-
 Compliance
ComplianceHow Veza Strengthens SOC 1 Compliance: Common Control Failures & How to Fix Them
Learn more -
 AI
AIModel Context Protocol (MCP): Implications on identity security and access risks for modern AI-powered apps
Learn more -
 Data Security
Data SecurityGitHub OAuth Attack Alert: A Developer’s Worst Nightmare and How to Prevent It
Learn more -
 Compliance
ComplianceAchieving DORA Compliance: A Practical Guide for Financial Organizations
Learn more -
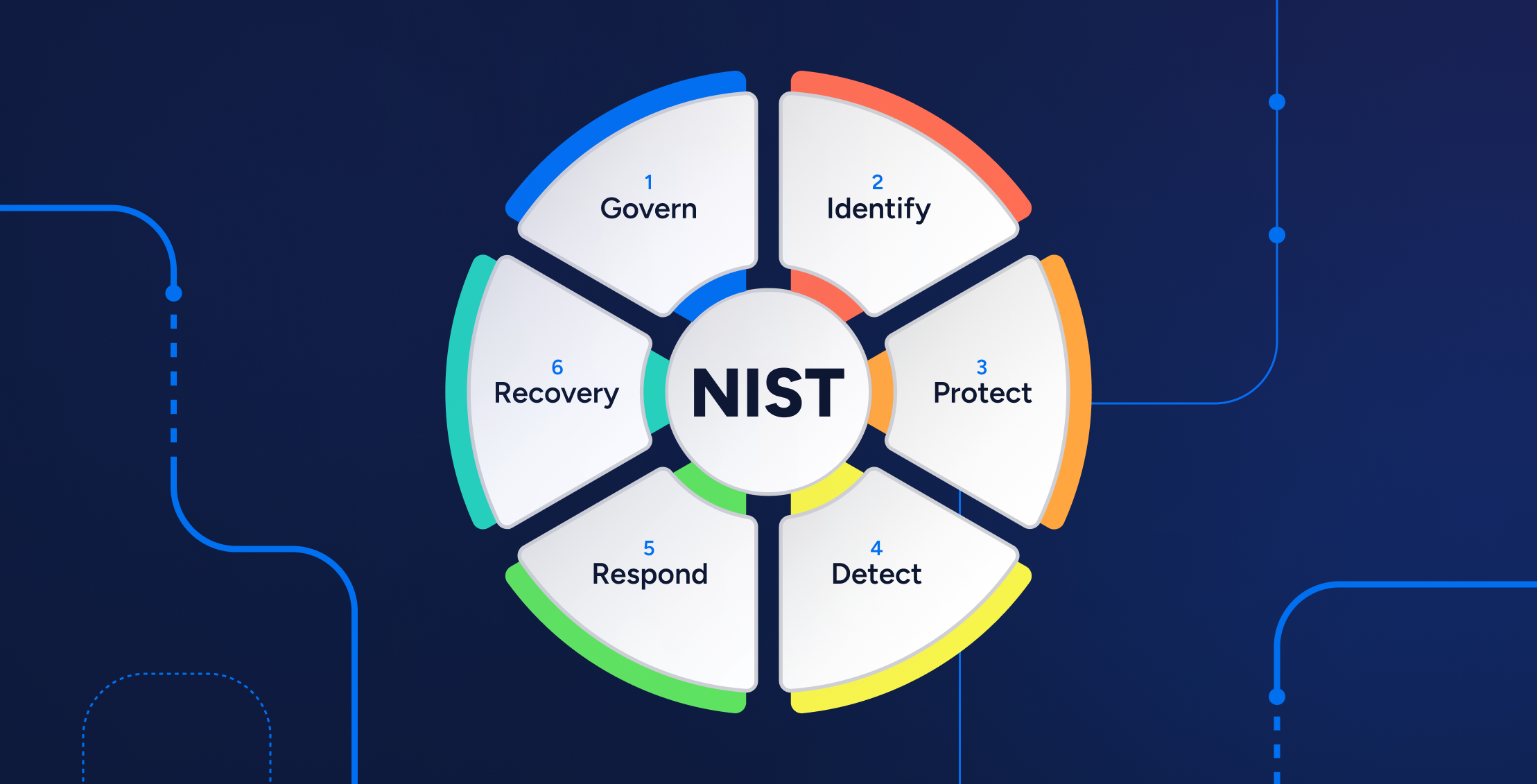 Data Security
Data SecurityWhat is NIST Compliance? Guide & Checklist [2025]
Learn more -
 Data Security
Data SecurityModern Access Request Processes: Best Practices & What to Avoid in 2025
Learn more -
 Data Security
Data SecuritySimplifying Security: The Power of Effective Access Control in Cybersecurity
Learn more -
 Data Security
Data SecurityAutomated Access Revocation & Remediation at Scale
Learn more -
 Data Security
Data SecuritySecuring Snowflake: A CISO’s Guide to Effective Access Control
Learn more