-
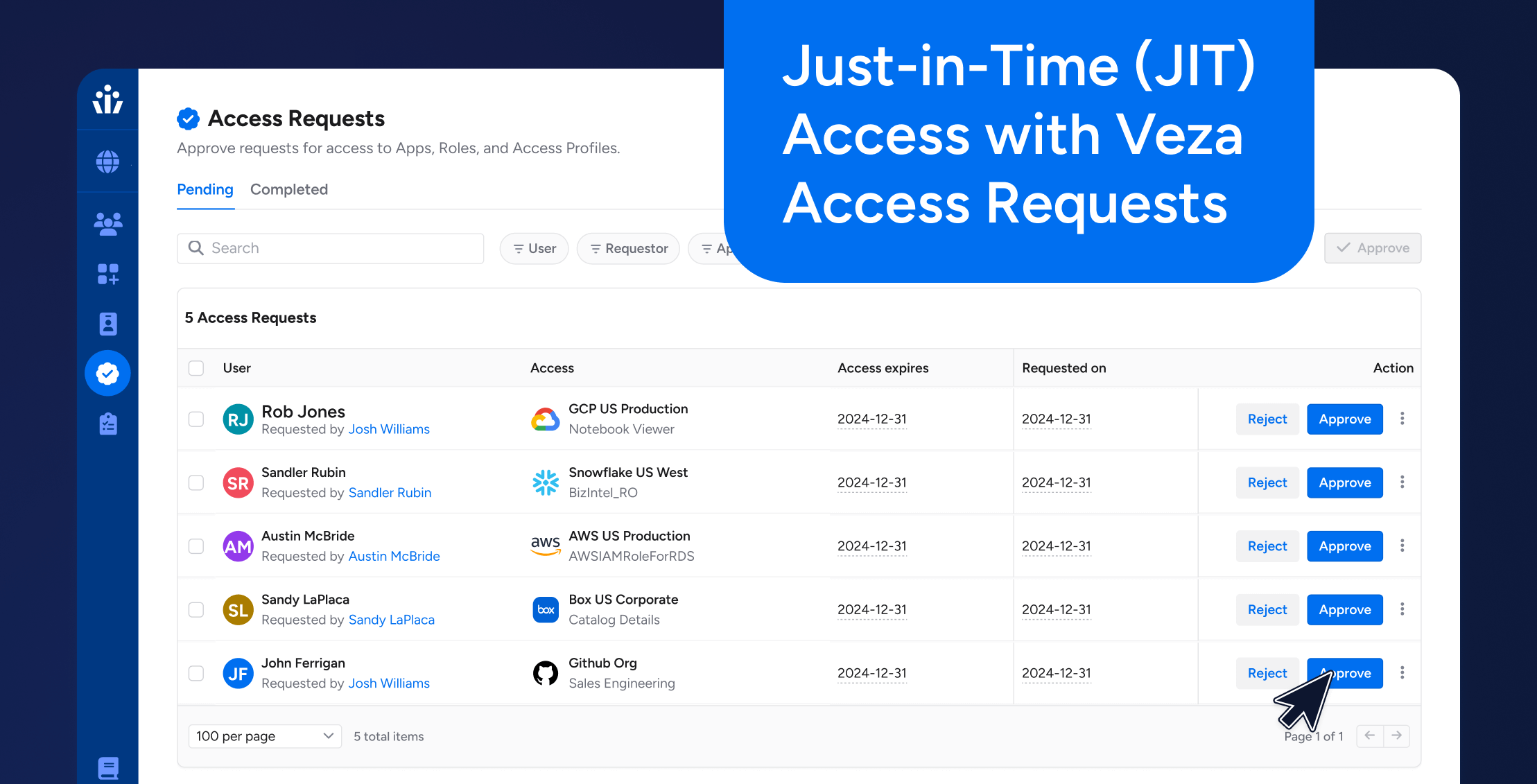
