Securing identity and access across today’s enterprise means managing permissions across hundreds of systems, from cloud platforms to SaaS applications. Veza’s advanced search capabilities provide security teams with unprecedented visibility into “who can access what” across their organization’s entire digital ecosystem.
Transforming Identity Security with Veza VQL
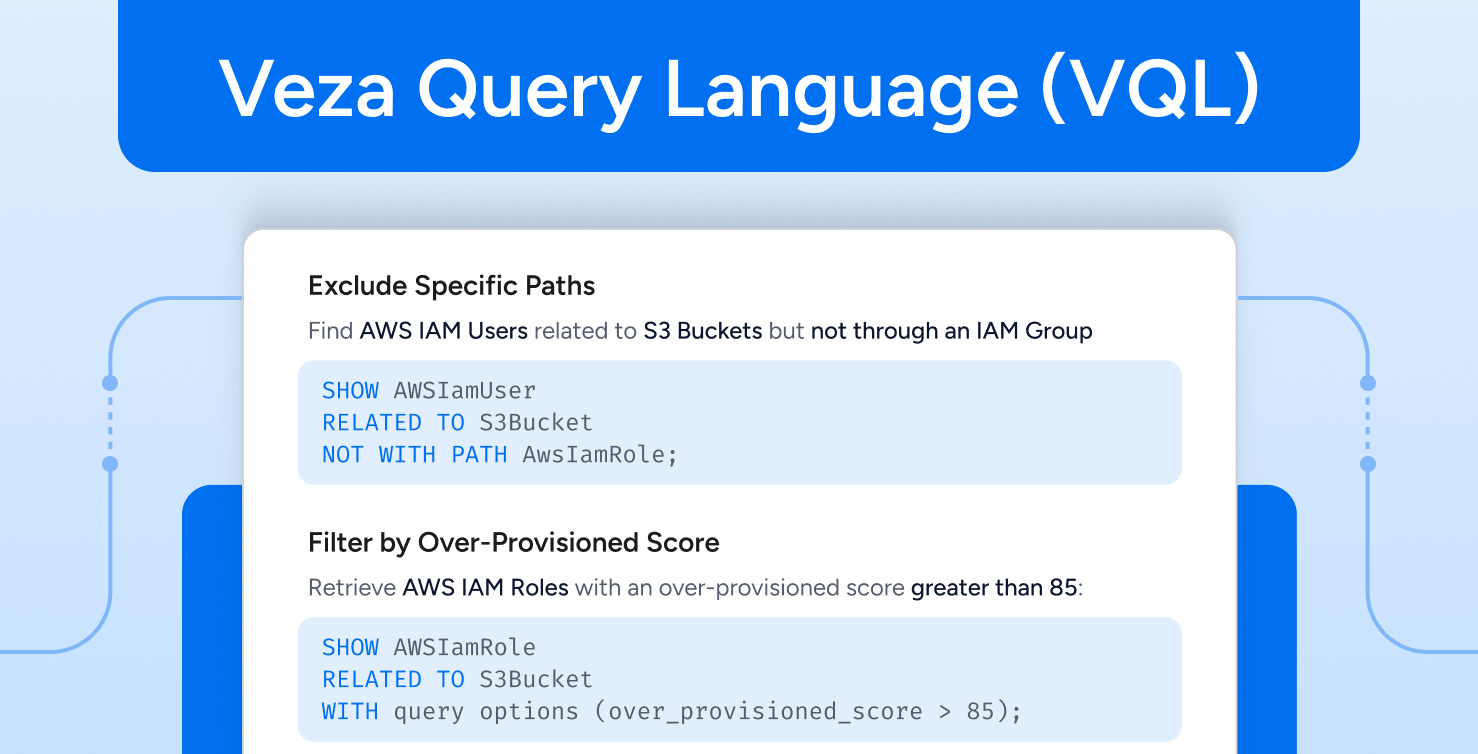
We’re excited to announce a major leap in Veza’s search functionality with VQL (Veza Query Language), our powerful yet intuitive SQL-like syntax designed specifically for identity access queries. VQL transforms complex query needs and requirements into approachable statements with a familiar syntax. For example, finding inactive service accounts with secret access becomes as simple as:
SHOW Identity
WHERE identity_type = 'NONHUMAN' AND is_active = false RELATED TO SecretThis simplicity helps security teams to rapidly identify access risks without specialized programming skills and a deep understanding of the schema mechanics. By making these capabilities accessible through both an interactive interface and a robust API, VQL empowers security professionals performing hands-on investigations (insider threat, access drift, responsible data handling, privilege drift, etc.). Additionally, VQL can be used to quickly build queries for ongoing monitoring of the security risks.
