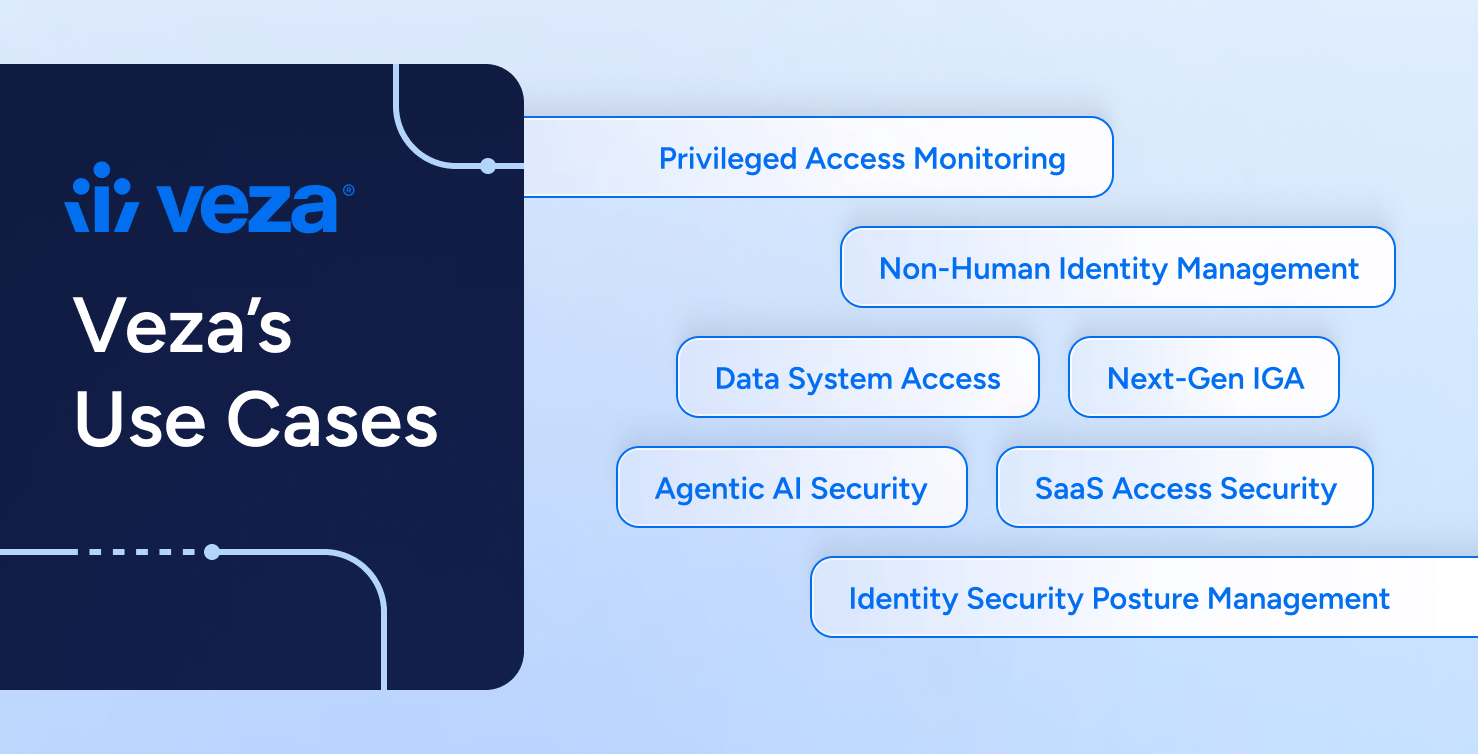
Veza is built for the messy reality of enterprise identity. Thousands of systems, millions of permissions, cloud and SaaS exploding, non-human identities multiplying faster than humans, and AI embedding itself everywhere. These are the scenarios where Intelligent Access proves itself – where principles turn into practice, and risk becomes governable.
