
The thought of nameless, faceless strangers getting their hands on our personal data, locking us out of our own files, threatening to do unthinkable damage unless we pay them a ransom horrifies the average person. Amplify that by 10,000 and you’ll know the dread cybersecurity teams face 24/7.
Read on to learn what ransomware is and how you can avoid falling prey to it . . .
Modern, sophisticated ransomware attacks are:
- Rising in number
- Evolving in complexity
- Costing organizations more budget, cycles, and brand reputation damage than ever before
According to the Verizon DBIR, ransomware attacks grew about 13% last year alone — nearly as much as they had during the previous five years combined – with phishing and compromised credentials as the leading threat vectors:
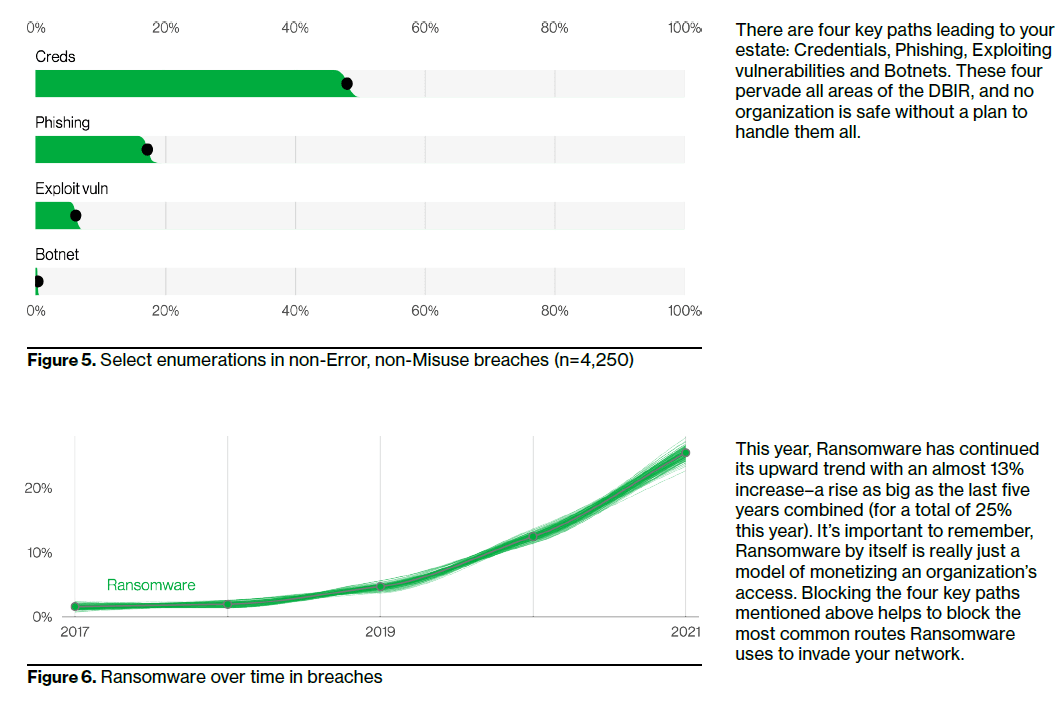
But let’s back up . . .
What is a ransomware attack?
For all the front-page headlines, a surprising number of users and executives still don’t understand ransomware and what it takes to avoid attacks. To start with the basics, malware, or malicious software, aims to access and compromise endpoints and servers for nefarious purposes. Ransomware is specialized malware that locks up a user’s files and related systems while threat actors demand payment, often in the form of cryptocurrency, before (hopefully) giving them back again.
