Sometimes, one reviewer simply isn’t enough. Reviews of high-privilege entitlements, in-scope applications, or complex environments often require multiple sets of eyes. In these cases, no single person has the complete context to determine whether a user’s access is truly appropriate. That’s where multi-level review becomes the smarter, more reliable approach.
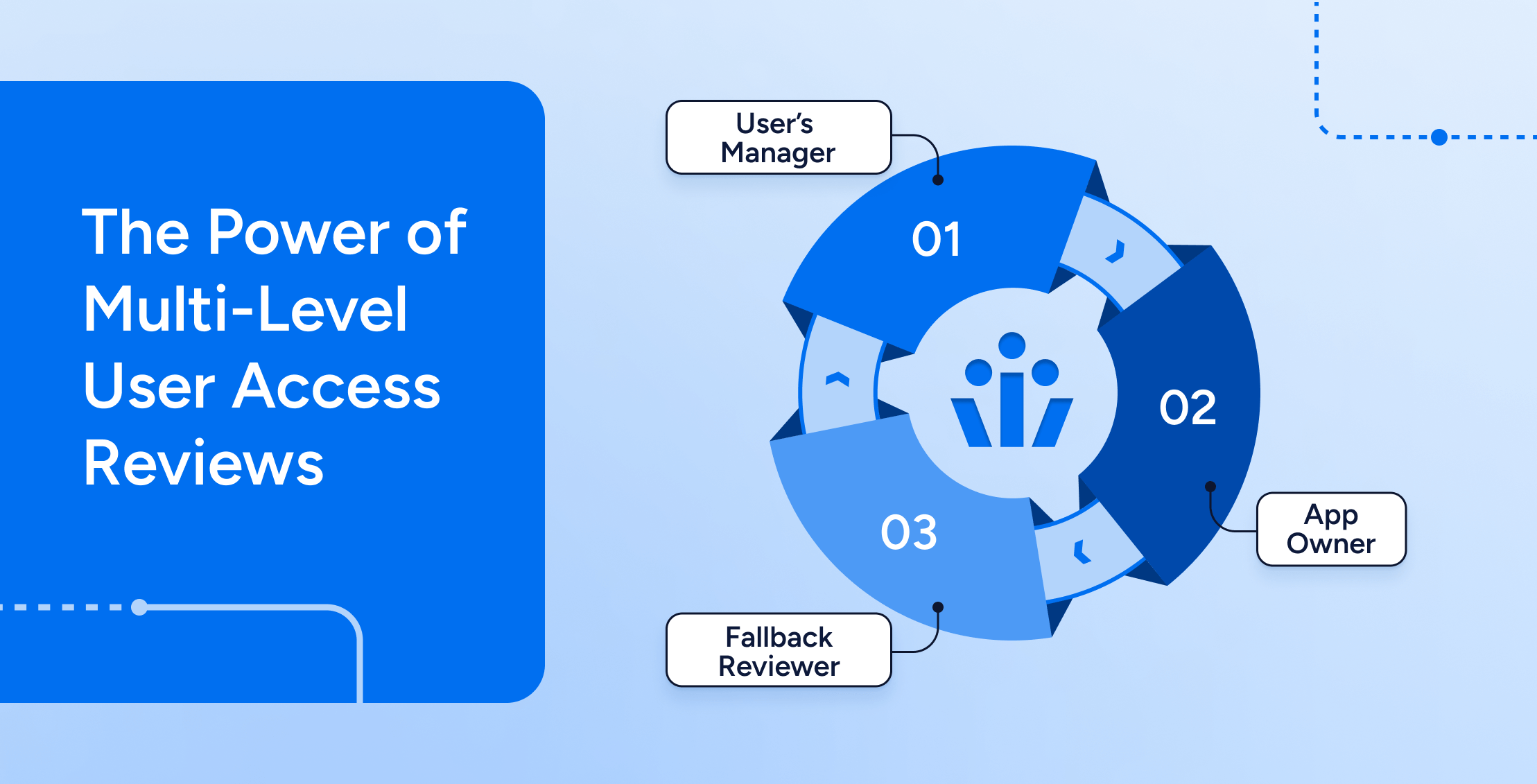
Veza’s multi-level review capabilities, a feature of Veza Advanced Access Reviews, add an additional required review level, ensuring access recertification decisions reflect reviews from separate parties. This ensures that different parties separately assess the different factors determining whether a user is qualified to maintain access. For instance, does the user have a legitimate, job-based justification for the access? This may be best assessed by the user’s manager. Additionally, is the user or some aspect of his access risky or within acceptable bounds? This may be best determined by an application, business process, or entitlement owner. Independently, neither of these parties are going to make a thorough or well-reasoned access recertification decision. Together, however, these separate parties can perform a more thorough review of user access – better than either party can achieve on their own.
