Introduction
The authorization landscape is a high-velocity, ever-changing conundrum for the modern enterprise. Organizations are in constant motion: teams and projects restructure frequently while employees cycle in, out, and around the organization, driving a perpetual churn of joiners, movers, and leavers. Users constantly request and are granted new access to applications, systems, and other resources. Non-human identities (NHI) proliferate as new applications, workloads, agents, and services come online. And the list goes on.
Events like these result in a broad accumulation of access for users and NHIs over time. New users, of course, are granted a minimal set of access to applications and resources needed to become productive, whilst users changing roles need to have new and different types of access granted commensurate with their new responsibilities. Departing users, most obviously, need to have their access revoked upon termination. And, NHIs need to adhere to a strict governance and lifecycle process – clear ownership, the minimal level of permission for each NHI’s intended purpose, and assured destruction when each NHI reaches its end of life. All of this needs to be managed while ensuring that the principle of least privilege is adhered to.
Why calendar-based reviews leave a security gap
Periodic access recertification campaigns are one way that organizations have traditionally attempted to certify that least privilege is being enforced. These campaigns are intended to be very thorough – focusing on user and NHI access across a broad swath of “in-scope” applications, usually performed quarterly or twice a year (depending on the organization’s GRC requirements). But these campaigns suffer from major shortcomings.
Firstly, these campaigns are time-consuming and labor-intensive due to their expansive nature and stringent requirements – hence, it is neither desirable nor feasible to run these reviews more frequently than what’s absolutely mandated. The level of effort involved means that other instances when access needs to be reviewed in a more timely manner don’t happen.
What on-demand access reviews are
Assessments to maintain or reject access really need to be made in closer proximity to the material security or user mobility events; they really cannot wait for the next review cycle in order to reconcile. A review process that is anchored solely to a rigid, calendar-based cycle inherently creates a “security gap” – a window of time between cycles where the organization is vulnerable and exposed to elevated access risk; when least privilege cannot be assured.
This is exactly where on-demand access reviews – sometimes called micro-certifications – can enable contextual, risk-based access governance. This capability transforms static recertification campaigns on a “tick tock” cycle into a dynamic, event-based control that helps ensure that access is reviewed and validated precisely when critical events or changes are detected, not many weeks or months later.
The Veza platform allows organizations to create on-demand access reviews based on when a specific security incident or user mobility event is detected. This detection event acts as a trigger for the initiation of one or more on-demand access reviews.
Common scenarios for implementing on-demand reviews include:
- Worker JML (Joiner, Mover, Leaver) events, especially Leaver and Mover:
- Certifying existing access when users need to be assigned new roles
- Validating new and preexisting access when a user transfers departments, gets promoted, or changes job function, and accumulates new access entitlements
- Immediately initiating a review of access upon employee termination to certify the swift removal of any residual access
- Validating permissions after a security incident occurs, such as MFA being disabled or a privilege escalation on a user’s account
- Reviewing a compromised user’s account access following an access breach to ascertain the blast radius
- Reviewing accounts newly detected as being orphaned or inactive
- Reviewing access for users observed having unusual or anomalous activity such as off-peak access, access from atypical locations, etc.
- Reviewing orphaned, inactive, or stale service accounts and keys, reducing the risk associated with long-lived NHIs.
Creating on-demand reviews
The Veza platform allows on-demand review triggers to be configured from either Veza Access Intelligence or Veza Lifecycle Management. On-demand review triggers from Access Intelligence rely on the in-built alerting and actioning framework that’s especially geared toward detecting both security and user record change events. Alternatively, Lifecycle Management workflows are designed to immediately execute when JML events are detected on the organization’s HR system or other authoritative source of identity, such as the payroll system or IDP. As such, native actions within Lifecycle Management workflows can immediately create and launch on-demand access reviews when JML events are detected.
Triggering on-demand reviews using Access Intelligence alerts
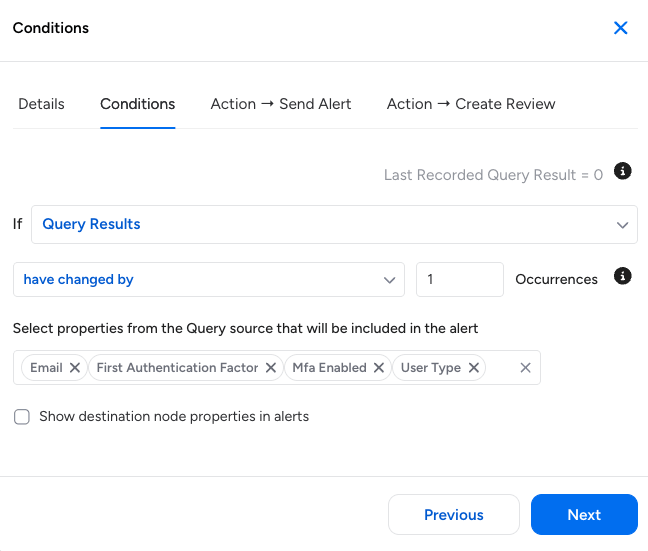
Access Intelligence rules and alerts provide an ideal framework for triggering access reviews when a property related to a user changes. These rules function as continuous security monitors – actively looking for user metadata or authorization state drift against defined baselines. When a deviation is detected, the rule’s configured action fires to create a new on-demand access review.
Example scenarios:
- A user is granted an additional role/permission, especially a privileged role/permission
- Access to a storage bucket/database table changes from read to write
- MFA suddenly goes from enabled to disabled for a user
- Users with access go dormant/inactive
- A user is granted new access, causing them to now violate a separation of duties (SoD) policy
- An API token expires
- A user’s risk score suddenly elevates beyond a certain threshold
These examples are just some of the security events that can be detected by Veza Access Intelligence by creating rules on queries and monitoring the output count of these queries. If the output count of a query is equal to/greater/less than a specific value or changes by a certain threshold value or percentage, Access Intelligence can trigger an access review – one among many other actions.
Specifically, Veza can create an alert for a predefined change and, in response, create an on-demand access review that necessitates the timely review and consequential approval/rejection of this updated access.
Triggering on-demand reviews as actions in Lifecycle Management workflows
While Access Intelligence rules focus on detecting and responding to security events or authorization state drift, Lifecycle Management workflows execute based on external identity or user mobility events detected at an authoritative source of identity, such as the organization’s HR system or IDP. These can be the JML events – a new individual is joining the organization, an existing employee is changing job function or role, or an employee is being terminated. And, on-demand access reviews can be created as an action within an existing Lifecycle Management workflow tied to these events to serve as a mandated “checkpoint” within the broader workflow.
Example Scenario: Employee Changes Role
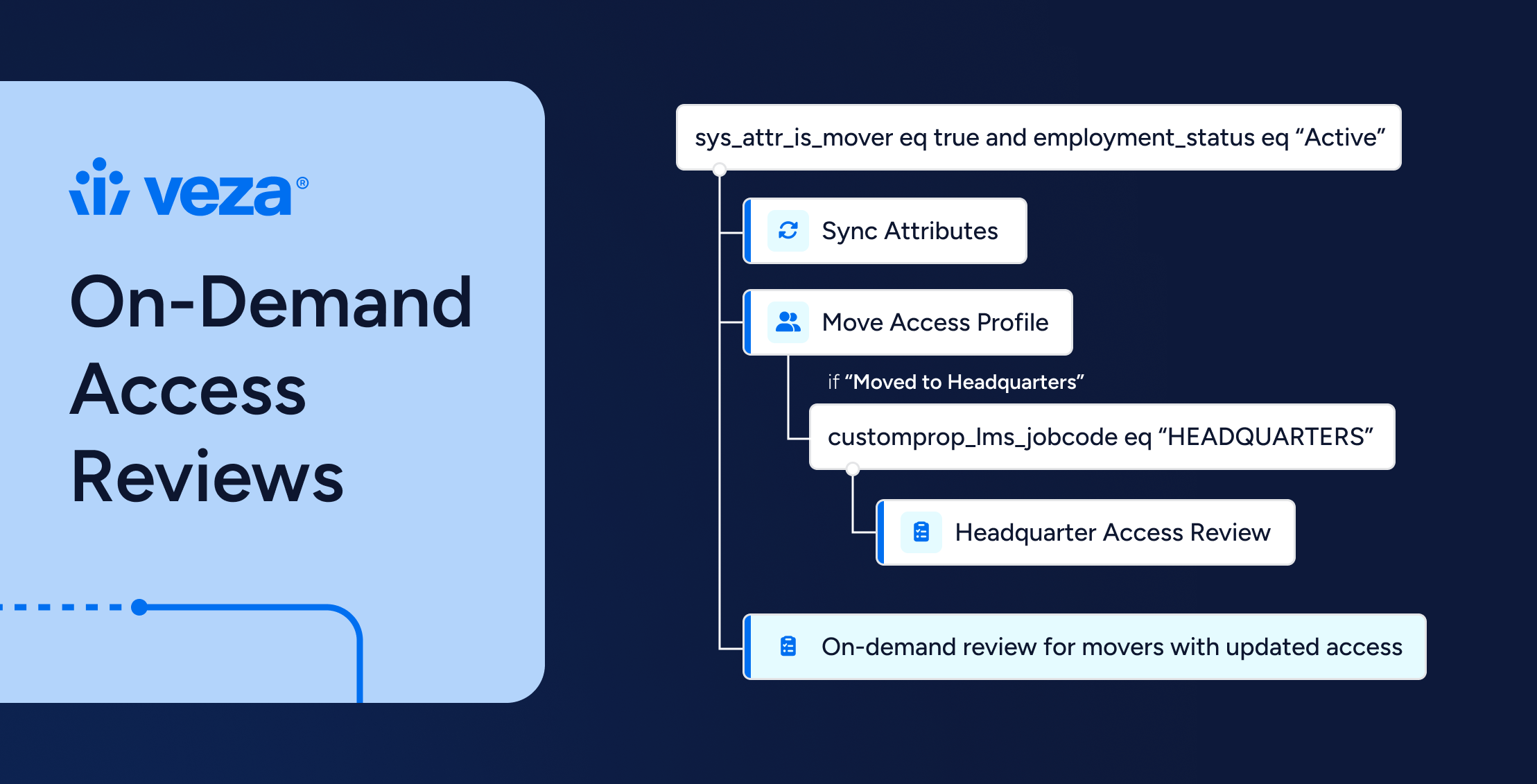
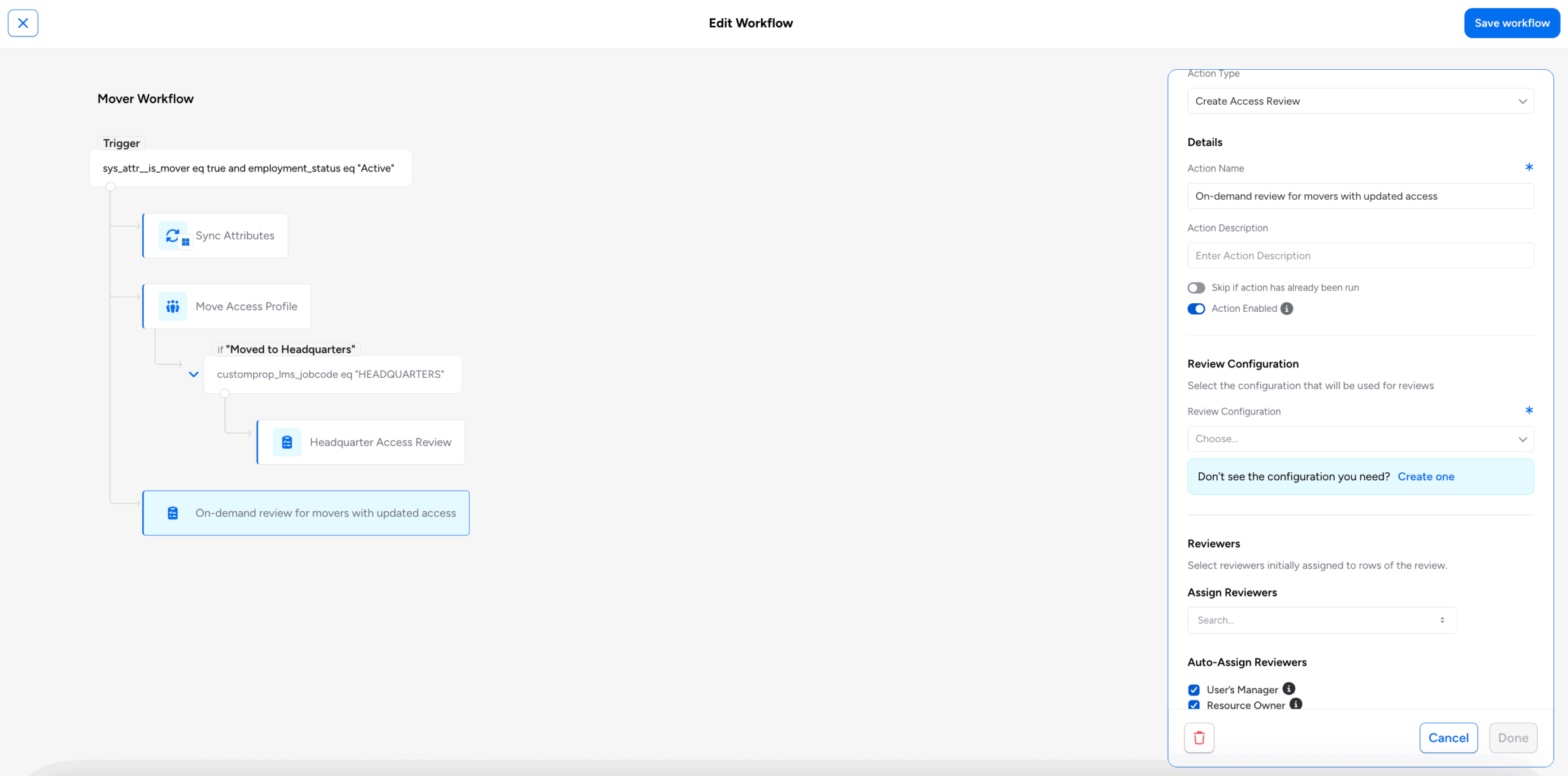
- Initiation: HR updates an employee record in the HRIS to reflect a new job code and title, department, and manager. This employee is changing roles.
- Workflow Execution: Veza Lifecycle Management detects the employee record change and executes the mover workflow. Many changes occur as part of this workflow, such as syncing the employee’s new job title, department, and manager details across applications and granting new access needed for her new role.
- Review Trigger: As part of the mover workflow, a Lifecycle Management action triggers the creation of access reviews for the “mover”. These reviews get auto-assigned to the mover’s new (i.e., current) manager and will determine how much of the mover’s accumulated access from her previous role should be justifiably maintained.
- Certification: These reviews focus specifically on the “mover”, asking her manager to justify the maintenance of any existing access and certify that no latent, unnecessary access remains for the mover across all applications. This step, combined with verifiable access removal, provides a final, auditable sign-off on the mover’s access.
By leveraging Lifecycle Management, on-demand reviews serve as a human-gated quality control layer for automated identity processes, ensuring that access is validated for completeness, ensuring compliance effectiveness immediately, not months later.
On-Demand Review Launch Configuration
Irrespective of whether on-demand reviews are triggered from an Access Intelligence alert or a Lifecycle Management workflow, several preparations are required:
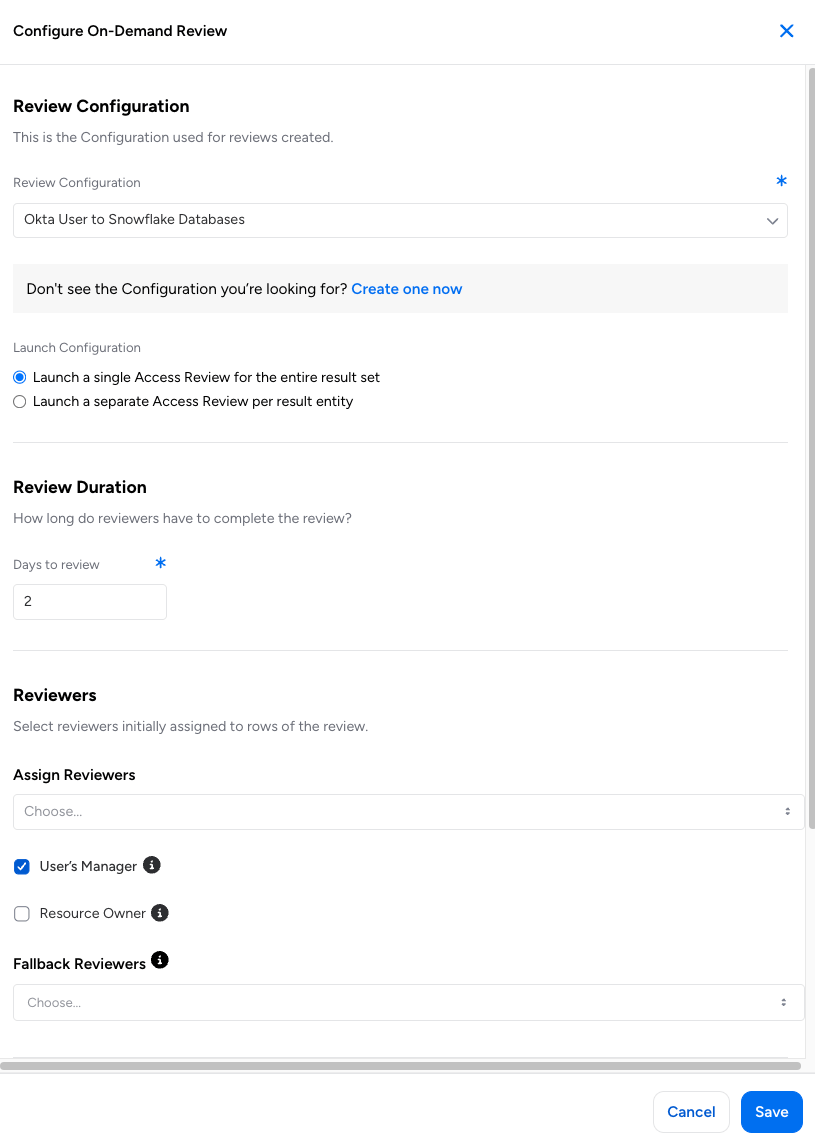
- Within Veza Access Reviews, a review configuration needs to be predefined. Review configurations define the scope of the review as well as other characteristics, such as the behavior of the review, what the reviewer can/cannot do in a review, and how the review is displayed to the reviewer.
- When configuring the Access Intelligence alert or Lifecycle Management action that actually triggers the review, the following must be specified:
- One or more review configurations from which to instantiate reviews on demand
- Criteria defining how those reviews get instantiated, such as whether the review requires single- or multi-level review, the duration of the review (i.e., relative due date from launch), default assigned reviewers, and more.
Additionally, administrators configuring Access Intelligence alerts can choose whether to launch a single review for the entire result set (Consolidated Mode) or launch separate reviews per result entity (Individual Mode). Which option is better depends on the use case that the on-demand review is intended to address.
Note: On-demand reviews launched from Lifecycle Management are always triggered in Individual Mode.
Consolidated Mode creates a single access review containing all entities that triggered the rule. The review uses the full result set from the original query used to trigger the alert. This typically works best for large datasets and broad policy enforcement, especially for reviews auto-assigned to application owners, since Consolidated Mode simplifies review management. For example, “Review all users with detected privilege escalations in Snowflake”.
Individual Mode creates separate reviews for each entity that triggered the rule. Each review is constrained to show only one of the specific entities that triggered the rule. This mode is ideal for reviews auto-assigned to the user’s managers since it enables entity-specific reviews, allowing more granular oversight with unique reviews for each resulting user. For example, “Review all residual access for Bradley, who just got offboarded”.
Important: Although access reviews are scoped by saved queries and Access Intelligence alerts are triggered by changes detected in saved query result sets, the saved query used to trigger the alert (i.e., triggering query) and the saved query used to scope the review (i.e. scoping query) DO NOT have to be the same. In fact, in most cases, these scoping and triggering queries end up being quite different.
For instance, imagine a scenario where administrators want to trigger an on-demand review of all privileged entitlements for individuals whose IDP user account exceeds a risk score threshold of 90. In this scenario:
Triggering Query:
IDP User where User Risk Score > 90
Scoping Query:
User to Role where Role.Is Privileged = True
Note that the triggering query and scoping query can be different because the results of the triggering query are used to dynamically constrain the scoping query when the on-demand review is launched.
Downstream Workflows
On-demand reviews can also benefit from the existing follow-on capabilities of Review Intelligence and Veza Actions. Review Intelligence accelerates completion of reviews by automatically recommending approval or rejection of specific line items based on specific attributes or prior decision data. Of course, Review Intelligence is optional since the criteria used to automate decision-making of quarterly access reviews may not necessarily be appropriate for on-demand reviews. Veza Actions leverage external integrations to trigger automated remediation workflows or notify users or other stakeholders when a line item has been rejected.
Conclusion
Veza’s on-demand review capabilities represent a critical leap forward in identity governance. They ensure access recertification is not solely tied to a fixed campaign schedule, but they enable organizations to transform recertifications into a proactive, risk-based, continuously executed control. Regardless of whether triggered by an Access Intelligence alert from a detected privilege drift or a user mobility event like an employee offboarding, on-demand reviews are created instantly and surgically scoped based on the specific event and user.
This approach ensures that access is recertified precisely when the risk changes, eliminating the security gap and establishing “always-on” access governance across the entire enterprise. It is a cornerstone for the transition from “check the box” compliance to real-time, risk-based identity governance.
Next Steps
Explore: 7 user access review software tools to know in 2025
Quick scan of current approaches and tradeoffs so you can benchmark what “good” looks like.
Learn: The Definitive Checklist for User Access Reviews
Practical steps to structure reviews and close gaps fast.
Engage: Request a demo
See event-driven reviews mapped to your environment.





