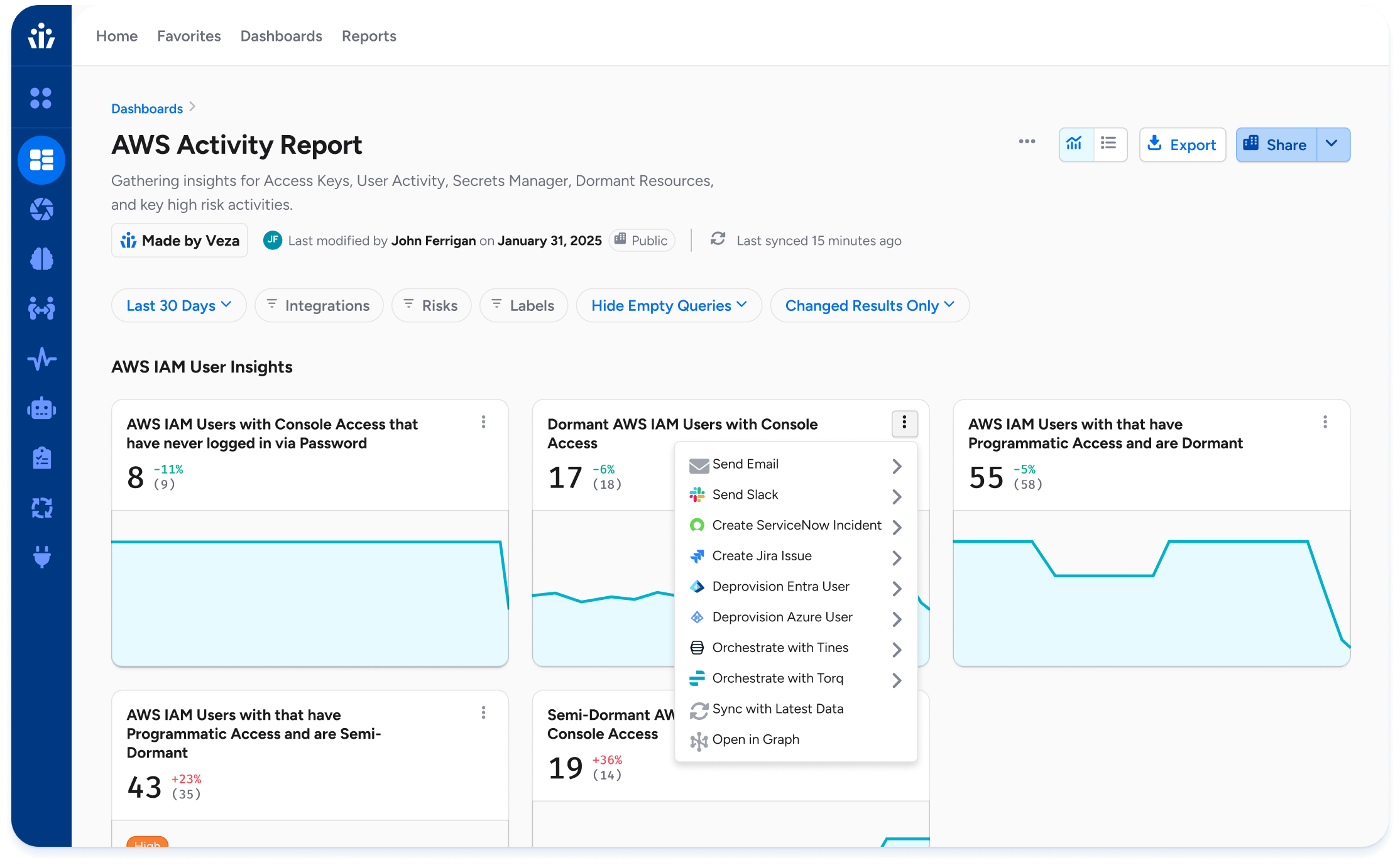
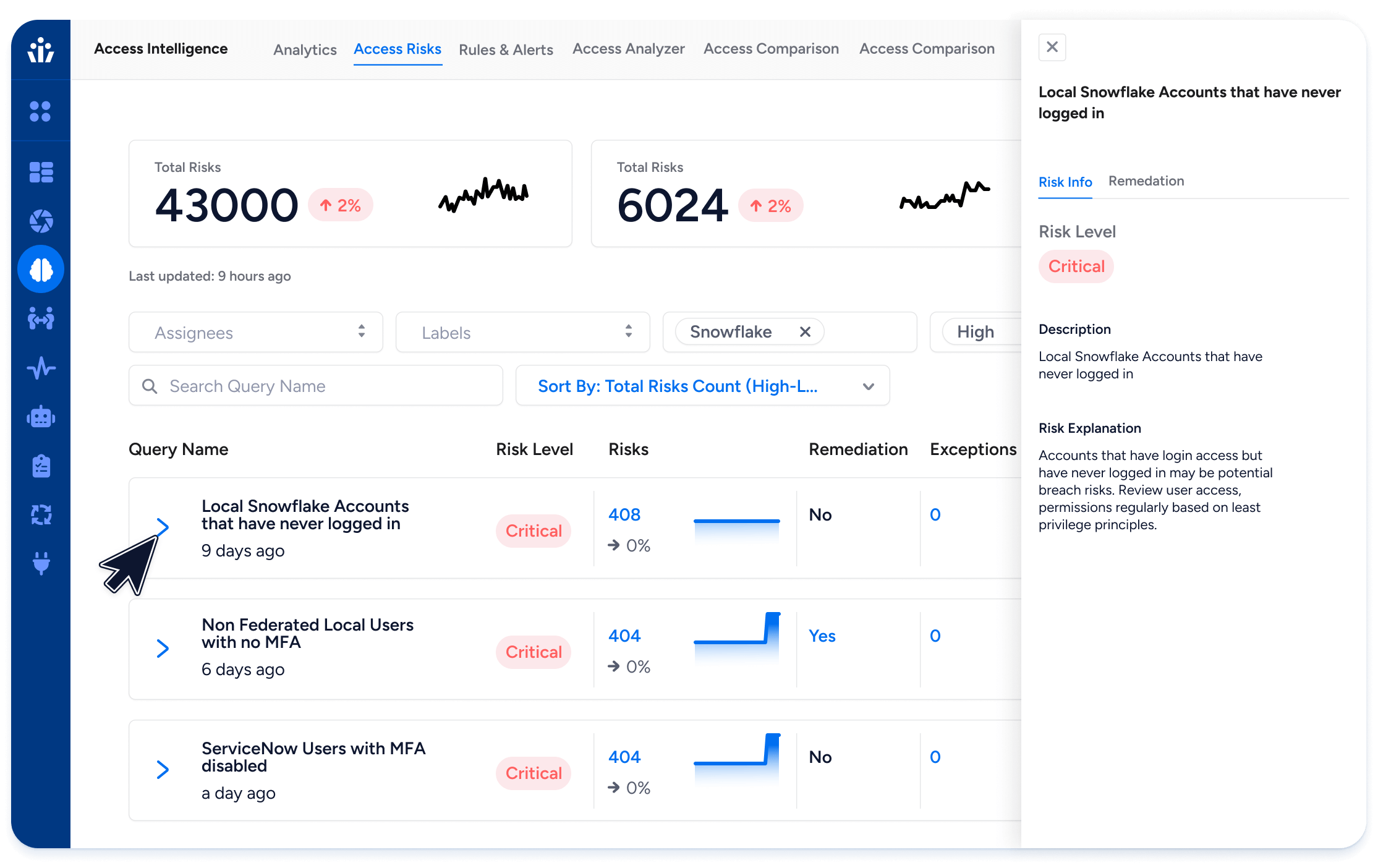
Access AuthZ
Automate the “Last Mile” of Identity Governance
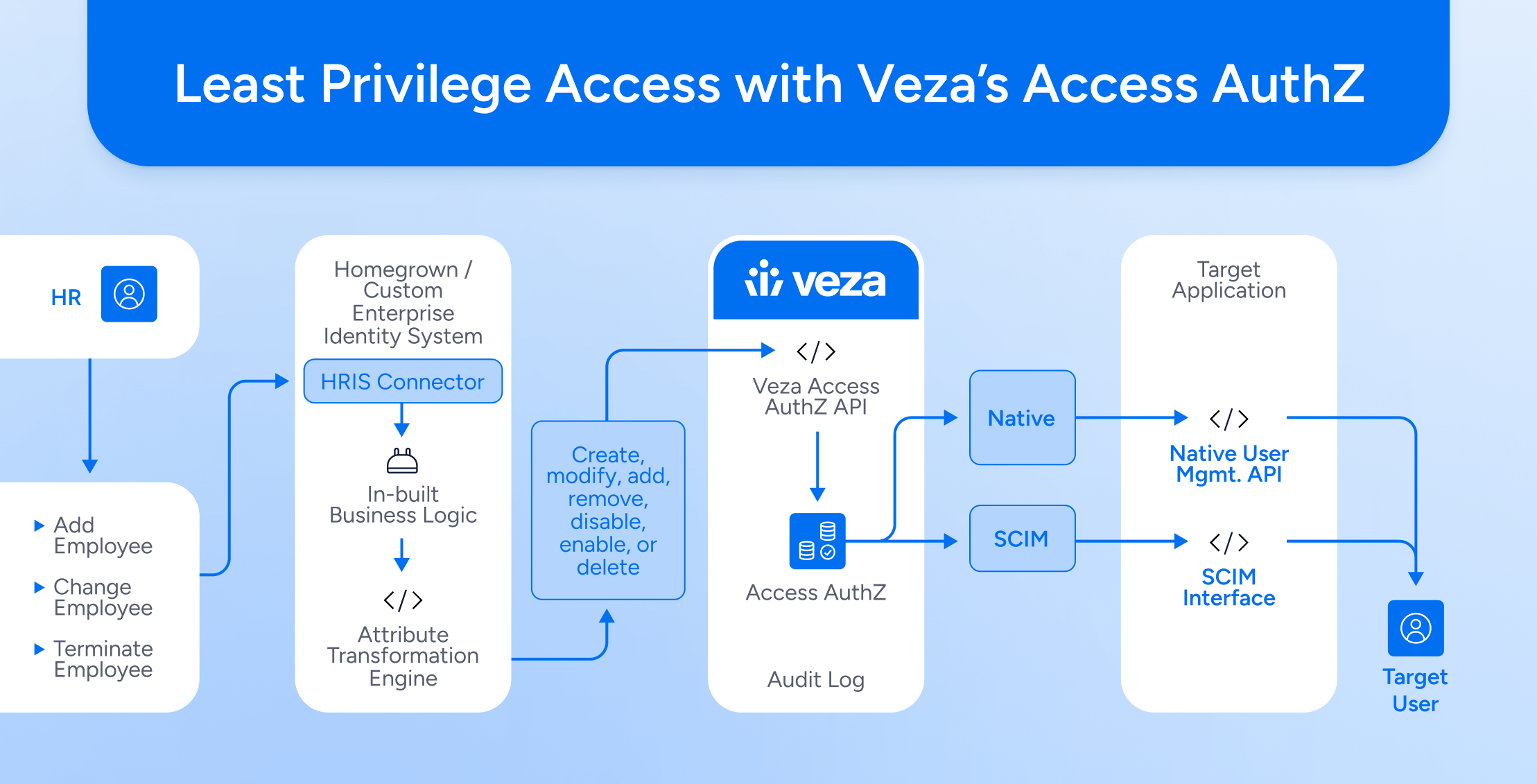
Bring automation to the point of enforcement. Veza Access AuthZ eliminates manual provisioning bottlenecks, so every identity, human or machine, gets the right access fast and loses it just as quickly when it’s no longer needed. Built on the Veza Access Graph, Access AuthZ gives enterprises the visibility, control, and automated execution needed to achieve true least privilege at scale.
