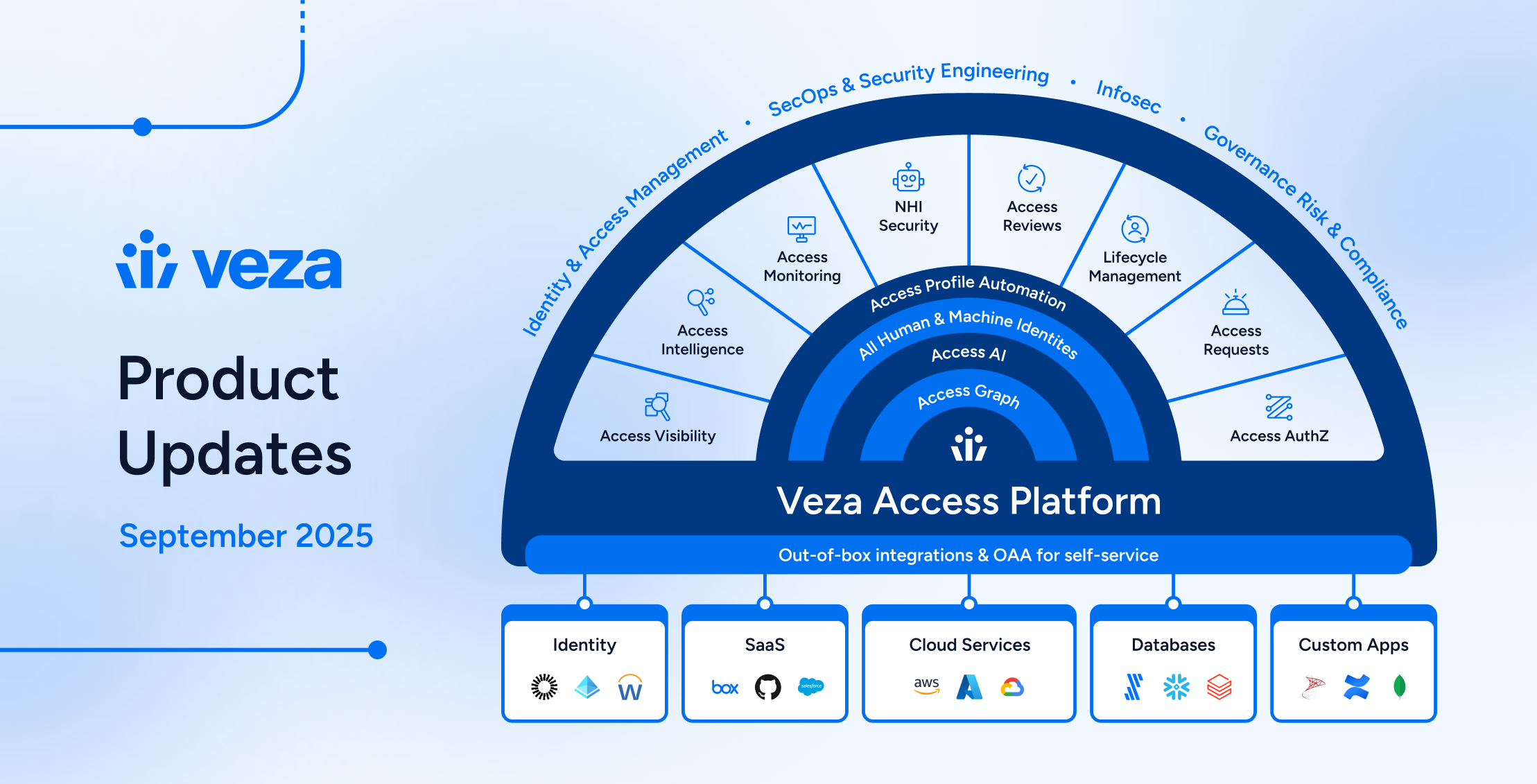
-
 IAM
IAM11 Best Zero Trust Providers for 2026
Learn more -
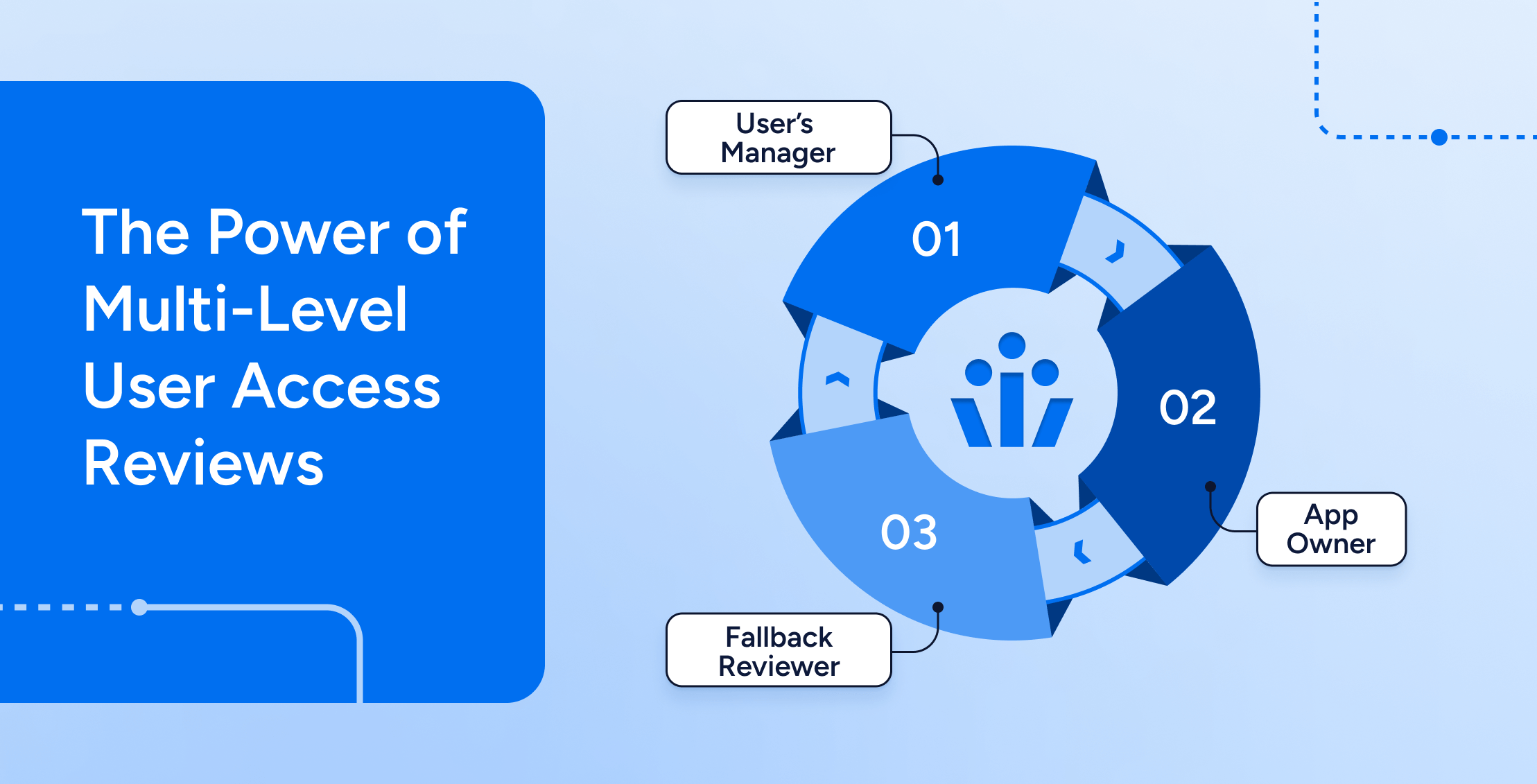 Compliance