Since first appearing in the 1980s, ransomware’s reach continues to grow as attacks become more prevalent and profitable for attackers, and more trouble for defenders:
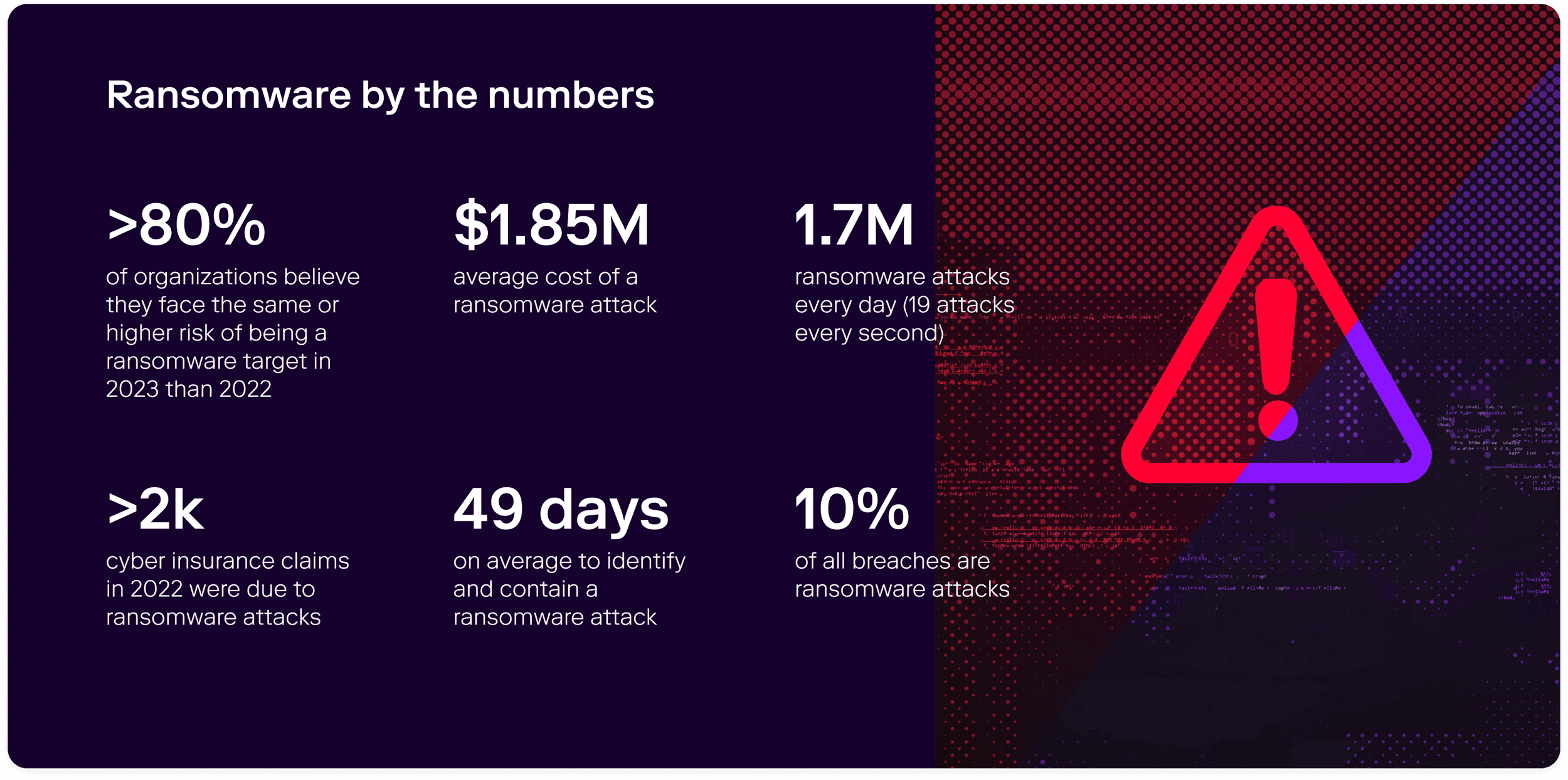
The three most prevalent or popular types of ransomware are:
- Encryptors that encrypt data on a system to render content inaccessible
- Screen lockers that block access to the whole system, usually confronting users with a “lock screen” ransom note with detailed instructions for paying the ransom in exchange for a decryption key
- Scareware: A variation in which popups try to convince victims they have a virus and telling them to download, and pay for, a bogus solution to resolve the issue
And like virtually every thriving industry, ransomware has been SaaS-ified by malware authors. Ransomware-as-a-Service or RaaS campaigns in which “customers” — other would-be cybercriminals — simply log into a portal or dashboard to define and launch attacks make it easy to get in on the action without specialized expertise.
How do ransomware attacks work?
Most attacks unfold in these three steps:
- Infection: An unsuspecting user opens an attachment or clicks on a URL that turns out to be malicious. A malicious macro runs, downloading a ransomware agent to the user device, then delivers its payload.
- Encryption: The agent starts encrypting files on a user device and perhaps attached file shares so no one can access them.
- Attack: The ransomware displays a message on the infected device informing users of their plight. The “lock” screen includes instructions on how to pay the ransom and obtain a decryption key.
Popular threat vectors for infection
The initial phase of a ransomware can take various forms:
- The “oldest trick in the book”: Phishing emails with corrupt attachments or links to sites used to deposit malware, or steal credentials. For cost, and convenience, phishers often target both low- and high-privileged users en masse.
- Spear phishing: Similar to the above but targeting select employees. For example, claiming HR needs a user to download and read a new policy. “Whaling” refers to spear phishing attacks aimed at high- or C-level executives.
- Social engineering: These campaigns trick people into opening attachments or clicking links by appearing to come from trusted entities or powerful authorities. Attacks may involve scouring public social media profiles to learn about targets’ routines and interests.