Privileged Access Monitoring
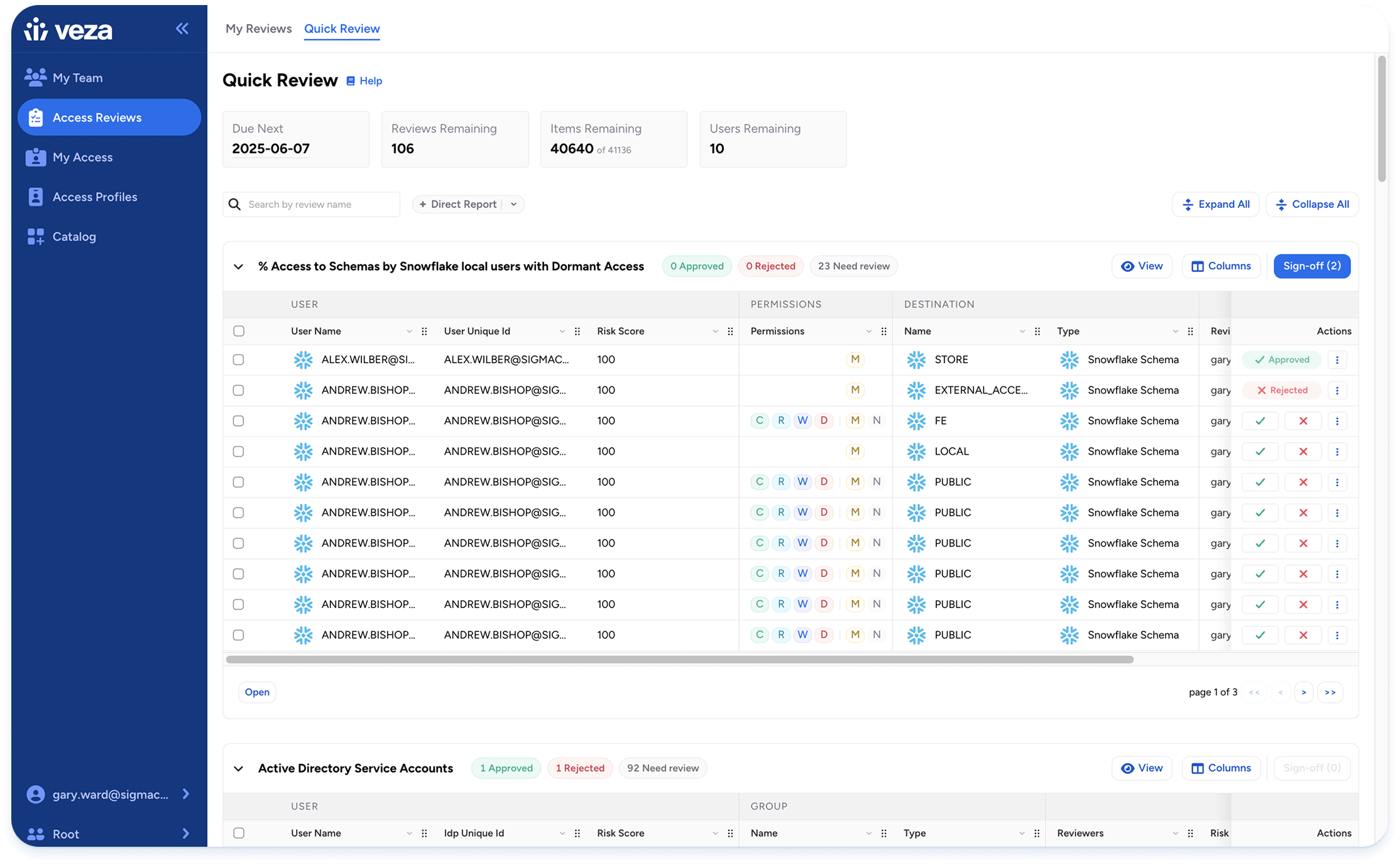
Privileged users remain the crown jewels for attackers. Yet most organizations still cannot answer clearly: who are my admins, and what can they really do? Guest accounts promoted to admin, forgotten local users in SaaS tenants, contractors left with standing rights, and over-permitted cloud IAM roles are all well-worn breach stories.
Legacy PAM and IGA tools show fragments, not the full picture. Veza unifies privileged access across SaaS, cloud, data, and on-prem into one graph. It reveals the blast radius for each identity, including federated identities assuming AWS, GCP, and Azure IAM roles, traces how permissions were inherited, and flags dormant or misconfigured accounts before they become incidents. Where PAM governs how elevated credentials are issued and used, Privileged Access Monitoring shows the effective permissions those identities actually hold, so you can see and shrink risk in real time. If you are modernizing beyond vaults and break-glass accounts, start with Veza for PAM to pair continuous entitlement truth with your PAM stack.
