We’ve come to expect the cost of a data breach to tick up a little each year, sort of like the NFL salary cap, but things changed dramatically this past year according to IBM’s 2024 Cost of Data Breach Report. Findings from the survey of organizations that suffered attacks show a pronounced spike in the cost of data breaches but also profound implications for using artificial intelligence (AI) to curtail losses.
The bottom line

What’s driving breach costs higher?
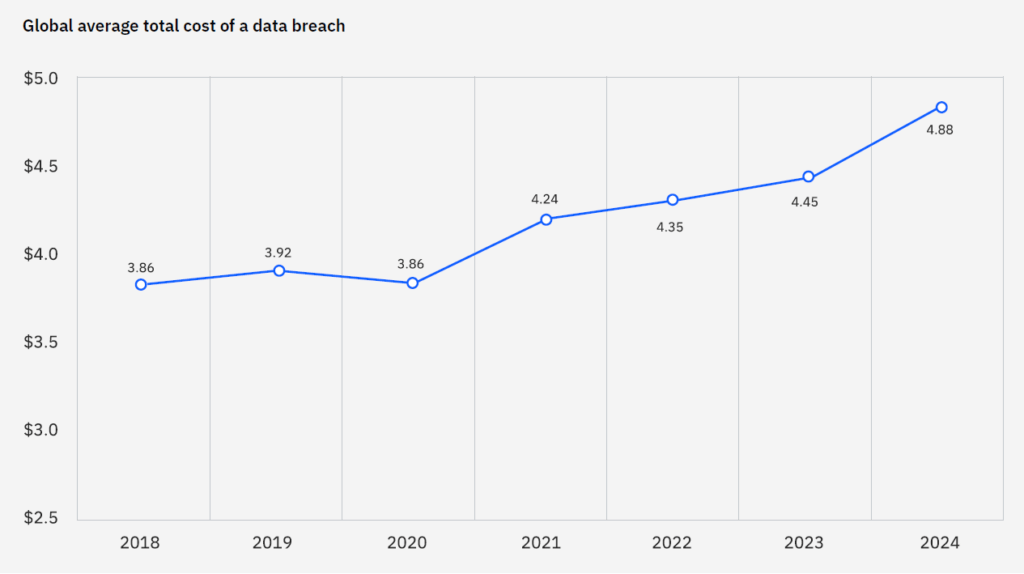
Based on research from the Ponemon Institute, the 19th report in IBM’s landmark series found the average cost of incurring a breach rose nearly 10% to $4.88 million, the largest increase since the height of the pandemic. The report cites business disruption — operational downtime and the impact of lost business — as the greatest contributing factor to the rising cost of data breaches.
All told, the combined cost of post-breach activities totaled $2.8 million, the highest during the past six years. And while the report does not specifically call it out, public admission of a breach clearly has the potential to drive cyber insurance premiums higher.
AI makes attacks smarter, faster, and more expensive
The sharp rise in cost stems in part from AI equipping threat actors to build and launch harder-to-detect attacks faster on a global scale. The report cites several dynamics contributing to the rising cost of breaches:
New risk lurking in ‘shadow AI’
IT continues to struggle to detect threats within unmanaged data as more workers dabble in using generative AI tools like Open AI’s ChatGPT. Unsanctioned use of LLMs by employees that’s outside IT’s control can include drafting emails, creating images, and at times even writing code. These practices may create shadow data, company information stored digitally outside of managed systems. This year’s report found that breaches targeting shadow data lasted longer and led to higher breach and recovery costs.
AI-led attacks cause skills gap to widen
AI’s capacity to refine, accelerate and automate social engineering and phishing attacks creates more noise — and more work — for detection tools and security operations center (SOC) teams looking to isolate real threats. With gen AI tools gaining popularity among threat actors, the percentage of breached organizations citing skills gaps as a primary contributor to incurring a data breach rose 26.2% this year compared to the 2023 report.
On the positive side, while only 1 in 5 organizations currently use AI in their cybersecurity practices, IBM findings prove it pays to fight fire with fire.
AI-powered security turns the tables on attacks
The most significant findings of the 2024 Cost of a Data Breach Report show the potential for using AI to prevent, investigate, and shut down cyber threats faster, to avoid breaches and lost business altogether. Just as AI helps bad actors launch modern attacks at unprecedented speed and scale, the same technology powers tools to identify, contain, and automate a response to new threats. As a result, overworked security teams can do more with less.
The report reinforces a need to continue investing in user education, but the “news” revolves around the value of building AI into defenses to minimize cost:
Extensive use of AI lowers the cost of breaches
The number of organizations using AI and automation ‘extensively’ in the SOC reached 31% in the 2024 study, which translates into a 10.7% increase in actual usage of AI. The number of organizations that use AI and automation on a limited (versus extensive) basis also increased by 9.1% — an extremely positive and powerful trend in reducing overall costs.
