-
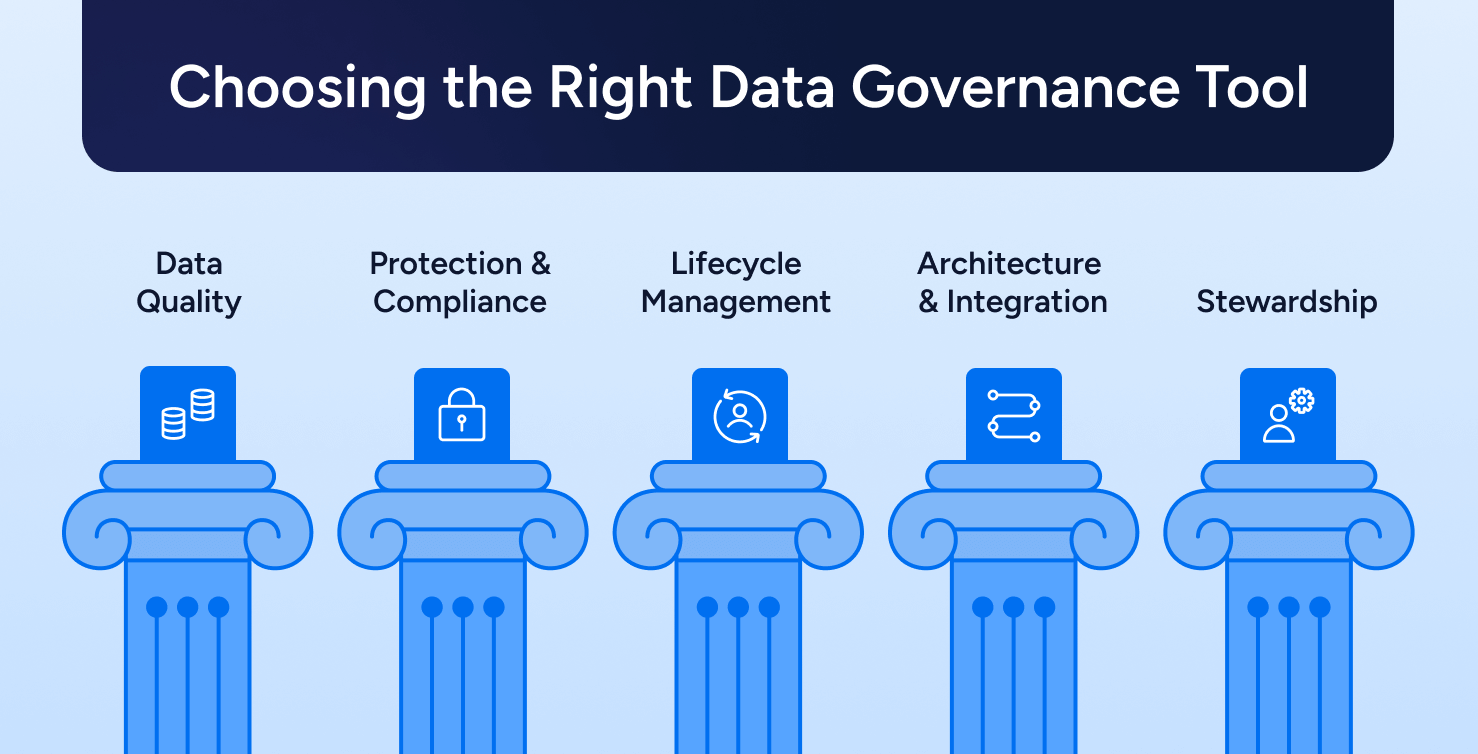 Compliance
ComplianceHow To Choose the Right Data Governance Tools [2025]
Learn more -
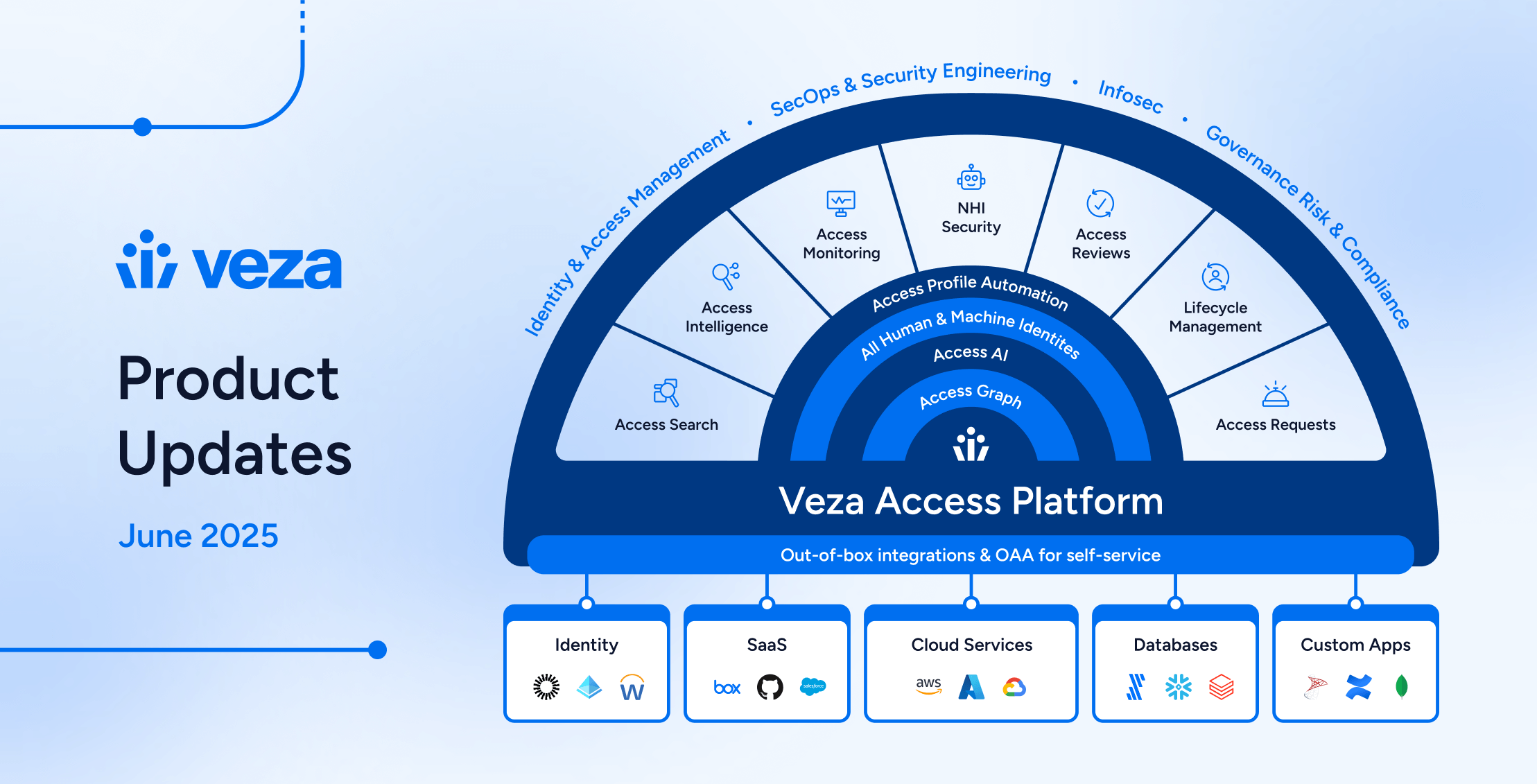 Company
CompanyVeza Product Updates – June 2025
Learn more -
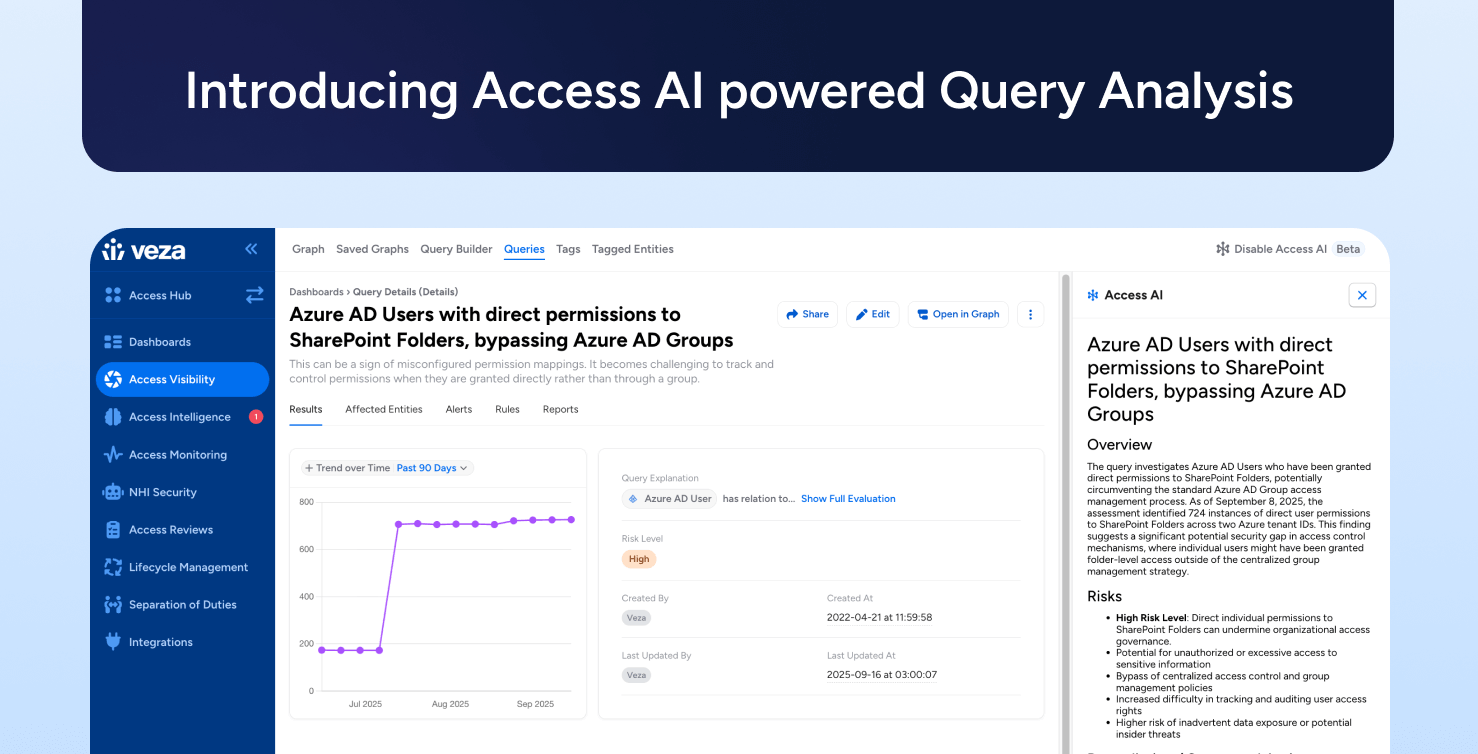 AI