The result is confidence. Compliance teams meet SOX and SOC 2 audits with evidence, not scrambling. Security teams enforce least privilege in practice, cutting down the blast radius of inevitable compromise.
Non-Human Identity Management
Non-human identities now outnumber humans by orders of magnitude. Service accounts, pipelines, tokens, and AI agents hold real privilege, often without ownership, expiration, or lifecycle. That is how secrets get embedded in repos, workloads impersonate roles across cloud accounts, and pipelines become invisible attack paths.
Veza pulls machines into the same Access Graph as people. It discovers service accounts across SaaS and cloud, enforces hygiene with credential rotation and vaulting, and maps impersonation rights that bypass traditional guardrails. Pipelines and workloads assuming roles across cloud environments are tracked and monitored with the same rigor as human admins. With features like Enrichment Rules and auto-assignment of owners, NHIs can be reviewed, governed, and time-boxed with the same rigor as workforce identities.
The impact is parity. Machines no longer accumulate unchecked privilege. They are discovered, owned, rotated, and reviewed, making the fastest-growing segment of the identity attack surface visible and auditable. See the Veza resource on NHI Management for more on what constitutes best practice in managing non-human identities.
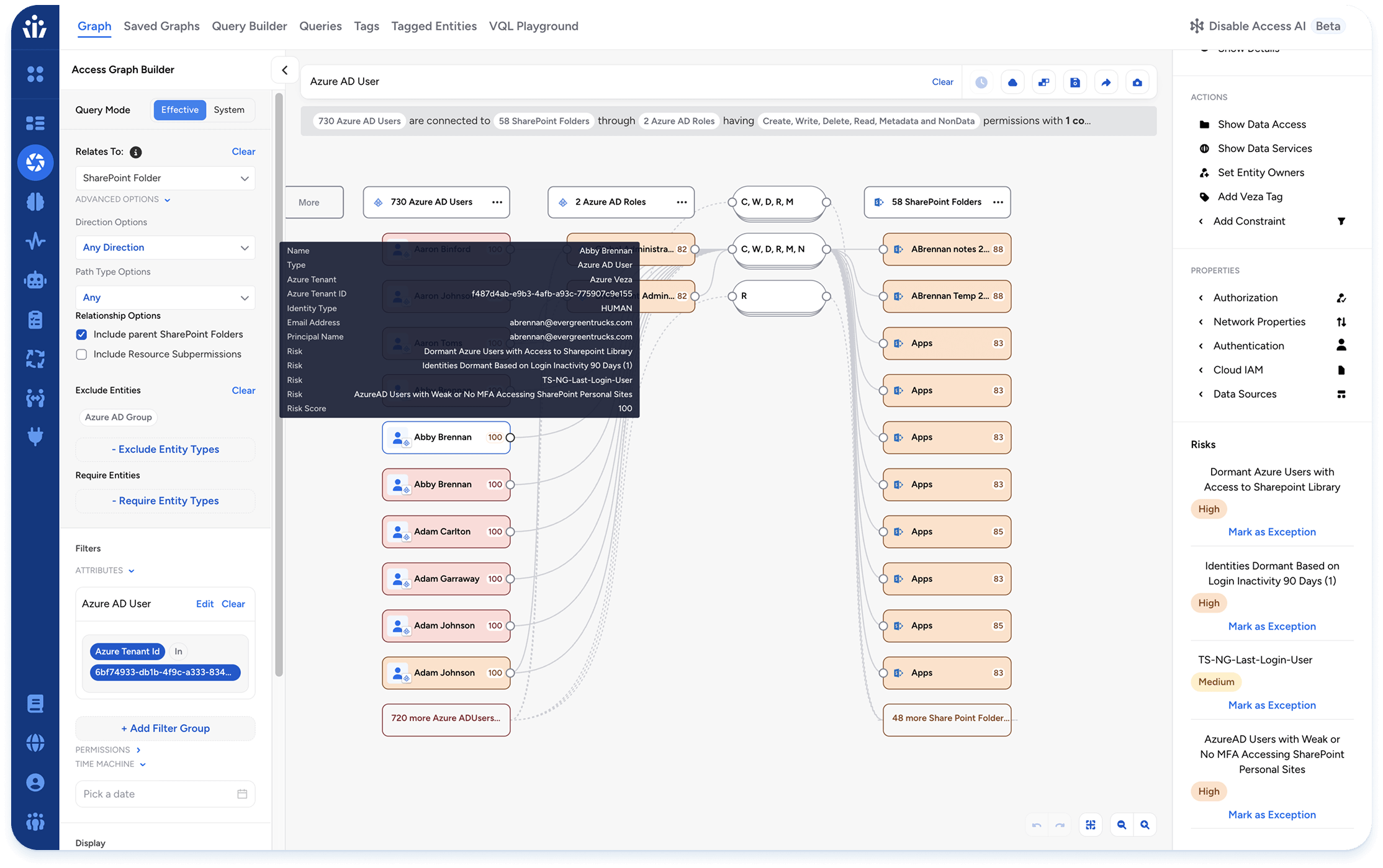
Data System Access
The most sensitive data is often in the least governed places: data lakes, ML datasets, shared drives, and cloud storage. These systems grow quickly, permissions spread faster, and classification rules lag. The result is over-exposed data and audit risk.
