Executive Summary:
SOC 1 compliance signifies strong financial controls, helping businesses build client trust. Non-compliance can lead to reputational damage and lost business opportunities. As organizations manage increasing complexity in financial operations, ensuring continuous compliance becomes a challenge. Veza helps automate access governance, enforce separation of duties (SoD), and strengthen cyber incident response to maintain audit-ready controls.
Introduction to SOC 1 Compliance and Its Importance
As the personal income tax filing deadline approaches in the United States, imagine working with your Certified Public Accountant (CPA) to prepare and file your taxes with the IRS. You trust your CPA to ensure everything is accurate, filed on time, and in compliance with the most recent tax laws. But how do you know that your CPA follows the correct processes? What if an independent auditor examined the CPA firm and provided a report stating that the firm has strong and well-documented processes to ensure that client tax returns are prepared accurately and filed promptly? You’d sleep easier knowing your taxes are in good hands. Conversely, if the report indicated the CPA firm had weak processes, you’d likely look for another accountant!
This is precisely how SOC 1 (System and Organization Controls 1) compliance works for businesses. Companies providing outsourced financial services, such as payroll processing, banking, cloud computing, financial software, medical billing and claim processing, must assure clients that their internal controls are reliable. SOC 1 reports serve as independent auditor’s validation, confirming whether a company’s controls are reliable and meet compliance standards.
In today’s business landscape, ensuring SOC 1 compliance not only helps safeguard financial data but also fosters trust with clients. Without SOC 1 compliance, companies risk exposing themselves to reputational damage and loss of business opportunities.
The Evolution and Types of SOC 1 Reports
SOC 1 evolved from earlier auditing frameworks to ensure financial reporting integrity. Over time, standards like SAS 70 and SSAE 16 introduced stricter requirements, culminating in today’s SSAE 18 standard.
SOC 1 reports are categorized into two types:
- Type I – A report on the suitability of control design at a specific point in time.
- Type II – A report on both design and operating effectiveness of controls over a period (e.g., six months or a year)
Organizations typically seek a Type II SOC 1 report, as it assesses both design and operational effectiveness over time—providing a higher level of assurance to clients.
SOC 1 and other Standards
SOC 1 vs. SOX: SOC 1 and SOX are closely related because they both deal with financial reporting and internal controls. Publicly-traded companies subject to SOX compliance often request SOC 1 reports from third-party service providers to ensure compliance with internal control requirements mandated by SOX. For example, a loan service provider serving public banks may need a SOC 1 report to prove financial controls for SOX compliance.
SOC 1 vs. SOC 2: SOC 1 and SOC 2 fall under the SOC framework issued by American Institute of Certified Public Accountants (AICPA), but SOC 1 focuses more on financial reporting control, while SOC 2 focuses on security, availability, and privacy. Note that there are common control areas between SOC 1 and SOC 2, such as access controls, incident management, and change management. In some cases, organizations pursue both reports to address different regulatory and customer requirements. For example, a financial service provider handling sensitive customer data and financial data may need both SOC1 and SOC 2 to demonstrate financial controls and security and privacy measures.
Global Relevance of SOC 1 Compliance: While SOC 1 is primarily a U.S.-focused framework, it is widely recognized and used by businesses operating internationally, particularly those serving US-based clients. Given different countries may have distinct auditing standards and regulatory requirements, businesses with global operations should evaluate SOC 1 alongside other relevant international compliance frameworks, like ISAE 3402, to ensure comprehensive compliance.
Unqualified and Qualified Report
An unqualified opinion, also known as a “clean” report, is the best outcome for a SOC 1 audit. It provides reasonable assurance to customers and stakeholders that the service organization has strong controls over its financial reporting processes.
A qualified opinion is issued when the auditor concludes that there are material misstatements in the system description or controls are not suitably designed or operating effectively. Specific reasons for a qualified opinion might include significant control deficiencies or lack of evidence to support operating effectiveness.
