Welcome to the Veza August 2025 Product Update! This month’s releases introduce new advancements across access governance and identity lifecycle management, with enhanced collaboration, reporting, and insights throughout the product.
Building on our commitment to making complex access challenges manageable, we’ve introduced AI-powered query capabilities, expanded Azure monitoring coverage, and strengthened compliance controls, while maintaining the security rigor demanded by enterprise customers.
Release highlights include:
AI-Powered Access Intelligence
- Natural Language Search for Query Builder – Access AI converts natural language questions into structured queries, making authorization analysis accessible to all users.
- Query Explanations with Access AI – Explanations for complex saved queries provide clarity on purpose, logic, and expected results directly from the query details view.
- Risk Profile Classifications – Enhanced 2,400+ out-of-the-box queries with systematic classifications across 8 risk categories (MFA Health, Privileged Access, Blast Radius, Dormant Access, Orphaned Access, Access Risks, Identity Hygiene, and Informational) for improved threat prioritization.
Enhanced Access Governance and Access Security
- Team-Based Dashboard Sharing – Share custom dashboards with specific teams, or with individuals via a direct email link.
- Query Change History and Audit Trail – Track the full before-and-after change history for Segregation of Duties and saved queries, including modifications to conditions and risk levels.
- Monthly Export Scheduling – Schedule query exports with granular monthly recurrence options.
- Enhanced Column Management – Administrators can now fully hide specific columns from reviewers for greater privacy and efficiency in Access Reviews.
- Default Group By Settings – Set default grouping behavior globally or per review configuration, with customizable collapse/expand behavior for reviewer efficiency.
Advanced Lifecycle Management and Automation
- Custom Attribute Transformers – Reusable transformation functions to replace complex pipelines with named macros for consistent attribute processing.
- APPEND and PREPEND Transformers – New attributes from combinations of existing values through string concatenation for dynamic construction of email addresses, usernames, and identifiers.
- Workflow Priority Configuration – Control execution order with six priority levels (Unset, Low, Normal, Medium, High, Critical) to ensure that critical provisioning operations execute first.
