I have the honor and pleasure of leading a world-class team on a mission toward advancing the state of the cybersecurity industry. I love building products from the ground up, working very closely with customers to address their pain points, and iterating with fast-paced engineering and GTM teams. Similar to how building a product is a function of following customer insights and prioritization, go-to-market strategies scale on the principles of:
- Why anything?
- Why Veza?
- Why now?
As we unveil our biggest product launch ever, we’re focusing on those three GTM principles to paint a clear picture of our vision for the future of identity security.
Why anything?
The “why anything?” principle (or, in some cases, “why do anything?”) is the easiest to answer when it comes to identity. Identity is considered the new perimeter for a reason: it’s critical to business growth and cybersecurity.
Identity is composed of users, groups, roles and associated permissions. Essentially this looks like:
- Users/Groups – Who are you? : Traditional identity systems provide definitions of users and groups – what is considered as “the identities”. Every system needs to be associated / assigned with an identity so that users can utilize the system.
- Roles/Permissions – What can you do? : The data to which the users (identities) are given access to and the actions they can perform is codified via the “authorization layer” including the roles that have associated permissions and the privileges an identity may have to a set of resources/objects. Every system has its own unique authorization permissions via which identities are given access to perform actions (read, updates, delete, updates, etc.) on resources.
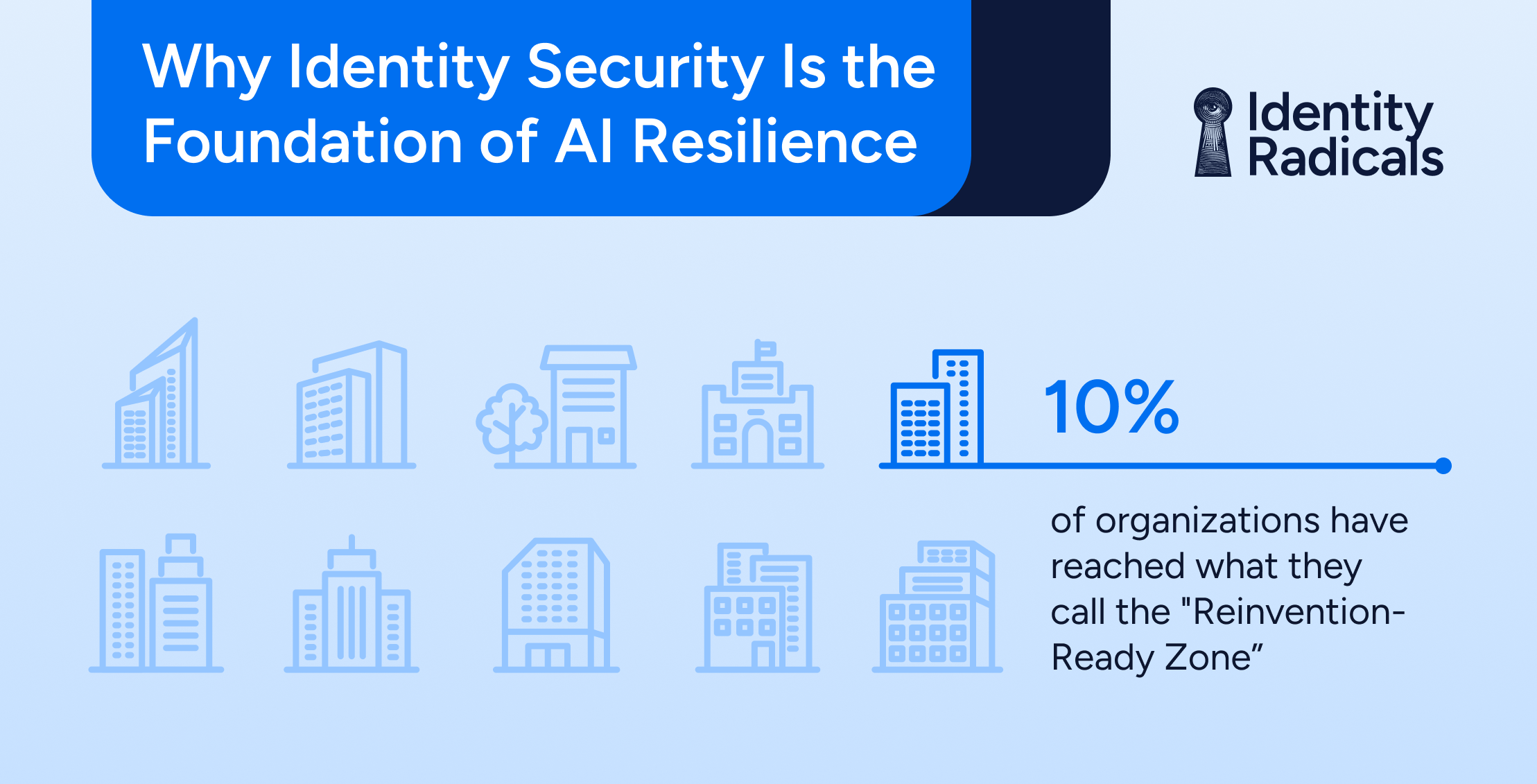
Identity is the weak link in most security architectures
With an increasing number of identity-related security incidents (privilege abuse, insider threats, credential thefts, MFA compromise, etc.), it’s clear to see that something is broken in the way organizations have traditionally managed and governed identity access. The results of this dangerous dynamic are dismal and are putting all of us at risk. Look to the headlines: breaches are constantly reported, including companies like Twilio, MGM, Uber and more. Although every breach is unique, there is a common theme: identity credentials are compromised and, by using those compromised identities, someone gets access to data that they should never have the ability to see.
Despite increasing rates of identity-related security incidents, identity is still a cornerstone of many business initiatives. Projects like new software-as-a-service (SaaS) adoption, new cloud adoption, new infrastructure services, new databases, adoption of modern AI models for business efficiency, etc. all start with identity.
So, why aren’t we protecting it?
Why Now?
As companies start, grow, and scale, they adopt countless SaaS apps, data platforms and infrastructure systems, with identities (some federated, some local) throughout these systems.
- Increasing authorization complexity of cloud-native systems: With the accelerated adoption of SaaS apps, data platforms and infrastructure systems, enterprises cannot possibly govern all these accesses of identities manually or statically via simple rules. The complexity of the cloud with its multiple federation and potential for many-layer role assumption is too complex to manage and secure without constant, automated governance. Without an automated process, your crown jewels are constantly at risk.
- Mass-market adoption of cloud-based authentication systems: SSO and MFA have reached the mainstream with companies like Okta and Microsoft making the tools widely available. These are necessary but not sufficient, and the proof is in the pudding: breaches reach headlines every day and the number and sophistication of attacks on IAM infrastructure will increase. Identity access needs a bold second act; modern identity security is the way forward.
- Orgs need to secure non-human identities, too: While human identity is critical, the increase in the use of machine identities and service accounts can not be ignored. These non-human identities empower systems to run, giving them access to the data they need to do their “jobs”. However, machine identities have no representation in identity provider systems (IdP) such as Okta, AD, Ping, Duo, OIM, etc. Yet, a compromised machine identity can be used to move laterally throughout an organization, similar to how a threat actor could use a human account.
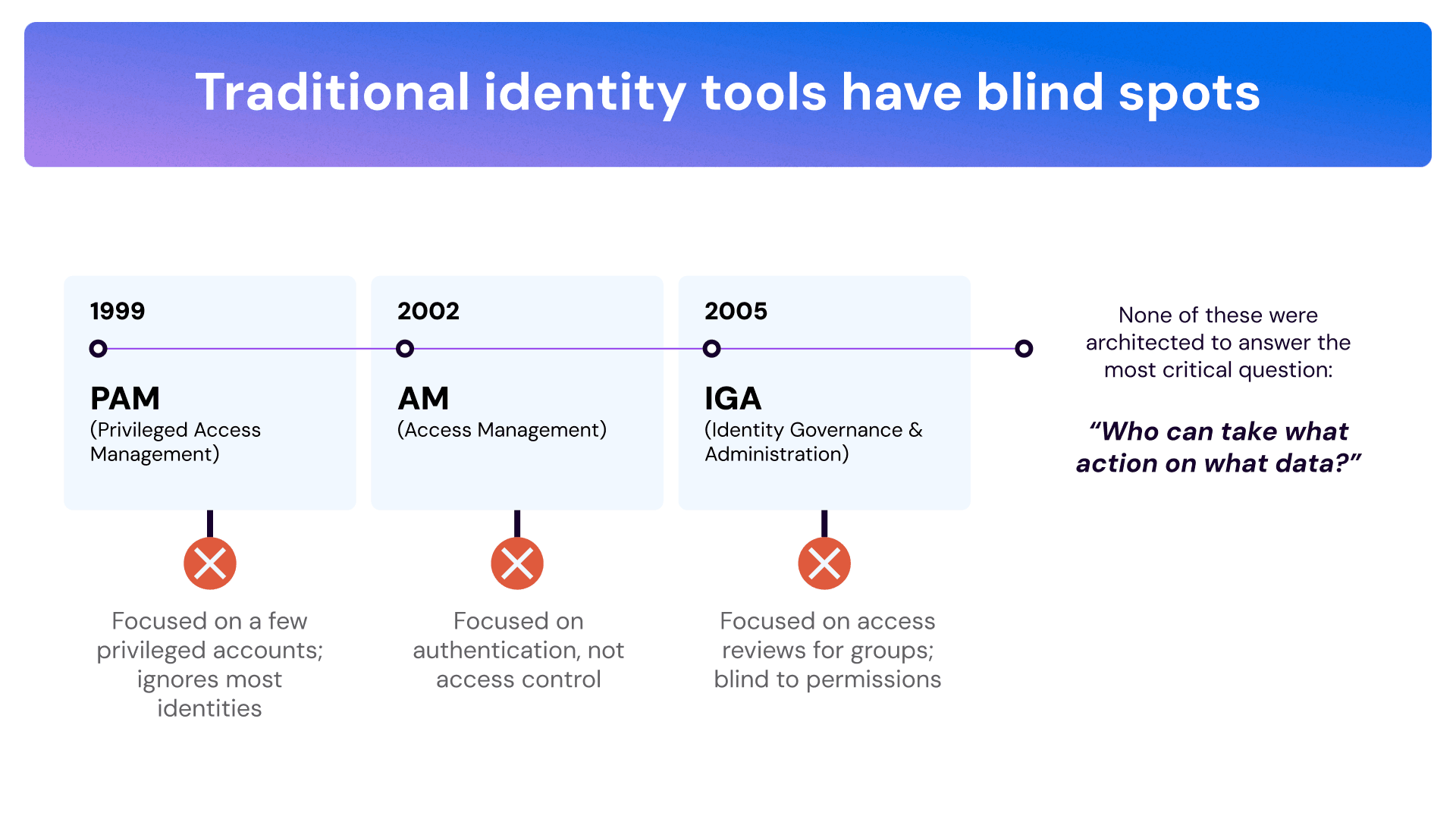
To further underscore the need for identity security, we can look to NIST. In early August, NIST released the Cybersecurity Framework 2.0, an overhauled version of the initial framework they released nearly a decade prior. Although the new framework still includes the former’s five main functions of cybersecurity – identity, protect, detect, respond and recover – the latest iteration includes a sixth critical component: govern.
Identity is now no longer about identity providers and SSO, but rather about:
- Modernizing Identity Governance
- Adding “Monitoring” to Privilege Access Management
- Identity with Detect and Respond
- Identity SecOps – bringing identity to SOAR platform
- Identity Posture Management – posture of every infrastructure is critical – just like our networks need to be secured, and our endpoints need to be secured, so do the identities need to be secured.
Why Veza?
If identity is the cornerstone of every security program, then access management is the mortar that ties the identities to resources. Access governance is the foreman making sure that the house will stand when a storm comes. Access governance is indispensable; the show cannot go on without it.
Our insights are simple yet profound: over the last decade, the industry has seen world-leading innovations around how to protect different segments of the infrastructure: network security, app security, and endpoint security. However, from a business value perspective, all these investments are for one primary reason: not to protect the infrastructure itself, but to secure access to data.
Our critical intuitions have been validated time and time again. We believe the “truth” of access to data is codified in the system-specific authorization permissions metadata. Until Veza, no one has built a system that configures, maps, and monitors these system-specific permissions and – most importantly – their associations to identities (human or machine) in near real-time. It was clear that while the industry has developed significant innovations (e.g. SSO) over the past decade, the hardest of the access problems – understanding system specific permissions and associating these to the identities – has still not been cracked.
