For identity, security, and audit & compliance teams, access reviews invariably mean that heavy, manual, and unpleasant burden that comes around several times per year. Reviewers are equally unhappy as they’re presented with massive spreadsheets of entitlements, lacking the critical context needed to make informed decisions. Veza’s risk-based access reviews solve these fundamental problems by transforming access recertification from a static, reactive process into a dynamic, risk-driven operation.
Risk-based access reviews and recertifications are built on the principle of providing a continuous, adaptive review of access entitlements based on access risk and least privilege. Besides tackling the essential use cases for access recertification: automating periodic review of user access to prevent entitlement creep and reduce stale or unnecessary access as a means to comply with regulatory mandates, Veza goes further by tightly coupling continuous risk monitoring with the review process. This is enabled with two powerful capabilities: event-driven on-demand reviews and risk-contextualized decision-making.
Use Case 1: Least Privilege Access Risks and Risky Events Trigger On-Demand Access Reviews
Traditional access reviews operate on a fixed calendar schedule, meaning risky access often persists unaddressed until the next audit cycle. Veza shifts this paradigm by enabling on-demand reviews triggered by real-time detection of risky events (i.e. over permissioning, dormant access, privilege drift, residual access, etc.) – powered by Veza Access Intelligence.
This capability monitors the blast radius of critical access. For instance, if a user’s risk score suddenly spikes due to a privilege escalation or a highly sensitive data store becomes accessible to users who don’t have MFA enabled, Veza can immediately trigger a surgical, targeted review for only the specific high-risk users/entitlements impacted.