NHI Security and Visibility
- New NHI Overview Dashboard – New landing page organizing NHI accounts by type and integration, with owner management, credential age tracking, and trend analysis.
- Okta App User Classification – App Users now inherit identity type classification from corresponding Okta User accounts for accurate human versus non-human identification.
- Enhanced Identity Type Visualization – Color-coded badges in Access Graph distinguish human users (blue) and non-human identities (green) for clearer access path analysis.
Expanded Cloud Platform Coverage
- Azure Activity Monitoring – Extended Access Monitoring support to Microsoft Azure (Entra ID, Azure Roles, SharePoint Online) for visibility into active permission usage versus over-provisioning.
- AWS IAM Roles Anywhere – Discover workloads using temporary AWS credentials via X.509 certificate authentication, including trust anchors, certificate revocation lists, and profile mappings.
- AWS Systems Manager Parameter Store – Visibility into parameters and type classifications for PCI 4.0 compliance, including IAM permission hierarchies for parameters and KMS keys.
- AWS Certificate Manager – Track X.509 certificates used for authentication across AWS services with full lifecycle visibility.
- OIDC Identity Provider Support – Visibility into AWS identity federation via OpenID Connect providers.
See each section below for more information on specific updates, and please contact the Veza support team with your valued questions and feedback.
Access Intelligence
Enhanced Dashboards for Cross-Team Collaboration
Team-Based Dashboard Sharing: You can now share custom dashboards directly with specific teams or via email notifications through an intuitive sharing modal:
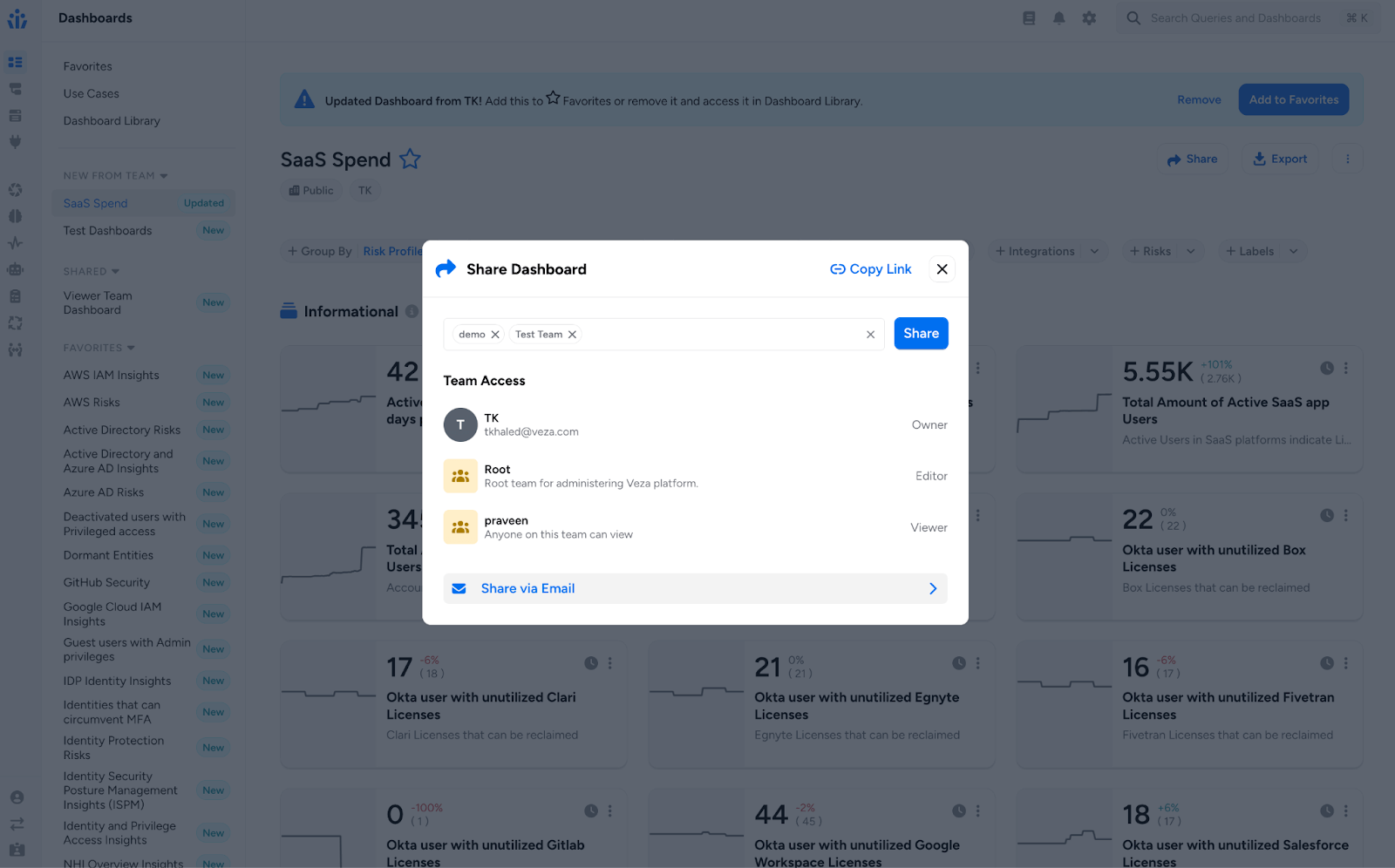
- Clicking Share when viewing dashboards now offers options for email or direct team sharing with intelligent validation.
- When sharing, you can preview which teams may have limited access due to integration restrictions. After sharing, dashboards are available in the recipients’ Shared Dashboards menu.
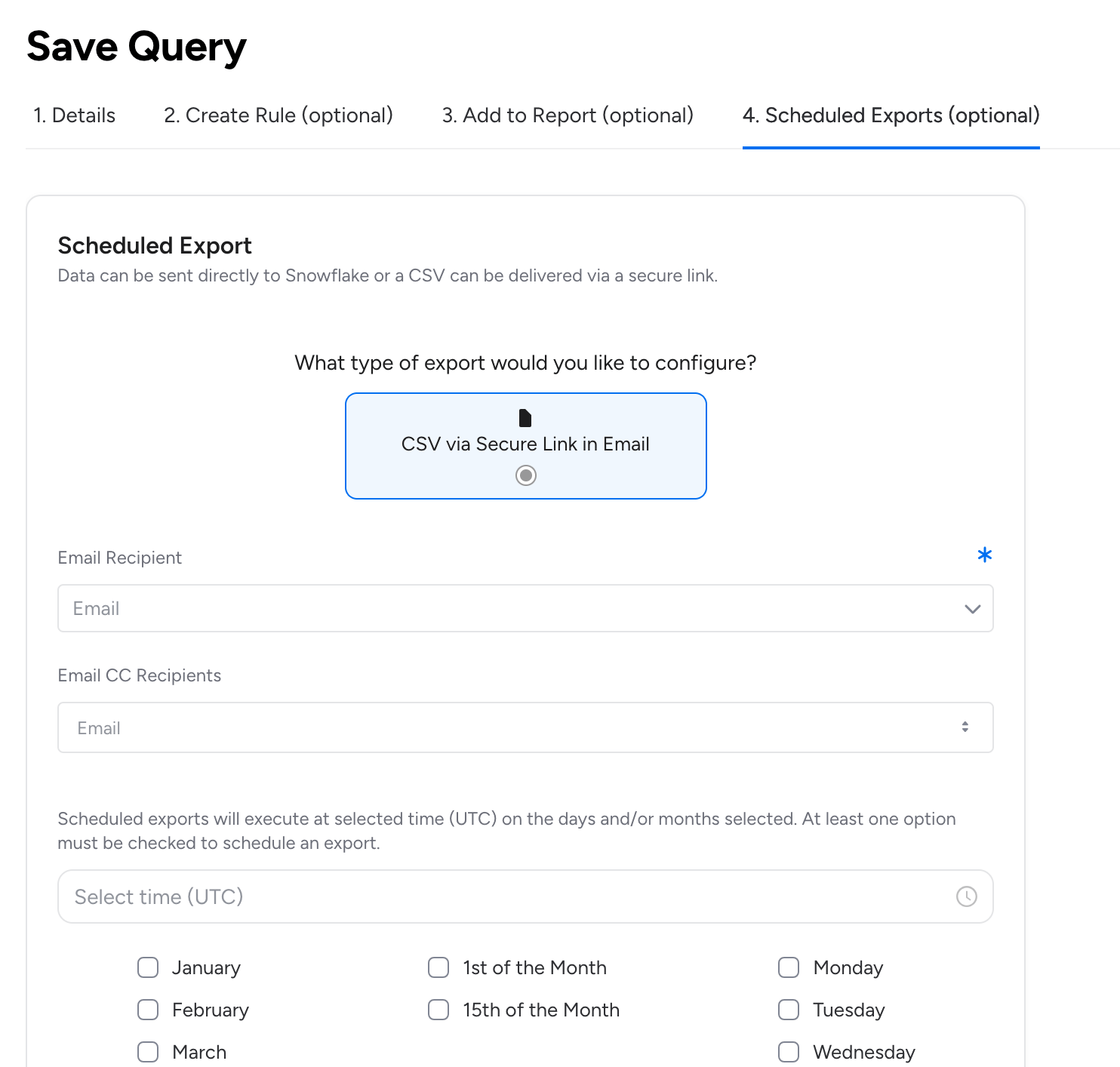
Enhanced Export Scheduling
Monthly Query Export Scheduling: Scheduled query exports now support monthly scheduling options in addition to the original weekly capabilities. You can now configure query exports to run on specific months of the year and choose between the 1st or 15th day, for greater flexibility with compliance reporting and periodic audits.
