-
 IAM
IAMIdentity Attack Surface Analysis: Securing the New Perimeter
Learn more -
 Compliance
ComplianceWhat is Third Party Risk Management (TPRM)?
Learn more -
 Identity Security
Identity SecurityBetter Together: Augmenting SailPoint with Full-Stack Access Visibility
Learn more -
 IAM
IAMWhat Are Non-Human Identities?
Learn more -
 IAM
IAMIdentity is Eating Security: Why Access Is the New Perimeter
Learn more -
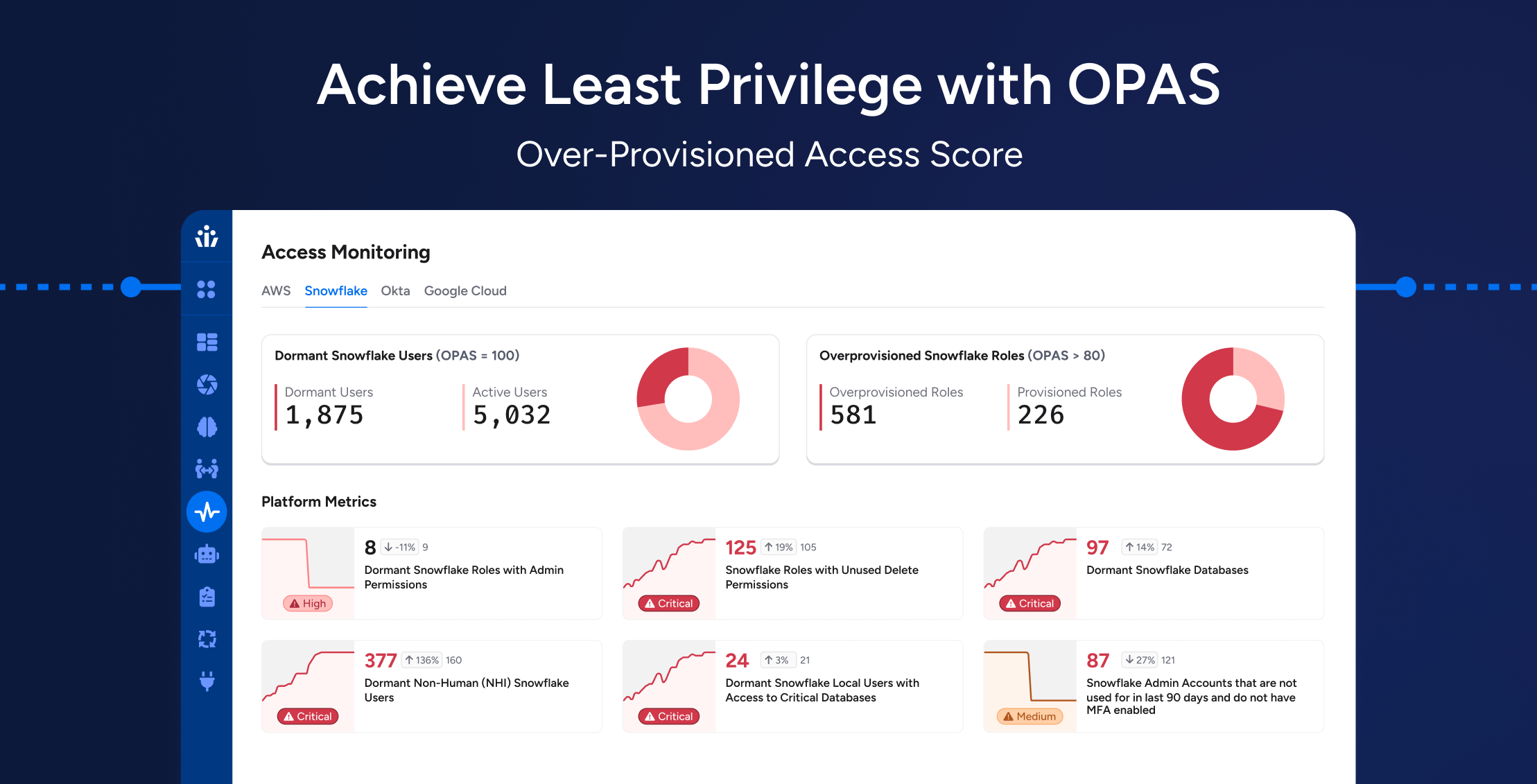 Compliance
ComplianceAchieving Least Privilege at Scale: How OPAS Helps Enterprises Reduce Hidden Access Risks
Learn more