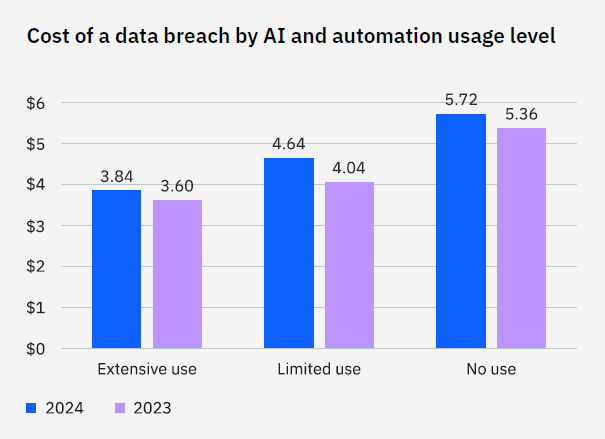
Organizations that use AI and automation extensively for security experienced average breach costs of $3.84 million while those that do not use AI saw costs surge to $5.72 million — an added expense of $1.88 million per breach.
Use of AI for prevention saves $2M+ per breach
Among those reporting extensive use, roughly one-quarter (27%) employed AI across all four high-impact security categories defined in the report: prevention, detection, investigation, and response. When broken down further, findings show that extensive use of AI in prevention workflows generated the largest cost-savings measured in the 2024 report.
Organizations that applied AI and automation to prevention reduced the cost of breaches by an average of $2.22 million — $5.98 million versus $3.76 million — compared with those that had not yet deployed AI in prevention technologies, a staggering 45.6% difference.
The more organizations used AI and automation, the lower their average breach costs. That correlation is striking and one of the key findings of this year’s report. Organizations not using AI and automation had average costs of USD 5.72 million, while those making extensive use of AI and automation had average costs of USD 3.84 million, a savings of USD 1.88 million.
IBM Cost of a Data Breach Report 2024
AI bridges skills gap for faster containment
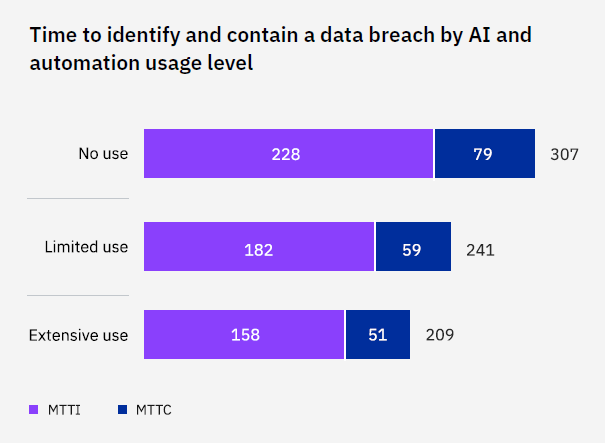
Automating the job of sifting through endless streams of security alerts to weed out false positives frees up skilled cybersecurity analysts to identify, investigate and shut down the real threats faster. On average, organizations that claimed extensive use of AI and automation identified and contained breaches nearly 100 days faster than other organizations — a powerful advantage in lowering costs.
Extensive use of AI also reduced average mean-time-to-identify (MTTI) and contain (MTTC) breaches by 33% for response and 43% for prevention.
Control access to control risk
Defenders without AI and automation to assist
IBM Cost of a Data Breach Report 2024
them can expect to take longer to detect and contain a breach,
and see costs rise compared to those who use these solutions.
For the past decade, cybersecurity leaders have accepted that they are unlikely to succeed at completely preventing unauthorized access to the network. Modern strategies focus on finding potential threats quickly and putting controls in place to block lateral movement and prevent misuse of compromised credentials and accounts. In other words, we “assume the breach” without accepting that the resulting damage and costs cannot be prevented.
One powerful strategy for limiting losses due to compromised identities is to limit the data, resources, and other assets those identities can access.
Visibility streamlines access management
Most organizations distribute data across multiple environments, including on-premise repositories and private and public clouds. Incomplete or out-of-date inventories can delay efforts to discover what data has been breached and how sensitive or confidential it might be. These delays can complicate the response and raise the cost of a breach. To mitigate risk, enterprises can employ AI-led data discovery and classification to detect sensitive data used in training or fine-tuning AI models.
Organizations must extend posture management to the AI models themselves to protect sensitive AI training data, gain visibility into the use of unsanctioned or shadow AI models, and AI misuse or data leakage. Developing response playbooks to deny access, and quarantine and disconnect compromised models is essential as well.