This approach ensures that the user access review process is preventative and efficient. Instead of reviewing thousands of low-risk users, the system only initiates reviews for the handful of users/resources that pose an immediate threat to the organization. These security-driven reviews are faster, more focused, and significantly improve the organization’s security posture in real-time.
Use Case 2: Risk Context for Intelligent, Informed Review Decisions
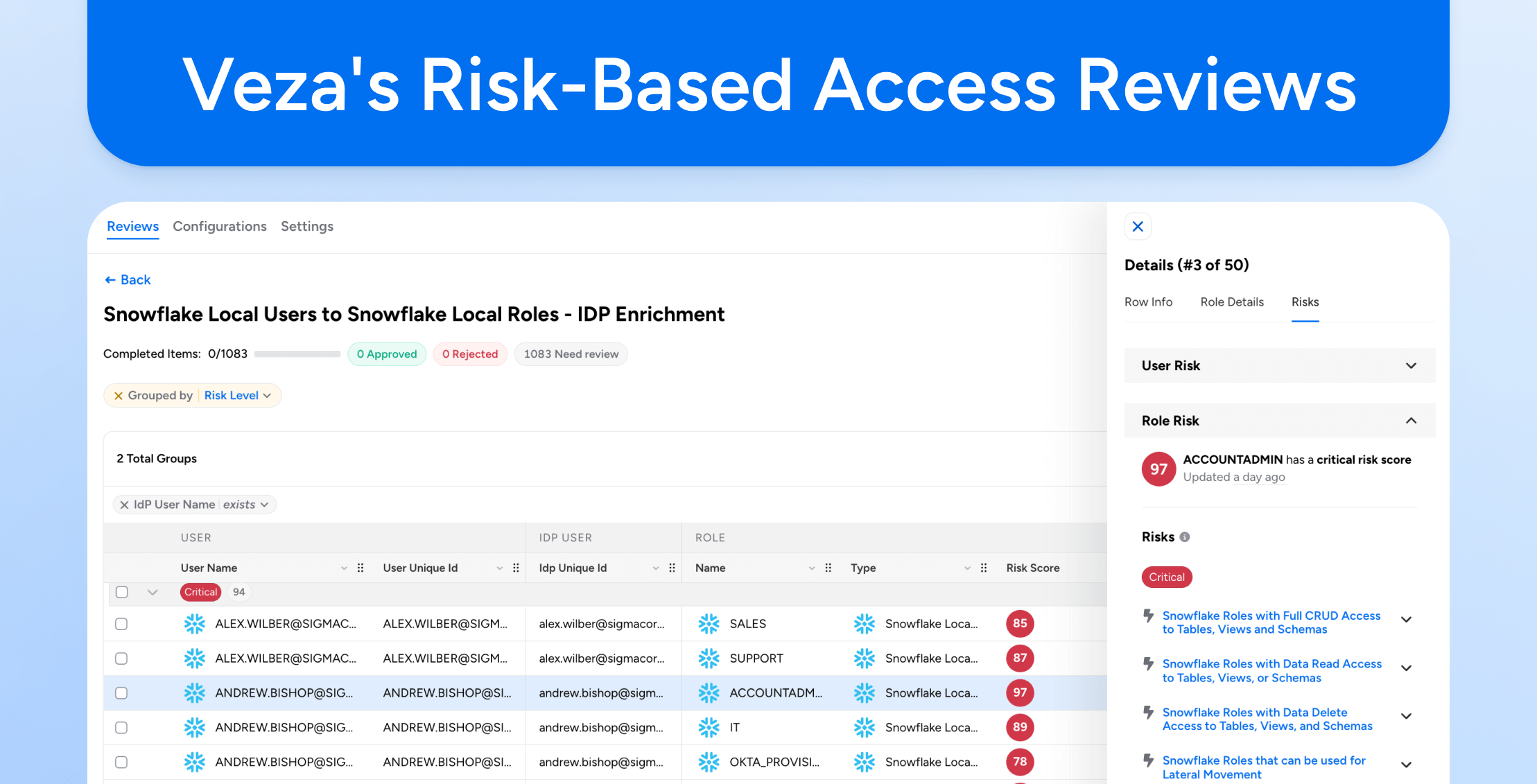
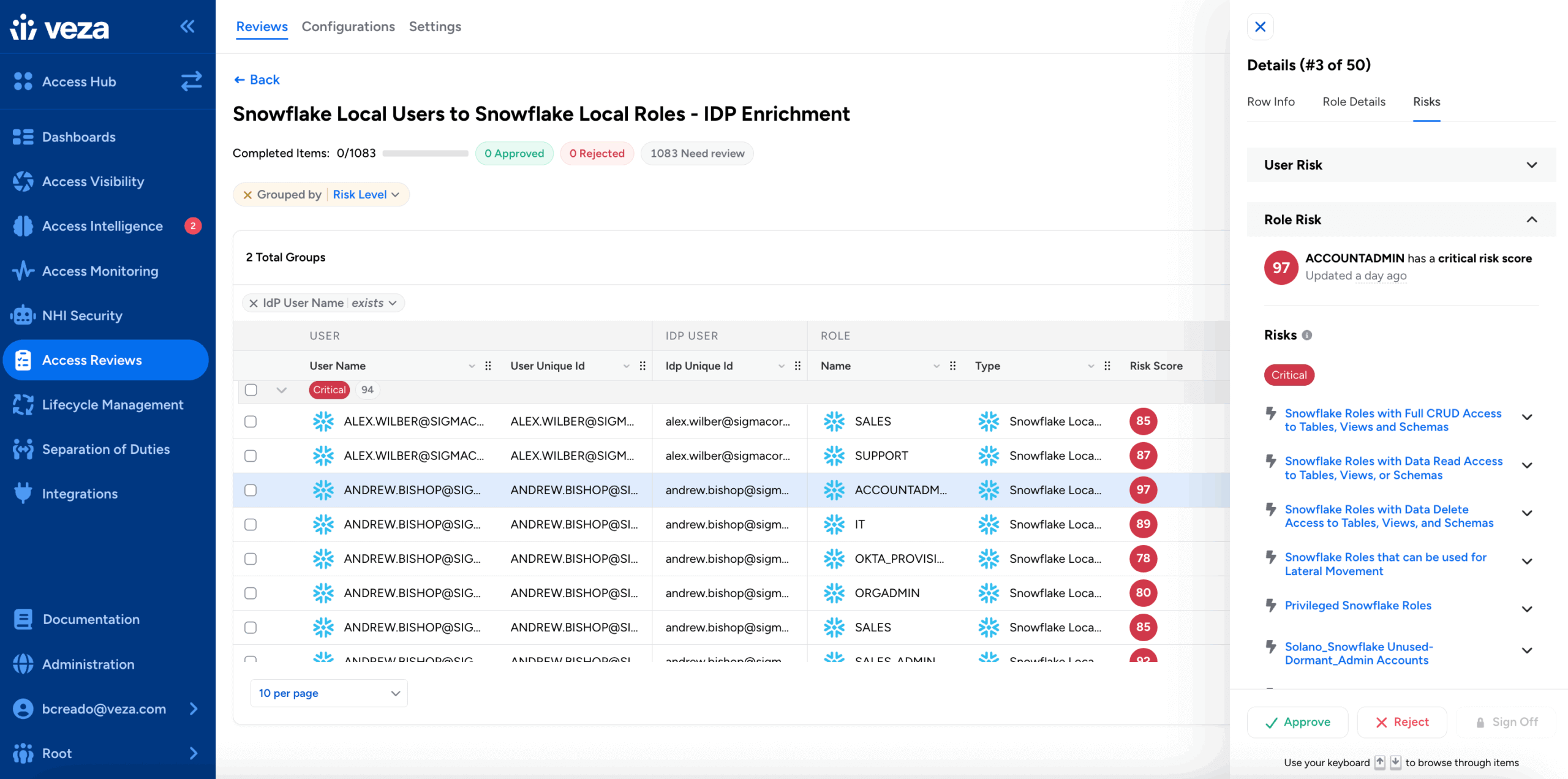
Even when a review is triggered, a reviewer’s primary challenge is the lack of information and context necessary to certify or revoke access. To address this, Veza injects a comprehensive risk context directly into the review workflow, empowering reviewers to make accurate decisions quickly.
Within the consumer-grade reviewer interface, the access being reviewed is immediately labeled with its associated risk scores. This score – fully utilizing the improved fidelity and scoring of Veza’s Risk Score 2.0 algorithm provides an immediate, quantitative assessment of risk, including an explanatory breakdown of the risk components, such as privilege level, separation of duties violations, exposure potential, vulnerabilities associated with the user or their accounts, access outliers, and more. Reviewers instantly know the severity of risk for each access line item that they are dealing with—e.g., whether it’s an admin user without MFA enabled or a privileged role, or a delete access to data in an AWS S3 bucket, or a member of their team granted access to unusual or rare entitlements compared to other team members.
One of the most crucial pieces of context is the access monitoring usage data related to a specific identity. Unlike systems that only track the last time a user logged into a cloud platform, Veza can monitor the last time the user actively exercised a specific role or access against a resource being