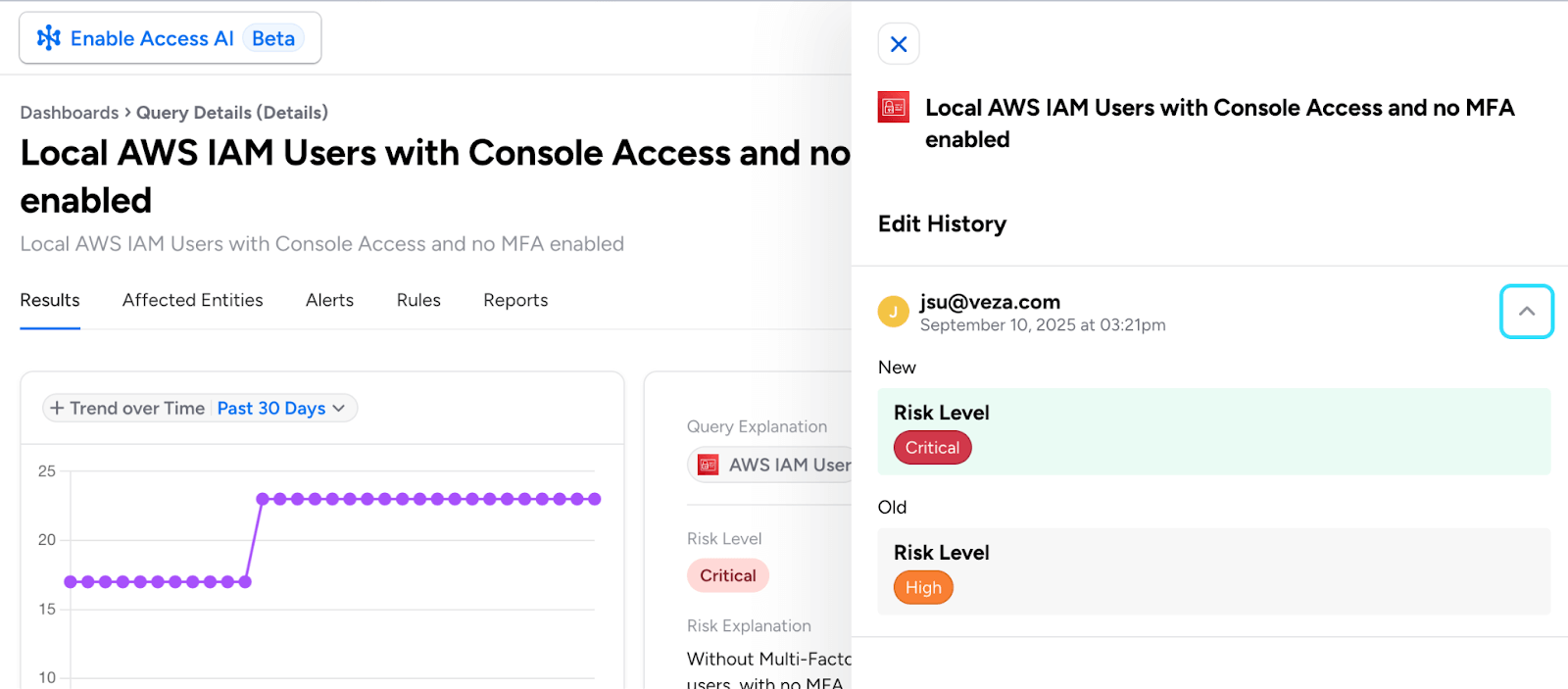
Query Change History and Audit Trail
You can now track changes to your critical security queries with the new Query Diff View available in saved query details. This new feature provides a complete audit trail for Segregation of Duties (SoD) queries and other saved searches, showing before-and-after comparisons of query conditions, names, descriptions, and risk levels.
Risk Intelligence
Risk Profile Classifications: Enhanced over 2,400 out-of-the-box queries with systematic Risk Profile classifications, organizing security findings into 8 distinct risk categories for improved threat prioritization and response.
