The Veza Access Platform was built from the ground up to help companies answer Identity Security’s most crucial question: Who can perform what action on what data?
Unlike legacy tools that deliver fragments of the picture, Veza was architected to unify visibility across all identities and systems. Four core advantages set Veza apart:
Graph Database
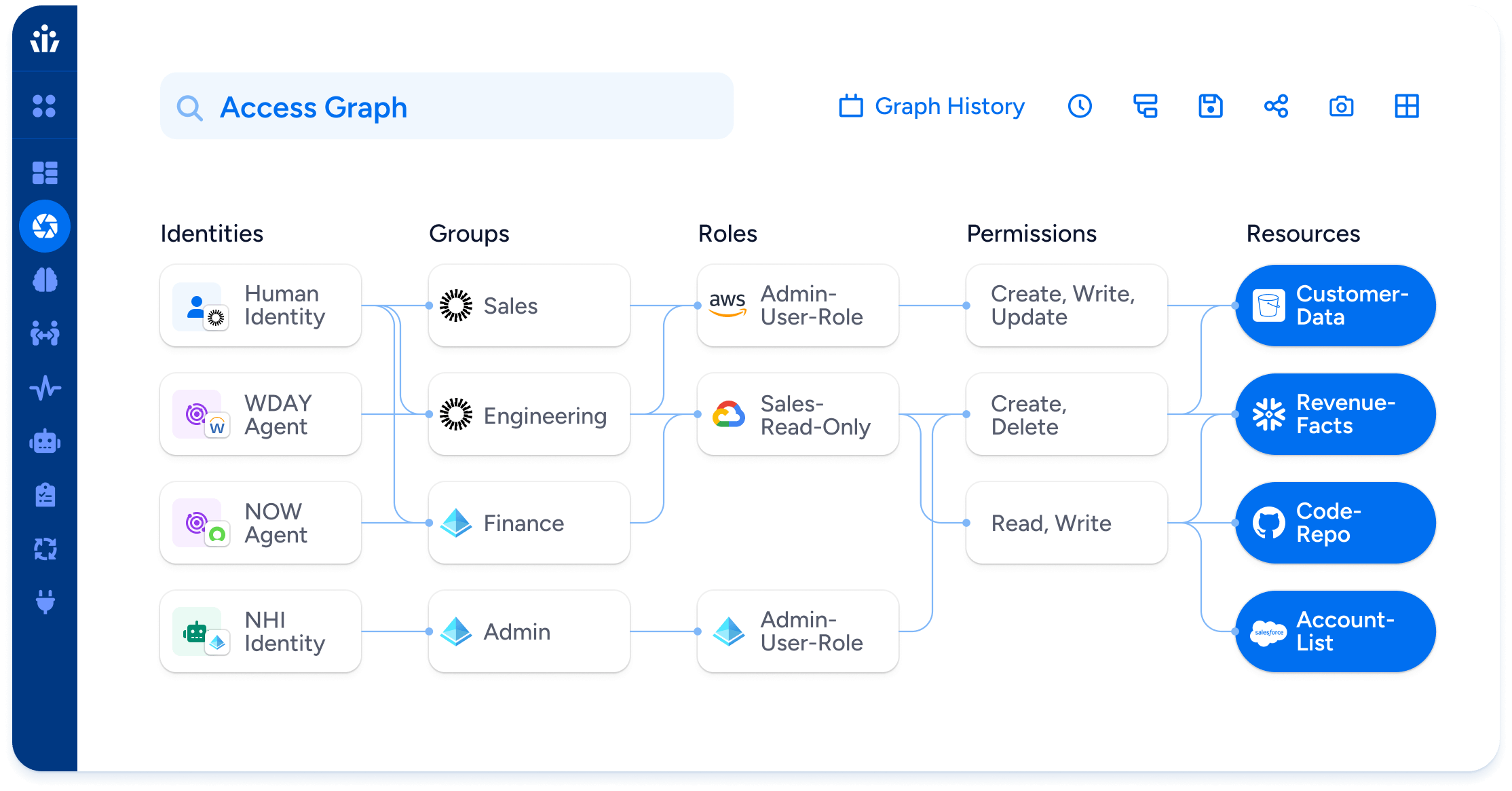
Legacy IGA and IAM systems are built on standard SQL databases. That worked well enough when access meant a handful of group assignments per employee, but it breaks down in today’s world of sprawling SaaS, multi-cloud, and non-human identities. The access fabric now includes billions of relationships across identities, groups, roles, policies, and resources; complexity, a relational model simply wasn’t designed to handle.
