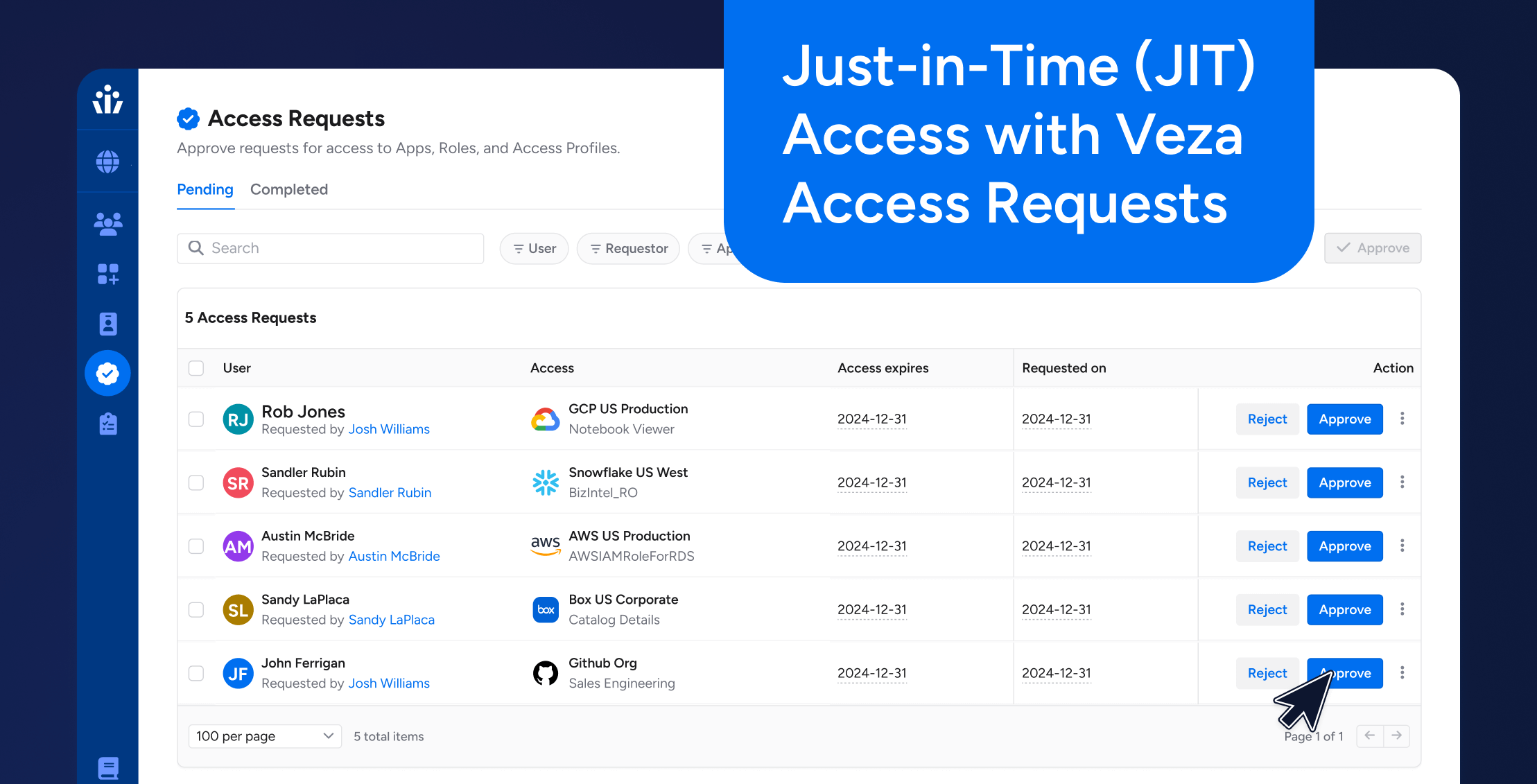
Glossary
-
Identity is Eating Security: Why Access Is the New Perimeter
Learn more -
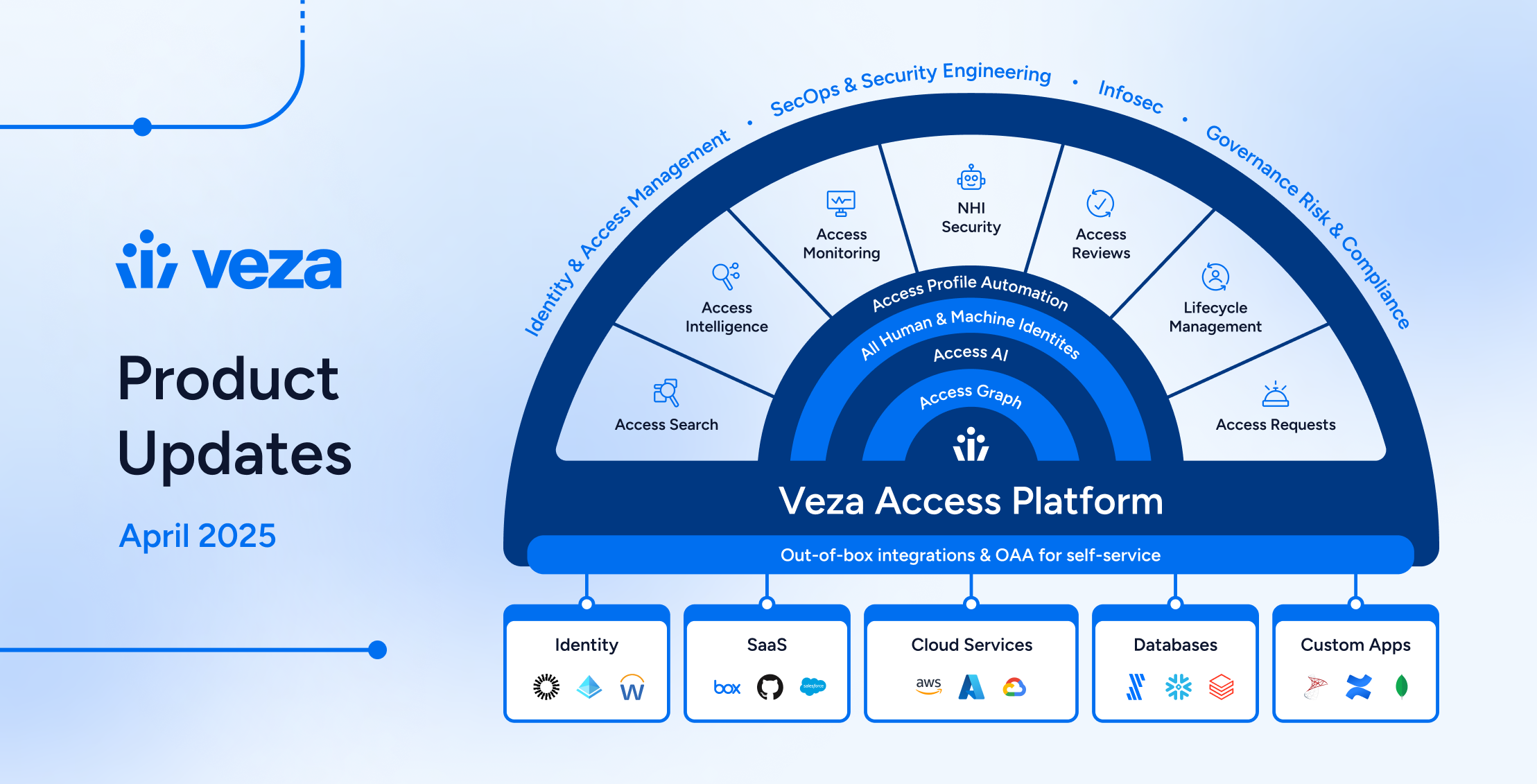
Veza Product Updates – April
Learn more -

Announcing Veza’s Series D: Securing Identities through Achieving Least Privilege
Learn more -

When Logging In Is the New Hacking: Nicole Perlroth on the Evolving Cyber Threat Landscape
Learn more -

What is non-human identity management
Learn more