ComplianceThe Power of Multi-Level User Access Reviews
Learn more -
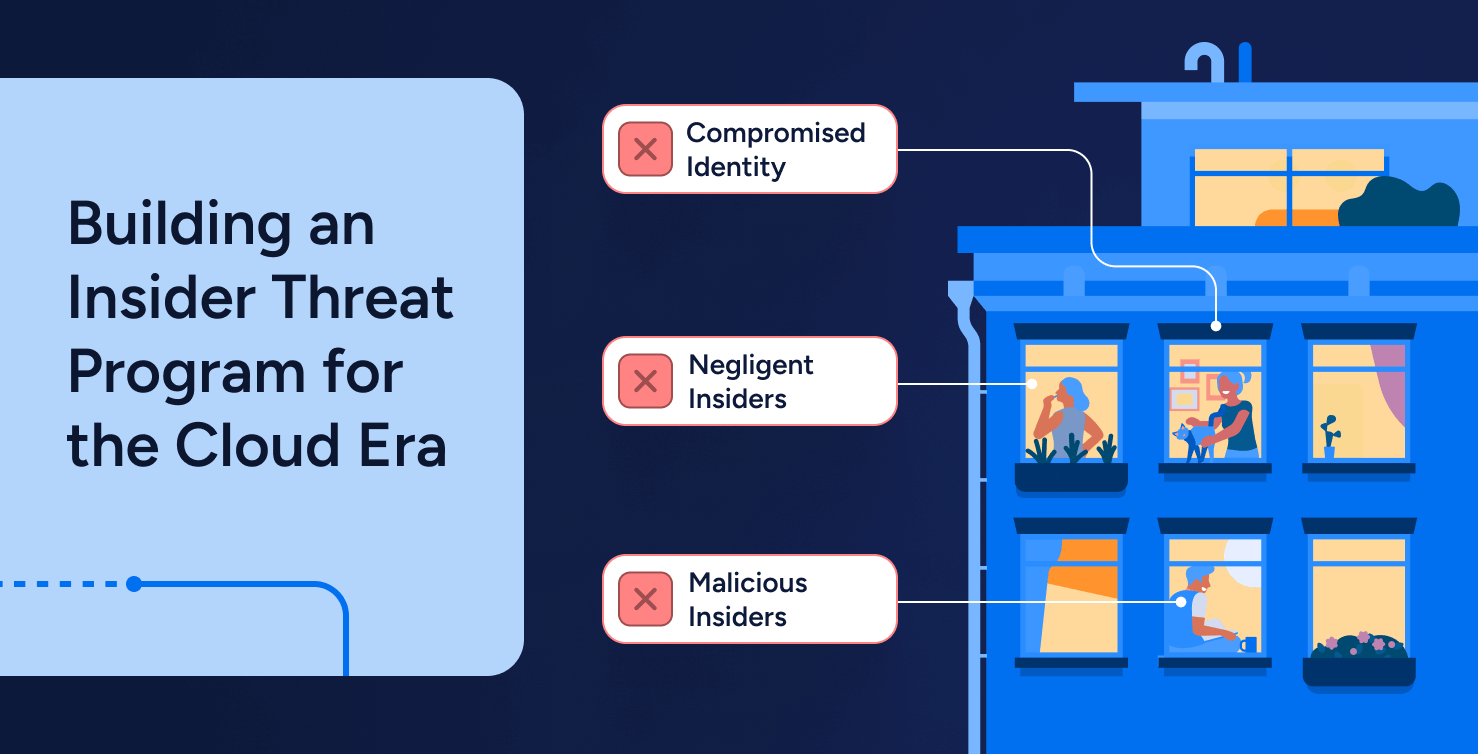 IAM
IAMWhen Identities Turn Against