Map every bot, token, and service principal to a named human owner. See effective permissions in plain language and keep keys and scopes within least privilege.
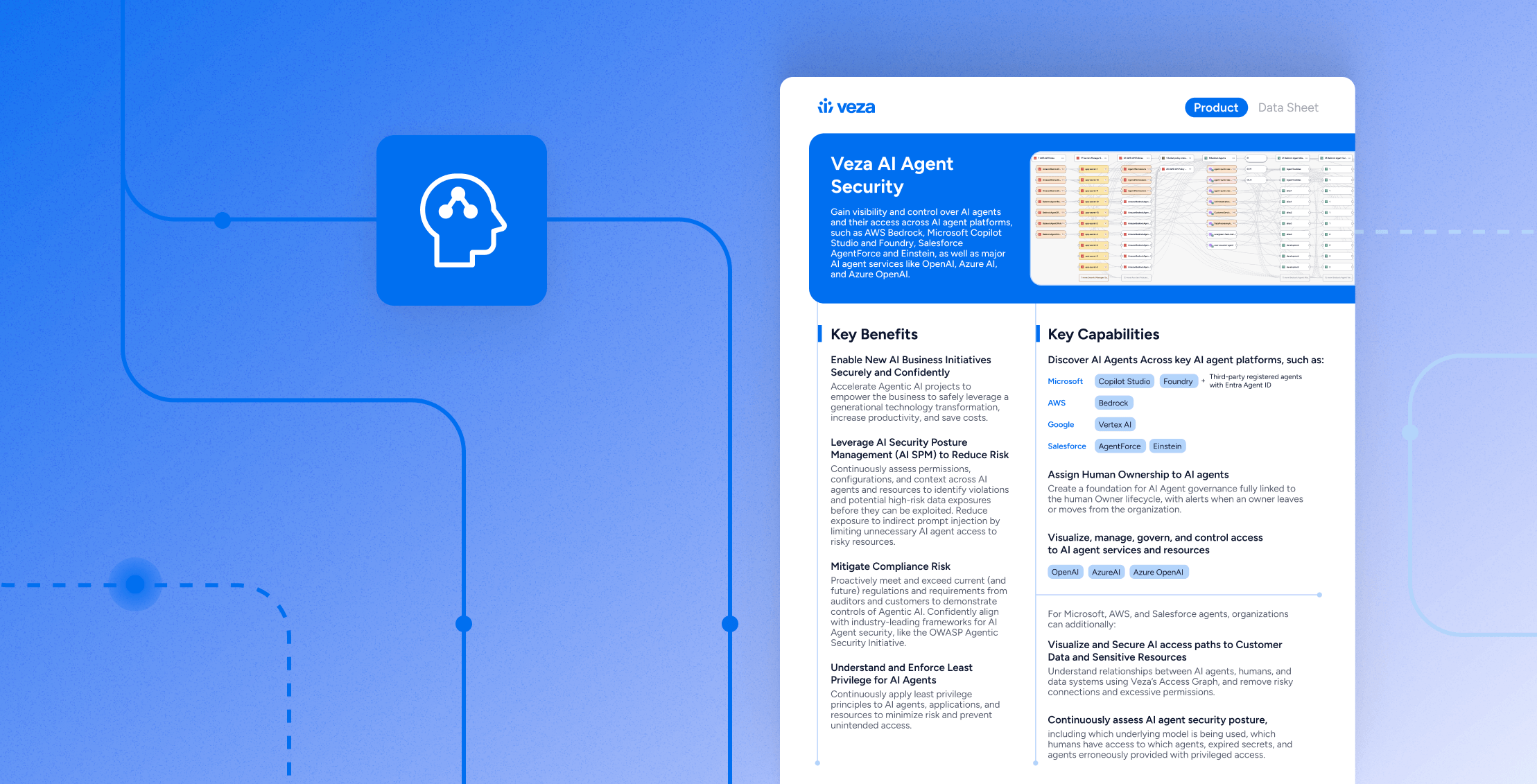
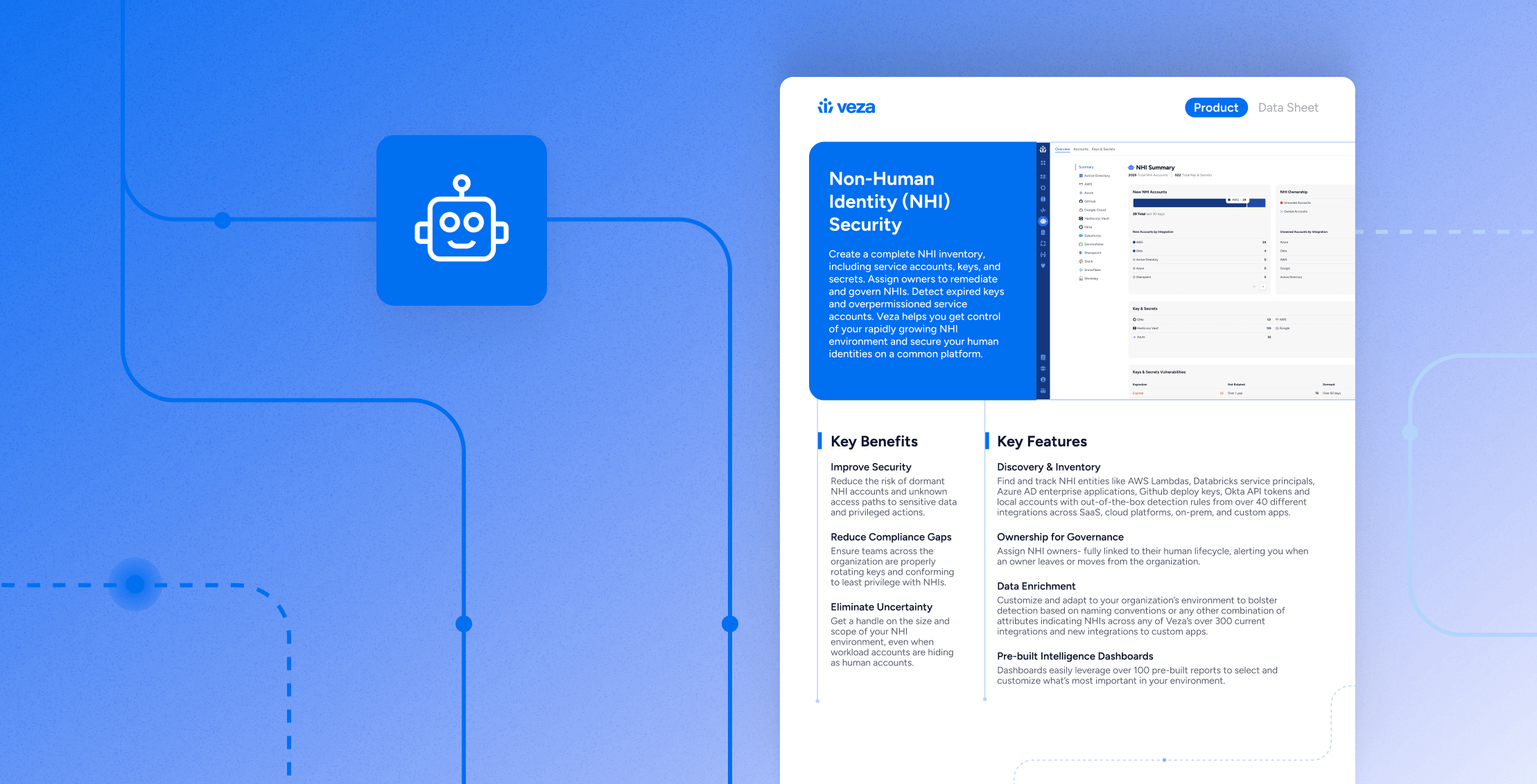
Build a complete NHI inventory across cloud, SaaS, data platforms, and directories. Assign owners and backups to every service account, API key, app registration, and workload identity. See who can do what to which data through effective permissions in the Access Graph, detect over-permissioned NHIs and expired credentials, and prioritize remediation with Access Intelligence. Out-of-the-box analytics and reports help you target risky scopes, enforce rotation and expiry on schedule, and produce evidence for audits and insurers. For coverage and the classes you’ll inventory first, see the Non-Human Identity Management use case.
Value highlights
- Ownership for governance: tie each NHI to a human lifecycle and alert when owners change.
- Visibility beyond vaults: find unmanaged secrets outside vaults and migrate them.
- Prioritized risk: target unrotated keys, inactive NHIs, and broad permissions first.
Who it’s for
- Identity, Security, and Platform engineering leaders
- DevOps and data platform owners accountable for production access
- Compliance and audit teams that need evidence, not screenshots
What you’ll learn
- How to assign and enforce NHI ownership with backups
- How to read effective permissions as plain-language actions on data
- How to automate expiry/rotation and notify owners on change
- How to generate evidence packs for audits and insurers
FAQ
What is NHI ownership?
Treat each non-human identity — service accounts, tokens, app registrations, workload identities — as an accountable identity with a named human owner and backup tied to effective permissions and data impact.
How does Veza discover NHIs?
Veza discovers and normalizes identities across cloud, SaaS, data platforms, and directories, then expresses effective permissions for blast-radius analysis and governance.
How do I keep ownership current?
Enforce owner metadata at creation, monitor permission changes, rotate keys on schedule, and notify the recorded owner when newly data-impacting rights appear. Use dashboards and reports to measure progress.