Why Identity Security Posture Management (ISPM) Matters Now
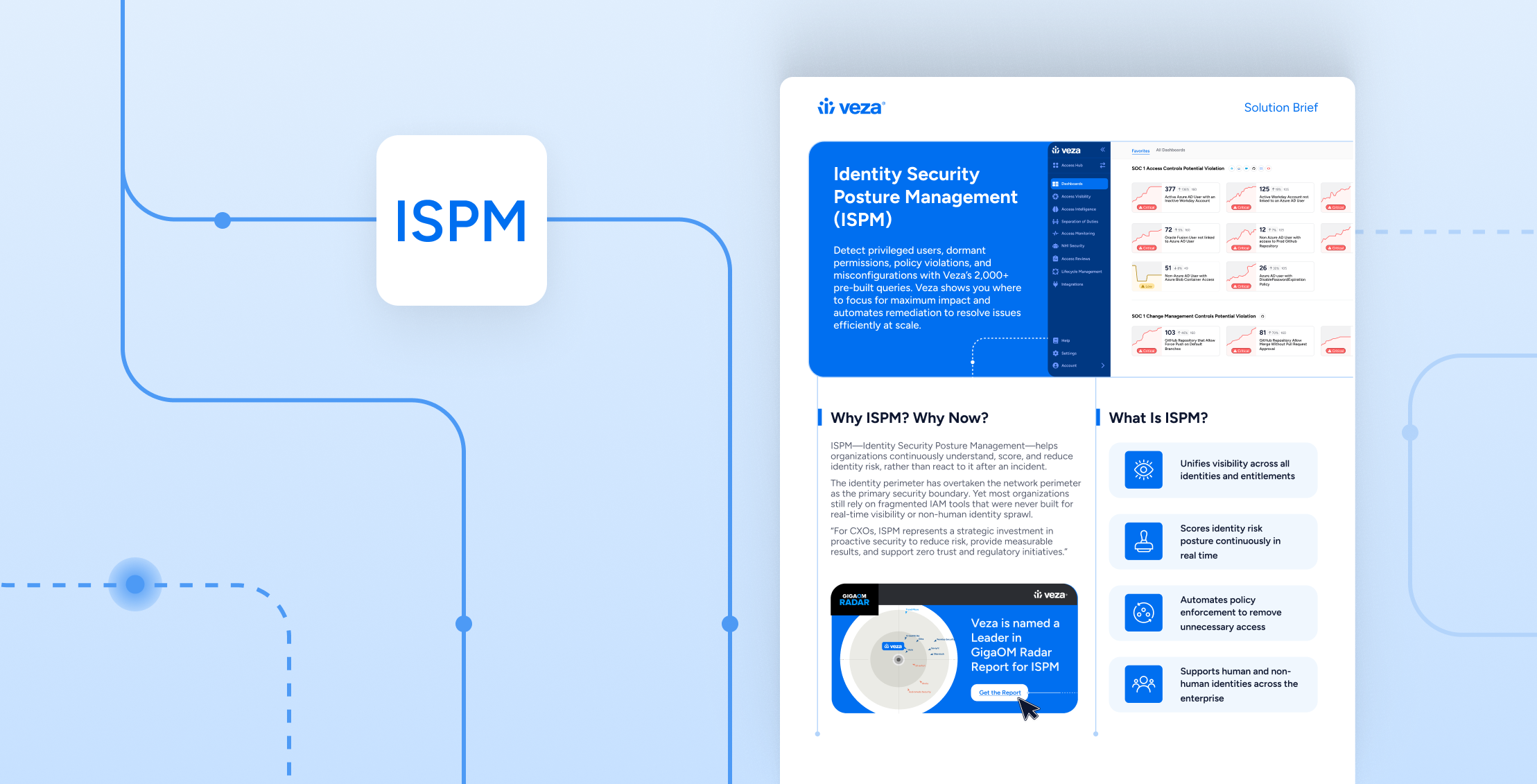
Identity Security Posture Management (ISPM) helps organizations continuously monitor, score, and reduce identity risk before it leads to an incident. Unlike traditional IAM tools, ISPM provides continuous visibility across both human and nonhuman identities, enabling proactive enforcement of least privilege and identity risk controls.
The identity perimeter has overtaken the network perimeter as the critical security boundary. However, most organizations still rely on fragmented IAM and IGA tools that were never designed for continuous visibility, automated remediation, or machine identity governance.
For CXOs and security leaders, ISPM represents a strategic investment in proactive identity risk reduction, measurable security outcomes, and support for Zero Trust and regulatory initiatives such as SOX, GDPR, HIPAA, and PCI DSS.
What Is Identity Security Posture Management (ISPM)?
ISPM is a modern security framework defined by industry analysts to help organizations understand and improve their identity security posture. It doesn’t replace IAM or IGA—it enhances them by providing continuous visibility, identity risk scoring, and policy-based automation across hybrid, SaaS, and cloud environments.
Learn more about how Veza supports modern governance in Next-Gen IGA.
Key Capabilities of Veza ISPM
- Unified Identity Visibility: Gain a continuous view of human and nonhuman identities across SaaS, cloud, and on-prem systems. Nonhuman Identity Management Use Case.
- Identity Risk Scoring: Quantify exposure and prioritize remediation with contextual scoring of entitlements.
- Nonhuman Identity Governance: Discover and control service accounts, APIs, and bots.
- Automated Remediation: Detect toxic combinations and dormant accounts, then trigger workflows in ITSM tools like ServiceNow or Jira.
- Audit-Ready Reporting: Generate continuous evidence for SOX, GDPR, HIPAA, SOC 2, and PCI.
Real-World ISPM Use Cases
- Access Investigations: Quickly trace the blast radius of a compromised account.
- Compliance Reporting: Simplify audits with posture-aware reporting.
- Least Privilege Enforcement: Detect and remove excessive entitlements at scale, leveraging Access Reviews Automation.
- Machine Identity Oversight: Govern nonhuman identities often ignored by legacy IAM tools.
Get Started with ISPM
Veza delivers ISPM as an execution layer that works with your existing IAM, IGA, and PAM tools – no forklift required. Download the ISPM playbook to see how Veza enables continuous identity risk reduction, proactive compliance, and measurable security posture improvement.