In the latest episode of our podcast, we had the privilege of speaking with Josh DeFigueiredo, the Chief Information Security Officer (CISO) of Workday. With 15 years of experience leading security at the HR and financial software giant, Josh shared invaluable insights into how identity security has evolved, the challenges of implementing least privilege at scale, and the future of identity security in an increasingly complex digital landscape.
The Changing Security Landscape
Fifteen years ago, when Workday was still a small startup, the security landscape was vastly different. The rise of cloud computing, AI, and machine learning has reshaped the way companies approach security. Josh emphasized that identity has become the front line of security, stating, “Hackers aren’t hacking in, they’re logging in.” As cyber threats have become more sophisticated, organizations like Workday have had to evolve rapidly to protect sensitive HR data for millions of employees globally.
Why Identity is Workday’s Top Security Priority
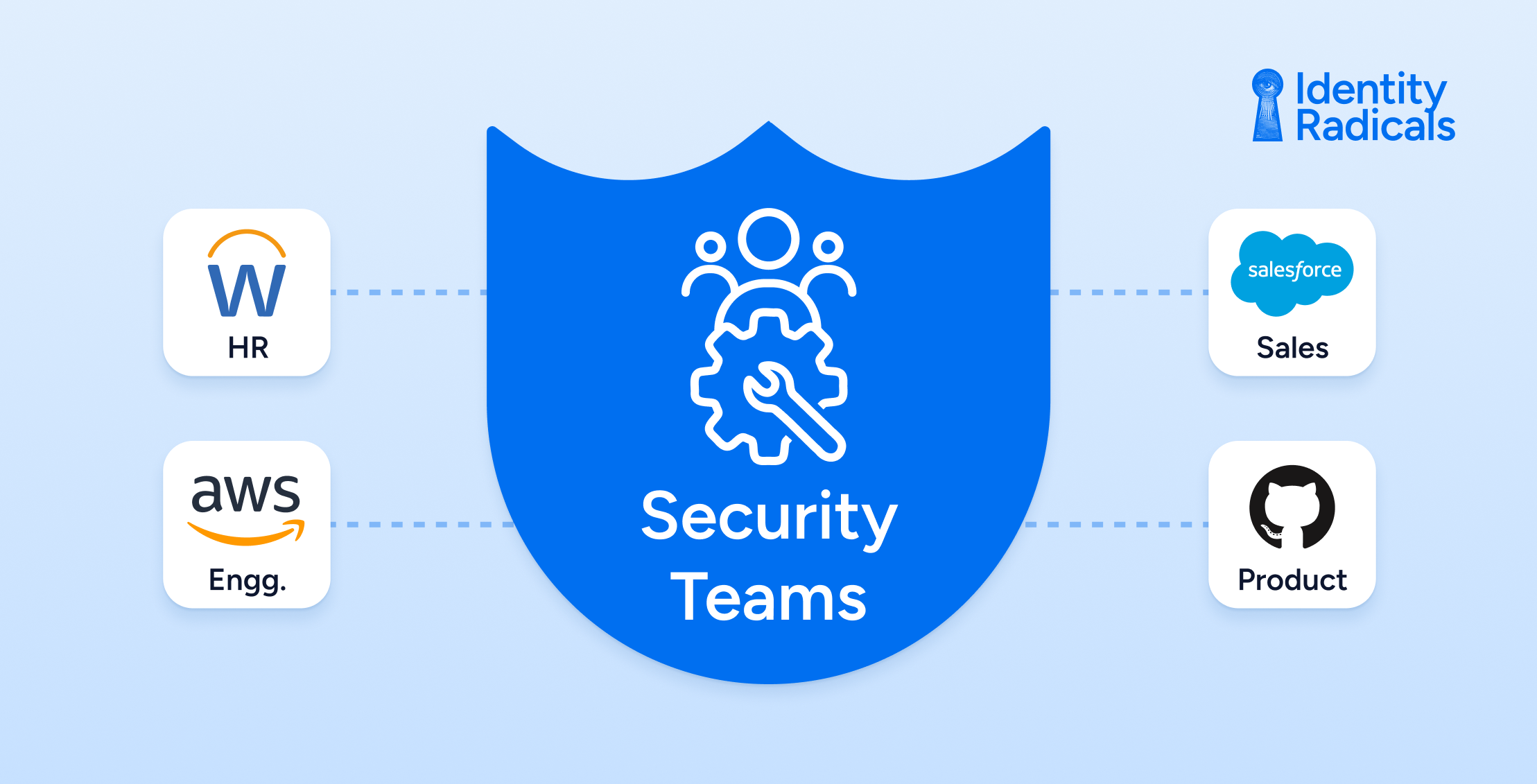
Managing identity security at scale is no small feat, particularly for a company handling sensitive financial and HR data. According to Josh, identity has become the most critical security concern for CISOs today. He noted, “If you’re a CISO and identity isn’t a major priority, you’re either doing something that most CISOs aren’t doing or you’re missing the mark.” With attackers increasingly targeting identity credentials, ensuring robust identity governance is essential for preventing breaches.
