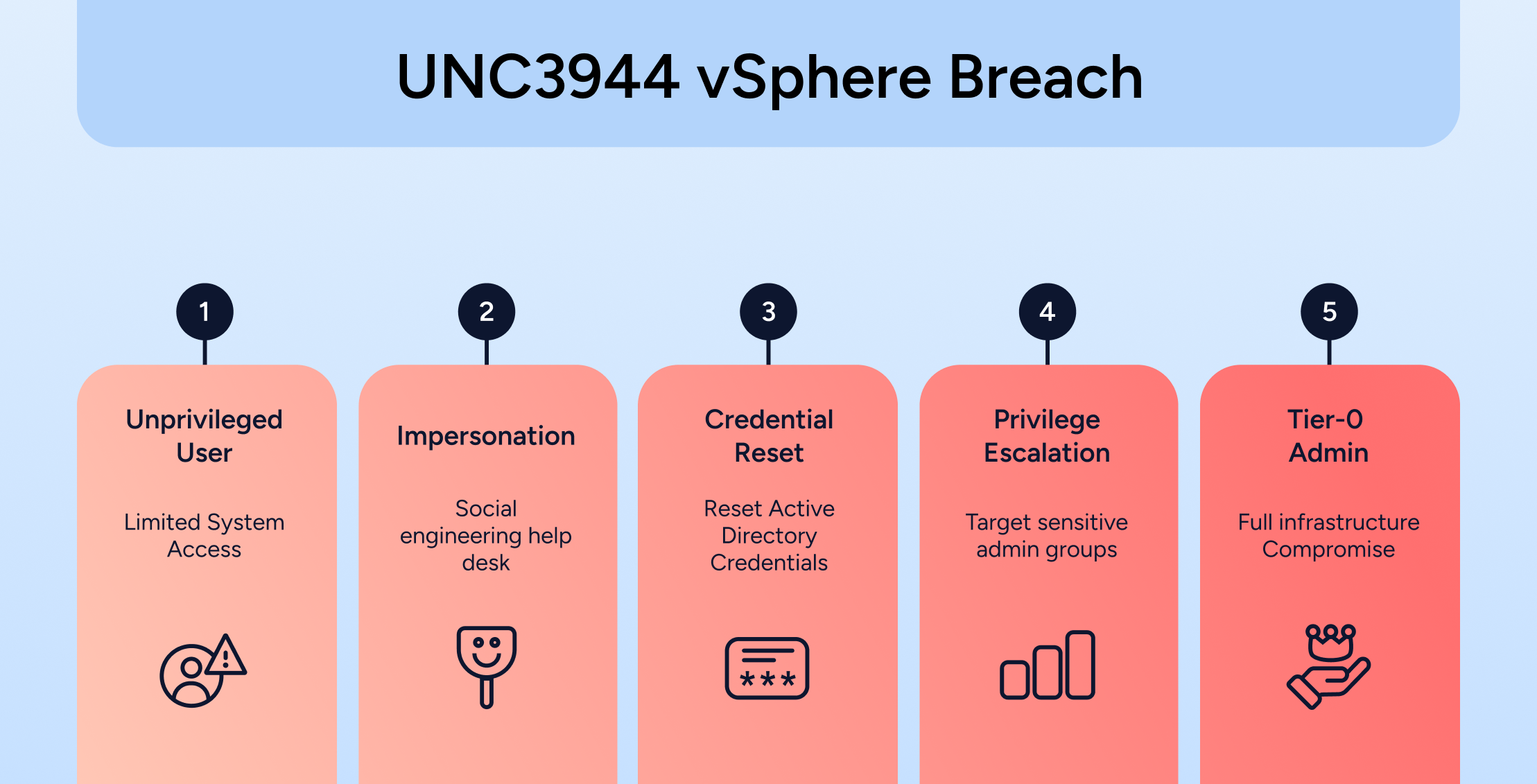
In July 2025, Mandiant’s threat intel team detailed how UNC3944 (aka Scattered Spider) breached VMware vSphere environments by weaponizing identity, not exploits. The attackers didn’t drop malware. They abused identity processes, bypassed endpoint defenses, and took control of infrastructure using nothing more than social engineering and privilege escalation.
It’s a modern blueprint for how identity-first attacks can dismantle virtual infrastructure from the inside out.
From Identity to Infrastructure
Phase 1: Vishing the Help Desk
It starts with a phone call. Unlike phishing, which uses email or messaging to deceive, vishing (voice phishing) leverages phone-based social engineering to manipulate humans directly. In this case, attackers impersonate employees, often targeting IT or administrative personas, to the help desk, requesting password resets for Active Directory (AD) accounts. These aren’t shot-in-the-dark attacks; UNC3944 uses previously obtained personal or org-specific details to make the ruse convincing. The initial goal is simple: establish a beachhead in AD using standard user credentials.