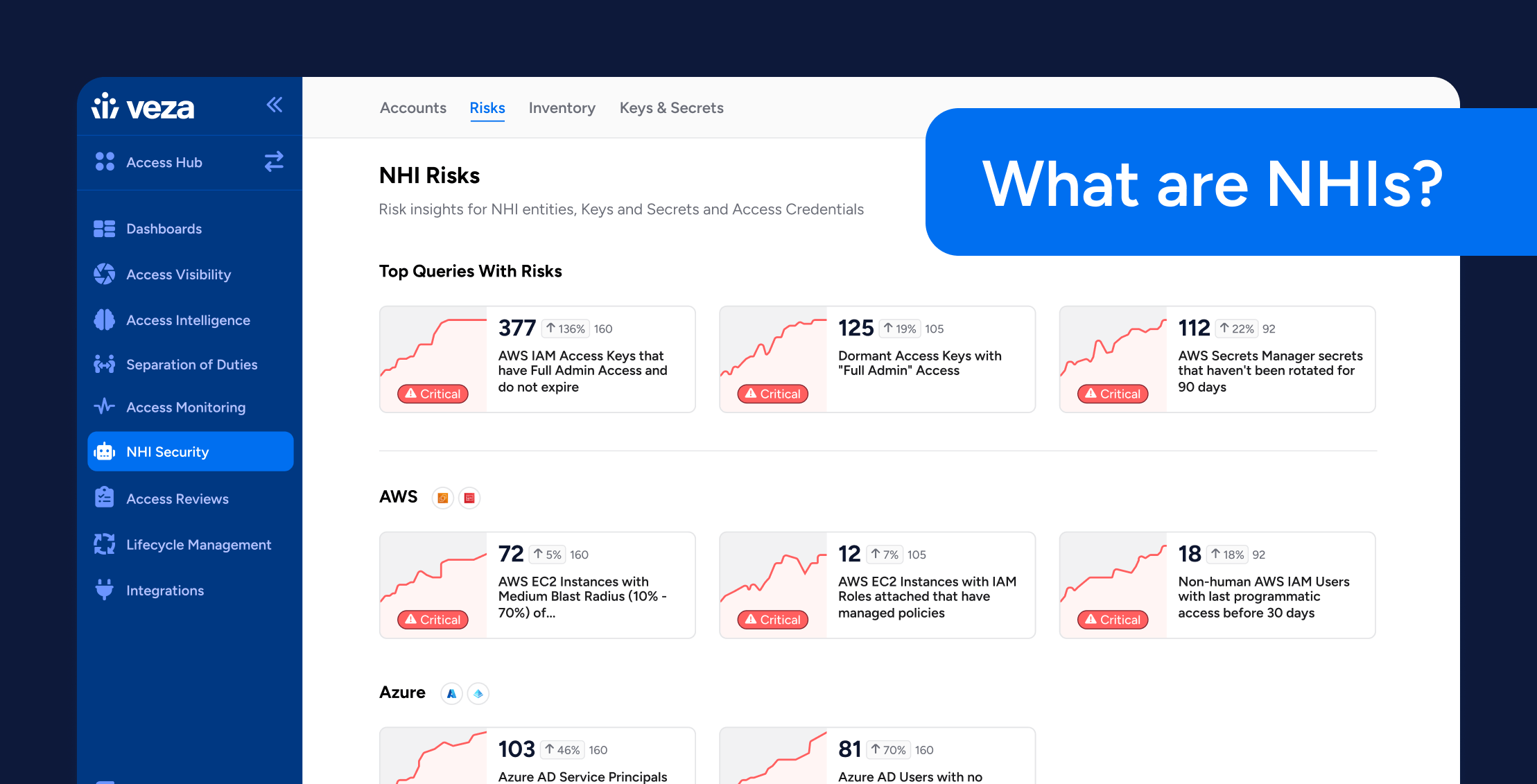 IAM
IAMWhat Are Non-Human Identities?