reviewed. For instance, this is the difference between seeing that a user logged into Snowflake 15 days ago vs. seeing that the user logged into Snowflake and last utilized the Sales_Admin role 15 days ago based on their activity. Importantly, knowledge of a lack of recent usage of a role or entitlement can be used by a reviewer as objective evidence to confidently revoke access, directly combating entitlement creep.
Veza Access Reviews is much more than a compliance tool to automate periodic access recertification campaigns; it can be leveraged as a strategic risk management control for all identity security use cases. By targeting high-risk users and resources using security event-driven triggers, enriching reviews with user activity data and the risk detection capabilities of Access Intelligence using the quantitative rigor of Risk Score 2.0, Veza Access Reviews helps Identity, Security, and Compliance teams transform their access recertification program from solely compliance-driven to risk-based. This integrated, intelligence-driven approach ensures:
- Continuous, automated enforcement of access hygiene
- Active enforcement of the principle of least privilege, and
- Effective shrinking of the attack surface
This helps guarantee that critical, in-scope applications, platforms, and systems remain protected at all times.
Choose what to do next
- Calibrate your review blast radius. Run a quick sanity check on scope, reviewer load, and policy drift with the Access Reviews data sheet.
- Watch continuous governance in motion. Prefer proof to promise. See how teams make identity risk visible, measurable, and actionable in the ISPM webinar.
- Turn decisions into shipped change. Baseline posture and prioritize least-privilege fixes with the self-guided Identity Security Assessment.
- See a tailored walk-through. Get a guided demo of risk-based reviews and Access Intelligence mapped to your priorities and tech stack.