Phase 2: Privilege Escalation in Active Directory
Once inside, attackers waste no time. They leverage internal knowledge repositories, SharePoint, Confluence, and others, to rapidly map out sensitive AD groups like “vSphere Admins” or “ESX Admins.” Modern AI-powered assistants, such as Microsoft’s Copilot embedded in SharePoint, are designed to help humans by delivering information lightning fast. But without strict controls, these bots can inadvertently expose poorly managed, high-impact assets to anyone who asks – legitimate users and attackers alike – accelerating the reconnaissance and privilege discovery phase.
This AI-driven speed, combined with social engineering pressure on help desks to reset privileged credentials, creates a perfect storm. In some cases, attackers escalate access further by directly adding compromised accounts to Tier-0 groups using native Windows tooling:
net.exe group "ESX Admins" DOMAIN\attacker /add
At this point, UNC3944 is no longer just inside your identity perimeter; it’s in the core.
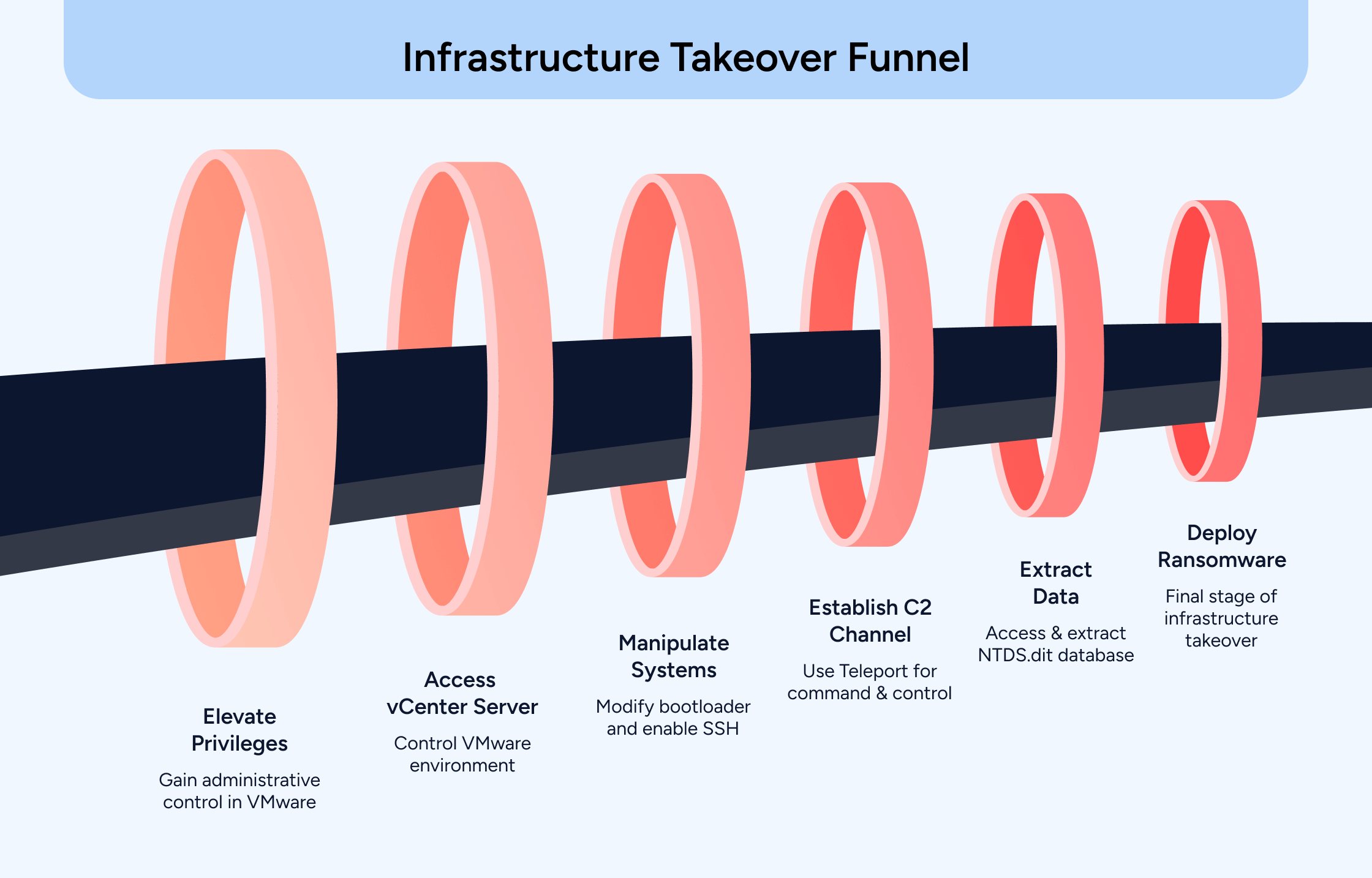
Phase 3: Pivoting to vSphere and vCenter (VCSA)
Armed with elevated AD access, they move laterally to the virtualization plane. Logging into vCenter Server (VCSA), they reboot appliances and tamper with the GRUB bootloader(init=/bin/bash)to drop into a root shell. From there, they reset the root password and enable SSH, quietly opening remote access channels to ESXi hosts. This isn’t just flipping a switch; attackers often modify firewall rules or network segmentation policies to ensure seamless connectivity from their command-and-control infrastructure. They may also leverage legitimate management tools and shares, such as SMB or NFS mounts, to move laterally and maintain persistence, all while flying under the radar of traditional endpoint detection (EDR) systems..