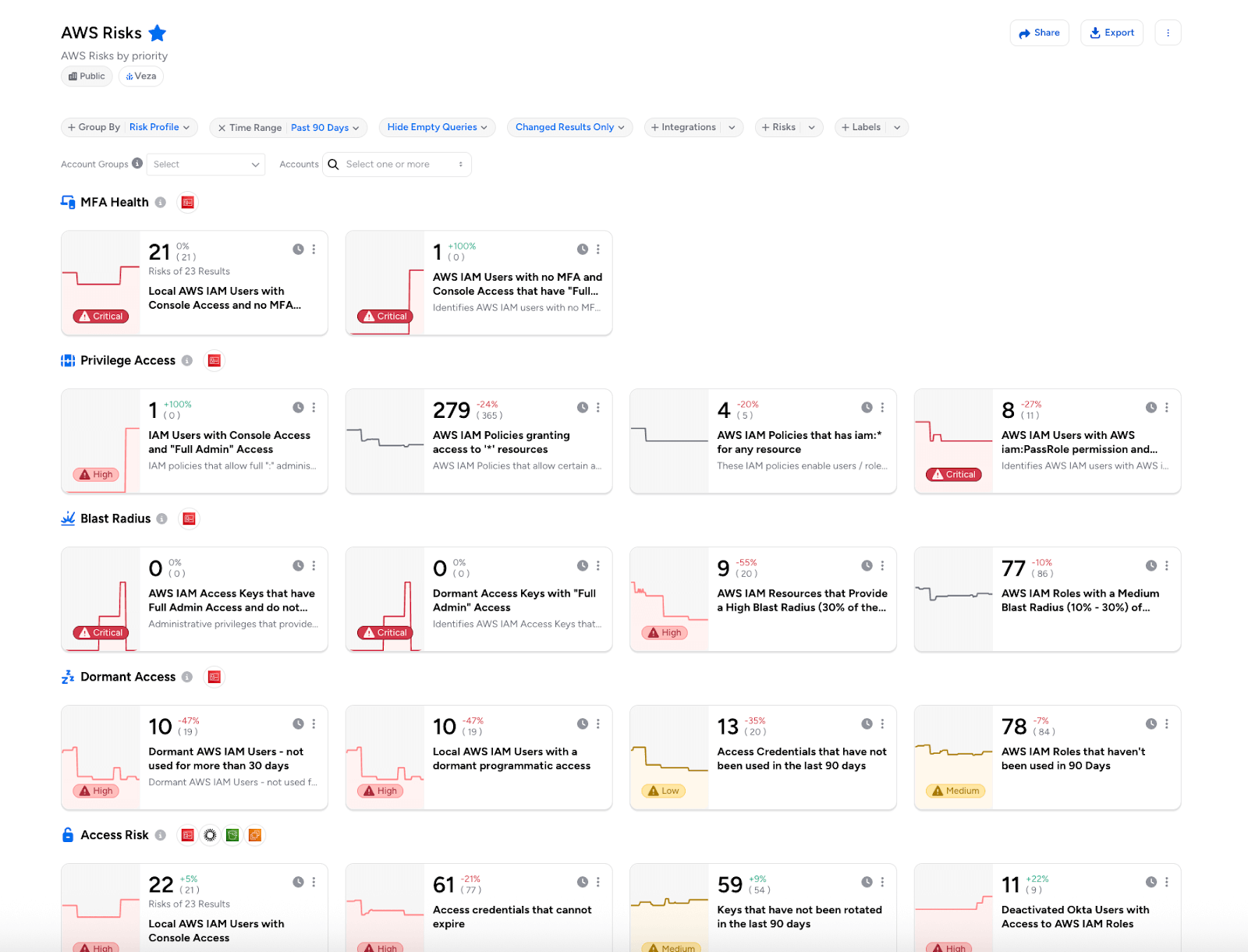
The new classification system spans:
- MFA Health: Identifies vulnerabilities in Multi-Factor Authentication implementation and enforcement
- Privileged Access: Excessive or high-impact privileges that could lead to significant damage if compromised
- Blast Radius: Quantifies the potential scope of impact from a single identity compromise, particularly for modifying or destructive permissions
- Dormant Access: Inactive identities (human and non-human) that retain access privileges despite extended periods of inactivity
- Orphaned Access: Local accounts on applications and data stores not governed by central identity management systems
- Access Risks: Captures specific known risk patterns and configurations not covered by other classifications
- Identity Hygiene: Evaluates identity management best practices, focusing on configuration cleanliness and orderliness
- Informational: Provides non-risk metrics, including counts of users, roles, resources, and groups.
This update enables consistent risk categorization across all Access Intelligence dashboards and reports, helping security teams to quickly identify and prioritize identity and access risks in their environment.
Design and Usability Enhancements (Early Access)
- Critical Risk Focus: Veza dashboards now automatically preselect the “Critical” risk level filter upon login, helping teams focus on the highest-priority security findings without manual configuration.
- Dashboard Group By Filter Improvements: To provide users with better analysis context out of the box, dashboard filters now group tiles by “Risk Profile” by default, and use “Past 90 days” as the default time range.
