Architecture-first, not bolt-on. See how Veza’s approach makes identity security clear and current.
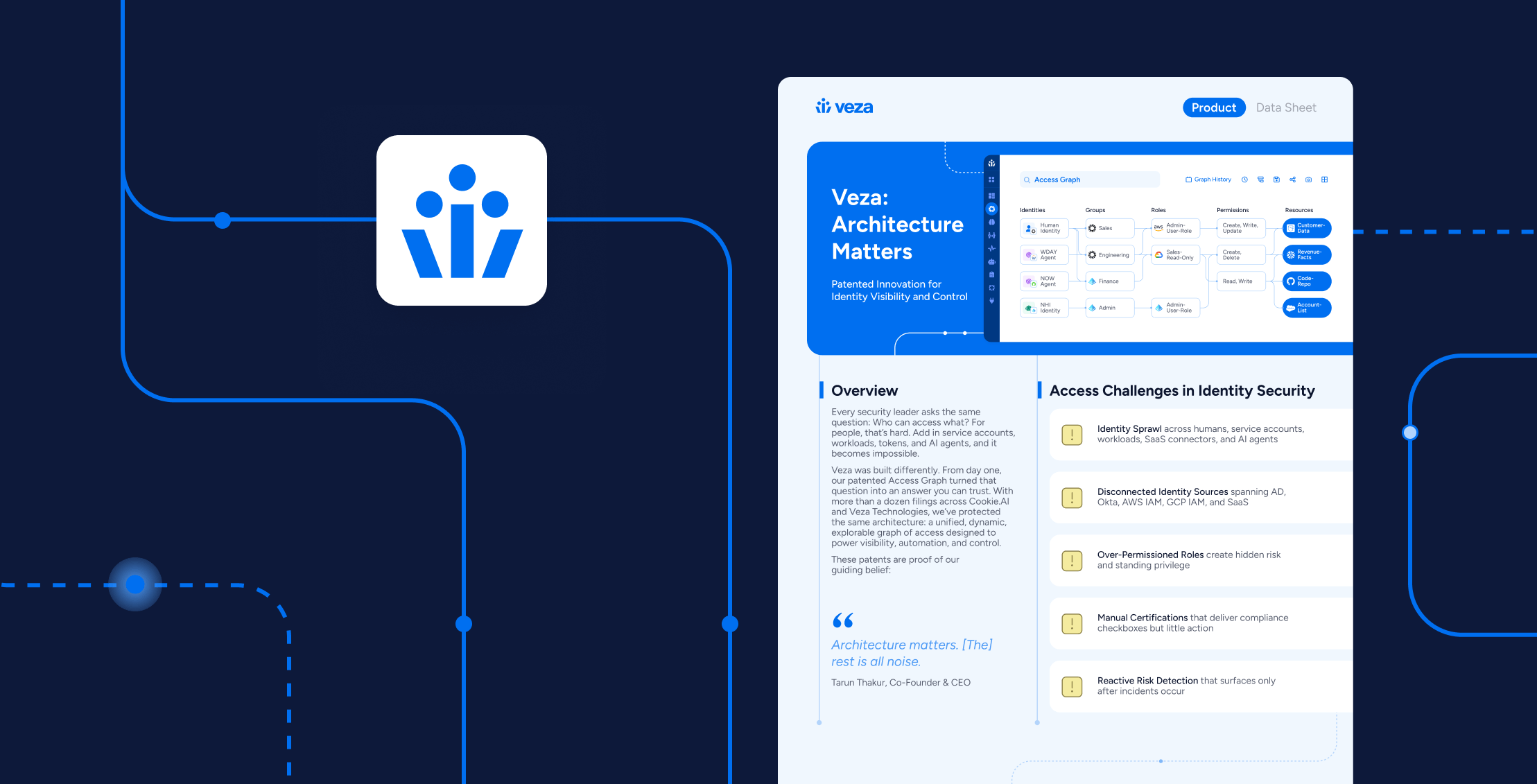
Identity is the attack surface. We started with the real problem, identity security at scale, and built an architecture that makes the answer to who can access what clear and current. The Veza Access Graph gives you one searchable map across clouds, SaaS, data systems, and non-human identities. It computes effective permissions you can act on, stays fresh with event-driven updates, and turns policy into enforceable controls with approvals and evidence.
This solution brief distills the approach and the patent coverage behind it: graph modeling, canonical truth, freshness, governance that sticks, and performance that holds at enterprise size. For the deeper narrative, see Architecture Matters: Veza Access Graph & Patents.
Built for practitioners, not slides. The brief shows how Veza Access Graph spans AWS, Snowflake, and SaaS; how effective permissions create entitlement truth for humans and NHIs; and how push updates plus workflow evidence turn visibility into control at enterprise scale.
What you’ll find inside
- One view you can actually query across clouds and SaaS – foundational to modern identity security
- Entitlement truth from effective permissions (humans + NHIs) for cleaner access reviews
- Decisions based on current signals from source systems, not last month’s export
- Approvals and evidence captured in the flow of work for audit-ready identity security
- Fast answers at enterprise scale so SecOps stays unblocked
You can also explore adjacent resources: the ISPM Buyer’s Guide for posture and governance patterns, our IVIP Guide for visibility and intelligence use cases, and a simple path to see your own environment in the Access Graph when you’re ready.
For background reading, NIST: Zero Trust Architecture (SP 800-207) and AWS IAM best practices provide helpful context that we operationalize in day-to-day identity security work.
Fill out a quick form to get the solution brief and get a concise overview of the patents and the architecture they protect.