Veza’s patented graph database was engineered specifically for this challenge. It stores and queries the relationships between identities and resources at enterprise scale, allowing security teams to trace the full path of access: from an individual identity, through groups, nested roles, and policies, all the way to the specific permissions on a resource. This makes it possible to answer not just what access exists, but how it was granted, unraveling the hidden structures that obscure the truth in legacy tools.
Only a graph-based architecture can deliver both the granular detail of a single entitlement and the broad context of an identity’s full access footprint. That combination is what enables enterprises to make correct access decisions at scale; something SQL-based systems will never be able to achieve.
Effective permissions
In the cloud, access isn’t determined by a single setting. AWS, for example, uses more than a dozen steps to evaluate whether an identity can act, combining identity-based policies, resource-based policies, inherited roles, conditional checks, and overrides. Other platforms like Azure, GCP, and SaaS apps add their own layers of complexity.
Most identity tools stop short of resolving these interactions. They can tell you a group membership, or a role assignment, but not the effective permissions that actually result. Veza calculates the real access outcome, across all systems, and translates it into business language – create, read, update, delete – so both technical and business stakeholders can make decisions without decoding vendor jargon.
Recent updates reinforced this with remediation validation in Access Reviews. When a reviewer rejects access, Veza checks the Access Graph to confirm the entitlement was actually removed. That closes a long-standing governance gap and turns reviews from rubber-stamping names into decisions about what an identity can really do. You can see this capability called out in our product update notes at Veza Product Updates, June 2025.
Breadth of integrations
Identity risk doesn’t respect boundaries. Sensitive entitlements live across SaaS apps, cloud platforms, and on-prem systems. Traditional tools tend to specialize in one domain – on-prem, or cloud, or SaaS – leaving enterprises with a patchwork of partial solutions.
Veza takes a different approach: 300+ pre-built integrations across the enterprise stack, delivered without the heavy agent installs or multi-month projects that slow legacy IGA deployments. Integrations typically take less than an hour to set up, and they ship with out-of-the-box dashboards and risk reports that deliver immediate value.
This breadth keeps expanding. Recent additions include multi-account Snowflake support, risk score sharing with CrowdStrike, and enhanced Salesforce guest access visibility, ensuring enterprises can capture not just more systems, but richer context. For custom and homegrown apps, Veza’s Open Authorization API makes it possible to import access metadata with a lightweight JSON schema. That way, organizations get a truly complete view of access, not just a partial map.
