
Introduction: The New Identity Risk Frontier
Identity is eating security
- 60% of Cisco Talos IR cases in 2024 involved identity-based attacks
- 79% of attacks are malware-free, according to Crowdstrike
If your security strategy still focuses on traditional network defenses, you may be missing the bigger picture. The growth of cloud applications, remote workforces, and machine identities has expanded the identity attack surface. It is more complex and dynamic than before.
This is where Identity Security Posture Management (ISPM) plays a key role. ISPM is an emerging approach that enables organizations to understand, monitor, and continuously manage identity risk. It represents the next step in identity security, providing visibility, risk scoring, and automated enforcement across all identities—both human and non-human.
In this blog, we will explain what ISPM is, why it is relevant today, and how Veza supports organizations in managing their identity landscape effectively.
What Is Identity Security Posture Management (ISPM)?
Simply put, ISPM is about continuously understanding and managing the overall health of your identity environment. It takes a real-time, risk-focused approach to identity security that goes beyond traditional IAM or IGA tools.
What sets ISPM apart are its core capabilities:
- Continuous posture scoring provides up-to-date insight into the riskiness of your identity setup at any given moment.
- Over-permission detection: Identifies users or machines with excessive access and helps address those quickly.
- Real-time remediation: Automates policy enforcement to reduce risky access without waiting on manual reviews.
- Comprehensive coverage: Includes both human users and non-human identities such as service accounts and API keys.
Unlike legacy tools that depend on periodic audits and static snapshots, ISPM delivers an always-on view and control, which is essential for keeping pace with today’s dynamic environments.
Why ISPM Matters: Managing an Expanding Identity Attack Surface
The growth of machine identities in enterprise environments has quickly surpassed that of human users. As noted in Technology Magazine, this surge is being driven by cloud services, automation, and APIs, with some environments reporting 82 machine identities for every human one.
This scale introduces real security and governance challenges. Most traditional IAM systems weren’t built to continuously monitor or control non-human identities at this volume or velocity, leaving organizations exposed to silent privilege escalation, forgotten service accounts, and compliance gaps.
Breaches involving compromised credentials remain a significant concern. Research from the 2024 Cost of a Data Breach report by IBM highlights that credential theft is the leading cause of data breaches, accounting for a substantial portion of incidents.
Additionally, a 2024 survey by AppViewX found that organizations have, on average, 20 times more non-human identities than human identities, underscoring the complexity of managing machine identities alongside human users.
These statistics emphasize the need for continuous, real-time oversight in managing identity risks. ISPM offers a proactive approach to identify and remediate risky access, ensuring organizations can effectively navigate the complexities of today’s dynamic environments.
How Veza Powers ISPM: Visibility, Enforcement, and Continuous Risk Scoring
Veza was designed to tackle today’s identity challenges head-on. Here’s how we deliver on ISPM’s promise:
- Unified visibility: Gain clear insight into every user, group, role, and permission across your environment with Access Intelligence and Activity Monitoring. These tools provide real-time visibility into who has access to what and what they’re doing with it.
- Continuous risk scoring: Surface risky entitlements and track posture changes in real time using Next-Gen IGA, which brings continuous context to identity governance.
- Automated enforcement: Apply policy-based remediation with Lifecycle Management, enabling teams to reduce excess access and enforce least privilege without manual intervention.
- Human and non-human identity coverage: Govern access for both people and systems – including service accounts, bots, and API keys – using Non-Human Identity Management.
Our customers consistently tell us Veza helps them cut through identity noise, reduce their attack surface, and get ahead of compliance, without getting stuck in slow, manual processes.
The GigaOm ISPM Radar Report: Analyst Validation That Builds Confidence
The GigaOm ISPM Radar marks one of the first formal efforts to define Identity Security Posture Management as a distinct category. It benchmarks vendors across real-world capabilities, product execution, and strategic innovation, making it a useful reference point for security leaders navigating a noisy market.
