Introduction
Problem Statement:
Enterprises today face escalating challenges in managing identity security across both human and non-human identities. Compliance demands, privilege escalation, toxic access combinations, and shadow IT all contribute to risk. The traditional, reactive approach to access governance is no longer sufficient. Enterprises need a new operating model—one built for automation, agility, and continuous remediation.
Solution Overview:
Veza Actions transforms identity security from a passive control mechanism into an active operational engine. By automating access remediation and operationalizing responses to access risks in near real-time, Veza enables organizations to secure their environments continuously.
Veza Actions is purpose-built to operationalize identity security at scale, enabling:
- Real-time remediation for access risks
- Automated orchestration of identity workflows
- End-to-end visibility, analysis, and enforcement — all from a single platform
Veza’s Role:
Veza operationalizes identity security by embedding it directly into daily operations, transforming access governance from a reactive control into a proactive, automated process. With platform capabilities like Access Graph, Access Monitoring, Access AI, and Veza Actions, organizations gain continuous visibility, intelligent detection, and real-time remediation—all from a single platform. The result: identity security that’s always on, always actionable, and always aligned with the pace of the business.
What are Veza Actions?
Veza Actions is the operational muscle of the identity security platform — the arms and hands that automate identity decisions at scale. It powers the most critical access use cases, including:
- Identity security posture management
- Privileged access monitoring
- Cloud Entitlement Management
- SaaS access security
- Non-human identity (NHI) discovery and lifecycle
- Data system access governance
- Agentic AI security
Veza Actions doesn’t just alert — it empowers teams to automatically take action through intelligent automation. It’s how organizations operationalize access decisions and enforce identity controls in near real-time, as risks emerge.
Actionability Across the Organization
Access risks don’t exist in isolation. Veza Actions enables secure and agile remediation across teams:
- Security teams can trigger hyper-automated playbooks.
- App owners and data owners receive direct access to insights and workflows.
- Business units (HR, Finance, etc.) are empowered to review and remediate risks in their domains.