Learn more -
 IAM
IAMIdentity is Eating Security: Why Access Is the New Perimeter
Learn more -
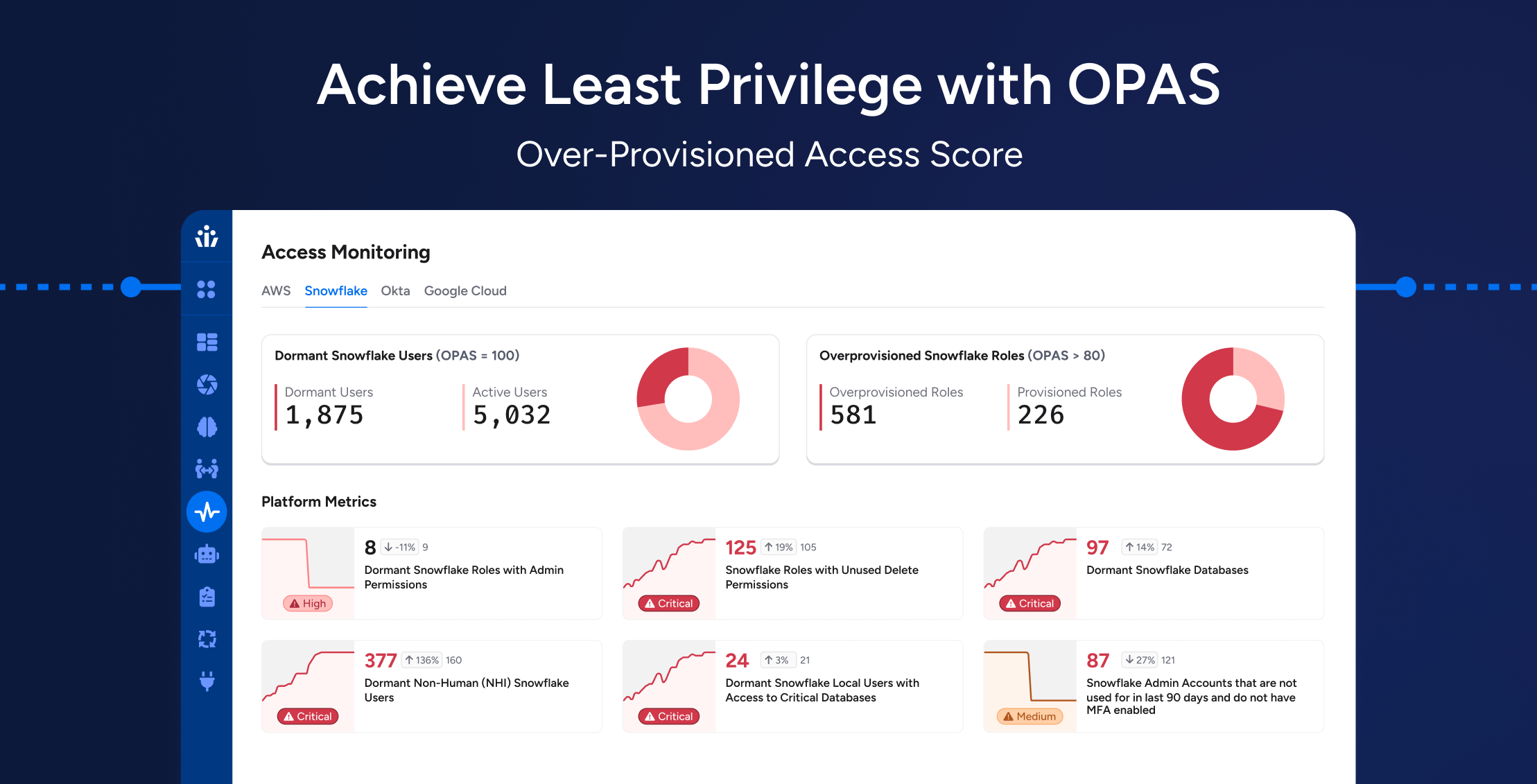 Compliance
ComplianceAchieving Least Privilege at Scale: How OPAS Helps Enterprises Reduce Hidden Access Risks
Learn more -
 Identity Radicals