Key Capabilities
How Access
AuthZ works
Ingest and normalize
Aggregate permissions and entitlements across clouds, SaaS, data systems, and directories into a single authorization model in the Platform Overview.
Decide with context
Optionally leverage risk, usage, and data context from the Veza platform to determine who should get what, and why. Align with modern visibility and intelligence practices outlined in the IVIP explainer, then preview blast radius before changes.
Enforce and reconcile at scale
Execute adds, changes, and revokes consistently through Access AuthZ. Reconcile target systems to the intended state and keep evidence synced for audits. See coverage in the Integrations overview.
Integration Ecosystem
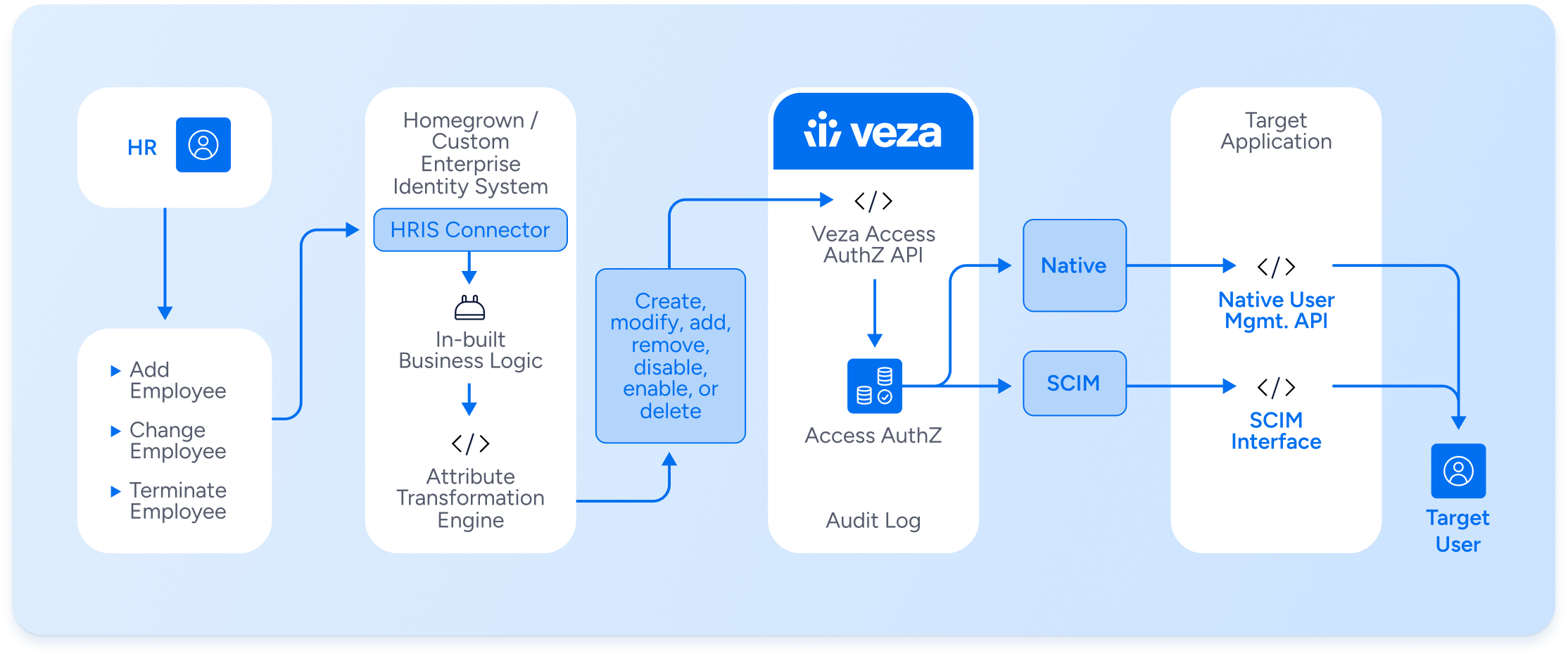
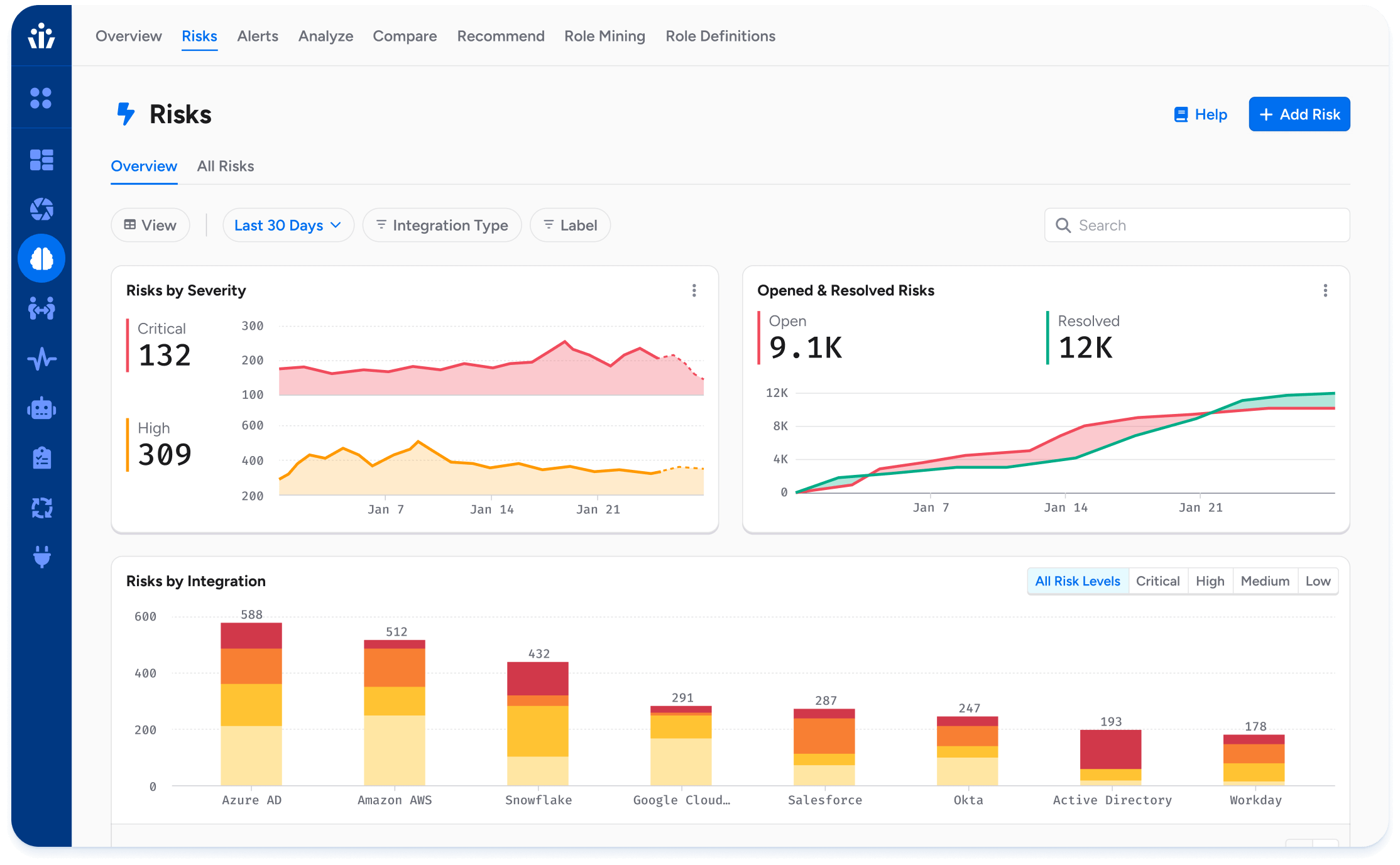
Outcomes
Use Cases
Empower Least Privilege, Everywhere
With Access AuthZ, identity and security teams can automate the final step of access governance, ensuring that every identity, human or machine, always has the right access and nothing more.