Access Monitoring
Azure Activity Monitoring: Veza Access Monitoring capabilities now support Microsoft Azure (including Entra ID, Azure Roles, and SharePoint Online), providing visibility into which Azure AD identities are actively using their assigned permissions versus those that may be over-privileged.
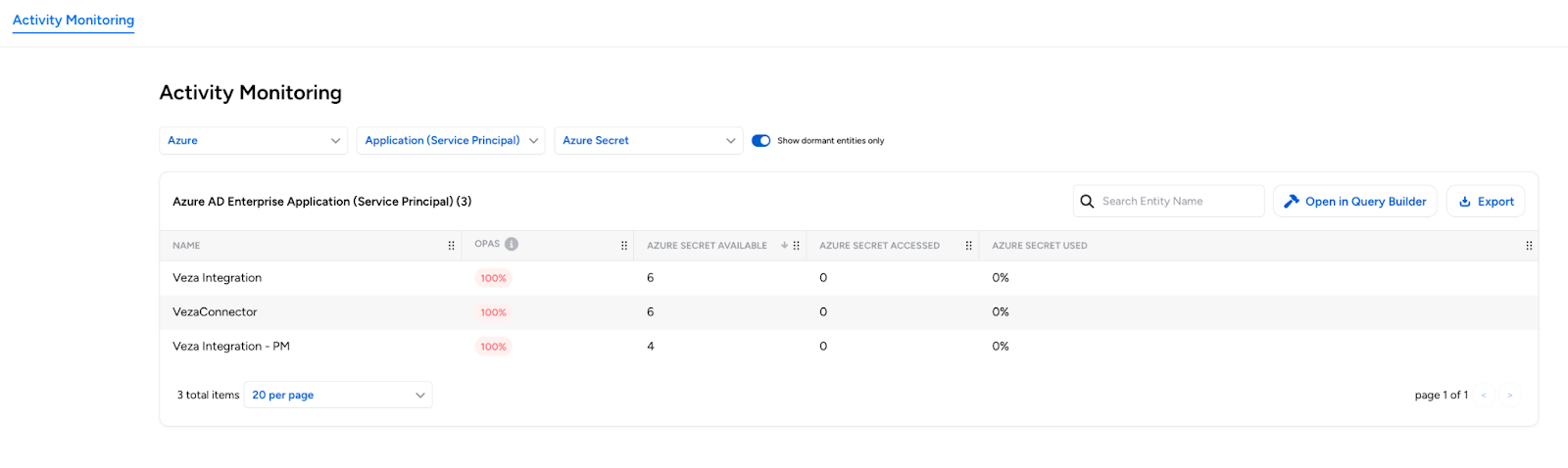
This expansion complements existing support for AWS, Snowflake, Google Cloud BigQuery, Okta, and SharePoint, helping organizations to track and audit user activities across the entire ecosystem.
Access AI
Natural Language Search for Query Builder (Early Access)
Query Builder now includes Access AI integration, enabling natural language search capabilities that automatically convert your questions into structured queries. This feature leverages the same Access AI engine that powers Graph Search, making complex authorization queries more intuitive and accessible to all users.

How to use it: Simply start typing natural language questions in the search field, and Access AI will construct the appropriate query with entity types and filters based on your input. For example, ask “Show me all AWS IAM users who can delete a particular S3 Bucket,” and Access AI will build the corresponding query.
{% hint style=”info” %} Access AI is currently in Early Access. Contact your Veza support team to enable this capability for your tenant. {% endhint %}
Query Intelligence with Access AI
Query Explanations with Access AI: You can now get instant explanations for complex saved queries directly from the query details view. Click the new Access AI button when viewing saved query details to get an overview of the query’s purpose, logic, and expected results, making even the most complex authorization queries easier to understand and troubleshoot.
Access Visibility
Advanced Query Builder Options
Query Builder has received several enhancements:
- Path Type Selection: You can now choose between “Permission” paths (following only permission-granting relationships) and “Non-Permission” paths (following organizational or structural relationships) for more precise source and destination entity searches
- Automatic Permission Summarization: When using “Relates To” options, columns now display summarized Effective and System permissions, providing immediate visibility into both raw permissions and calculated effective access.
- Relationship Direction Control: You can now specify whether queries show incoming relationships (entities pointing toward the source), outgoing relationships (entities the source points to), or any direction.
- API Enhancement: Queries of the SOURCE_NODES_WITH_COUNTS type now support the `include_permission_summary` option, returning a summary of effective access and system-level permissions in the API response.
Enhanced Graph Visualization
Identity Type Visual Indicators in Authorization Graph: We’ve made it easier to visually distinguish identity types when exploring access paths and authorization relationships. Identity nodes in Access Graph now display color-coded badges, blue for human users and green for non-human identities (service accounts, bots, API keys).
Access Graph Path Controls: Graph Search now supports the same advanced query options available in Query Builder. You can now specify “Direction Options” (Outgoing, Incoming, or Any Direction) and “Path Type Options” (Permission, Non-Permission, or Any) under advanced search options.
Access Reviews
Streamlined Review Experience
Enhanced Column Management: The new Admin > Manage Columns option for individual reviews allows administrators to exclude specific columns in the Reviewer Interface. This complements the existing option to hide columns by default, and removes the selected columns entirely from reviewer availability, ensuring sensitive or irrelevant data fields remain out of sight.
XLSX Reports: It’s now possible to generate consolidated Excel workbooks across multiple access reviews in a single file, for easier compliance reporting and audit preparation.
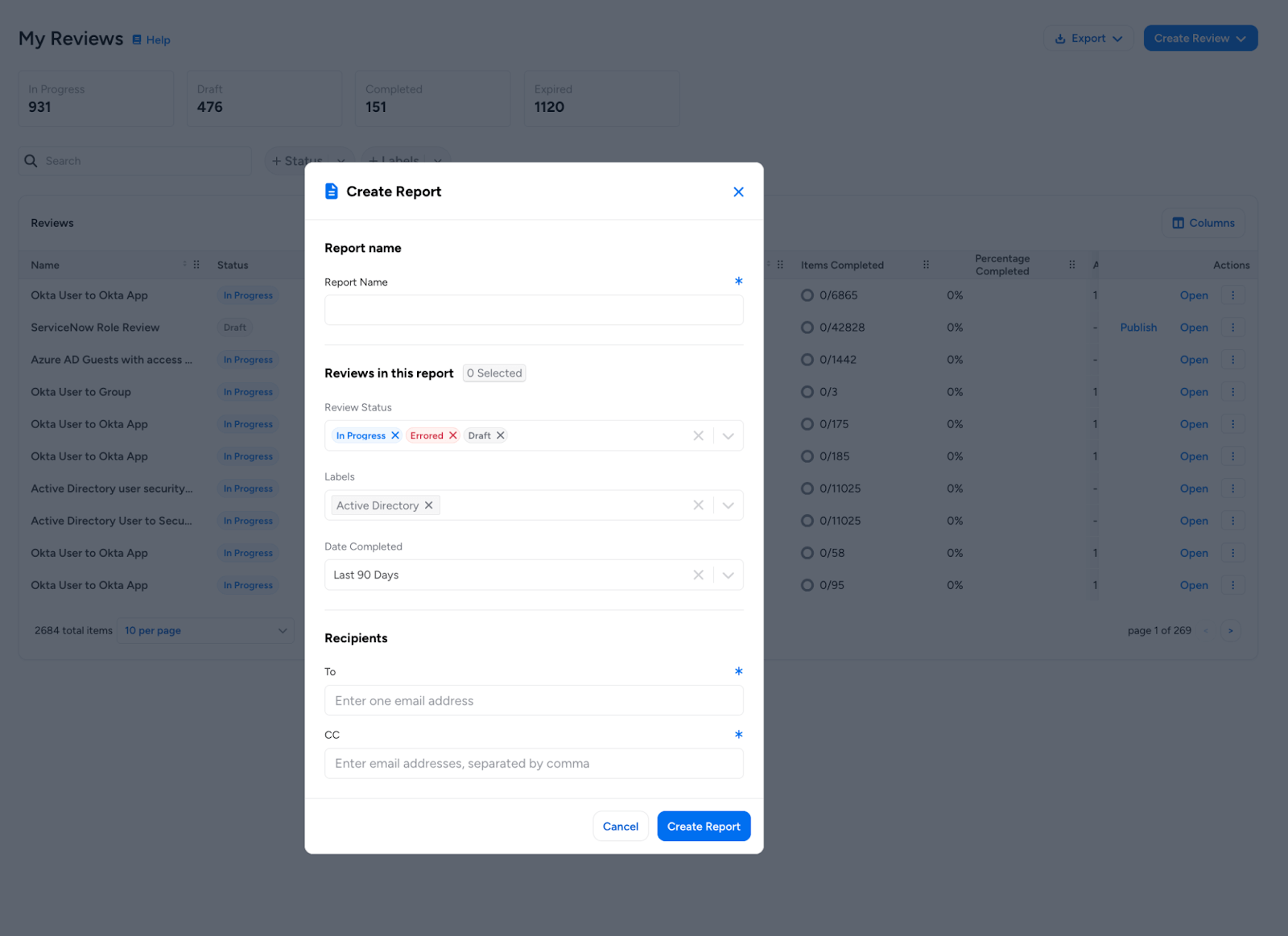
Default Group By Settings: Administrators can now set the default grouping behavior for access reviews both globally and per review configuration. This enables customization of the default grouping column (e.g., Source, Destination, or Risk Level) and whether rows are automatically collapsed/expanded.
In the reviewer interface, all review items are now automatically organized according to these settings for improved review efficiency. Admins can now set their current column customizations (including group by settings) as the default for all users via the Admin menu.
One-Click Risk Score Details: Clicking a source or destination Risk Score in an Access Review now automatically opens the Risks tab for insights into the contributing risks for that entity. This eliminates the need for multiple clicks and provides reviewers with access to full risk context in a single view.
Access Requests
Intelligent Approval Workflows
Skip Inactive Approvers: Access Request policies now intelligently handle inactive approvers. When all approvers at a particular step are inactive, the workflow automatically skips to the next approval level. This prevents requests from stalling due to departed or inactive personnel. Administrators can configure per-step using the new skip_inactive_approvers setting (API-only configuration).
Smart Auto-Revocation Notifications: To prevent duplicated notifications, automatic emails for auto-revocation triggered by Access Reviews are now disabled by default. Administrators in new Veza environments must now explicitly configure notifications in Access Request Settings, depending on their communication needs.
