-
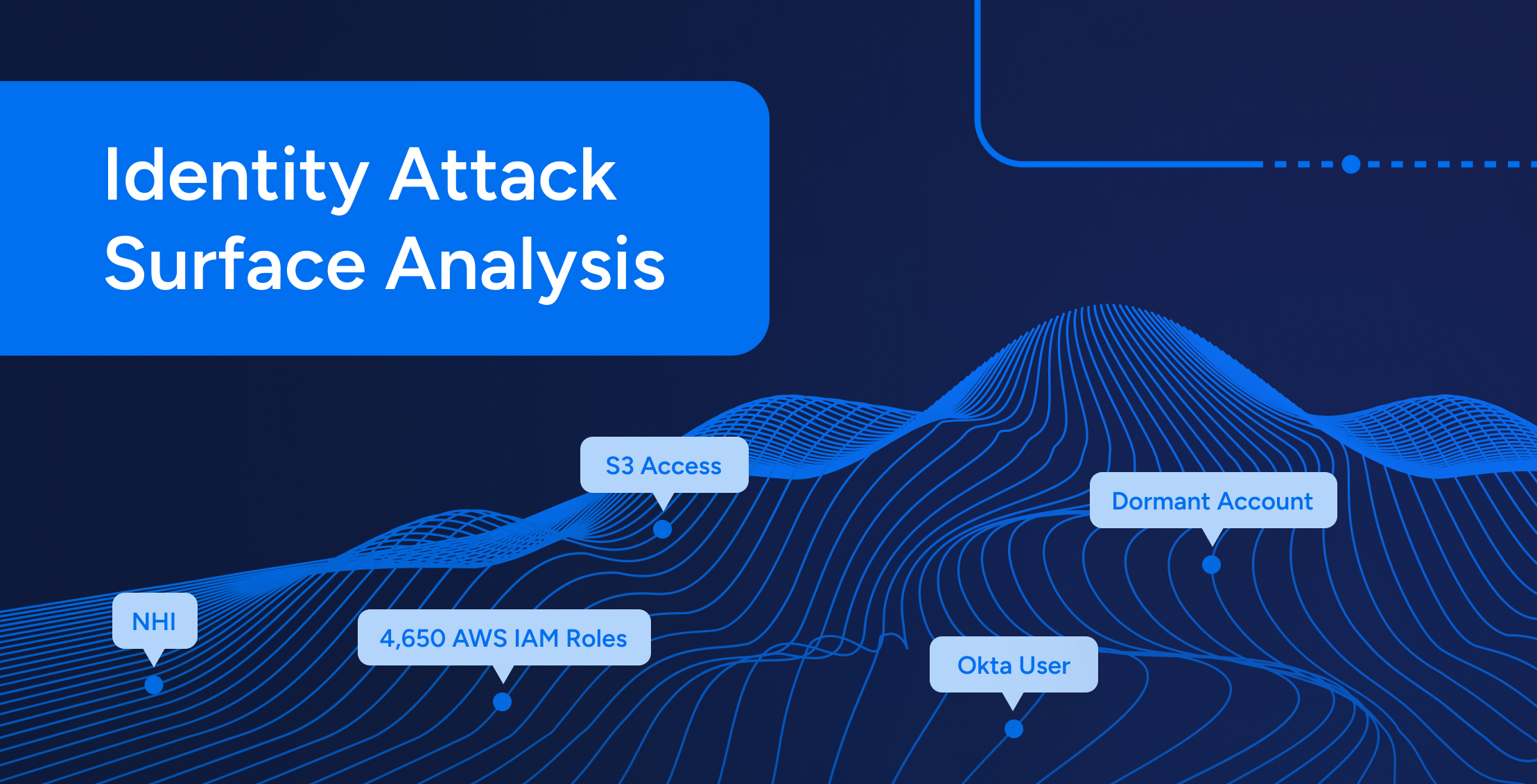 IAM
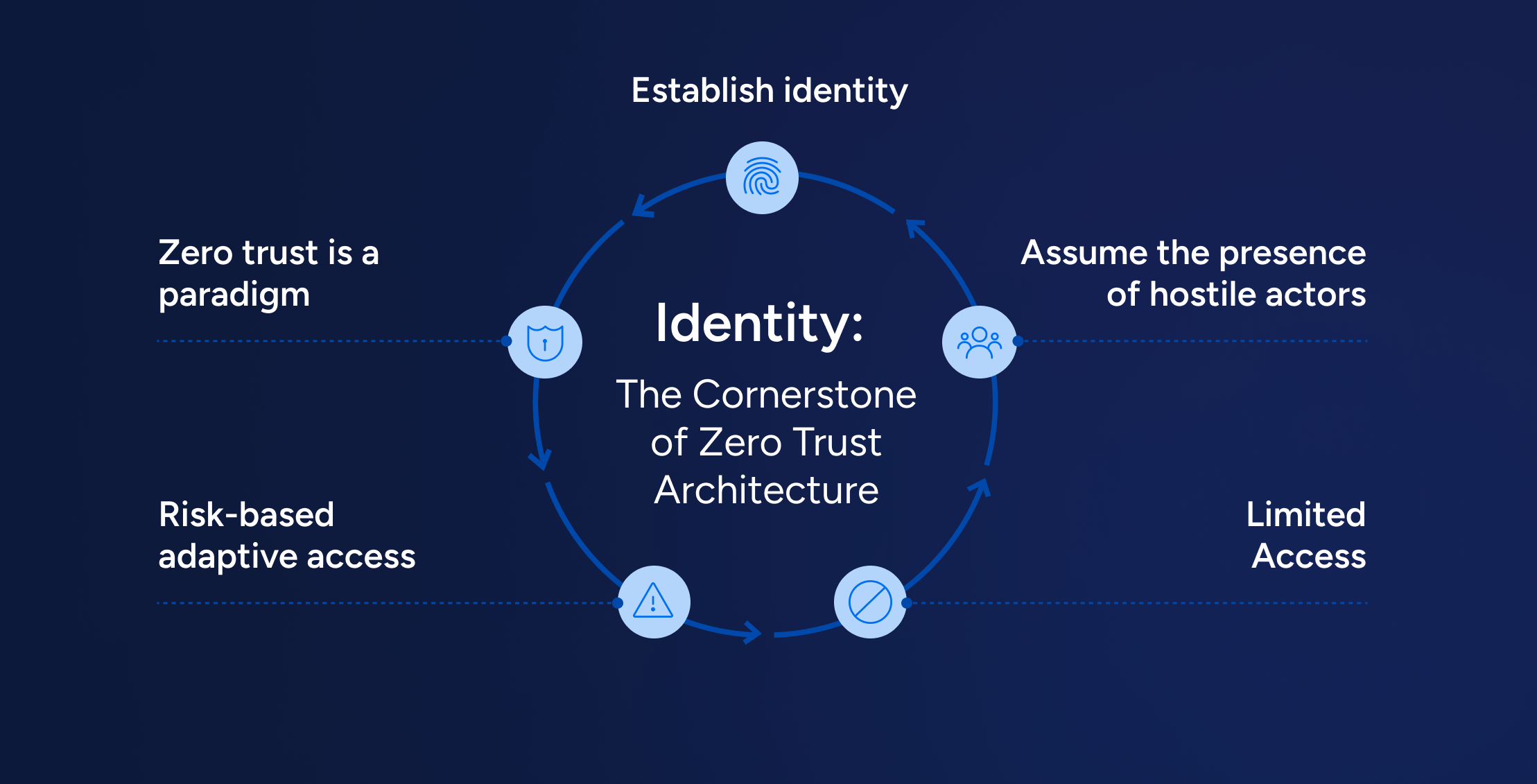
IAMIdentity Attack Surface Analysis: Securing the New Perimeter
Learn more -
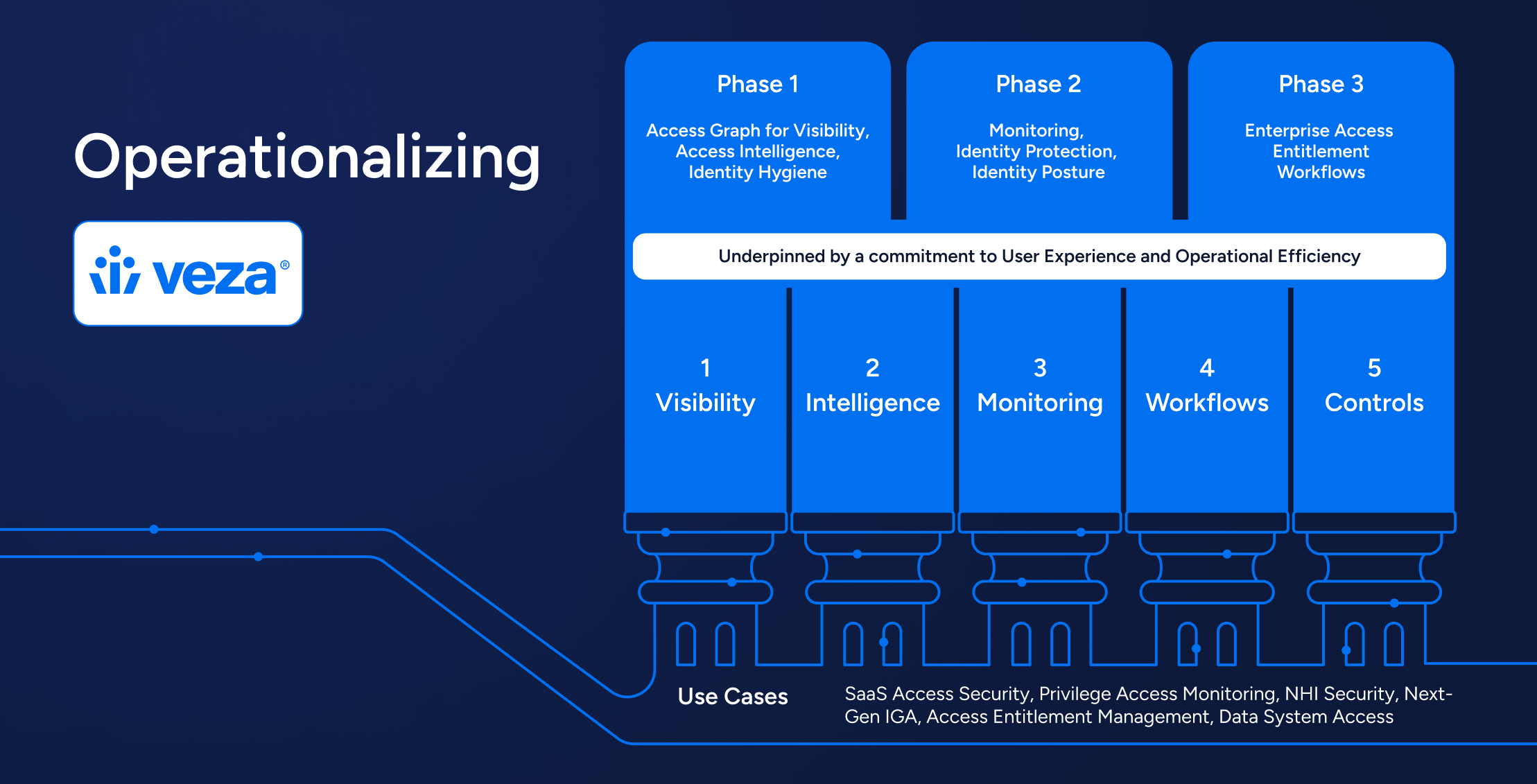 Identity Security
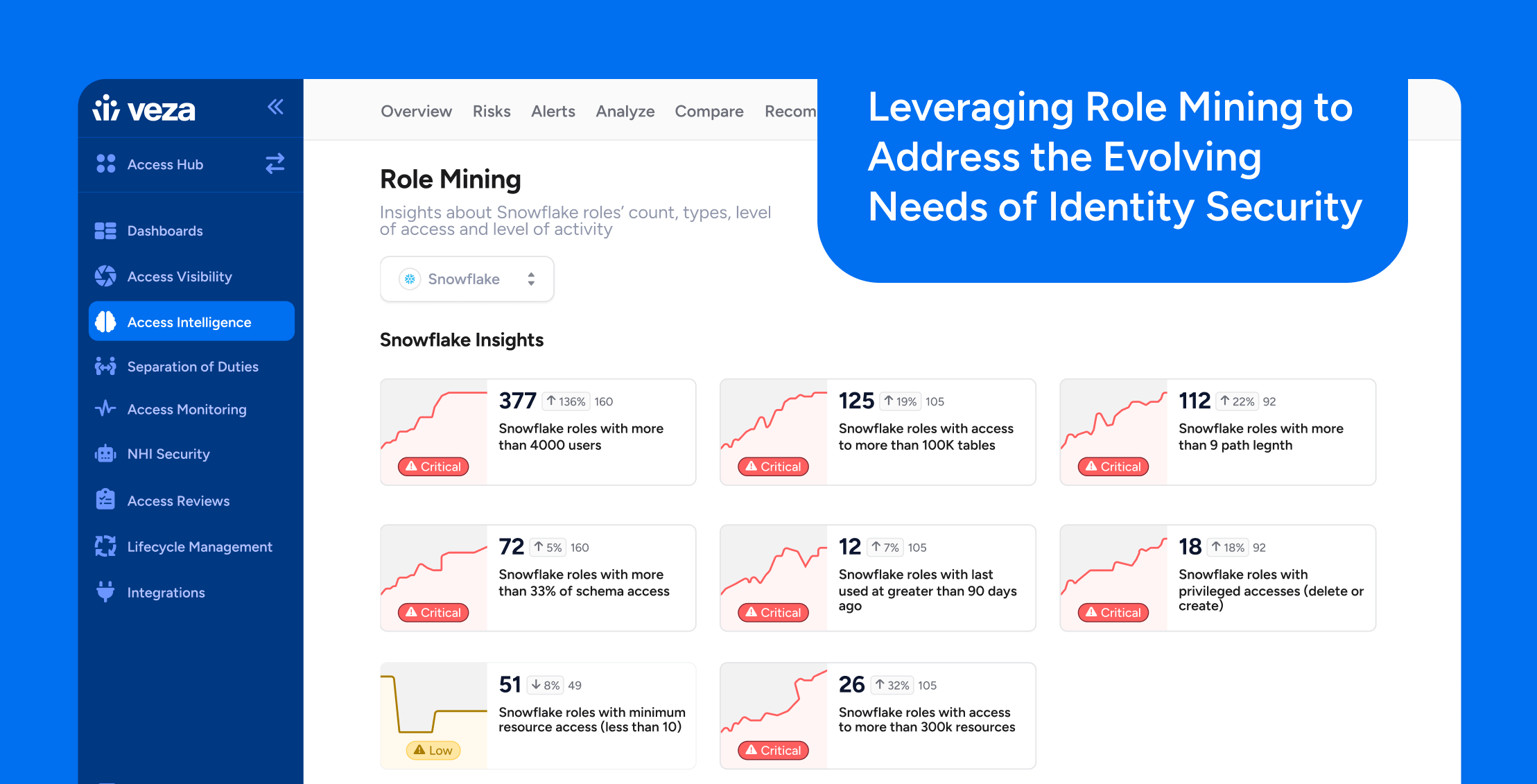
Identity SecurityOperationalizing the Identity Security Platform with Veza Actions
Learn more -
 Identity Security
Identity SecuritySaviynt Review: Features, Flaws, and Smarter Identity Security Alternatives
Learn more -
 Identity Security
Identity SecurityDefending Against Volt Typhoon: A CISO’s Playbook with Veza’s Identity Security Platform
Learn more