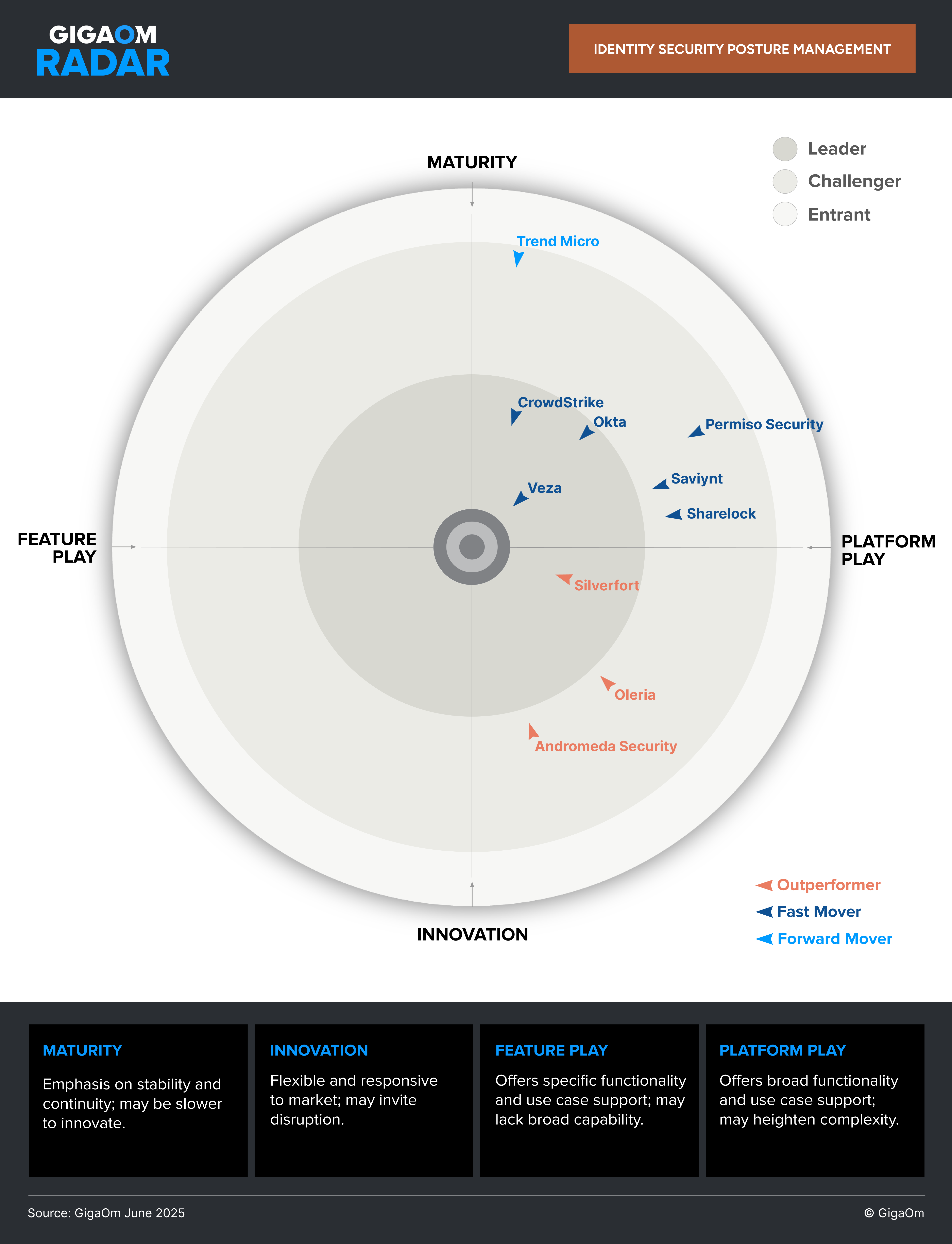
Veza is proud to be recognized as a Leader in this report. This placement validates our approach to managing identity risk through continuous visibility, enforcement, and risk scoring, and confirms that our platform is built to scale with the demands of modern environments.
For buyers, the report offers an independent, comparative lens. For the broader market, it signals that ISPM has moved from emerging ideas to operational reality and sets a clear bar for what good looks like.
Business Impact: How ISPM Drives Security, Compliance, and Operational Efficiency
For business and security leaders, identity risk is no longer just an IT problem; it’s a board-level priority. Over-permissioned users, unmanaged service accounts, and a lack of clear visibility aren’t simply operational headaches. They translate into real risks: audit findings, costly breaches, and regulatory penalties.
Identity Security Posture Management (ISPM) provides organizations with a clear, proactive framework to manage this risk at scale, moving from reactive firefighting to strategic control.
Here’s what ISPM delivers in practice:
- Lower risk, better control: Continuous assessment of identity posture helps identify risky permissions and potential insider threats early, reducing the chances of privilege misuse or lateral attacks—all without adding manual overhead to already stretched teams.
- Audit readiness on demand: Whether preparing for SOX (Sarbanes-Oxley Act), HIPAA Security Rule, ISO 27001 audits, or internal governance checks, ISPM simplifies compliance by providing up-to-date, real-time reports that demonstrate effective access control and policy adherence, eliminating the last-minute scramble and resource drain.
- Faster decisions, fewer delays: With actionable intelligence at their fingertips, security and IT teams can approve or revoke access quickly and confidently, streamlining operations and preventing bottlenecks that slow down business.
- Business-aligned security: Real-time visibility into identity risk across cloud, SaaS, and on-premises environments gives executives and security leaders a unified view that supports informed decision-making and strategic planning, not just tactical firefighting.
ISPM isn’t about adding complexity or more noise. It’s about reducing risk with precision and clarity. Veza helps turn this from a concept into an operational reality that businesses can rely on.
Frequently Asked Questions About ISPM
What is Identity Security Posture Management (ISPM)?
ISPM is a continuous approach to assessing and managing identity risk across all users and systems. It moves beyond traditional IAM by delivering ongoing visibility and enforcement. For a thorough explanation, see NIST’s guidance on Digital Identity Guidelines (SP 800-63-3).
Why is ISPM important now?