Phase 4: Establishing Remote Access and C2
SSH access is then enabled on ESXi hosts, with root credentials either reset or harvested. Teleport, a legitimate remote access tool, is deployed as a covert command-and-control (C2) channel. In simple terms, a C2 channel is the communication link that lets attackers send commands and receive data from compromised systems remotely. Using Teleport’s encrypted tunnel allows attackers to fly under the radar of most host-based detection systems, providing and maintaining persistent, full control over the virtual infrastructure.
Phase 5: Extracting NTDS.dit via Disk Swap
This is where things get surgical. The attackers locate a domain controller, power it down, detach its virtual disk, and mount it to a compromised system. They extract the NTDS.dit file, and now they have the entire Active Directory database as an offline copy. This method bypasses in-guest monitoring tools entirely, granting access to hashed passwords and the full identity graph.
Even SIEM platforms, often the last line of centralized visibility, struggle to catch this tactic. The extraction occurs beneath the guest OS, outside the scope of most EDR and XDR agents. While a well-instrumented SIEM can surface indirect indicators like domain controller shutdowns, unexpected disk mount events, or anomalous activity from backup or virtualization admins, these signals are easy to miss. Without context, they blend into background noise, dismissed as routine ops, not the prelude to domain takeover.
Phase 6: Backup Sabotage
With control over vCenter and privileged access to Active Directory and backup systems, attackers move to sabotage recovery capabilities by deleting critical snapshots, backup jobs, and storage repositories. These destructive actions are typically executed using compromised backup administrator roles or accounts previously added to sensitive AD groups earlier in the kill chain, granting them the necessary permissions within backup platforms.
This often involves leveraging enterprise backup tools such as Commvault, Veeam, or Veritas NetBackup, which manage on-premises backup operations. Attackers exploit these platforms’ administrative consoles, APIs, or service accounts to disable or delete scheduled backup jobs, remove or corrupt backup repositories and snapshots, and manipulate service accounts to automate or maintain destructive activities.
Additionally, hybrid and cloud-integrated backup solutions like Microsoft Azure Backup Server or AWS Backup are not immune. Because these systems synchronize data between on-premises infrastructure and cloud storage, attackers with sufficient privileges can propagate sabotage across both domains, increasing the blast radius and complicating recovery efforts.
Phase 7: Ransomware at the Hypervisor Layer
The final move is as blunt as it is effective. Using SCP or SFTP over SSH, ransomware binaries are pushed to ESXi hosts. Virtual machines are shut down, datastores are encrypted, and recovery paths are blocked. By the time endpoint agents detect anything, if they even do, the blast radius is already full scale.
Why This Is an Identity Security Issue
- Identity is the Primary Thrust: The attack does not exploit software flaws—it exploits human trust, Android and Admin-level identity workflows, and process gaps.
- Tier‑0 Controls are Critical: Privileged accounts used by vSphere admins become weapons once compromised, making AD guardian integrity essential.
- Lateral Movement Starts with Identity Abuse: The power to manipulate virtualization infrastructure hinges on identity privilege escalation.
Identity Security Defensive Controls
Part I: It’s Time to Face the Risks of Active Directory
Improving identity security starts with acknowledging a hard truth: Organizations still running on-premises Active Directory (AD) are exposed by design. These risks stem from core architectural weaknesses, particularly AD’s reliance on remote process execution, which opens the door to lateral movement and privilege escalation. Regardless of security tooling, these risks can’t be fully mitigated with tooling alone. The core design of on-prem AD leaves it exposed, Without modernization or compensating controls, AD will remain a soft target in the enterprise stack.
Part II: Recognize that Infrastructure Security is Identity Security
The GTIG and Mandiant guidance make one thing clear: infrastructure security starts with identity. Before you can defend workloads, you need to understand who has access, how they obtained it, and what privileges that access enables. From help desk resets to hypervisor-level permissions, every stage of the kill chain is identity-reliant.
