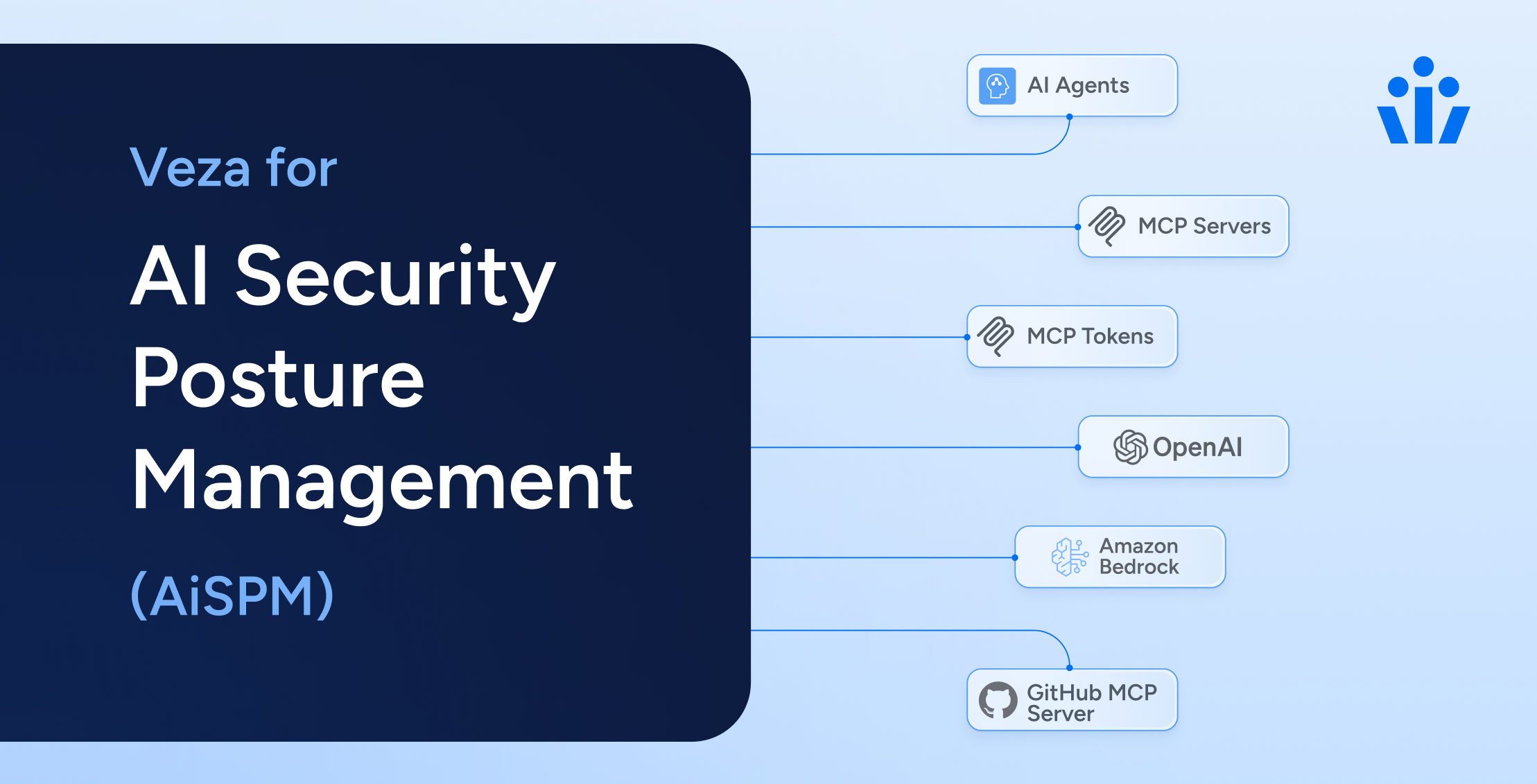
AI agents are transforming enterprise productivity and introducing an entirely new class of security threats that traditional tools can’t defend against.
As organizations rush to deploy autonomous agents and connect them to sensitive data, they’re also opening the door to unprecedented attack vectors: data poisoning, malicious Model Context Protocol (MCP) connections, and identity sprawl at massive scale. This new agentic workforce can’t be governed with yesterday’s IAM or DSPM systems.