An unqualified report reinforces customer confidence and can help maintain and attract business partnerships. In contrast, a qualified report may raise concerns about the reliability of the service organization’s processes and might lead some customers to reconsider their partnership or seek additional assurances.
Challenges to Stay In Compliance with SOC 1
Business applications are increasingly numerous, technically complex, and interconnected. Companies today not only leverage a large number of applications to support business operations, but these applications run across multiple platforms and are also becoming increasingly complex and interconnected. For example, a payroll processor, once relied on manual wire transfer, may use a SaaS payment processing solution with an in-house developed AI agent for payment approval, and the approval and payment data may be stored in a cloud storage solution.
Business operations are distributed globally. Companies’ operations are becoming progressively decentralized, making it challenging to maintain consistent business processes. Using the same payroll processor as an example, the payroll calculation and recording can be done in multiple locations globally. It is difficult to make sure that all locations follow the same procedures.
Common SOC 1 Compliance Failures
As business applications become more interconnected and operations expand globally, organizations find it difficult to maintain effective SOC 1 controls. Here are some common SOC 1 control failures:
- Weak Logical Security Controls: As businesses expand, their financial access governance becomes more challenging. With systems growing in number, complexity, and interconnectivity, organizations often lose track of who has access to critical financial systems. Without strong identity governance processes, this can lead to excessive user privileges and violations of separation of duties (SoD), such as a single employee both approving and processing wire transfers—creating a significant risk to compliance.
- Lack of Incident Response Controls: While SOC 1 does not mandate data breach notifications, it requires auditors to disclose any material breaches. Many organizations lack the necessary incident response plans and tools, which can result in delayed action when breaches occur. Timely breach detection and response are critical to mitigating risk and ensuring that incidents are properly documented in the SOC 1 report.
- Deficient Change Management Controls: Change management in SOC 1 environments can be problematic, particularly when enforcing separation of duties between developers, testers, and approvers. Without clear controls in place, organizations risk unapproved modifications to financial systems, increasing the potential for errors or fraud. For example, an insurance company may fail to monitor SoD in change management. As a result, developers may deploy unwanted modifications to the medical bill processing system.
These challenges and common failures highlight the critical need for proactive identity governance and automated controls that ensure SOC 1 readiness. Organizations must address these gaps with modern security tools to maintain strong financial controls and remain audit-ready.
How Can Veza Help with SOC 1 Compliance Automation and Audit Readiness?
Ensuring continuous SOC 1 compliance requires proactive identity governance, automated enforcement of access policies, and real-time monitoring. Many organizations struggle with manual processes, lack of visibility into access controls, and fragmented security tools.
Veza simplifies compliance by centralizing access control and automating key processes and helps organizations to keep competitive advantage in the marketplace.
Veza’s unique Access Graph provides full visibility into who has access to what within your environment. Then atop the Access Graph, Veza’s Access Governance and Access Intelligence products equip organizations with modern tools to efficiently manage controls at scale, helping to maintain SOC 1 compliance audit readiness while reducing manual effort and costs with automation.
Quick Start Guide on Implementing SOC1 Controls with Veza
- Phase 1: Connect core systems to establish baseline visibility.
- Phase 2: Automate access controls and enforce SoD rules.
- Phase 3: Set up compliance dashboards for continuous monitoring.
- Phase 4: Enable real-time violation detection to prevent compliance failures.
Automating Logical Security Controls
Without automation, organizations risk excessive privileges, untracked changes, and missed compliance deadlines. Veza ensures SOC 1 audit readiness and continuous oversight by automating key identity security processes, including:
- User Access Review: Veza Access Reviews supports user access reviews for regular and privileged users. It also pulls in non-human identities and local application accounts. Additionally, Veza provides visibility into nested groups and roles, offering full transparency on inherited access, as well as full permissions on resources.
- User Provisioning and Deprovisioning: Veza Lifecycle Management and Access Requests allow organizations to operationalize and automate their security policies related to birthright user provisioning and just-in-time access requests. These processes are augmented with policy-based approval workflows and automated deprovisioning when users no longer require access or depart the organization. This ensures timely provisioning and deprovisioning for joiners, movers, and leavers, as well as just-in-time access to applications and resources when required. This approach also helps minimize standing privilege within in-scope systems.