Below are the best practice defensive actions you’ll typically find built into enterprise-level identity security platforms. These controls focus on maintaining a clear, measurable identity posture, a critical component of an organization’s overall security posture that ensures access is properly governed and monitored.
| Control Area | Recommended Action |
|---|---|
| Help Desk Identity Verification | Implement positive identity verification—camera checks, callbacks, challenge questions—for any credential resets, especially for privileged roles. |
| MFA Hardening & Access Control | Enforce phishing-resistant MFA (e.g., Authenticator with number matching), disable SMS/voice-based resets. |
| Identity Visibility & Monitoring | Detect and alert on AD group modifications, password resets, and unusual access to privileged accounts. |
| Isolation of Admin Identities | Apply least privilege segmentation—use dedicated jump hosts with MFA for access to vSphere relevant admin identities. |
| Privileged Infrastructure Hygiene | Encrypt Tier‑0 VMs, disable unnecessary services, restrict reset access on ESXi hosts, ensure backups are immutable and separate from AD-managed systems. |
The UNC3944 blog underscores a critical reality: Identity is the kill chain’s entry point. Protecting privileged identities, hardening help desk workflows, and securing integration paths between identity systems and infrastructure (like vSphere) are foundational to stopping hypervisor-level ransomware attacks. These aren’t just tactical actions – they’re minimum requirements for maintaining control over Tier-0.
Where do ISPM and IPIV Fit into the Killing the Kill Chain
UNC3944’s intrusion path exploited blind spots in identity posture, starting with human-centric processes (help desk resets) and culminating in infrastructure abuse (vCenter, ESXi).
Based on combined guidance from GTIG, Mandiant, and NIST SP 800‑125A Rev 1 (Security Recommendations for Server-based Hypervisor Platforms), this is precisely where ISPM and IVIP platforms play a strategic role, turning identity best practices into measurable, enforceable controls across your environment.
ISPM and IPIV platforms embrace a shift-left model, aligning closely with CISA’s Secure by Design principles, to ensure identity security is embedded early and enforced continuously. In short, these platforms are built to proactively detect and correct the exact types of weaknesses that this attack chain leverages.
How ISPM helps:
- Exposes risky identity configurations, e.g., accounts with outdated or no MFA, service accounts with lateral movement potential, or AD groups with privileged access to vSphere.
- Surfaces gaps in policy enforcement, such as shared accounts, stale admin credentials, or excessive rights to backup systems.
- Monitors posture drift across identity systems and infrastructure.
How IPIV helps:
- Maps identities to infrastructure permissions—clarifying which users or NHIs can access vCenter, ESXi, backup systems, and more.
- Detects anomalous access behaviour, like sudden SSH enablement on hypervisors or unsanctioned changes to Tier-0 assets.
- Visualizes the blast radius of a compromised identity, helping teams respond faster and scope containment.
Identity Is the New Perimeter – Visibility and Posture Are Your Defense
The UNC3944 attack sequence underscores a fundamental shift in enterprise security: identity has become the new perimeter. Traditional defenses focused solely on malware and endpoint detection no longer suffice. Instead, continuous identity posture management and comprehensive visibility into identity-to-infrastructure relationships are essential.
Platforms that provide real-time monitoring, clear visualization of access pathways, and policy enforcement across both identity systems and critical infrastructure enable security teams to detect and disrupt attack chains early, well before social engineering calls escalate into catastrophic data center breaches.
Identity visibility and posture shouldn’t be treated as secondary controls. They’re foundational to preventing breaches and enforcing least privilege. Following best practices means making identity security a core part of your strategy, not just an afterthought.
Next Steps:
Want to see the full picture? Explore our Access Graph to visualize your identity risk in real time, and check out Activity Monitoring for deep insights into access behavior across your environment.
If visibility gaps are your team’s daily battle, this piece on Identity Visibility and Intelligence Platforms (IVIP) explores how modern teams are mapping entitlements across SaaS, cloud, and on-prem systems to get ahead of privilege escalation.
And if your org is ready to move from manual audit cycles to continuous posture monitoring, this resource on Identity Security Posture Management (ISPM) lays out the next step: live access scores, real-time remediation, and proactive enforcement that closes the identity gap, before attackers open it.
Schedule a demo to see how your team can get visibility into access before it’s exploited.
About the Authors
Rob Rachwald is VP of Marketing at Veza with over 20 years of experience driving product marketing and demand generation in cybersecurity. Rob laid the foundation of this blog by outlining the core concept and framing the attack’s significance in today’s identity security landscape.
Matthew Romero is a Technical Product Marketing Manager at Veza who transformed Rob’s initial draft into a detailed, authoritative blog. Matthew brings deep SecOps expertise and a knack for translating complex security topics into clear, actionable insights.
Taylor Parsons is a seasoned security professional with over 15 years in cybersecurity and IT. Currently focused on security and risk at Veza, Taylor provided critical fact-checking and refined the narrative to sharpen focus on the attack’s technical impact and real-world relevance.