You: Building an Insider Threat Program for the Cloud Era
Learn more -
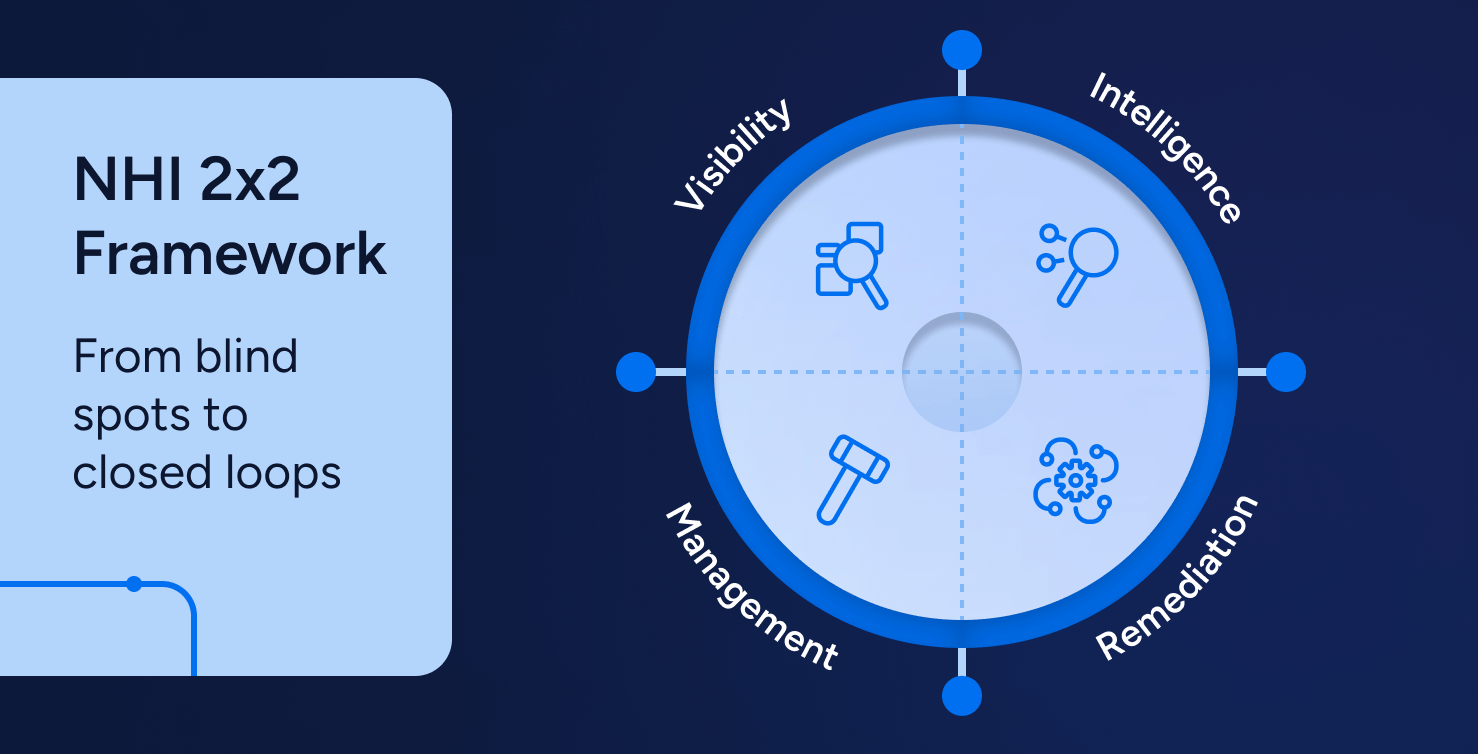 IAM
IAMNHI 2×2 Framework: From Blind Spots to Closed Loops