Importantly, multi-level reviews are not the same as assigning multiple reviewers to the same items in a review. The latter creates a “first decision wins” situation, whichever reviewer acts first on the assigned line item effectively makes the decision and completes the task. This isn’t necessarily a bad practice – it’s actually very convenient in scenarios where any one of multiple individuals are legitimately authorized to make access recertification decisions. Think multiple system administrators or multiple application owners. On the other hand, multi-level reviews enforce a true dual-party control, requiring both parties (i.e. reviewers) to independently approve in sequence. This approach delivers more defensible access recertification decisions that stand up to audits and meet compliance requirements – one of the reasons why they’re frequently used for reviews of highly privileged entitlements or sensitive, in-scope applications and systems.
Unlike assigning a single level review to multiple reviewers, multi-level reviews run in sequence. Think of these reviews as having a Level One (L1) reviewer and a Level Two (L2) reviewer. L1 decides first whilst L2 sees only what passed the initial review by L1. Now, what passes (or fails to pass) depends on the configured decision mode for a multi-level review. But, a decision that doesn’t pass at L1 stops the process – eliminating the need for further review. This can be very efficient without necessarily compromising on oversight or running the risk of “rubber stamping”.
Use Cases for Multi-Level Access Reviews
Multi-level reviews address the need for heightened scrutiny and collaborative decision-making in UARs. By requiring multiple parties to sequentially review and sign off on access rows, organizations can enforce stricter controls, reduce the level of effort without resorting to rubber stamping, and create evidence that parties of distinct roles agreed.
Use this model when risk, privilege level, or blast radius is high, when segregation of duties (SoD) applies, or simply when auditors expect documented dual control. Typical patterns include:
1. Accelerating Multi-Stakeholder Consensus
For highly sensitive or business-critical applications, a single reviewer’s sign-off is not enough. Multi-level reviews mandate approval from different stakeholders who possess distinct knowledge bases and different perspectives, ensuring a more comprehensive risk assessment.
Example:
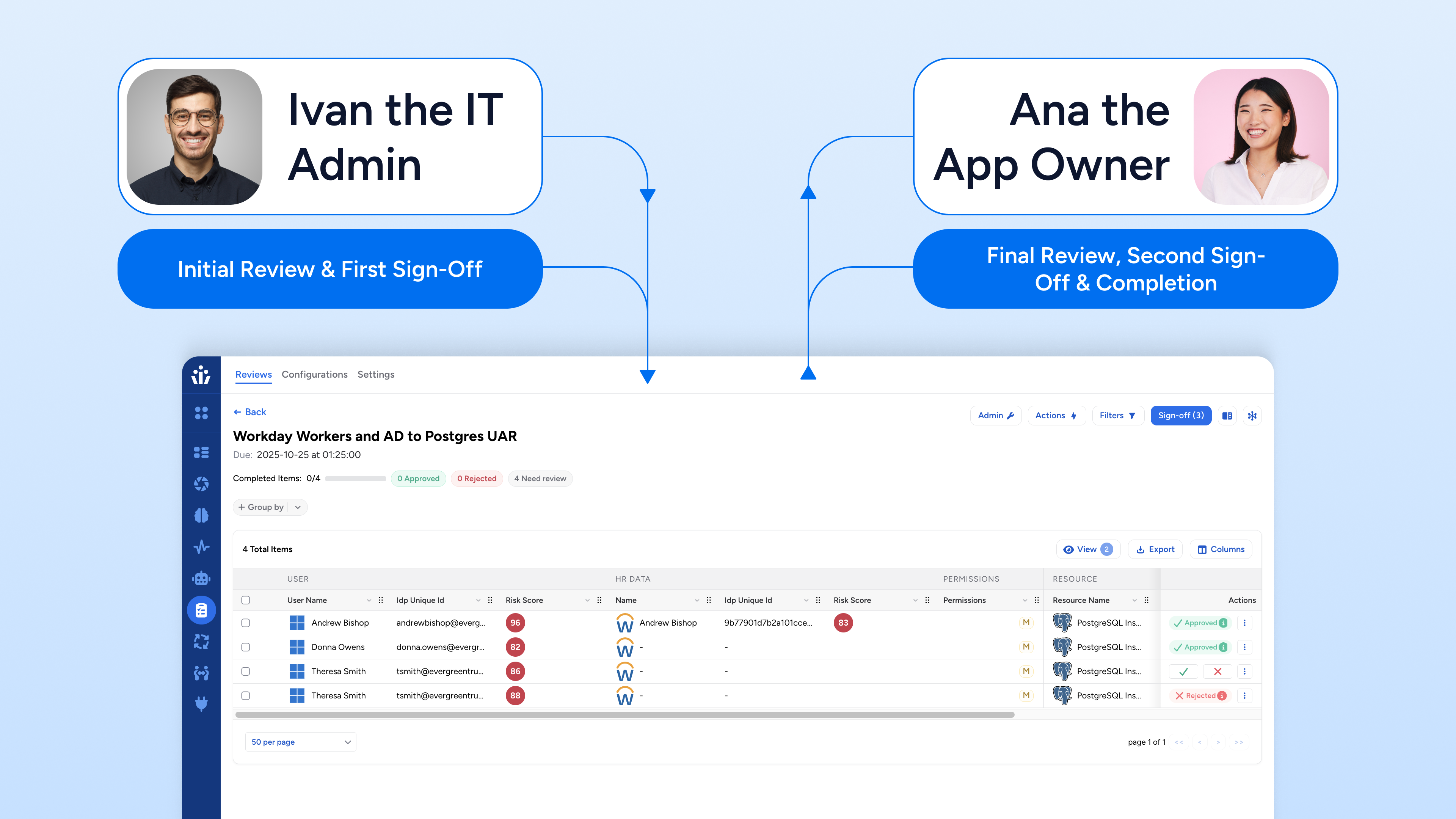
A common configuration is routing the L1 Review to the user’s manager who understands the user’s daily responsibilities and can confirm job need and actual use whilst assigning the L2 Review to the application owner, who validates resource fit, entitlements, and blast radius, resulting in a collective, informed decision.
The Benefit:
This dual sign-off ensures that the need for access (validated by the manager) and the risk associated with granting it (assessed by the application or resource owner) are thoroughly considered, strengthening the overall security posture. By default, both levels must unanimously approve for acceptance whilst a rejection at either level is final. Veza Advanced Access Reviews also supports configurable decision modes, additionally including unanimous rejection and last decision, to match your security policy or access risk tolerance – more about this in a bit.
2. Reducing Burden on Later-Stage Reviewers
Without a multi-level approach, application owners or security teams often face an overwhelming volume of access line items to review for recertifications. Stories abound about poor application owners being forced to review thousands and thousands of existing user and entitlement combinations in their own applications without a shred of context informing them who these users are – let alone what role or job function they may have in the organization that necessitates access. The invariable outcome? Rubber-stamping!
How Veza Helps:
The sequential nature of Veza’s multi-level review inherently acts as a filter. By default, L2 reviewers only see rows that “passed scrutiny” by L1 reviewers. This means that any access that didn’t “pass” at the first level is immediately bypassed from the subsequent review phase.
The Benefit:
This greatly reduces the workload for the final L2 approvers, allowing them to focus their attention and expertise only on the review line items that have already passed initial scrutiny.
3. Real World Examples of Strengthening Accountability and Audit Readiness
User access review campaigns often struggle to demonstrate clear accountability, who approved what, and on what basis. Multi-level reviews introduces a structured decisioning sequence that captures both levels, providing transparency into the review process.
In practice, L1 reviewers (such as managers) validate business justification for access, while L2 reviewers (such as application or data owners) confirm adherence to GRC and security requirements. Each step leaves an auditable trail of who reviewed, what decision was made, and when it occurred. This dual validation model ensures that approvals are not only accurate but also fully traceable, allowing organizations to produce verifiable evidence during audits.
The Benefit:
Multi-level reviews elevate UARs from a compliance checkbox to a defensible control, reducing audit gaps, minimizing a common rubber-stamp approval scenario, and demonstrating that access decisions are based on deliberate, accountable oversight.
How Veza’s Multi-Level User Access Reviews Work
Multi-level review is a sequential, two-tier process.
Two Sequential Review Levels
- L1 Review: This is the initial review phase where L1 reviewers make the first decisions on line items within the review.
- L1 reviewers are notified as soon as the review starts upon publishing. L1 reviewers can act on all assigned rows – as per normal.
- Multi-level reviews may be configured to auto-advance to L2 upon a) decisions on all rows have been completed and signed-off on reaching the L1 expiration date set on the review. Once an L1 reviewer signs off, the first-level reviewer cannot change their decisions, regardless of whether the review has proceeded to the second level or not.
- L2 Review: This is the final review phase where L2 reviewers act.
- L2 reviewers only see rows assigned to them along with the decisions made by earlier L1 reviewers. They can approve or reject the “passed”rows, but cannot change decisions on rows that were made at L1.
Decision Modes
Veza’s multi-level reviews offer flexible decision models that let administrators define how access decisions are finalized across multiple review stages based on the decisions made by the L1 or L2 reviewers. Depending on organizational policy or risk appetite, reviews can follow one of three decision modes.
- Unanimous approval requires that both the L1 and L2 reviewer must unanimously agree before access is considered approved — a single rejection automatically denies the line item. This is the most stringent decision model and Veza’s default behavior.
- Unanimous rejection flips the previous logic, allowing approval if any reviewer agrees, but requiring a consensus to reject. This is the most cautious approach for decisioning designed to minimize user disruption.
- Finally, Last decision gives authority to the final reviewer in the chain, whose decision determines the outcome regardless of prior inputs.
This flexibility enables organizations to tailor their review workflows to balance control, collaboration, and efficiency.
Automation and Visibility
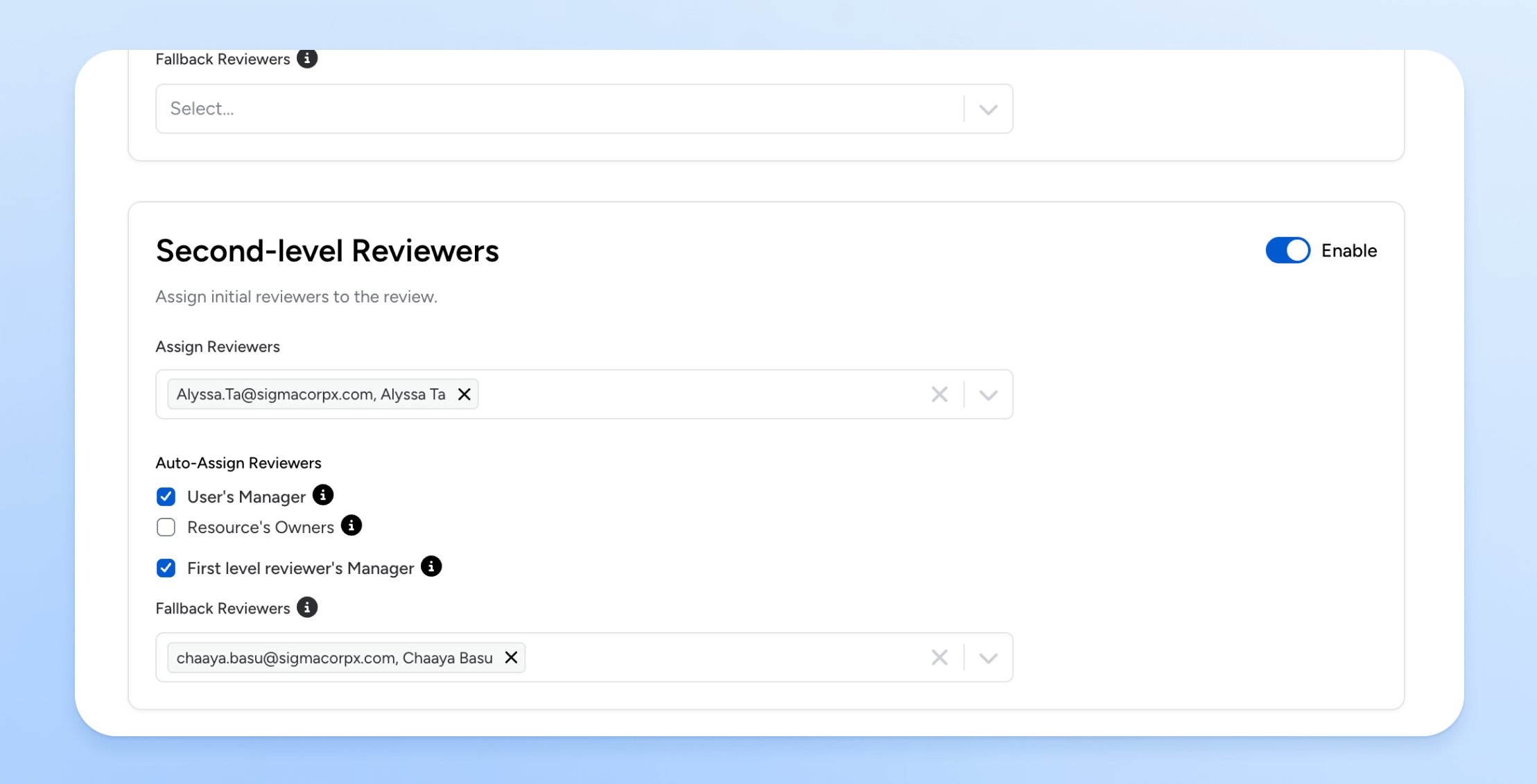
- Reviewer Assignment: Each level is assigned to different reviewers and both levels support reviewer auto-assignment. You can explicitly assign reviewers or auto-assign based on the user’s manager, the resource’s owner, or the first-level reviewer’s manager. As a safeguard, Veza automatically prevents the same user from being assigned L1 and L2 reviewer responsibility on the same line item in the review.
- Notifications: Review start notifications are sent to L1 reviewers when the review starts (if configured). L2 reviewers are notified only when their review phase begins. This precise timing prevents alert fatigue and confusion.
- Reporting: Reports generated for multi-level reviews document decisions at every level, helping auditors see exactly how each access recertification decision was made.
Veza Actions: Automation triggers are managed distinctly per level. Actions for rejected rows (e.g., revoking access via a webhook or creating a service desk ticket) or actions for approved rows trigger at the earliest level that the rejection or approval decision is locked in. However, this can vary depending on the decision model used.
By implementing multi-level reviews in Veza Advanced Access Reviews, organizations embed a crucial layer of accountability and diligence into their access governance process, significantly enhancing their security controls and compliance assurances.
Next Steps
Risk-Based Access Reviews
How to focus reviewers on what matters first.
Veza’s Risk-Based Access Reviews and Recertifications
Get the Definitive Checklist for User Access Reviews
A practical, step-by-step program to modernize reviews and pass audits.
Definitive Checklist for User Access Reviews – Veza
See a Live Multi-Level Review in Veza
Run a sample campaign and watch Actions handle approvals and revocations.
Schedule a demo – Veza