Veza connects to classification and tagging tools so data sensitivity shows up in queries. It monitors unstructured systems continuously, flags external access to sensitive datasets, and generates “blast radius” maps whenever broad entitlements expose PCI or PII. With Enrichment Rules, metadata flows directly into dashboards and reviews, so teams can act on context, not just raw permissions. If you are mapping coverage across your estate, you can scan the current roster of supported platforms here: Integrations.
Governance shifts from retroactive fire drills to proactive assurance. When regulators ask how sensitive data is protected, you can point to controls already in place.
Next-Gen IGA and Role Engineering
Traditional IGA was designed for static roles and slow-moving environments. Today, roles overlap, drift, and accumulate permissions across hybrid identity sources, NHIs, and SaaS. Role sprawl becomes both a security and productivity problem.
Veza brings intelligence to role governance. Usage-aware role mining surfaces redundancies and bloated entitlements. Roles can be labeled and prioritized by risk, then right-sized into least-privilege bundles. Reviews validate changes, while lifecycle automation ensures roles do not accumulate dormant access over time.
The result is an IGA that adapts to reality, not one that lags behind it.For a deeper look at outcomes and patterns, see Next-Gen IGA.
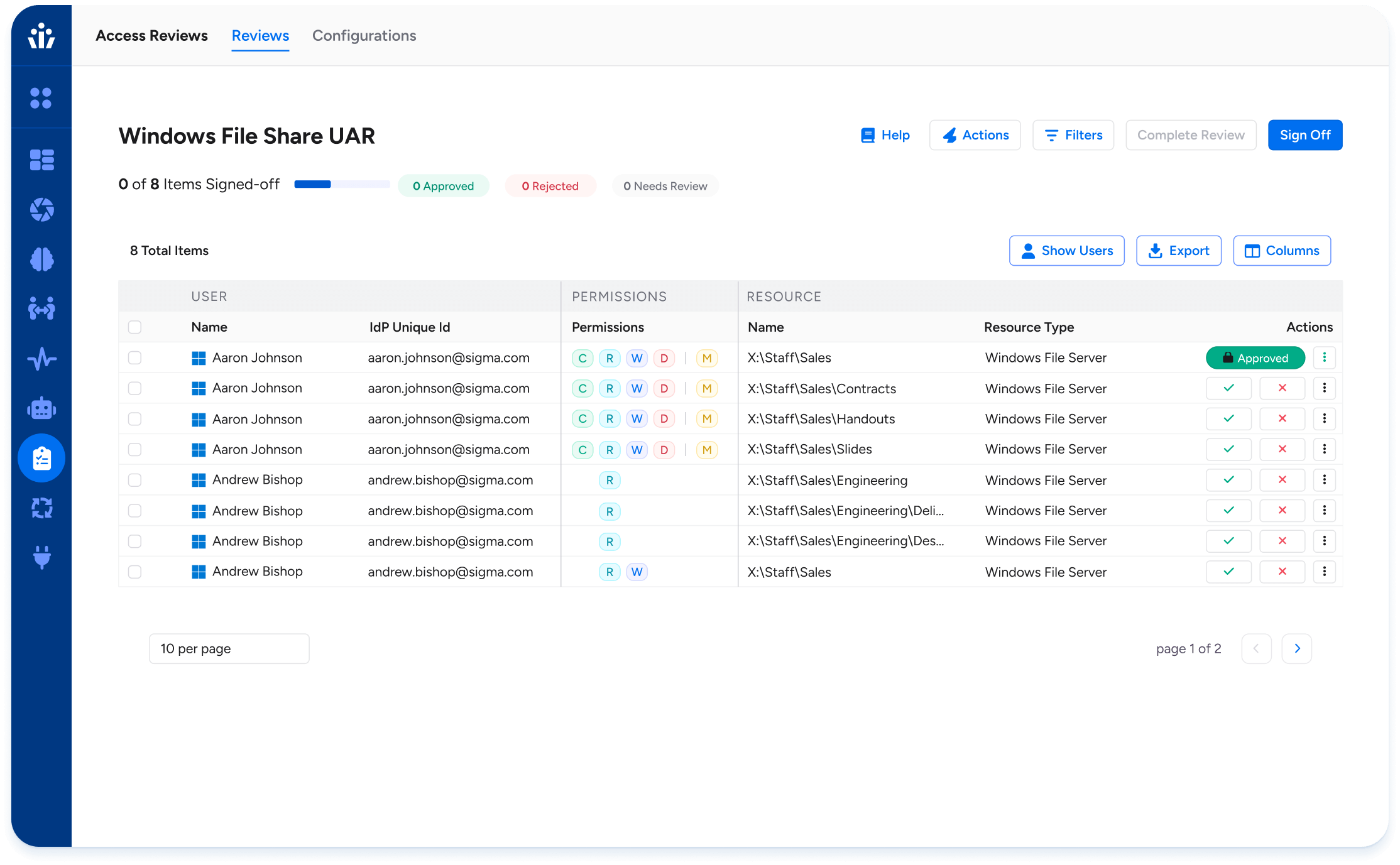
SaaS Access Security & Governance
Every SaaS app brings its own permission model, MFA requirements, and account sprawl. Guest users and local admins proliferate. Inactive identities sit with standing access. SaaS quickly becomes the weak link in the access chain.
Veza consolidates SaaS visibility into one graph, surfacing risky local accounts, inactive privileged users, and weak MFA configurations. Automated scans highlight deviations. Access Profiles keep SaaS requests consistent with enterprise policy. With these controls, SaaS stops being a blind spot and starts being governed.
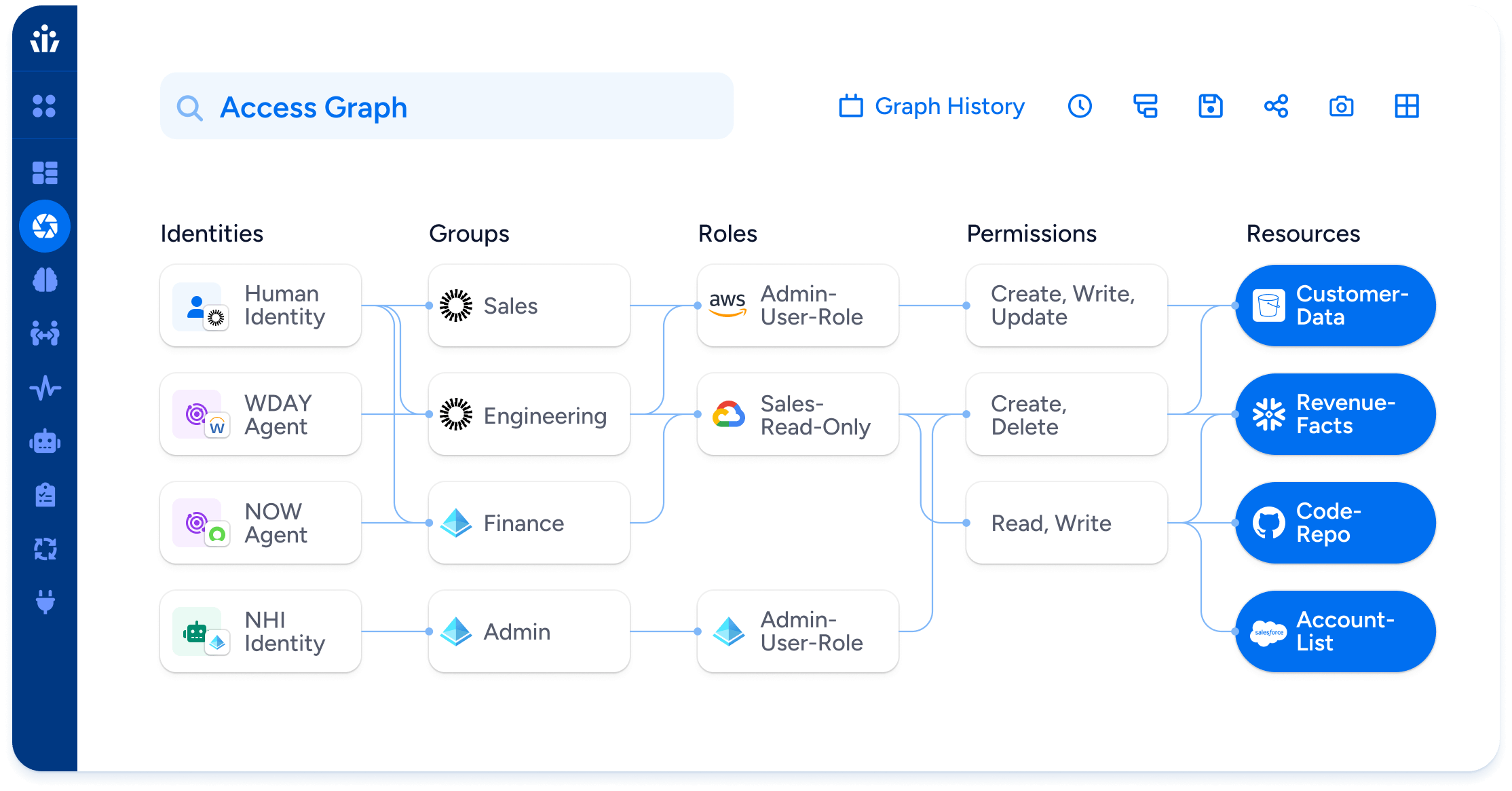
Identity Security Posture Management (ISPM)
Identity is now the true perimeter. But posture across thousands of systems, millions of entitlements, and multiple identity sources is too complex for manual scorecards. Without continuous visibility, dormant accounts, policy drift, and ungoverned NHIs become inevitable.