Learn more -
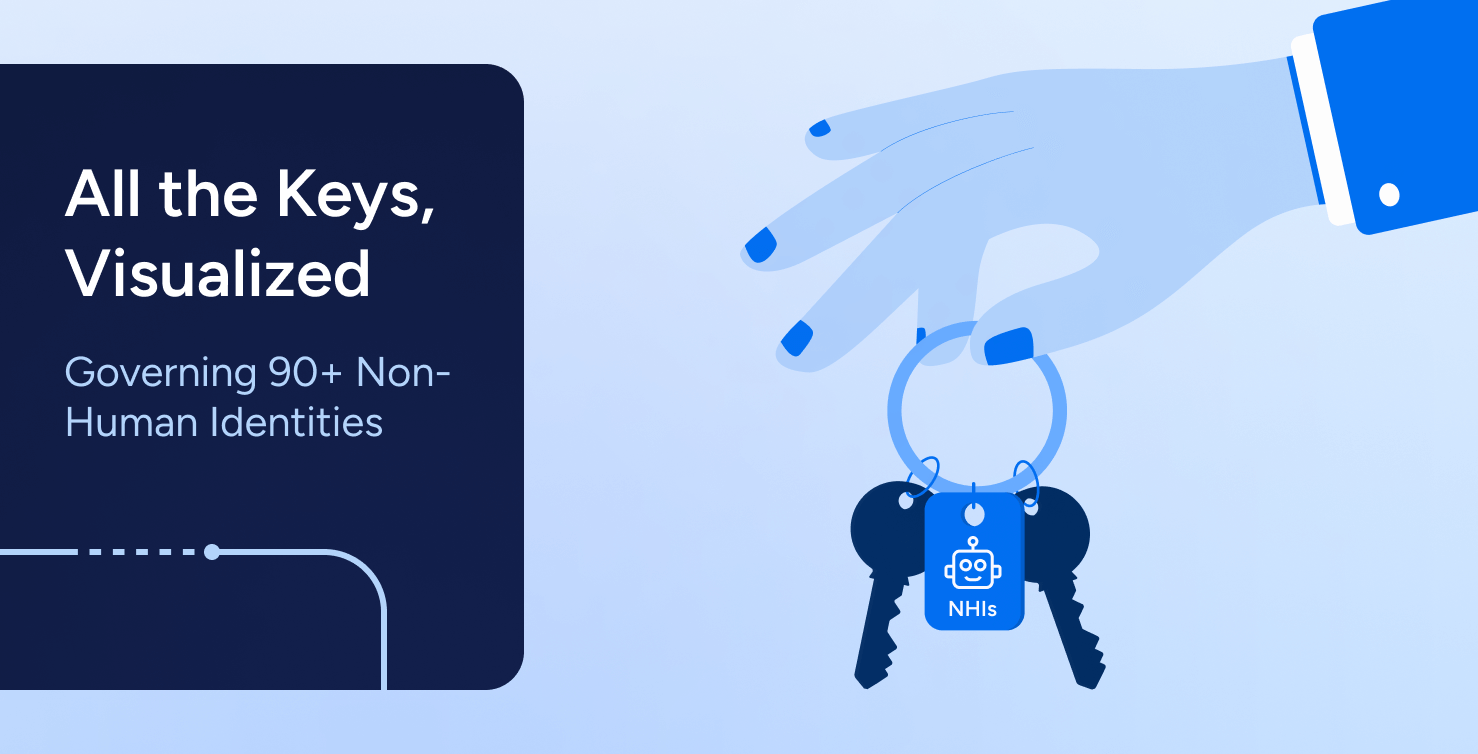 IAM
IAMAll the Keys, Visualized: Governing 90+ Non-Human Identities
Learn more