Glossary
-

Reflections from Gartner IAM London: Visibility Leads to Observability
Learn more -

GitHub OAuth Attack Alert: A Developer’s Worst Nightmare and How to Prevent It
Learn more -

Achieving DORA Compliance: A Practical Guide for Financial Organizations
Learn more -
How Veza Simplifies SOX Compliance: Automating Access Controls & SoD Monitoring
Learn more -

The Evolution of Identity and Security at Workday: Insights from CISO Josh DeFigueiredo
Learn more -
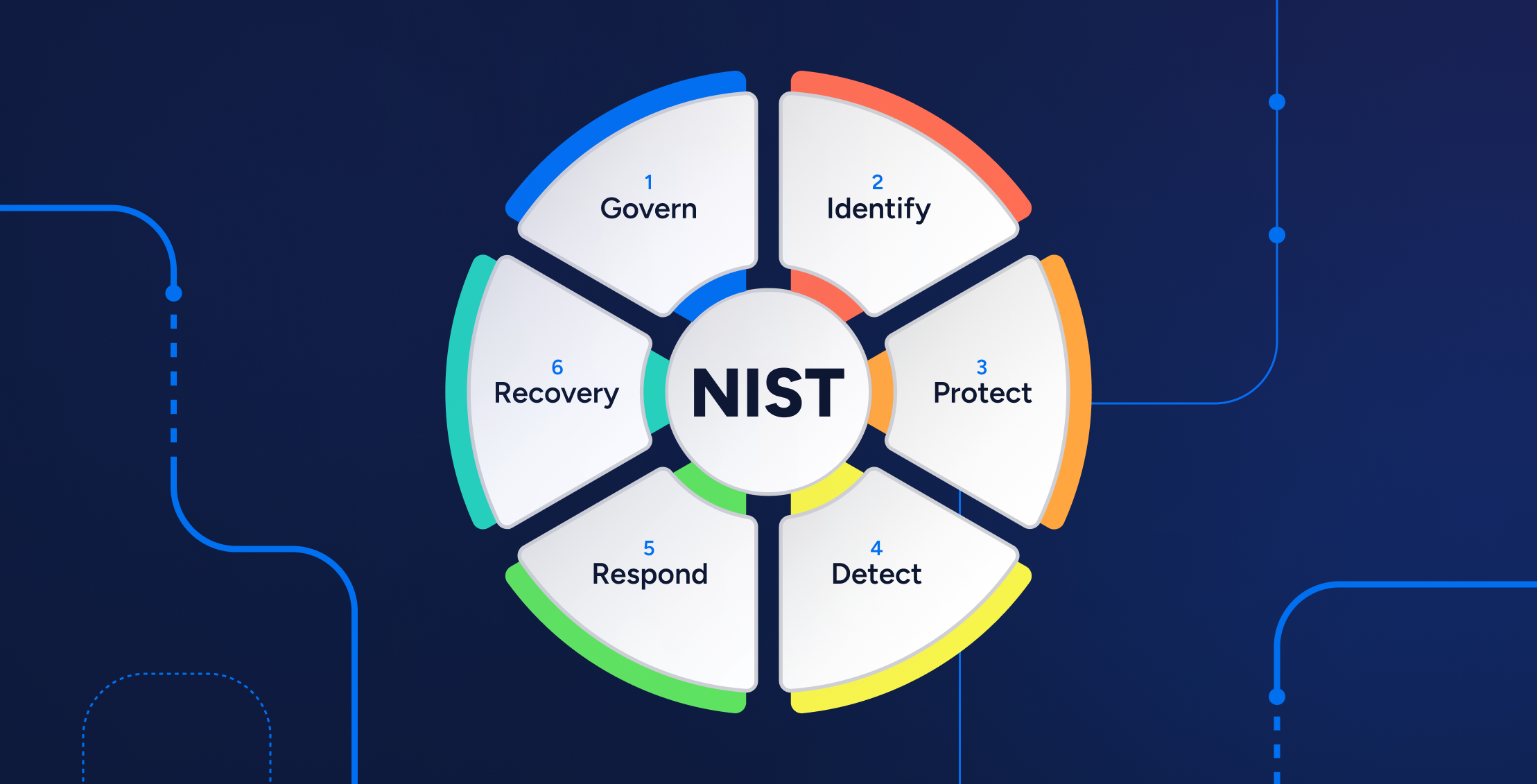
What is NIST Compliance? Guide & Checklist [2025]
Learn more