The identity perimeter is expanding rapidly due to cloud adoption, remote work, and the proliferation of non-human identities. Traditional tools struggle to keep up. This Microsoft Security Blog on Identity Security highlights why identity is the critical security boundary today.
How does ISPM differ from traditional IAM?
IAM primarily focuses on access provisioning and lifecycle management. ISPM adds continuous risk scoring, real-time monitoring, and automated remediation. For a vendor-neutral explanation of the differences between IAM, IGA, and PAM, see this Core Security guide.
What features should I look for in an ISPM solution?
Look for continuous risk scoring, over-permission detection, support for non-human identities, and automated remediation capabilities. The joint NSA and CISA release on Identity and Access Management Recommended Practices offers practical, authoritative guidance.
How does Veza support ISPM?
Veza provides unified identity visibility by mapping identities and their permissions across your environment. Our platform continuously assesses risk posture, detects over-permissioned access, and helps automate remediation. Veza supports both human and non-human identities, enabling proactive identity risk management at scale.
Learn more about Veza’s approach in these key areas:
- Non-Human Identity Management: https://veza.com/use-cases/non-human-identity-management/
- Agentic AI Security: https://veza.com/use-cases/agentic-ai-security/
- Lifecycle Management: https://veza.com/product/lifecycle-management/
Why trust the GigaOm ISPM report?
GigaOm is a well-regarded, independent analyst firm known for thorough research and vendor evaluations. Their ISPM Radar report provides an objective, data-driven assessment of the market and technology leaders. For buyers, it’s a trusted guide to cut through hype and identify solutions that deliver real-world value.
How quickly can ISPM reduce my identity risk?
While timelines vary based on environment complexity and integration, organizations implementing ISPM with an Identity Visibility and Intelligence Platform (IVIP) often see measurable risk reduction within weeks. The continuous visibility, real-time risk scoring, and automated enforcement capabilities of an IVIP enable security teams to quickly identify and remediate risky access, accelerating improvements in identity security posture from day one.
How Does an Identity Visibility and Intelligence Platform (IVIP) Power ISPM?
At the heart of effective Identity Security Posture Management is the ability to see, understand, and act on identity risk continuously. This is where an Identity Visibility and Intelligence Platform (IVIP) comes into play.
An IVIP serves as the technology backbone for ISPM by providing:
- Unified Visibility: It pulls together identity and permission data from every corner of your environment — cloud, on-premises, SaaS, and hybrid systems — creating a single, comprehensive view of who has access to what.
- Continuous Risk Scoring: Instead of static snapshots or periodic audits, an IVIP analyzes access and permission changes in real time, flagging over-permissioned users, orphaned accounts, and unusual access patterns as they emerge.
- Automated Enforcement: By integrating with policy engines and orchestration tools, IVIPs enable automated workflows that promptly remediate risky access, reducing manual workload and speeding up risk mitigation.
Without an IVIP, organizations are stuck in a reactive cycle — chasing down identity issues after the fact, missing critical blind spots, and struggling to keep pace with the dynamic identity landscape.
In short, an IVIP turns ISPM from theory into practice, empowering security teams to manage identity risk proactively and at scale.
Conclusion and Next Steps
The identity perimeter has evolved, and so should your approach to securing it. Identity Security Posture Management is becoming a foundational practice for managing today’s complex identity environments.
Veza supports organizations with industry-leading visibility, continuous enforcement, and real-time risk scoring to help maintain a strong, adaptable identity security posture.
Elevate Your ISPM Strategy
If ISPM resonates with your security goals, you’re in good company. Many teams are expanding beyond traditional identity controls toward continuous risk management. Here’s how to build on that momentum:
- Start with the essentials
Learn how ISPM closes visibility gaps that legacy identity tools can miss by delivering continuous insights and enforcement.
Read the blog → https://veza.com/blog/identity-security-posture-management/ - See ISPM in action
Explore how organizations leverage ISPM best practices with Veza to streamline risk reduction and compliance.
Customer stories → https://veza.com/use-cases/ - Ready to take the next step?
Download the GigaOm ISPM Radar report for an independent market perspective, or request a demo to see how Veza can support your identity security goals.
Download the report → https://veza.com/resources/gigaom-radar-for-ispm/
Schedule a demo → https://veza.com/schedule-a-demo/
About the Authors
Matthew Romero is a Technical Product Marketing Manager at Veza, where he translates complex identity security concepts into practical strategies for SecOps and IT leaders. With deep experience in Microsoft’s Defender portfolio and a background in building for the practitioner, Matthew brings a grounded, engineer-to-engineer perspective to emerging frameworks like ISPM and IVIP. He’s been in the trenches and knows what it takes to move from theory to operational impact.
Rob Rachwald is Vice President of Product Marketing at Veza and a long-time voice in the cybersecurity space. With over 20 years of experience launching category-defining security platforms—from early-stage startups to industry leaders—Rob has a sharp sense of where the market is headed. His focus at Veza is on helping organizations rethink identity as the core of security strategy, and he’s played a key role in shaping how ISPM is understood by both buyers and analysts alike.






