the repetitive work. Extend the same pattern to the next system and the next set of identities. Measure progress in smaller blast radius, faster reviews, and fewer exceptions.
What to do next:
You do not need permission to begin. You need a first step and a path that holds. If you want to explore how Intelligent Access lands in your environment: