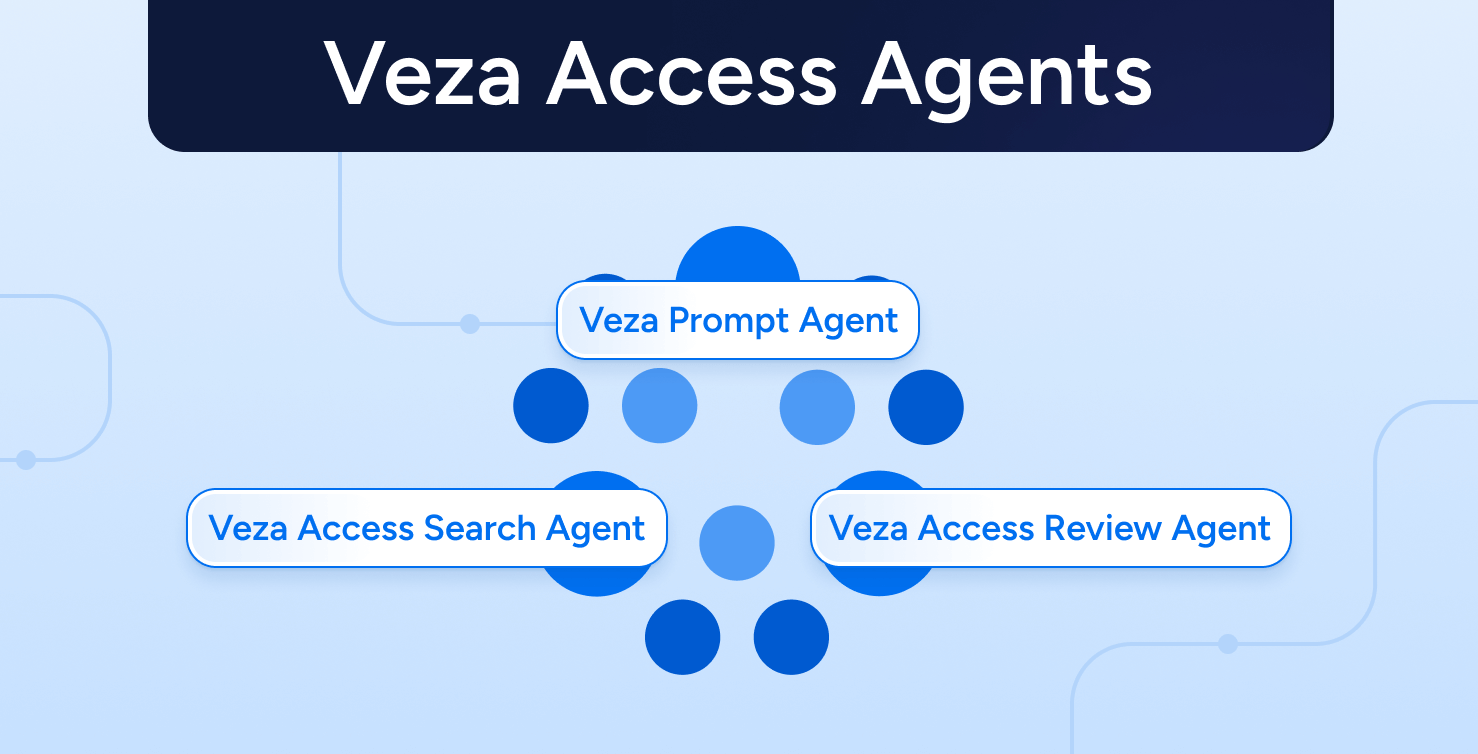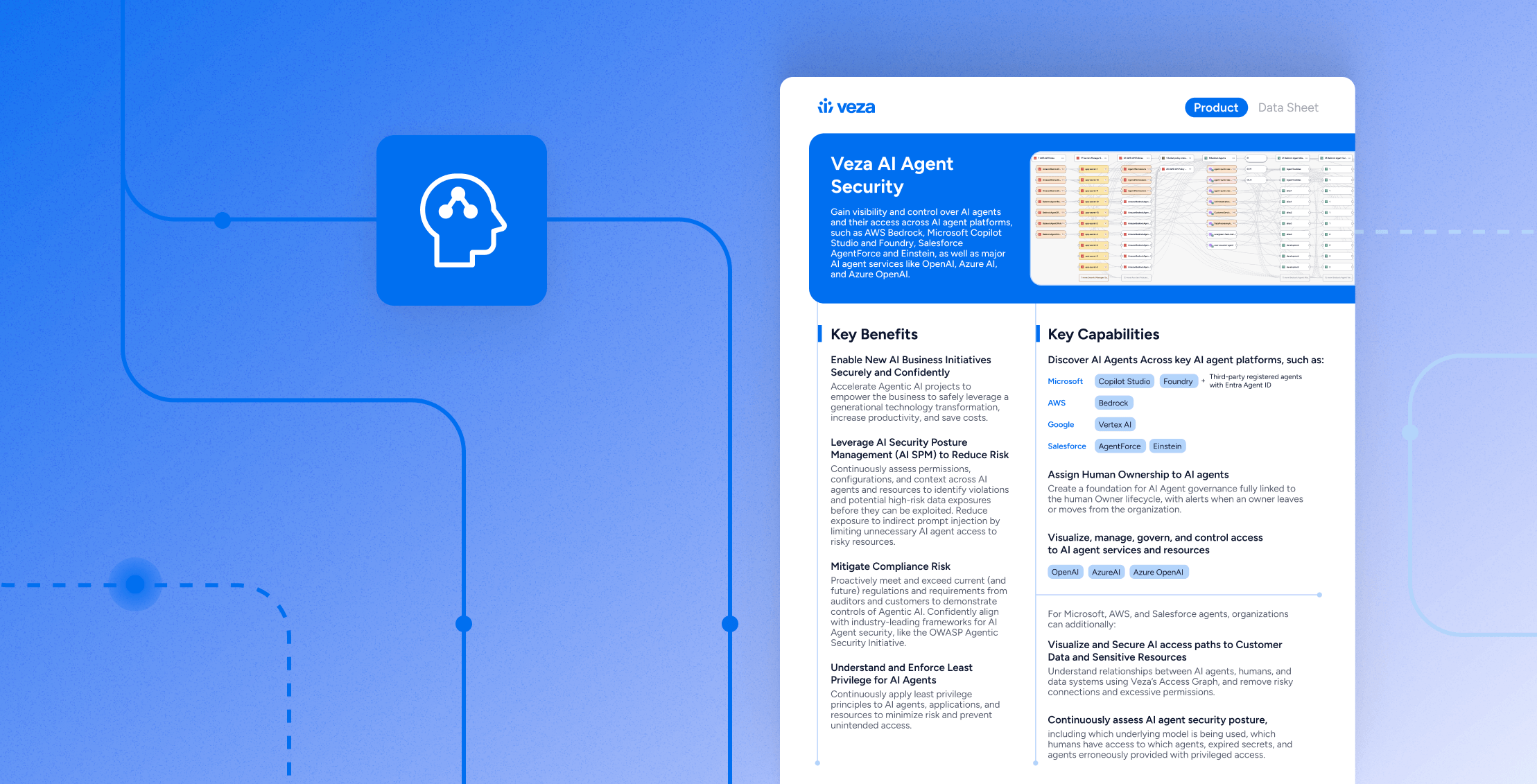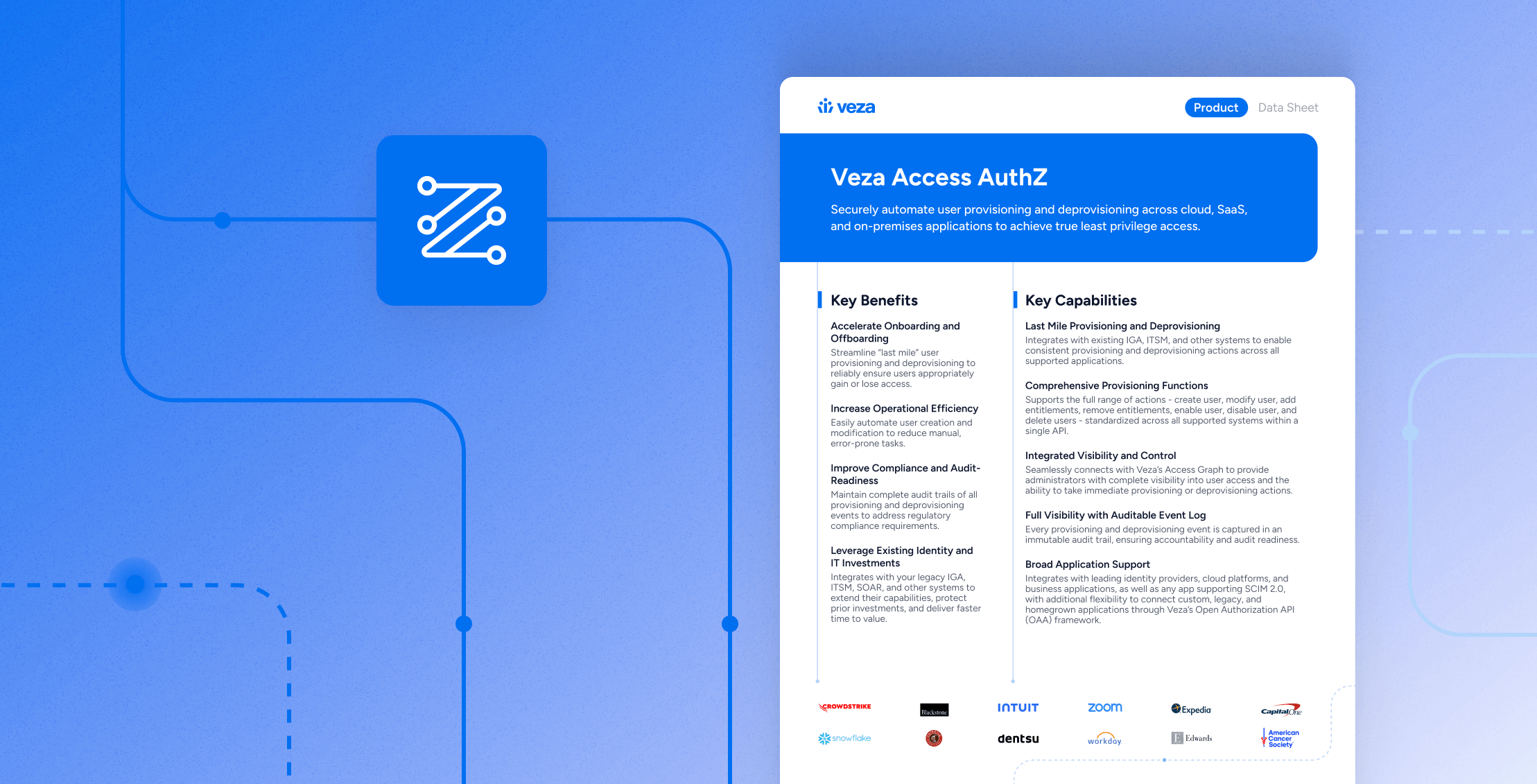
Automate the last mile of identity governance
Access AuthZ turns intent into action by automating access grants and revocations across cloud, SaaS, on-prem, and custom apps. Built on the Veza Access Graph and powered by the Open Authorization API (OAA), AuthZ closes provisioning gaps so every identity gets — and loses — the right access on time.
Why Access AuthZ
- Eliminate manual bottlenecks — Replace ticket queues and brittle provisioning scripts with automated access grants and revocations.
- Enforce intent beyond SCIM — Extensive native application and platform support, plus support for the universe of SCIM-based applications; additionally, reach legacy, custom, and homegrown applications through Veza’s flexible OAA Write framework.
- Operate with confidence — One model anchored by Veza’s Access Graph combined with end-to-end auditability.
- Accelerate IGA modernization — Reduce time to provision/deprovision and shrink access debt
See how AuthZ fits the platform in the Platform Overview.
What you’ll discover inside
- Last-mile provisioning and deprovision that standardizes create/modify/enable/disable/delete users and add/remove entitlements operations across applications, systems, and platforms through a single API.
- Unify visibility & control: One integration provides both visibility via the Access Graph (identities, entitlements, activity) and provisioning and deprovisioning capabilities.
- Full auditability with immutable logs for every operation to simplify compliance and forensics.
- Integration coverage across IdPs/directories, clouds, business apps, databases, and DevOps/IT ops — plus SCIM 2.0 and custom targets via OAA Write.
The datasheet includes a concise architecture view and a representative integration list.
With Access AuthZ, identity and security teams can automate the final step of access governance—ensuring that every identity, human or machine, always has the right access and nothing more.
How it works (at a glance)
- Enforce with AuthZ using native integrations, SCIM, and OAA to add, change, or remove user access consistently — even where out-of-the-box connectors stop.
- Reconcile & audit to verify results and prevent drift with evidence.
Learn the insight/decision side in the Access AI Data Sheet.
Outcomes
- Faster service delivery — Shorter time to grant/revoke access for users and service accounts
- Reduced operational overhead — Standardized automation replaces one-off scripts and swivel-chair work.
- Improved audit readiness — End-to-end evidence of what access was changed and when.
- Protect existing investments — Works with legacy IGA, ITSM, and SOAR platforms as well as homegrown applications to deliver time-to-value fast.
Who it’s for
IAM & IGA owners • Security & identity architects • Platform/app/data teams • Compliance & audit leaders