Download our latest article to explore:
How attackers are exploiting AI supply chains and model lifecycle
Why legacy IAM, IGA, and CSPM solutions fail in the age of AI
The emerging blueprint for AI Security Posture Management (AI SPM) and how an Access Graph reveals who (or what) can take action on your data
The enterprise is rapidly deploying an autonomous “agentic workforce.” But these AI systems introduce a new, insidious threat landscape that traditional security tools cannot address.1 Moreover, these AI systems are more than just the foundation Large Language Models (LLMs) they are built on: they are active systems that connect to corporate data, interact with external tools, and execute complex tasks on behalf of users. This creates a fundamentally new security challenge. The risk is no longer confined to the data on which the model was trained. It now extends to every piece of data an agent can access at inference time via the prompt or Retrieval-Augmented Generation (RAG) and every action it can perform with the tools it’s given. This could extend even further with Just-in-Time (JIT) approvals for additional permissions and access that an agent might request during a run and Model Context Protocol (MCP) connections to external systems. An agent with access to a CRM can inadvertently expose customer data; one connected to financial systems could be tricked into executing unauthorized transactions.
Therefore, to secure AI, you must be able to track and govern the entire agentic lifecycle and data ecosystem—from the data used for training and fine-tuning to every real-time data retrieval and tool execution in its operational workflow.2 As industry analysts at Gartner note, a core function of AI Security Posture Management (AI SPM) is to discover AI models and their associated data pipelines to evaluate how they create risk. You need to know precisely what data every model and agent had access to, because that data is now part of the asset you are deploying.
The New AI Threat Landscape: From Data Poisoning to Malicious MCPs
The risks associated with AI are not just theoretical. They represent a new class of threats that target the integrity and confidentiality of models and enterprise data, as well as the complex supply chains that support them.
- Training Data Poisoning: Attackers can intentionally manipulate the data used to train a model, introducing vulnerabilities, backdoors, or biases. By poisoning as little as 1-3% of a dataset, an attacker can significantly impair an AI’s accuracy. This could cause a fraud detection model to overlook criminal activity or a customer service bot to promote malicious links.
- Model Inversion and Data Leakage: Through sophisticated query techniques, attackers can reverse-engineer a model’s outputs to reconstruct parts of the sensitive data it was trained on, such as private medical photos or proprietary source code. This risk is amplified when AI agents, which often lack user-specific access controls, inadvertently include sensitive data in their responses that the user is not authorized to see.
- Compromised AI Supply Chains & Malicious MCPs: AI agents could rely on a supply chain of external tools and data sources to perform tasks, often connected via the Model Context Protocol (MCP). An MCP server acts as a bridge, giving an agent access to new capabilities. However, these servers represent a new attack vector. A malicious or compromised MCP server can feed an agent tainted context, poison it with malicious tools, or exploit over-permissioned credentials to exfiltrate data—a risk compounded by the fact that security is often an afterthought in the rush to adopt new AI technologies.
These AI-specific attacks have real-world consequences. In a widely reported incident, an open-source AI penetration testing framework called HexStrike-AI was repurposed by threat actors within hours of its release to exploit zero-day vulnerabilities in Citrix NetScaler systems, shrinking the time-to-exploit from weeks to minutes. According to the 2024 Verizon DBIR, the use of stolen credentials remains a top breach vector, and with AI agents, a single compromised agent identity can have a catastrophic blast radius.
Clearly, the problem of least privilege is at least as important for AI systems as it is for other parts of the IT infrastructure.
Why Legacy Security Tools Fail the AI Test
Existing security tools were not designed for this new reality. Their fundamental architecture prevents them from surfacing and reducing the unique risks associated with least privilege in the AI lifecycle.
Posture Management is NOT Least Privilege: Cloud Security Posture Management (CSPM) can identify a misconfigured cloud resource, and Data Security Posture Management (DSPM) can find sensitive data at rest. However, as Gartner points out, a key driver for AI SPM is the need to map the data pipelines used by models—a task for which these tools lack the necessary identity context.
Existing Identity and IAM / IGA / PAM are Built for Humans: Traditional Identity Governance and Administration (IGA) and Identity and Access Management (IAM) platforms are built around the structured “joiner-mover-leaver” lifecycle of human employees. They cannot cope with the explosive growth and chaotic, automated lifecycle of agents. While the exact ratio varies by organization, industry reports consistently show that agent identities now dramatically outnumber human identities, often by a factor of 45 to 1 or more. Their underlying relational databases are ill-equipped to calculate the complex “effective permissions” across the thousands of identities and billions of permissions in a modern enterprise.4
Non-Human Identity (NHI) Security is Built for Deterministic Workloads: The emerging space helps enterprises discover, govern, and secure service accounts, keys, and secrets. This is the lifeblood of more traditional workloads, like enterprise applications, containers, and virtual machines. This is an effective approach when the tasks and purposes of the workload are “deterministic”- that is, constrained, repeatable, and predictable. AI doesn’t work this way.