Lifecycle Management
Advanced Attribute Transformation
Custom Attribute Transformers: You can now create reusable attribute transformation logic using custom functions to replace complex transformer pipelines. It’s now possible to define a custom transformer (such as $CLEAN) within a Lifecycle Management Policy and use it throughout that version. For example, $CLEAN might combine ASCII | LOWER | REMOVE_CHAR, “.@,” into a single reusable function to normalize attributes before writing to the destination system.
APPEND and PREPEND Transformers: Attribute transformations now support string concatenation capabilities for creating new attributes from combinations of existing values. For example:
- Construct email address from first and last name: {first_name | APPEND, “.” | APPEND, “{last_name}”}@company.com → john.smith@company.com
- {location | PREPEND, “CORP_”} → CORP_NYC
- You can append or prepend logic in combination with other transformers to populate any target attribute, such as user name, email addresses, etc.
NEXT_NUMBER Enhancement: The NEXT_NUMBER transformer now supports an optional maximum length parameter. When enabled, this option will automatically truncate the base string before appending numerical suffixes.
Workflow Orchestration
Workflow Priority Configuration: You can now control workflow execution order within a Policy via six priority levels: “Unset”, “Low”, “Normal”, “Medium”, “High”, and “Critical”.
When multiple workflows trigger simultaneously, the highest-priority tasks execute first, helping ensure that critical provisioning and deprovisioning operations take precedence over other operations.
Property Mapping Visibility: For better insight into how entity attributes in Veza Access Graph correspond to the original attributes in integrated systems, API responses containing synced attribute definitions now include a `native_name` field with the actual system properties (e.g., “mail” in Active Directory).
This information can be useful when configuring attribute mappings or debugging unexpected or failed transformations.
Enhanced User Experience
Common Synced Attributes Ordering: The policy editor now supports precise sequencing of common synced attributes with drag-and-drop reordering. This enables prioritizing which common synced attributes are applied when synchronizing identities.Dynamic Integration Icons: Enhanced the Lifecycle Management Identities view with icons to indicate the active source of identity. This provides better visual clarity into which system is currently managing each identity’s attributes, especially when multiple sources of identity are configured for the policy.
Non-Human Identity (NHI) Security
Enhanced NHI Visibility and Management
New NHI Overview Dashboard: We’ve introduced a comprehensive Overview page for Non-Human Identities that provides improved visibility into your organization’s service accounts and automated identities.
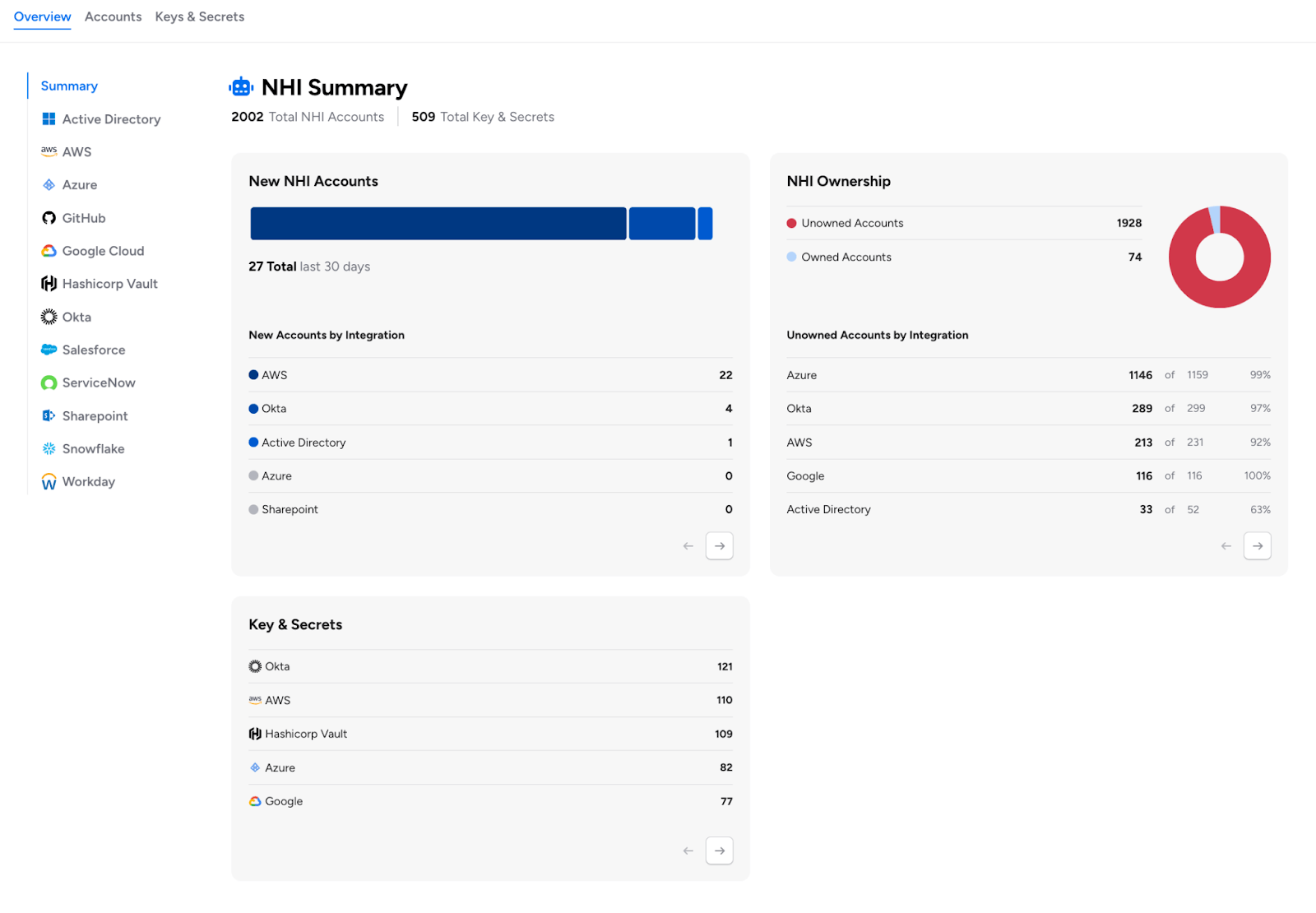
This new landing page offers:
- NHI Discovery & Visualization: View NHI accounts organized by both NHI type and integration type across all Veza integrations
- Human-to-NHI Owner Mapping: Filters to identify which users own NHI accounts for accountability and governance
- NHI Age Tracking: Monitoring for NHI credential lifetime to identify stale or risky accounts
- User Access Reviews for NHIs: Quick options to review and certify NHI permissions
- Historic Analysis: Trends and changes over the selected date range
Okta App User Identity Classification: Improved Okta App User identity classification to inherit the identity type from the Okta App User’s corresponding Okta User account.
- When an associated Okta User exists, the App User now automatically adopts the same identity type classification (human or non-human).
- For App Users without corresponding Okta User accounts, Veza defaults to marking them as human identities.
Access Hub