Why VQL
When analyzing your access risk landscape, the most important questions aren’t just about data—they’re about relationships. Who has access to what? How did they get that access? What paths exist between identities and sensitive resources?
While traditional SQL excels with relational databases, specialized graph query languages like Cypher and Gremlin are typically used for navigating complex graph relationships. However, these graph languages introduce a steep learning curve for security teams. Investigating whether a former employee retains backdoor access might require mastering complex graph traversal syntax—overwhelming users with their investigations.
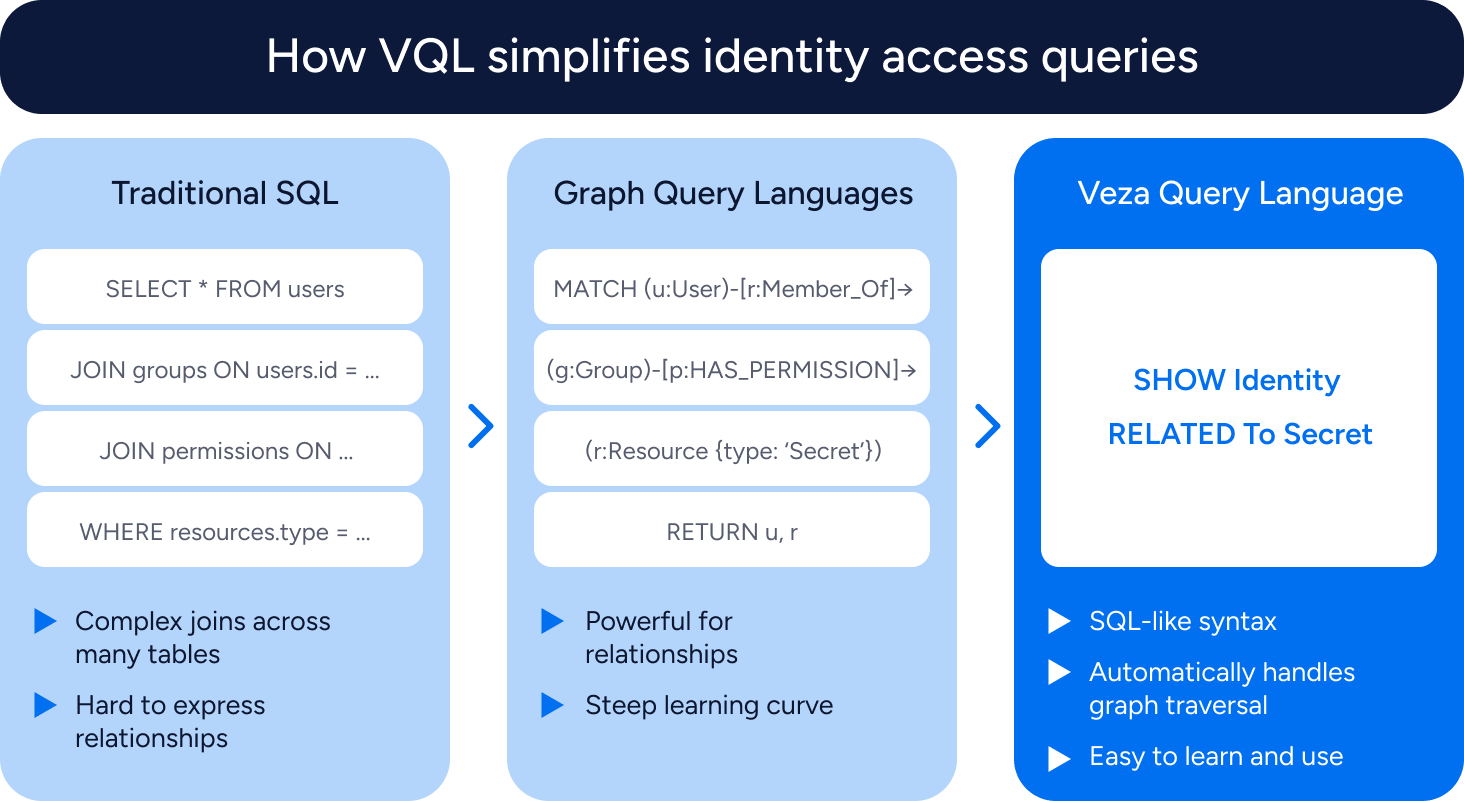
VQL bridges this gap with SQL-like syntax while automatically managing the complexity of permission paths behind the scenes. This enables our users to immediately write effective queries like:
SHOW Identity
WHERE identity_type = 'NONHUMAN' AND is_active = false
RELATED TO SnowflakeTableRather than requiring complex graph traversal syntax to track identity relationships across multiple systems, VQL’s RELATED TO abstraction handles this complexity for you. Security teams can focus on identifying and remediating actual risks rather than struggling with query syntax.
Understanding VQL Syntax
At its core, a VQL query follows a straightforward structure similar to SQL:
SHOW [NodeType] [{ attributes }] -- Specify what to look for
[WHERE (filter conditions)] -- Add filter criteria
[RELATED TO [NodeType] [{ attributes }]] -- Connect to other entities
[WITH EFFECTIVE|SYSTEM PERMISSIONS = ALL|ANY()] -- Filter by permissions
[HAVING [entity_result_count (condition) |
percentage_of_total_count (condition)]] -- Filter by total relationships
[RESULT INCLUDE [output options]] -- Control result formatVQL supports standard comparison operators (=, <, >, <=, >=, !=), text operators (STARTS_WITH, ENDS_WITH, REGEX), and list operators that security professionals likely already know. This familiar syntax drastically reduces the learning curve for new users.
Here are some practical examples of how VQL can help you address real identity security scenarios:
Identifying dormant access to sensitive systems: A critical security hygiene practice is to identify and remediate standing access from dormant identities. Non-human accounts (e.g., service accounts, machine identities) are often created for a specific purpose and forgotten, leaving them active and vulnerable. An attacker who compromises one of these accounts may gain persistent, unnoticed access to critical assets.
This query pinpoints these high-risk accounts by searching for all NONHUMAN identities that are is_active = true but have a last_login_at date older than 90 days, and are related to sensitive Secret objects.
SHOW Identity { name, id, provider_id, is_active, identity_type, last_login_at, risk_score }
WHERE identity_type = 'NONHUMAN'
AND is_active = true AND last_login_at < current_date - 90
RELATED TO Secret RESULT INCLUDE DESTINATION NODES;Detecting privilege access without admin role: Identify non-admin users with roles that enable impersonating service accounts—a common method that attackers use to elevate privileges after compromising user accounts:
SHOW GoogleWorkspaceUser where full_admin = false
RELATED TO GoogleCloudRole WHERE permissions
LIST_CONTAINS 'iam.serviceAccounts.actAs'Finding access to encryption keys: Cryptographic keys represent highly sensitive resources. This query identifies AWS users with the ability to encrypt or decrypt data using KMS keys:
SHOW AwsIamUser { name, id, is_active, identity_type }
WHERE is_active = true
RELATED TO AwsKmsKey
WITH SYSTEM PERMISSIONS = ANY ('kms:Encrypt', 'kms:Decrypt', 'kms:ReEncrypt*')
RESULT INCLUDE DESTINATION NODES;Flagging toxic combinations: Granting a user the ability to define accounts payable payment terms and modify accounts payable invoices poses a significant segregation of duties (SoD) risk. Such access could enable manipulation of payment terms (e.g., creating overly favorable terms for specific vendors) and alteration of invoices to match those terms, potentially facilitating unauthorized payments to personal or fraudulent accounts.
SHOW OktaUser
RELATED TO `OAA.Coupa.Role` where (name = ('Accounts Payable')
OR name = ('Accounting Supervisor'))
AND RELATED TO OracleEBSFunction where name = ('AP_APXSUMVT')Veza documentation includes detailed syntax and examples you can adapt for a range of use cases.
Access AI with VQL
VQL serves as the execution engine for Veza’s Access AI, our Gen AI product for access security fabric. Access AI translates your questions into security insights, with a robust query language such as VQL to power its capabilities.
We designed VQL with SQL-compatible filter expressions, leveraging the foundation that large language models already understand. This means Access AI can efficiently translate natural language into precise VQL queries—for example, turning “Show me disabled AWS IAM users” into SHOW AwsIamUser WHERE is_active = false.
This approach offers several advantages:
- Immediate productivity: Security teams can ask natural questions and get accurate results without learning query syntax
- Consistent results: Every natural language query gets translated to the same underlying VQL, ensuring reliable, reproducible outcomes
- Progressive learning: As users become more experienced, they can view and modify the generated VQL, gradually building expertise while remaining productive
By combining VQL’s identity-specific capabilities with the ease of natural language, Veza democratizes the understanding of access throughout your organization. Business teams discover risks, security professionals investigate complex scenarios, and automated workflows monitor privilege violations continuously—all powered by the same underlying query language.
For a deeper dive into how Access AI transforms security investigations, check out our blog post on the practical applications of generative AI.
The Road Ahead For VQL
VQL represents a fundamental shift in how security teams will investigate and monitor identity relationships with Veza. By combining the familiarity of SQL with specialized capabilities for traversing complex permission paths, VQL aims to empower both security analysts and automated workflows.
We’re excited about the potential of VQL and are actively developing components and features to realize this vision. If you’re interested in learning more about our roadmap or providing input on priority use cases, please reach out!
Ready to see what VQL can do for identity security?
Whether you’re just learning about Veza or ready to dig deeper, here are a few ways to take the next step:
- Learn how identity security is evolving in 2025. Download the State of Access Report to understand the latest risks and best practices for securing access across cloud, SaaS, and data.
- Explore how Veza helps teams detect privilege drift, toxic combinations, and hidden risks. Check out our Next-Gen IGA Resource Page to see how modern identity governance works in practice.
- Ready to try it for yourself? Request a Demo.
About the Authors
Amber Li is a Principal Product Manager at Veza, where she focuses on building solutions that help organizations govern access across complex enterprise environments. With more than a decade of experience at Deloitte advising enterprises on risk, compliance, and security, Amber brings deep expertise in translating real-world identity challenges into product capabilities that solve them.
Austin Allen is the Founding Technical Writer at Veza. He specializes in translating complex technical concepts into clear, accessible content for identity and security professionals. With a background spanning creative writing, technical editing, and operations, Austin brings both precision and storytelling to Veza’s documentation and thought leadership.
Shanmukh Sista is a Principal Engineer at Veza, leading the Access Intelligence team that powers dashboards, queries, rules, and alerts across the Veza platform. He played a key role in shaping the technical accuracy and query design showcased in this blog. With deep expertise in IAM, AI, and large-scale data architectures from his work at PayPal, Lululemon, and now Veza, Shanmukh bridges engineering vision with customer outcomes.