The reality is that permissions for AI systems like agents are a hybrid of past models and approaches. They often inherit human permissions when they are working on behalf of a user; in this case, they have access to what the person invoking them has. In other cases, an AI agent might have its own access, service accounts, and keys; here, it looks much like a more traditional NHI.
The Power of an Access Graph: Mapping the AI Data Lineage
To solve these novel challenges, identity security and getting to least privilege requires a new foundation. A modern AI SPM needs the foundation of an Access Graph, a purpose-built graph database to map the complex web of permissions and relationships across the entire enterprise. However, for AI, it needs to be much broader and comprehensive than before. It must encompass both human and non-human identities because AI agents can act like either or both. The criticality of having a single platform to cover all identity types is underscored because that is exactly what is required to solve the least privilege problem for AI.
This comprehensive Access Graph provides a single source of truth by ingesting authorization metadata from hundreds of integrations—spanning identity providers, cloud platforms like AWS, Azure, and GCP, data systems, and SaaS apps. It then computes the true effective permissions for every identity—human and agent—answering the fundamental security question:
“Who can take what action on what data?”.
For AI, this capability is transformative. The graph provides a complete, auditable map of an AI agent’s data provenance. It visualizes the entire chain: from the developer who initiated the training, to the service account identity used, to the specific data sources it accessed (like Amazon S3 buckets or vector databases), and even to the external tools and MCP servers the deployed agent can connect to.
AI SPM in Practice: From Data Lineage to Runtime Governance
A graph-powered AI SPM delivers tangible security outcomes that are impossible with legacy tools.
1. Discovering Shadow AI and Enforcing Model Compliance
A primary driver for AI SPM is the rapid, often decentralized deployment of AI models and agents, creating a “shadow AI” problem where systems are used without IT oversight. A modern AI SPM platform addresses this head-on by providing a comprehensive discovery capability. An authorization graph can automatically inventory all AI assets in your environment—from agents developed in AWS Bedrock, Azure AI, and Google Vertex AI to the MCP servers they connect to.3 This complete inventory is the foundation for governance. Once CISOs and IT teams can see every agent and model in use, they can enforce compliance. By mapping exactly which agents are accessing which models, security teams can create policies that ensure only sanctioned and vetted models are used. This is critical for preventing the use of non-compliant open-source models that may introduce vulnerabilities or violate data privacy regulations, answering the crucial question: “What AI models are in use, and do they represent an unacceptable risk?”
2. Mapping the AI Data Lineage to Prevent Data Entanglement
Before deploying a model, you must understand its potential data exposure. An authorization graph allows you to ask critical questions like, “Show me all AI models that were trained on sensitive PII data from our production Snowflake database.”. By visualizing the full data pipeline for every model, you can identify and mitigate risks of data entanglement before a model ever goes live, ensuring that models trained on sensitive data are not deployed in contexts where that data could be inadvertently leaked.
3. Securing the End-to-End AI Supply Chain
An AI system is only as secure as its weakest link. A robust AI SPM provides full-stack visibility into the entire AI supply chain, from the LLM platforms like OpenAI and AWS Bedrock, to the vector databases and infrastructure they run on. Crucially, this includes mapping the permissions of MCP servers and the tools they expose. This allows you to enforce consistent access policies and prevent an agent from connecting to a malicious or over-privileged MCP server that could lead to data exfiltration or unauthorized actions.
4. Governing Deployed AI Agents with Least Privilege
Once an agent is in production, its runtime permissions must be strictly controlled. An authorization graph provides a real-time view of what every agent can access and do. If an agent is compromised, security teams can instantly query its identity to see its full “blast radius”—every system it could connect to and every action it could perform—and contain the threat in minutes, not days. This allows organizations to enforce the principle of least privilege for their entire agentic workforce, ensuring agents built on platforms like Microsoft Copilot or Google Vertex AI only have the minimum access required.
The Future of Secure AI is Identity-Powered
Adopting AI without a clear understanding of its permissions across the entire data ecosystem and supply chain is a critical governance failure. The unique risks of data poisoning, model inversion, and compromised MCPs demand a new security paradigm. AI SPM, powered by an authorization graph, provides the essential governance infrastructure for the AI era. By delivering a definitive, queryable system of record for the permissions and data provenance of every AI agent, organizations can replace uncertainty with visibility, enforce least privilege, and unlock the transformative potential of AI with confidence and control.