Administrative Controls for Improved Manager Experience
Manager View Configuration: Administrators can now customize the My Team view in Access Hub with configurable filtering to exclude Non-Human Identities and contractors from appearing in lists of direct reports. The settings page now provides options to specify properties and values to identify specific worker types to exclude, helping managers focus exclusively on human direct reports in Access Hub.
Veza Integrations
Expanded AWS Security Coverage
- AWS IAM Roles Anywhere: The AWS Integration can now discover workloads running outside of AWS with temporary AWS credentials using X.509 certificate-based authentication instead of long-term access keys. The AWS IAM Roles Anywhere service maps trust anchors, certificate revocation lists, and profiles to their associated permission sets.
- AWS Systems Manager Parameter Store: Added support for AWS Parameter Store to help meet PCI 4.0 compliance requirements. Veza now extracts parameters with type classifications (`SecureString` indicates secrets) and parses the hierarchy of IAM permissions for parameters and KMS keys.
- Required permissions: `ssm:DescribeParameters` and `ssm:ListTagsForResource`
- AWS Certificate Manager Support: Added discovery and tracking of X.509 certificates used for authentication across AWS services, including certificates used with IAM Roles Anywhere.
- Certificate discovery requires additional IAM permissions: `acm:ListCertificates`, `acm:DescribeCertificate`, `acm:ListTagsForCertificate`.
- IAM Access Key Permissions: Veza now discovers and displays both system and effective permissions for AWS IAM Access Keys, providing complete visibility into programmatic access patterns.
- Neptune Graph Database Discovery: The AWS integration now extracts Neptune Global Databases, Neptune Clusters, and Neptune Instances, providing visibility into graph database infrastructure and access patterns.
- Neptune discovery requires `rds:DescribeGlobalClusters` permission in your AWS-Veza integration trust policy.
- OIDC Identity Provider Support: Veza now supports AWS identity federation with OIDC provider extraction. Organizations using OpenID Connect for AWS access can now use the AWS integration for visibility into external identity relationships (previously supported exclusively for SAML identity providers).
Enterprise Integration Enhancements
- Veza: The built-in Veza integration now includes entity types: Veza Auth Group and Veza Role Mapping for visibility into how external SSO groups map to Veza teams and roles for federated identities. This enables search, access reviews, and alerting based on authorization chains from external IdP groups to Veza teams and roles.
- Cassandra: Integration configurations now support connections using TLS encryption and custom CA certificates.
- Improved Identity Status Detection:
- Okta: `SUSPENDED` users are now marked as inactive alongside `DEPROVISIONED` users.
- Google Workspace: “Archived” and “Suspended” accounts are now correctly marked as inactive.
Veza Platform
Enhanced Monitoring for Veza Platform Events
- Platform Event Alert Subscriptions can now use Veza Actions for ServiceNow and Webhooks as the delivery method. This can enable ticket creation or downstream automations when specific platform events occur (such as when an Insight Point is unavailable or an integration extraction fails).
- Veza now emits a `DATASOURCE_EXTRACTED_NO_CHANGE` event when an extraction runs for an integration, but results in no data changes.
- Veza now emits an `INSIGHT_POINT_DEGRADED` event when an Insight Point has partial connectivity (indicating some HA replicas/instances of this Insight Point are online, while others are offline).
- Custom SMTP email configurations now support OAuth 2.0 authentication for Microsoft 365, providing a secure authentication method for customers sending emails from their own domains.