AIIntroducing Access AI powered Access Risk Analysis
Learn more -
 Identity Security
Identity SecurityBeyond Insider Risk: Operationalizing Identity Threat Response with Veza + CrowdStrike
Learn more -
 Identity Security
Identity SecurityRansomware Isn’t Just Malware Anymore – It’s an Identity Problem
Learn more -
 AI
AIHow to Govern OpenAI Access While Enforcing Least Privilege: Three Enterprise Perspectives
Learn more -
 Identity Radicals
Identity RadicalsThe SharePoint Blind Spot: How Legacy IGA Failed to Stop Volt Typhoon
Learn more -
 Compliance
ComplianceDOJ’s Bulk Data Transfer Rule: Why Identity Visibility is Now a Compliance Requirement
Learn more -
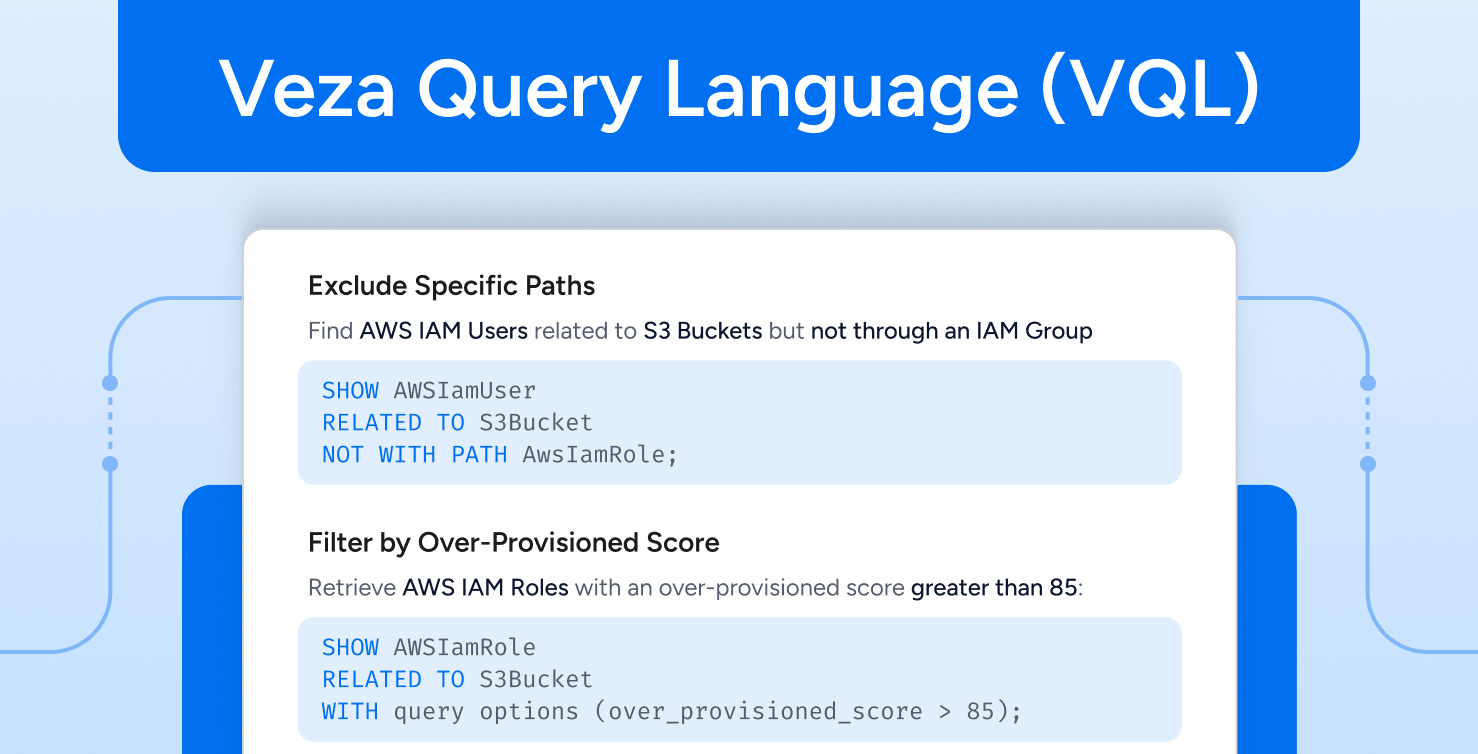 Identity Security
Identity SecurityIntroducing VQL – Veza Query Language
Learn more -
 Identity Radicals
Identity RadicalsOvercoming Identity Silos: Toward Unified Identity Security
Learn more