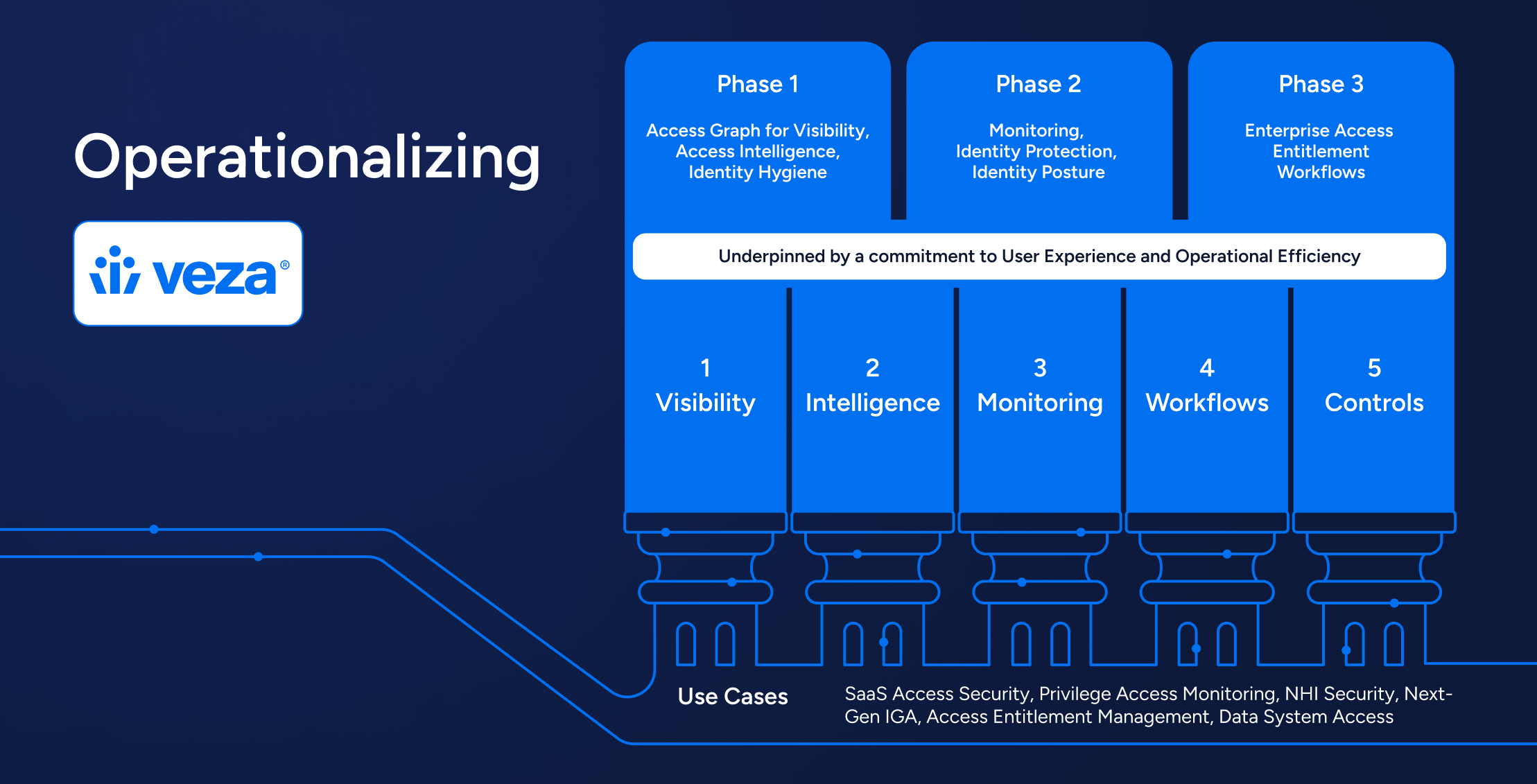
How Veza Actions Operationalizes Identity Security
1. Visibility That Drives Action
With Veza Graph + Access Visibility + Access Intelligence, organizations get a unified view of all identities, permissions, and entitlements. This visibility becomes actionable through Veza Actions, enabling quick resolution of risky access or excessive privileges.
The Push: Full visibility allows teams to remediate instantly, not days later.
Source: Veza Access Graph Overview
2. Near Real-Time Monitoring and Smart Alerts
With Veza Access Monitoring, alerts are no longer passive notifications. Instead, via Veza Actions, they trigger automated remediation workflows integrated with platforms like Jira, ServiceNow, Slack, Tines, or Torq.
- Example: A privileged access anomaly in AWS can auto-trigger a Jira ticket for the cloud engineering team without any manual steps.
The Push: Access Monitoring + Veza Actions = automatic remediation at the moment of risk.
Source: Veza Access Monitoring
3. Automation Across Identity Workflows
Veza Actions enables seamless execution of common identity security workflows, including:
- Access reviews when privilege escalation is detected
- Entitlement de-provisioning
- Toxic combination detection + revocation from AD/Okta
- Privileged elevation alerts that trigger access decisions
- Policy violations that auto-create engineering tickets
The Push: Identity security tasks don’t sit in a queue—they happen instantaneously
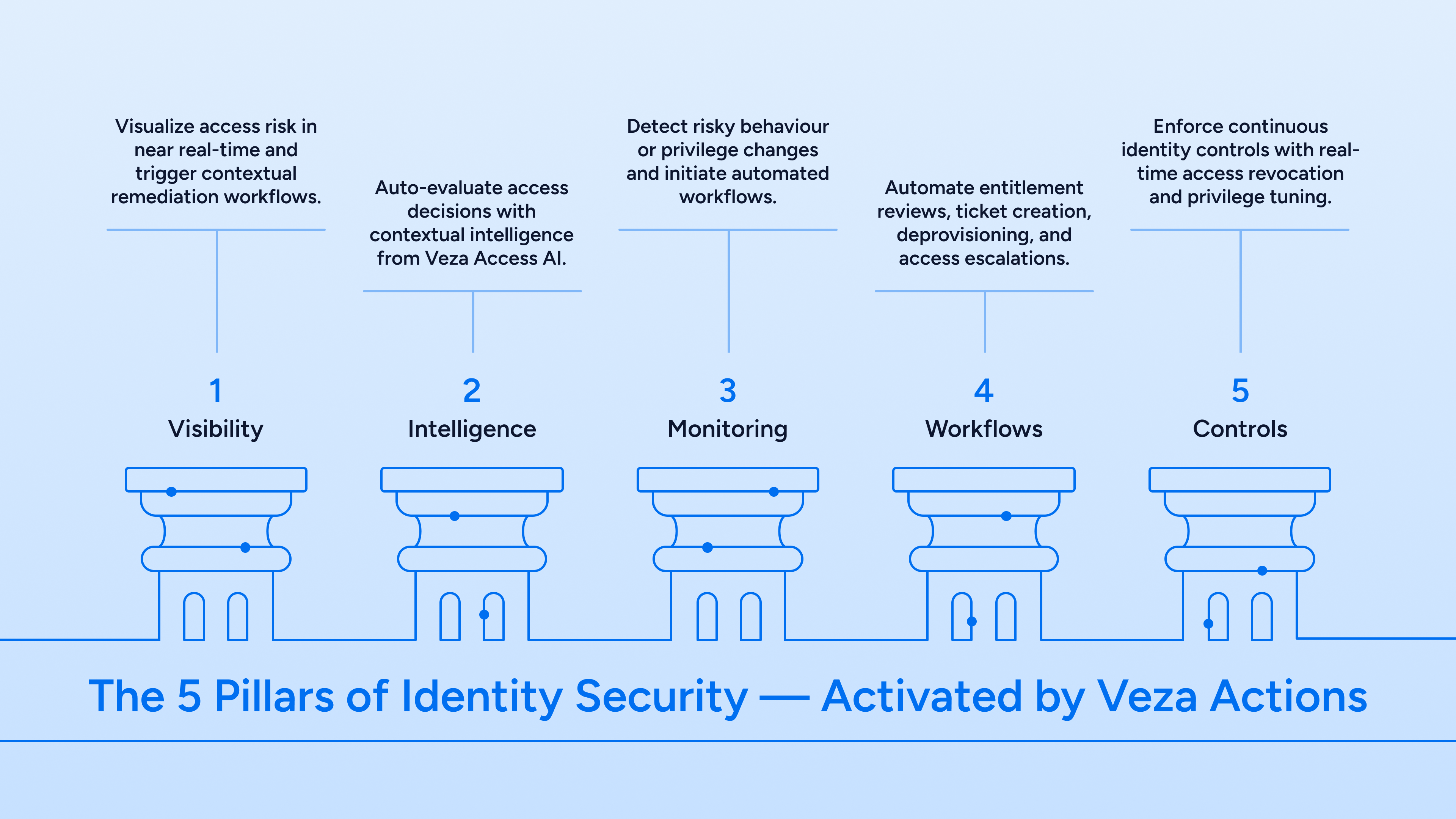
The Push: All five pillars work together under Veza Actions to deliver continuous, automated security.
Source: Veza Platform Overview
Veza Actions In Practice: Sample Use Cases
Privileged Access Alert → Hyper-Automated Orchestration
- Detects high-risk access events, like AWS root user logins or sudden privilege escalation.
- Automatically notifies the security team, disables the session or revokes access, and triggers an orchestrated response across Jira and Slack — all without manual intervention.
Toxic Combination Detected → De-Provision User
- Flags conflicting access — like a user with both Finance approval and Payments initiation rights, or a developer with unrestricted source code access and the ability to push directly to production.
- Automatically deprovisions risky entitlements in Okta and AD to eliminate toxic combinations before they’re exploited.
Access Policy Evaluation → Workflow Initiation
- Flag violations of defined access policies, such as public access to an S3 bucket or sensitive data exposure.
- Automatically generates a Jira ticket for the responsible CloudOps or Security team, kicking off a remediation workflow with full context.`
The Push: These aren’t hypotheticals—they’re automated and live within Veza today. Source: Tarun Thakur on LinkedIn
Conclusion: Continuous Remediation with Veza Actions
Veza Actions closes the loop on identity security. It’s no longer about identifying a problem and waiting for remediation. It’s about enabling organizations to operationalize security through real-time, smart automation.
With Veza Actions, you:
- Don’t wait for quarterly access reviews
- Don’t rely on disconnected alerts
- Don’t chase flagged compliance issues retroactively
Instead, you:
- Operationalize access control with intelligence
- Remediate identity risk as it emerges
- Empower business teams to act on the access they own
The Push: Identity security is no longer passive—it’s operational, proactive, and built to scale.
Call to Action
If your current identity governance approach is manual, reactive, or siloed, it’s time to explore how automation can operationalize identity security at scale.
Deepen Your Understanding
- Automated Access Revocation & Remediation at Scale
Learn how Veza Actions automates access deprovisioning and remediation, transforming identity security from reactive to proactive.
See It in Action
- The State of Access 2024: On-Demand Webinar
Explore how organizations are tackling the complexities of identity and access management. In this webinar, Veza experts—including Field CTO Tarek Khaled—unveil key findings from the State of Access 2024 report, offering practical insights into achieving least privilege and enhancing identity security.
Take Action
- Schedule a Demo
Ready to operationalize your identity security program? See how Veza helps automate remediation, enable cross-functional workflows, and drive continuous enforcement.
About the Contributors
This piece was developed by Matthew Romero, Technical Product Marketing Manager at Veza, in collaboration with Santosh Kumar, Senior Director of Product Management at Veza; Tarek Khaled, Field CTO; and Sandler Rubin, Senior Director of Product Management.
The contributors brought together perspectives from product, field, and engineering to explore how organizations can move beyond traditional identity governance. Their combined experience spans product development, customer challenges, and the evolving security landscape—shaping a conversation rooted in real-world complexity.