- Authentication: Veza Access Intelligence allows the configuration of the organization’s authentication policy and flagging violations. Security teams can identify violations such as missing MFA enforcement, weak password policies, and bypassed Single Sign-On (SSO).
Strengthening Cyber Incidents Response
In the event of a security breach, Veza supports blast radius analysis, helping organizations mitigate potential damage and reduce the financial impact. For example, if an attacker gains unauthorized access to a finance system, Veza can immediately identify all affected accounts, revoke access, and generate compliance reports to document the incident response—ensuring minimal business disruption. Veza Access Intelligence, Access Monitoring, and Non-Human Identity Security strengthen identity and data security monitoring by continuously scanning permissions for security misconfigurations, deviations from best practices, access risks and compliance violations.
Continuous Monitoring of SoD in Business & Change Management Controls
Veza supports the effective implementation of separation of duties (SoD) through its SoD capabilities within Veza Advanced Access Intelligence. For instance, Veza can detect if an employee has permissions for approving invoices in NetSuite and creating invoices in Coupa. It prevents conflicts of interest that could lead to fraud and inaccurate financial reporting. Veza enforces real-time SoD monitoring through alerting when conflicts arise. Using cross-application analysis, Veza ensures proper segregation of duties across SaaS, cloud, on-prem and legacy systems. Here are some examples of the visibility that Veza’s platform can provide:
Change Management Controls:
- Enforcing SoD between software development and production deployment (e.g., flagging SOC1-related GitHub repositories without branch protection).
- Monitoring SoD between developers, testers, and approvers.
Business Process Controls:
- Detecting conflicts where an individual both enters invoices and approves payments.
- Identifying users with dual permissions for wire transfers and bank statement reconciliation.
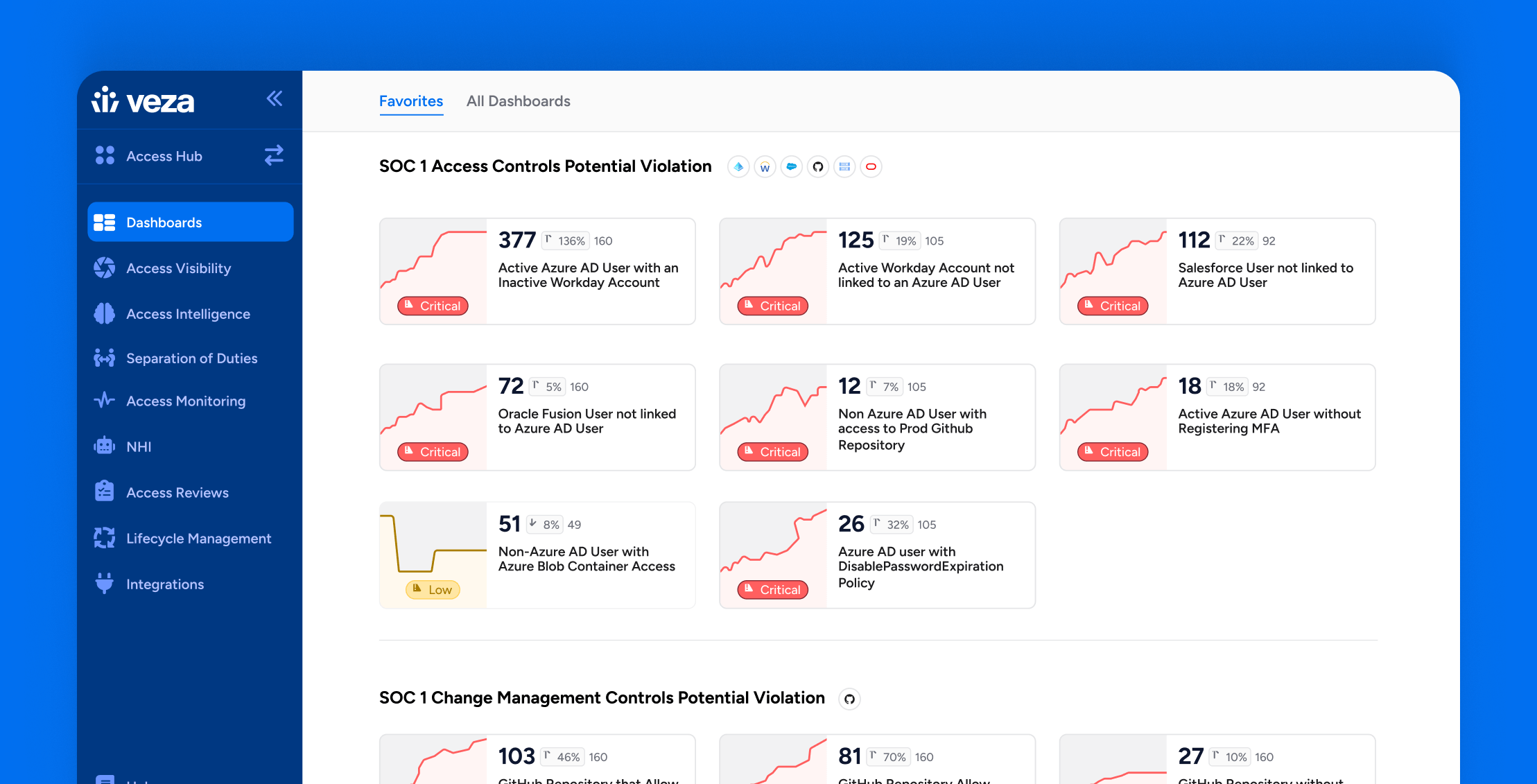
Audit-Ready Reports & SOC 1 Dashboards