The Challenge of Implementing Least Privilege at Scale
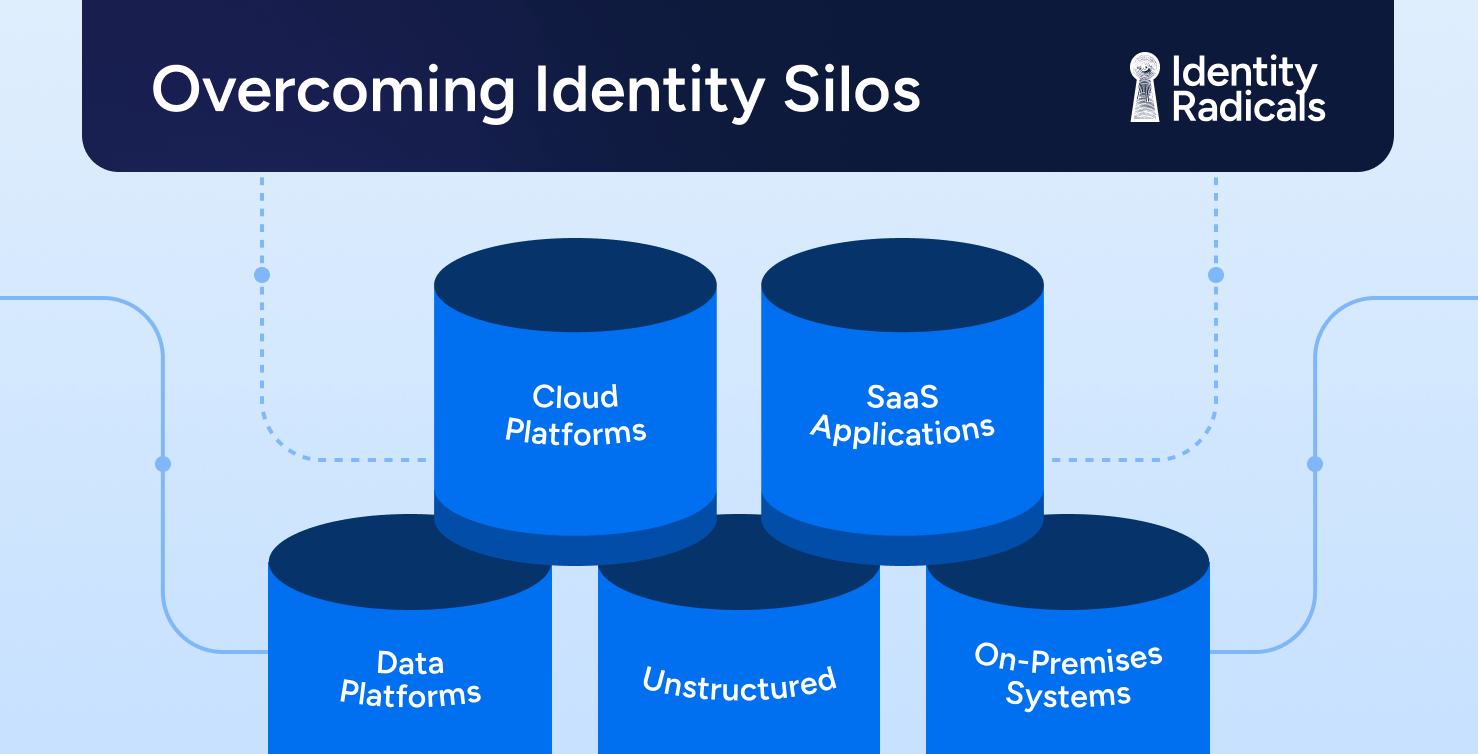
One of the most pressing security challenges Workday faces is enforcing least privilege access across a large, complex organization. Visibility into permissions and access needs is a continuous struggle, requiring a combination of strong governance, automation, and innovative technologies. As Josh put it, “If there’s a silver bullet, I’ll buy it.” While no single solution exists, Workday has invested heavily in access visibility and control to minimize risk.
Security and Privacy: Two Sides of the Same Coin
Josh also highlighted the intersection of security and privacy, explaining how security is the foundation for privacy compliance. However, with rapidly evolving regulations, companies must remain agile. He joked, “We probably won’t be compliant with [new privacy regulations] by the time we’re done recording this episode.” This ongoing challenge underscores the need for continuous adaptation in security strategies.
The Future of Identity Security
Looking ahead, Josh sees both exciting opportunities and increasing complexity in identity security. AI and machine learning are playing a growing role, enabling advancements such as real-time authorization and natural language processing for identity management. However, the fragmentation of identity solutions remains a concern, making interoperability and standardization critical areas of focus.
Key Takeaways for Security Leaders
Josh’s insights serve as a powerful reminder of the importance of identity security. Here are some key lessons for security professionals:
- Identity is the primary attack vector – Organizations must prioritize identity security to stay ahead of threats.
- Least privilege is difficult but necessary – Maintaining tight control over permissions is essential to minimizing risk.
- Security and privacy must evolve together – Compliance isn’t static; it requires ongoing effort and adaptation.
- AI and automation will shape the future – Leveraging these technologies can enhance security but also introduce new complexities.
As identity continues to be the focal point of cybersecurity discussions in boardrooms, Workday’s approach offers valuable guidance for organizations looking to strengthen their identity security strategies.
To hear the full conversation with Josh DeFigueiredo, tune in to the latest episode of our podcast!