IBM Cost of a Data Breach Report 2024
Modern access outpaces manual efforts
As access scales to encompass more remote workers transacting online and via the cloud, even well-staffed IAM teams lack the cycles to keep up. Instead of continuing to manage permissions manually, experts must leverage automation to sort through data, find unusual access profiles, and manage permissions.
Least privilege lowers risk, cost, and workload
The IBM report found more than 60% of organizations that suffered a recent breach planned to increase their investments in cybersecurity. Along with standard tools for prevention and detection, progressive solutions like Access Entitlements Management, Identity Security Posture Management (ISPM), and Identity Threat Detection and Response (ITDR) stand to reduce the likelihood and cost of breaches dramatically.
For this reason, Veza’s approach to enabling least privilege uses AI to strengthen identity management, avoid business disruption, and lower recovery costs.
Veza applies AI to prevent breaches
With the recent addition of Access AITM, a generative AI-powered solution, to the Veza Access Platform, defenders can leverage a chat-like interface to:
- Understand who can take what actions on what data
- Review, prioritize and remove risky access or excessive permissions for both human and machine identities
- Recommend least privilege roles to support best practices in provisioning access
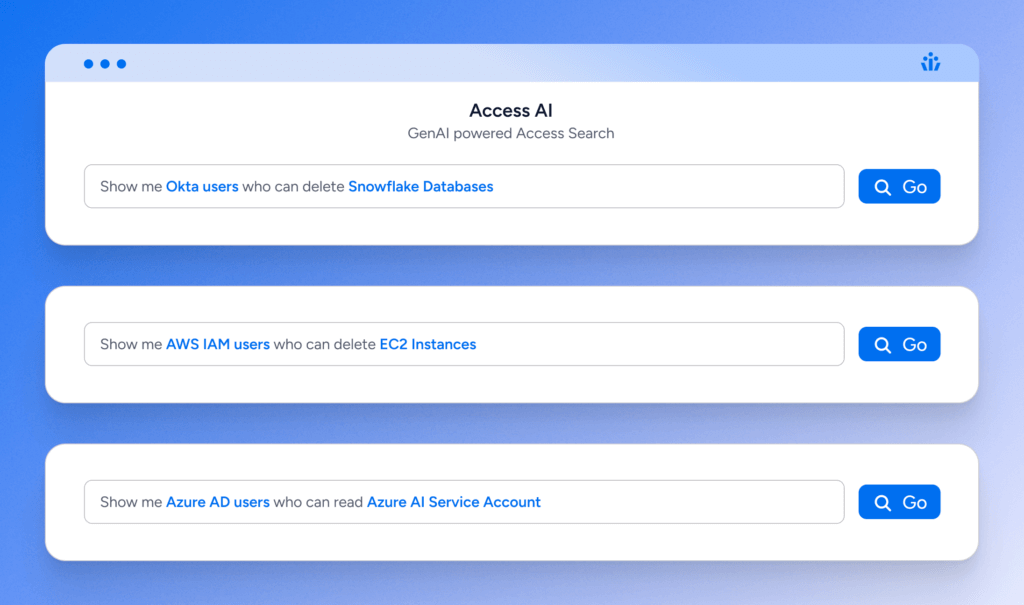
Access AI applies machine learning and generative AI to surface and contextualize recommendations for handling identity-based threats. AI equips IAM teams, security engineering, application security, and compliance teams to understand which individuals have access to particular assets, how they got it, and whether permissions should be amended or revoked.
The Veza platform:
- Understands human identities and non-human identities (NHIs)
- Surfaces dormant or excessive permissions
- Recommends actions to take during user access reviews and recertifications
- Automatically provisions and deprovisions access throughout a user’s lifecycle
Only Access AI:
- Streamlines management of permissions across SaaS, cloud, and identity systems as well as infrastructure services
- Recommends roles based on least-privilege
- Monitors activity for ITDR, Security Engineering, and Security Operations
- Provides Access intelligence for Cloud PAM, privilege threat hunting, privileged access assurance
Democratizing insights to bridge the skills gap
Granular real-time access intelligence helps security teams hunt for threats automatically across tens of thousands of identities and entitlements within hundreds of systems — a feat only achievable with the speed and intelligence enabled by AI. Visualizing authorization data provides powerful insights for understanding the implications of permissions and what steps to take.
Access AI adds natural language capabilities needed to search and return results that can be immediately understood and actioned by more people across more IT and business functions.
Learn more
To unlock the potential cost savings of AI, IAM leaders must maintain visibility and control over everyone – and everything — they grant access to. Take a closer look at how Access AI advances your least privilege, or schedule a demo today.
About the IBM report
The 2024 Cost of a Data Breach Report featured data collected from 604 organizations worldwide impacted by data breaches between March 2023 and February 2024.