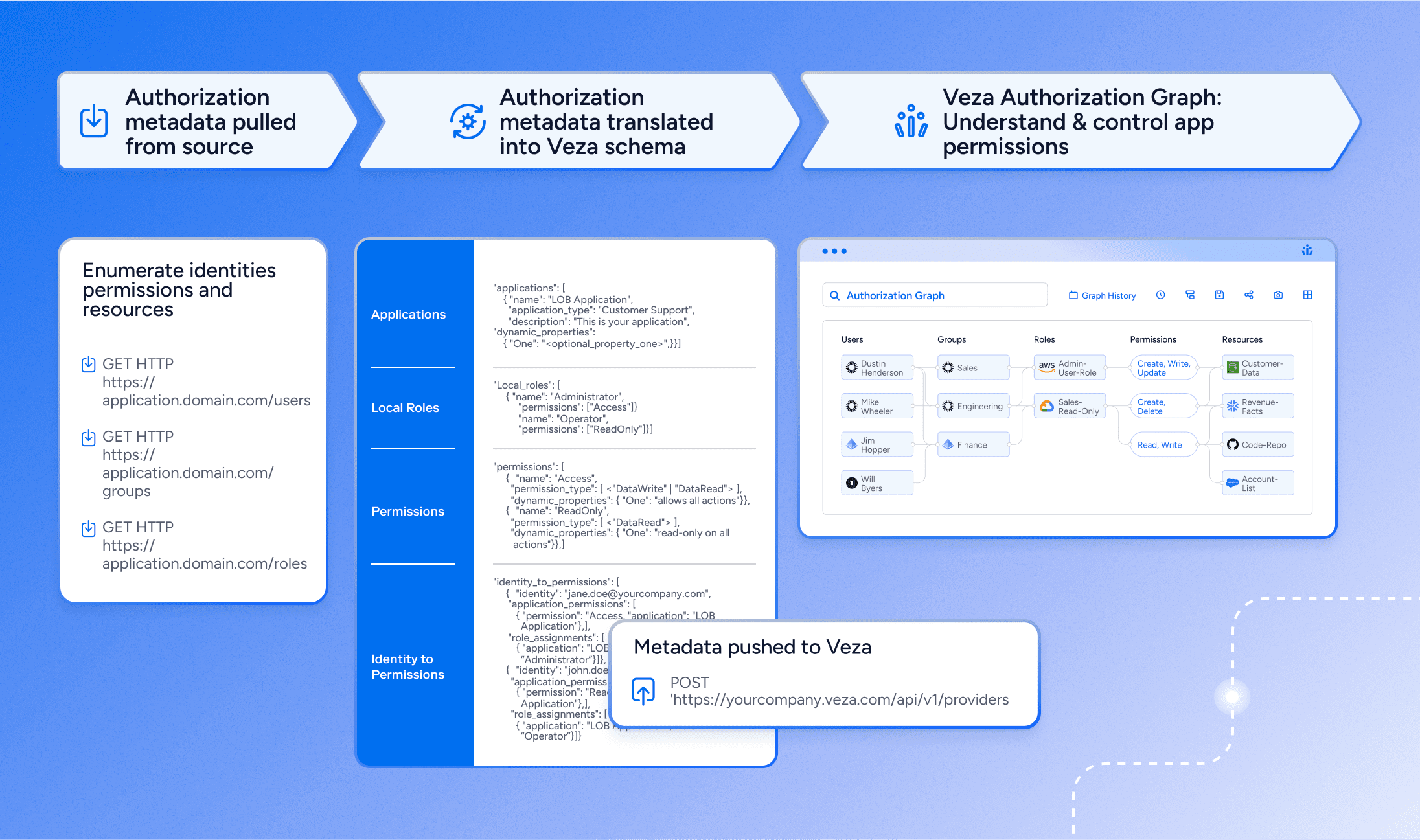
Between Veza’s 300+ pre-built integrations and quick deployment of custom integrations, it’s possible for the first time to create a single vantage point to view the complete picture of identity access in your organization.