Veza’s ISPM makes identity posture measurable and actionable. It unifies all identities in the Access Graph, assigning risk scores across SaaS, data, and cloud IAM. Over-permitted root accounts, unused IAM roles, and risky cross-account trusts are surfaced with the same visibility as workforce and SaaS identities, driving remediation through consistent policy enforcement. Reporting is audit-ready, with full traceability. Explore the ISPM use case for details on how Veza helps reduce posture risk, and if you are operationalizing posture as a program, this field guide is a helpful companion: Operationalize identity security.
The outcome is proactive identity defense. Instead of waiting for a breach or an audit to expose gaps, ISPM continuously surfaces and closes them.
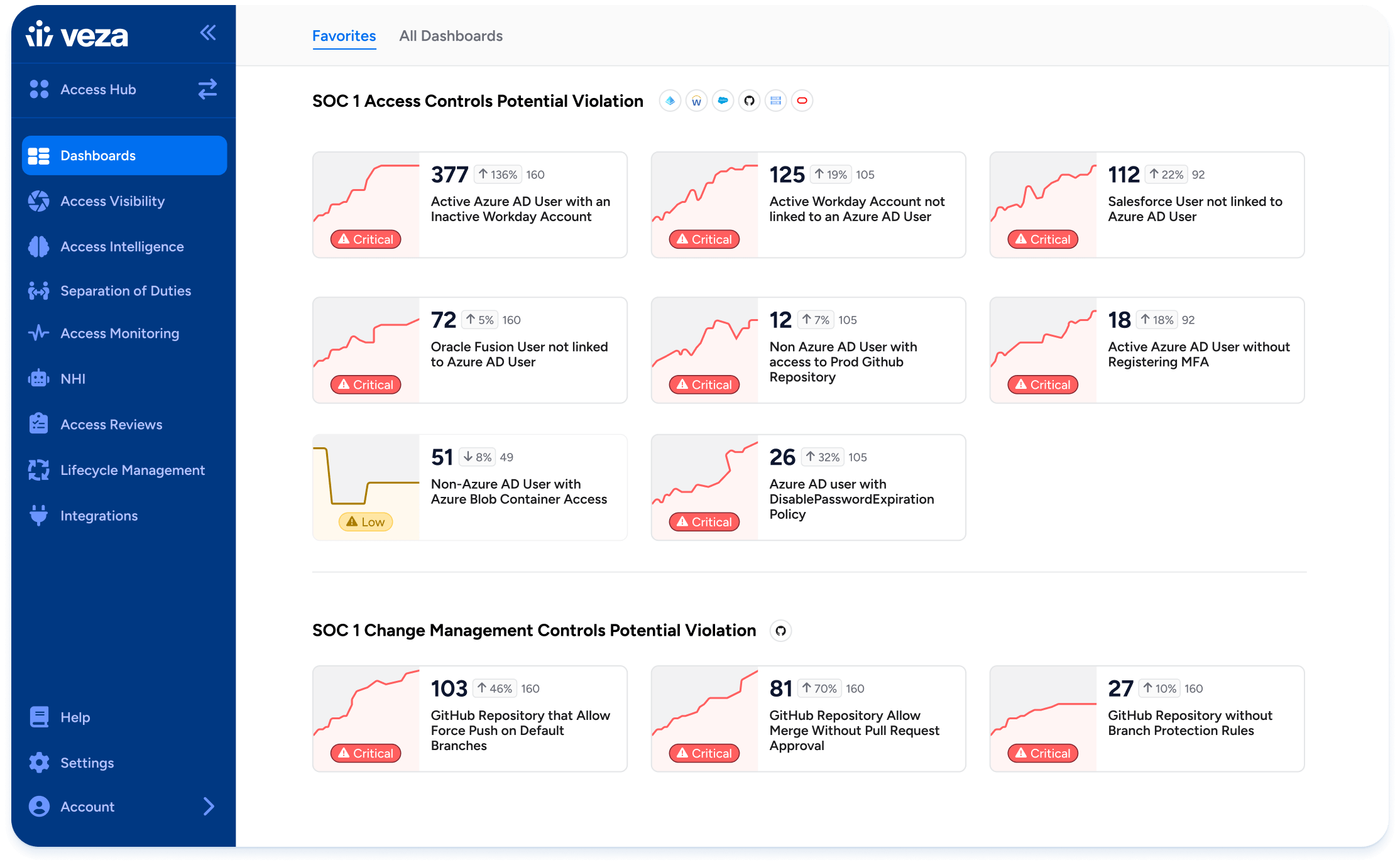
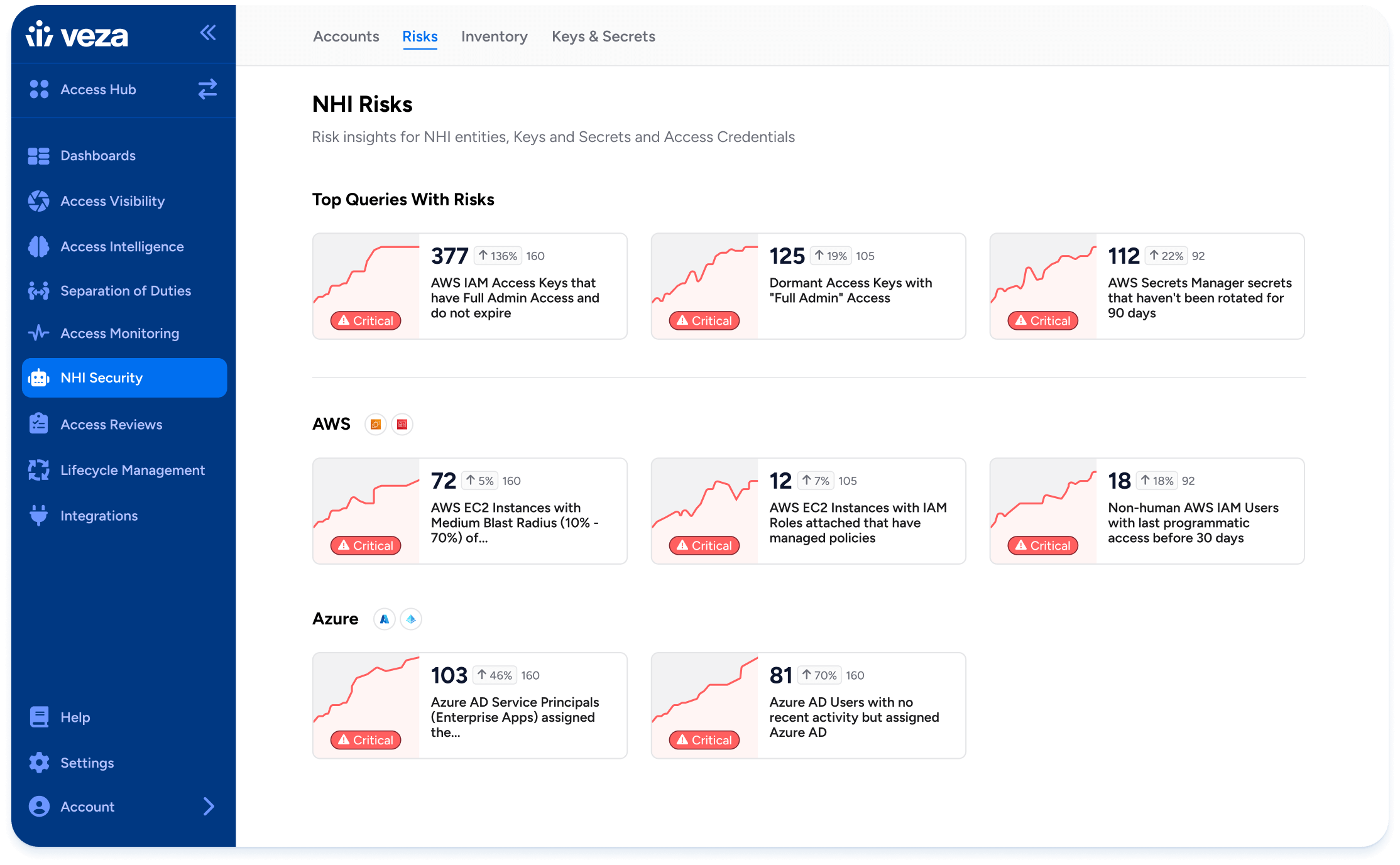
Agentic AI Security
AI agents are entering workflows as first-class actors. They call APIs, fetch data, and automate processes. Without guardrails, they accumulate privileges, impersonate across accounts, or expose sensitive data.