All of the aforementioned Veza products provide audit-ready reports to demonstrate the design and operational effectiveness of SOC 1 controls. Additionally, a configurable SOC 1 Dashboard built into the Veza platform enables immediate visibility and monitoring of SOC 1 compliance within your environment. Imagine a near real-time dashboard that continuously monitors compliance status, flagging SoD violations, unauthorized access, and policy deviations. Veza’s SOC 1 Dashboard provides an at-a-glance view of compliance health, enabling proactive remediation before audits occur.
Best Practice for SOC 1 Audit Readiness
Here are some best practices for maintaining SOC 1 compliance; however, for more specific guidance for your organization and industry, please consult your internal and/or external audit partners.
- Define Policies – Define clear policies on IT security and financial reporting.
- Monitor Controls – Implement and monitor access controls, change management, risk management and financial reporting processes.
- Test Internally – Perform internal audits periodically on relevant controls to find weaknesses.
- Fix Issues – Address control gaps in a timely and continuously improved process.
- Train Employees – Ensure your staff understands SOC 1 requirements and their roles.
By implementing automated access governance and continuous monitoring, Veza can help organizations significantly reduce the burden of SOC 1 compliance and improve security posture.
See how Veza enables SOC1 compliance automation for leading enterprises. Request a Demo today.
See how our customer used Veza to simplify their compliance programs:
- https://veza.com/resources/blackstone-case-study/
- https://veza.com/resources/sallie-mae-case-study/
- https://veza.com/resources/copperpoint-case-study/
- https://veza.com/resources/customers-genesys/
- https://veza.com/resources/barracuda-case-study/
- https://veza.com/resources/choice-hotels-case-study/
Curious how Veza supports the SOX program? Click here.
About the Author

Amber Li is a Principal Product Manager at Veza, focused on building next-generation Access Governance solutions to help organizations manage identity risks. Prior to Veza, she spent 13 years at Deloitte’s Risk Advisory division, assisting large enterprises in designing and implementing access controls, SoD, and change management frameworks. With extensive experience working alongside compliance teams, Amber has helped companies achieve compliance with SOX, SOC, ISO standards, and other regulations. She also was an external auditor for many organizations.