Identity RadicalsWhen Logging In Is the New Hacking: Nicole Perlroth on the Evolving Cyber Threat Landscape
Learn more -
 Compliance
ComplianceSimplifying CMMC 2.0 Compliance: Modern Access Control Strategies for Government Contractors
Learn more -
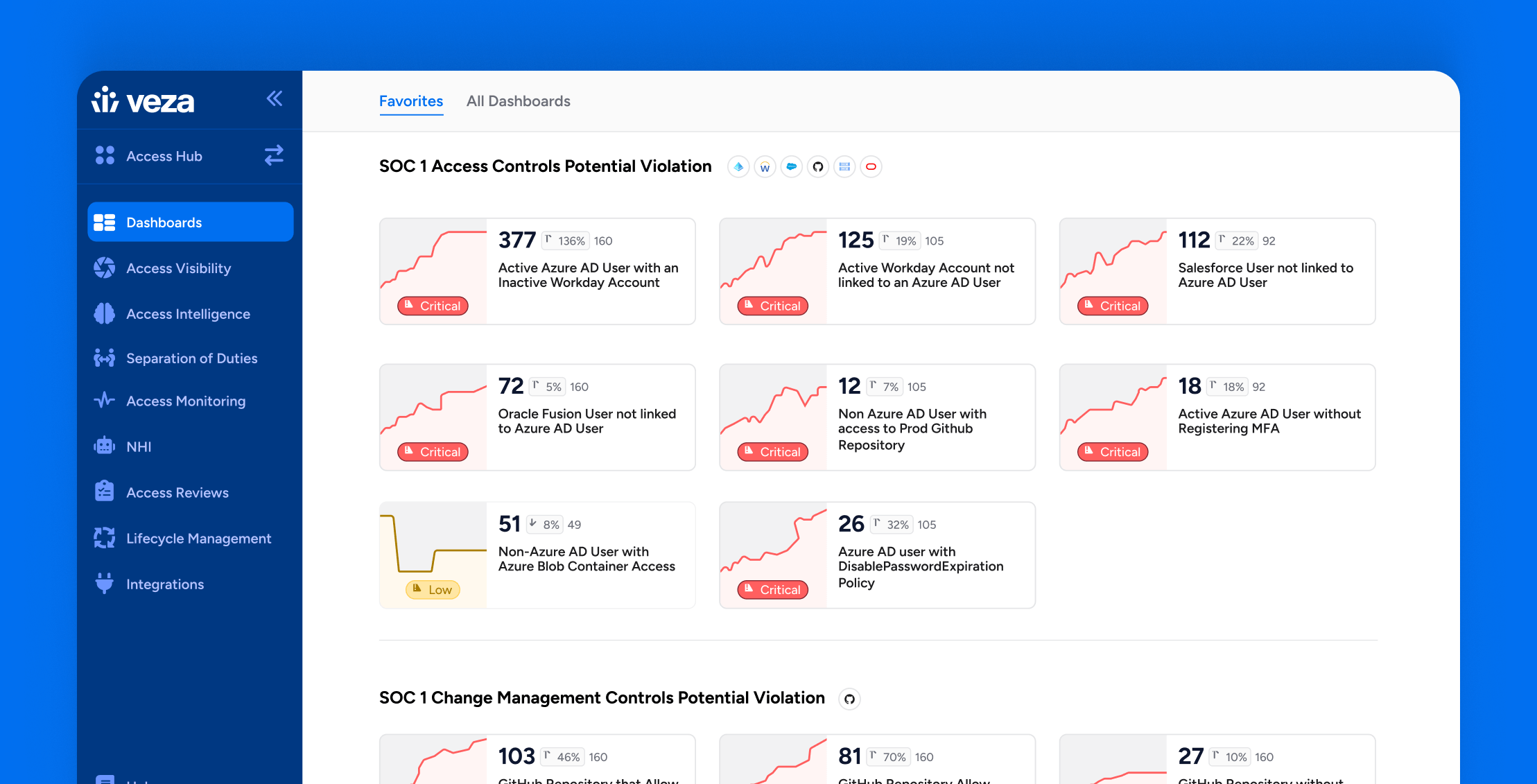 Compliance
ComplianceHow Veza Strengthens SOC 1 Compliance: Common Control Failures & How to Fix Them
Learn more -
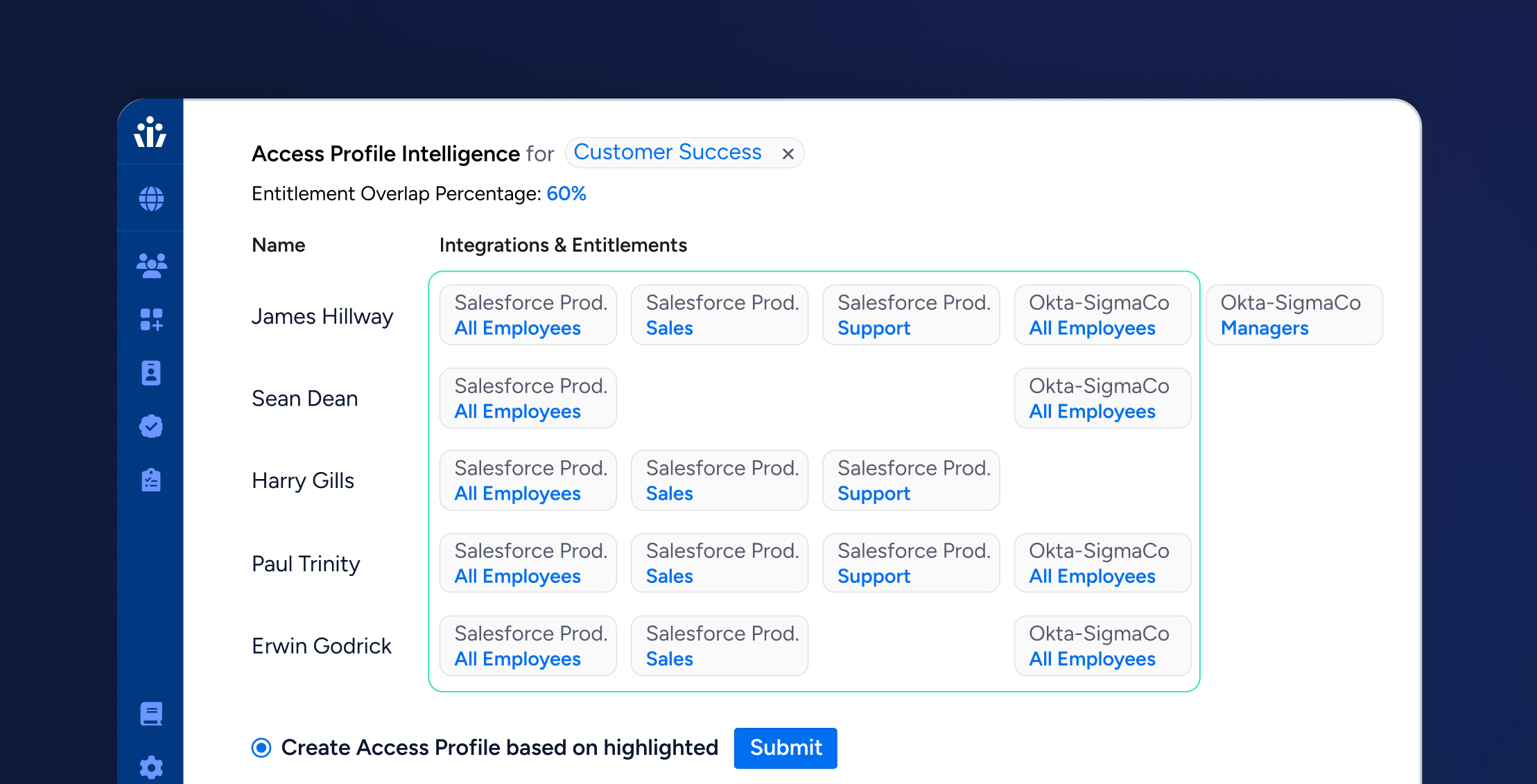 Compliance
ComplianceTransforming Access Lifecycle Management with Veza’s Access Profiles
Learn more