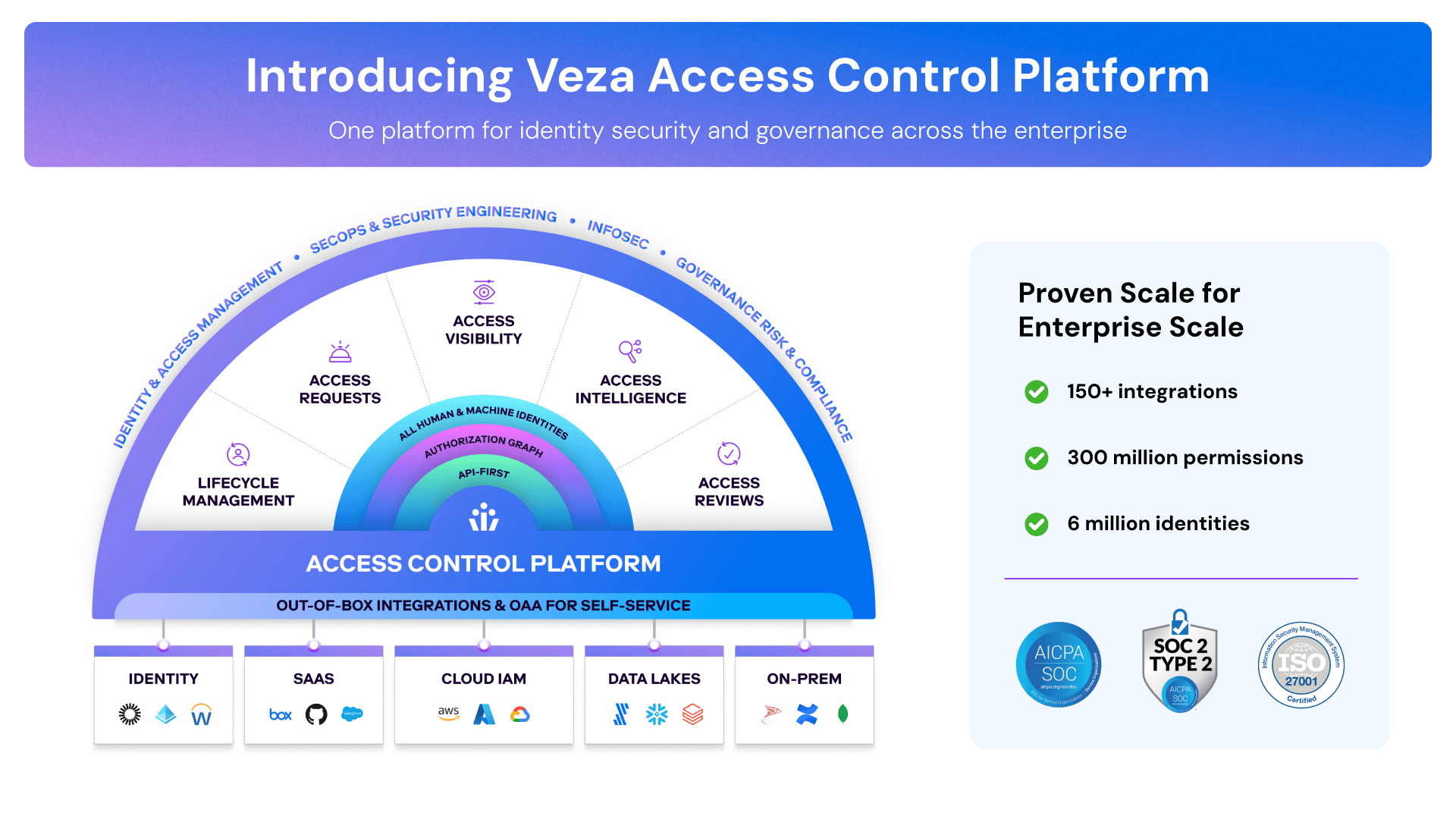
This is exactly why Veza was founded. We have invented a normalized Canonical Data Model that maps to any authorization method (RBAC, ABAC, IAM, etc.) used by end systems. This data model is realized as the Veza Authorization Graph which acts as the foundation for us to address access visibility, access intelligence, access monitoring, access lifecycle, and access requests.
It’s critical that the modern access control system – Veza – is applicable to enterprise systems. Such a system must encompass SaaS apps, data systems, infra services, and cloud services – each with its own authorization metadata. Understanding that customers need to manage and control access to all these systems, we have developed the Open Authorization API (OAA) that provides anyone with a self-service approach to integrate any application or system into Veza.
With Veza, we have a vision to build the future of access control. We believe that the cornerstone of the future access control platform is one which offers access visibility, access intelligence, access reviews, access lifecycle, and self-service access requests – all at enterprise scale and to any enterprise system.Unifying all aspects of the entitlement lifecycle is critical and Veza’s focus. The cloud is a highly interconnected ecosystem and point products addressing subsets without context of the overall will inherently lead to an insecure posture.
We’ve been building with these tenets in mind and I’m thrilled to announce Veza has taken a monumental step today in announcing Next-Gen IGA, a true game changer in identity security for the entire multi- and hybrid-cloud world.
To learn more about Next-Gen IGA:
- Read our official announcement ➡️ Read here.
- Learn how to leverage Next-Gen IGA to secure your org: Watch on-demand here.