Unifying Identity and Permission metadata
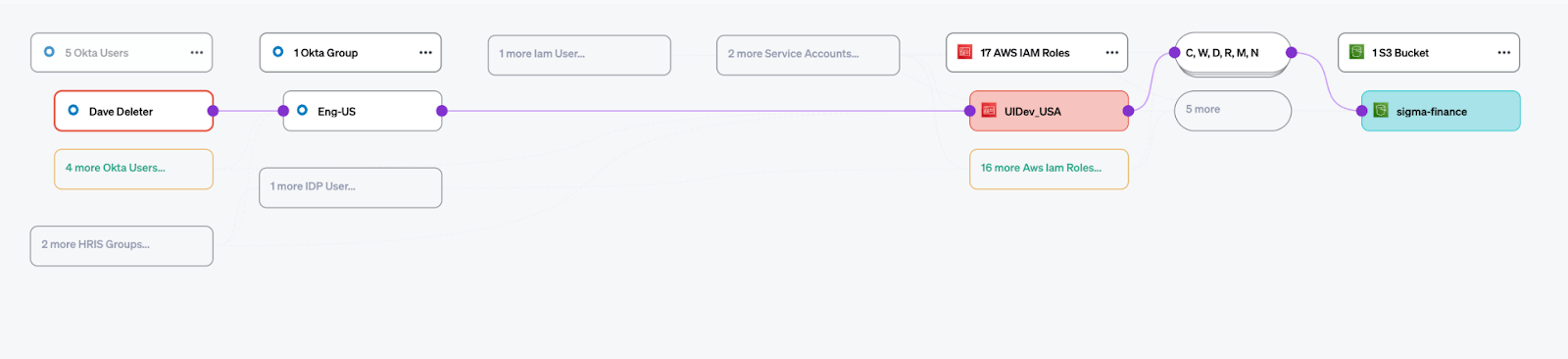
Fragmentation is the enemy of least privilege. Identity Providers (IdPs) know group assignments, but not the entitlements those groups grant. Cloud providers know role permissions, but not which federated identities can assume them. SaaS apps each have their own partial picture.
Veza eliminates this fragmentation by unifying identity and permission metadata into a single model. That means stitching together data from IdPs like Okta and Entra ID, cloud providers like AWS and GCP, SaaS platforms like Salesforce and Snowflake, and local accounts that often fall outside standard processes.
Recent updates expand this capability where growth is fastest: non-human identities are now a first-class part of the access surface. Features like GitHub secrets discovery, cross-organization impersonation visibility in Google Cloud, and dedicated role-based administration bring NHIs into the same governance flow as people. For a deeper look at how teams are operationalizing machine accounts at scale, explore NHI Management.
By resolving these identity silos, Veza makes it possible to answer the most important security question with confidence: who can do what on what data?
And because this unified architecture feeds directly into Access AI, those answers are no longer just raw data. They become contextual insights, plain-language explanations, and actionable recommendations. In other words, the same graph that maps billions of permissions also powers intelligent decisions, making least privilege sustainable at enterprise scale.
Architecture alone is not enough. To operationalize Intelligent Access, Veza translates its Access Graph into a suite of products designed for the real challenges security teams face every day. These are the practical tools that turn principle into practice.
Conclusion
The five pillars make least privilege durable. The Veza Advantage makes it practical. A relational view of access was built for a smaller world. Today you are governing billions of relationships across people, services, roles, policies, and data. The Access Graph was designed for that reality. It unifies identities and permissions across cloud, SaaS, data, and on-prem into one model you can query, explain, and trust. It resolves duplicates, traces inheritance, and stays current as source systems change. Because it computes effective permissions in plain terms like create, read, update, and delete, risk is evidenced, not implied.
That is Intelligent Access in action. Visibility that stands up in audit. Explanations that make sense outside the SOC. Decisions you can automate without guesswork. Keep the model honest, standardize the language, and let policy carry the repetitive work. Architecture turns least privilege from a quarterly project into the way your enterprise runs.
What to do next
- Explore your estate quickly. Start by mapping the systems that matter most and see how they plug into the Access Graph with Veza’s integrations library.
- Extend to custom apps. Bring homegrown systems into scope using Veza’s Open Authorization API. Here is a practical walkthrough to get started: Intelligent Access for custom apps.
- Bring NHIs under real governance. Treat service accounts, tokens, workloads, and AI agents as first-class identities with NHI Management.
- Apply the model in your environment. If you want to see how this architecture lands against your systems and data, request a demo.