Veza governs AI agents as rigorously as human identities. It discovers them in cloud, SaaS, and code repos, maps impersonation paths, and enforces time-bound access. With Access AI, teams can ask in plain language what agents can do, where they are over-permitted, and what to revoke.
The impact is innovation with control. AI agents can drive automation and scale without opening new doors for attackers. Learn more in Veza’s Agentic AI Security use case.
From privileged access to SaaS, data, non-human identities, and AI agents, these use cases show Intelligent Access working in the real world. They also point to something larger. The problems keep changing. The pattern does not. To keep least privilege alive, you need an architecture that adapts as the stack evolves.
Conclusion
The scenarios in this paper are the places where identity strategy either holds or breaks. Privileged access that stays narrow. Non-human identities that are owned, rotated, and right-sized. Data systems and SaaS estates that stop being blind spots. Posture that is measured and improved in a steady loop. AI agents that operate with the same boundaries and accountability as people. The pattern repeats because the architecture is consistent. See the full picture, describe it in a shared language, and let policy carry the work.
This is Intelligent Access in practice. The Access Graph brings identities, permissions, and resources into a model you can query and trust. Standardization turns technical noise into decisions people understand. Automation keeps those decisions in motion as the environment changes. The result is smaller blast radius, faster reviews, fewer exceptions, and evidence you can hand to an auditor without caveats.
You do not need a reset to begin. You need a first system, a first cleanup, and a policy you are willing to enforce. Start where risk is largest, prove the change with usage and effective permissions, then extend the same rhythm to the next system and the next set of identities. That is how least privilege endures.
What to do next
Explore the model in depth.
Ground your program in the five principles that make least privilege durable by reading the Five Pillars of Intelligent Access.
Connect principles to platform.
See why the architecture wins in real environments in The Veza Advantage.
Operationalize posture.
If posture is your priority, review how ISPM becomes measurable and actionable.
See it in your environment.
Bring your systems, your data, and your identities into view. Request a working session with the team: