
Introduction
At Veza, our mission is to invent the future of identity security. We are dedicated to advancing safety and resilience in a time when breaches and ransomware attacks are increasing in frequency, impact, and cost. We focus on enabling our customers to proactively identify and mitigate identity security risks and vulnerabilities before they allow an actual attack or theft.
Over the last four years, we’ve redefined the identity security landscape with our Access Graph, a visual and actionable representation that answers cybersecurity’s toughest question: “Who can take what action on what data?” Built on the Access Graph, our powerful Access Platform provides leading organizations – like Blackstone, Expedia and Wynn Resorts – with the true and complete picture of enterprise access, so that they can proactively detect and fix identity risks before they allow data breaches or ransomware attacks.
Today, we are excited to unveil our latest innovation for identity security teams: Access AI. At its core, Access AI represents a powerful new set of artificial intelligence capabilities that empower organizations to automate and enhance identity security operations. Access AI addresses longstanding challenges that have long burdened security teams, elevating risk levels and complicating security management. By harnessing machine learning (ML) and Generative AI (GenAI), Access AI democratizes the power of the Access Graph, so that anyone across the business can ask and answer questions in plain English, allowing anyone to fix excessive permissions.
The Power of Access AI
Access AI is a game-changer for teams across identity management, security engineering, application security, and compliance. It simplifies and enhances the analysis and management of access privileges, addressing critical questions such as who holds access, how it was granted, and whether entitlements should be revoked. Here are a few examples of how this applies across the Veza Access Platform:
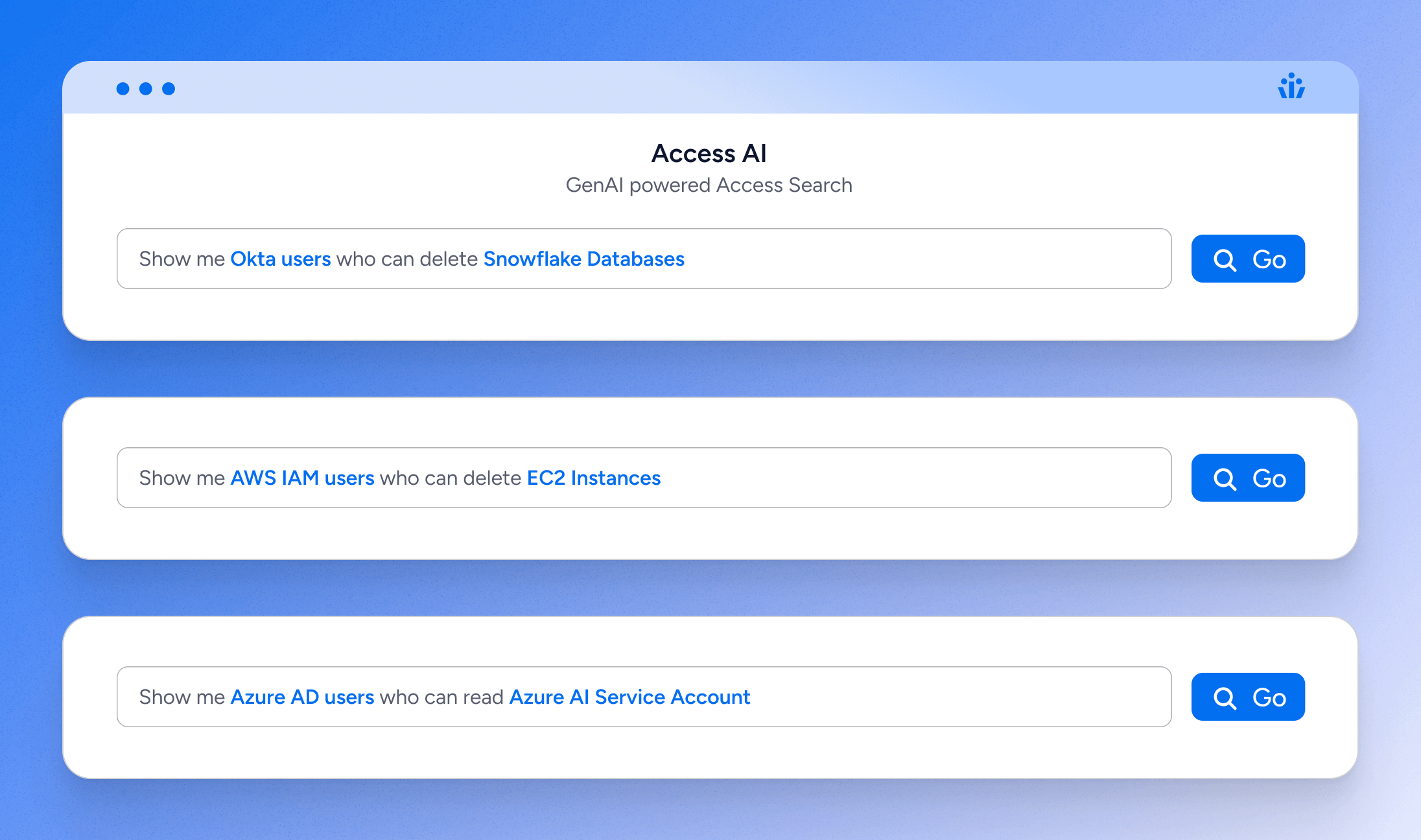
GenAI-powered Access Search
Access AI transforms the way organizations interact with their permissions metadata. Through the Veza Access Graph, users can now gain immediate insights into enterprise access using natural language prompts. This means you can effortlessly discover who has access to specific resources like Snowflake Tables or S3 buckets, or understand the access permissions for particular users, groups, or roles. This intuitive approach eliminates the need for complex queries and manual data sifting.
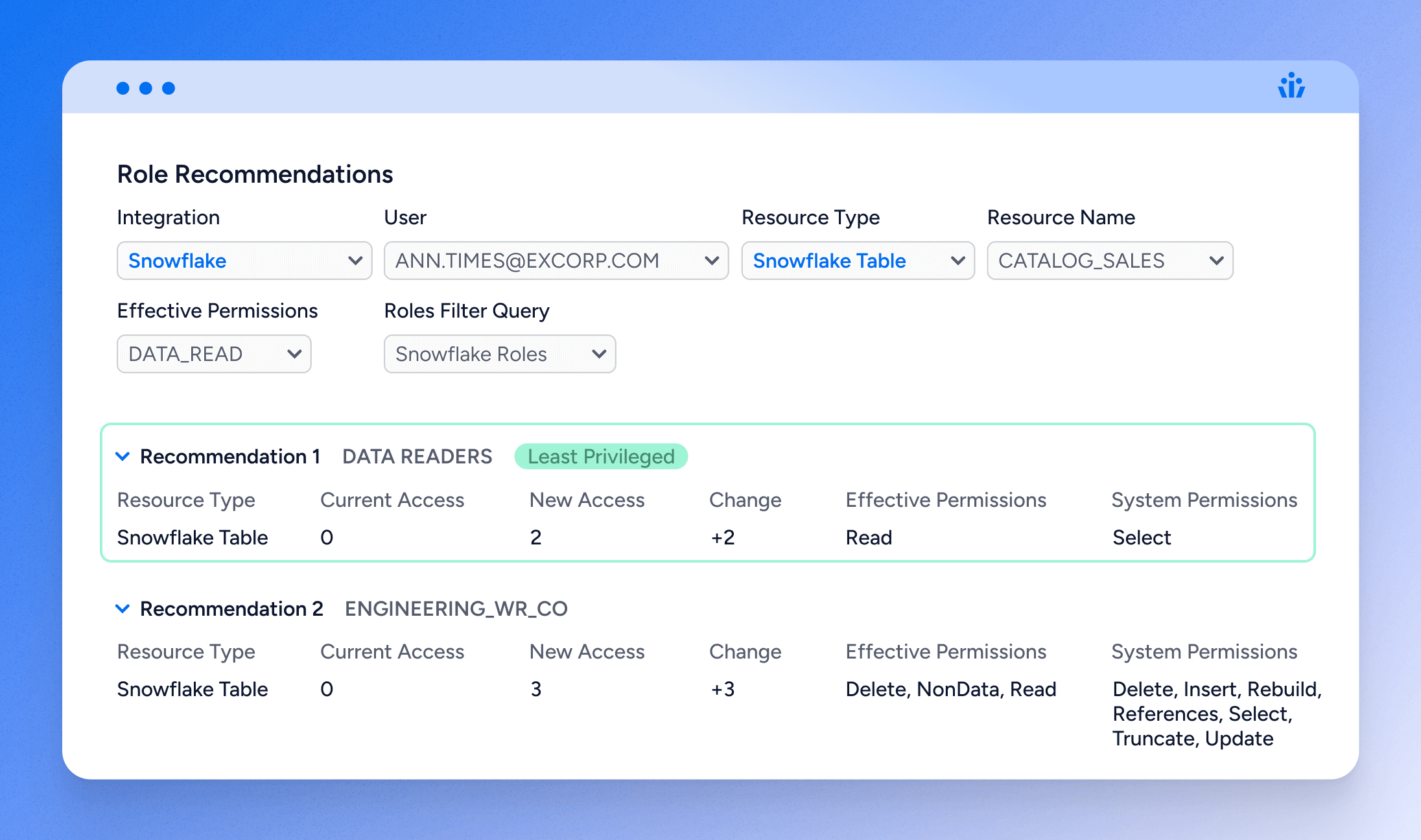
Least privilege role recommendations
Enforcing the principle of least privilege is crucial for maintaining robust security. Access AI streamlines this process by analyzing a user’s current access permissions and activity data to automate the identification and enforcement of least permissive roles. This ensures that users are granted only the permissions necessary for their job functions, thus minimizing potential security risks. Veza’s approach not only enhances security but also accelerates access provisioning without compromising on safety.
Streamline reporting for instant insights
Traditional reporting methods often involve navigating through lengthy and complex spreadsheets. Access AI simplifies this by automatically generating concise and digestible summaries of Access Intelligence findings. This feature is especially valuable for auditors, security teams, and business managers who need quick answers about data access, associated risks, and emerging trends. By delivering clear and actionable summaries, Access AI makes it easier for stakeholders to understand and act on critical security information.
The path forward
The transformative impact of AI and GenAI on identity security will be profound. At Veza, we are setting the standard for leveraging AI to advance identity security. With Access AI, we enable our customers to seamlessly navigate and control who has access to what, with unprecedented speed and accuracy.
We are committed to provide identity and security teams with the tools they need to confidently secure access in their organizations. Access AI represents a significant leap forward, offering powerful capabilities that make managing identity security more efficient and intuitive than ever before.
Ready to get started with Access AI?
Please submit our request form.