- Drive-by-downloads: Here, trouble starts when users unintentionally download a file or files, not always malicious, without realizing or agreeing to do so. Sometimes “malvertising” is used to attract and divert users to criminal servers or corrupt landing pages with malicious code that attacks the system even if they haven’t clicked on an ad.
Increasingly, malware also plays a role in multi-vector attacks in which multiple tactics, techniques, and procedures (TTPs) work together to perpetrate sophisticated, highly orchestrated campaigns.
Who is targeted with ransomware?
The short answer is: everybody. Consumers, corporate and government leaders and employees, and entire organizations all represent phishable targets.
That said, attackers tend to follow the money, and opt for the path of least resistance. Large organizations with deep pockets that can afford to pay steep ransoms, and SMBs that lack the budget to build state-of-the-art defense make equally attractive targets for opposite reasons.
Following that logic, and the money, most research shows finance, government, healthcare, education, and retail ranking among the top targets industry-wise.
Remote work raises the stakes
The software you use to collaborate with remote employees may have vulnerabilities that ransomware attackers seek to take advantage of. Remote employees tend to be less protected by ransomware essentials such as immutable data backups.
eSecurity Planet
In 2020, remote workers connecting to corporate systems via virtual private networks (VPNs) became major targets for ransomware and third-party attacks. VPNs safeguard data by encrypting traffic across the Internet but may also contain unpatched vulnerabilities or outdated versions that threat actors can leverage to gain access.
How much do ransomware attacks cost?
Research shows the average ransom itself keeps going up:
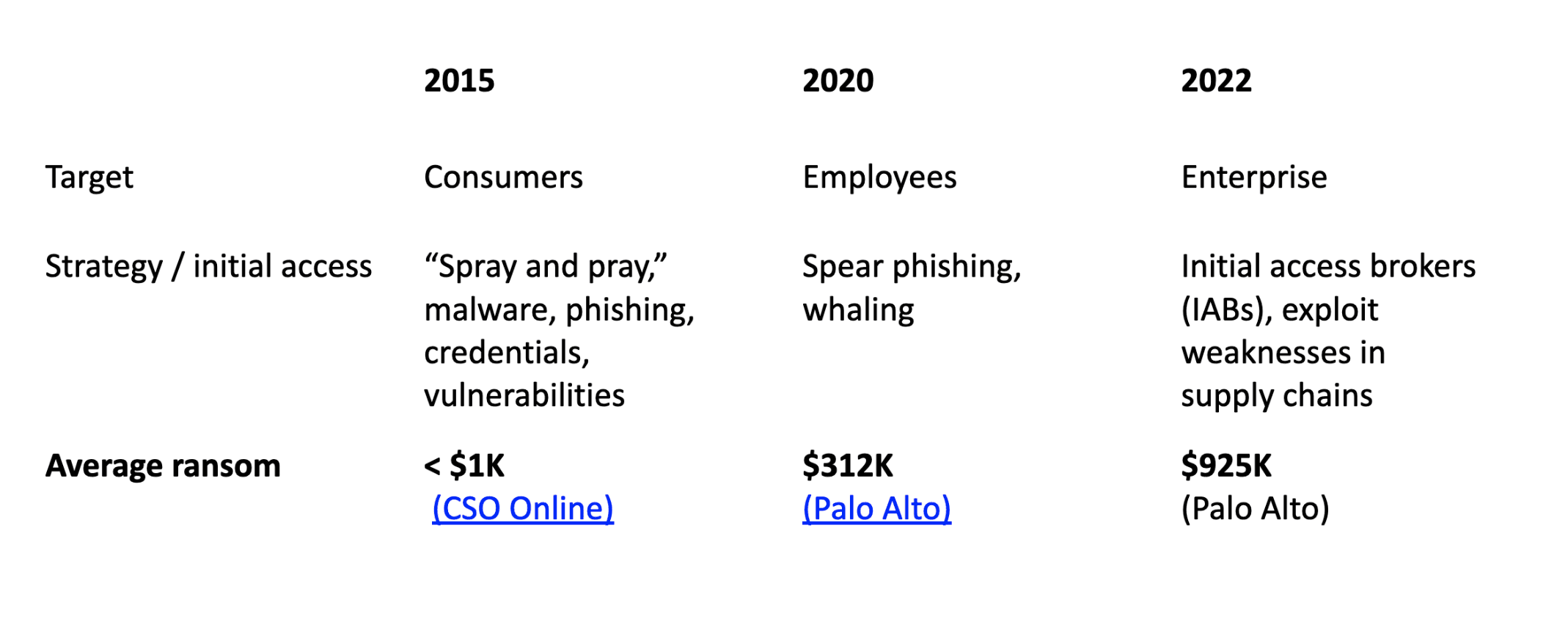
Aside from the ransom itself, ransomware attacks run up devastating costs through:
- Lost productivity from downtime: mitigation could take hours, days, even weeks, and might mean segmenting or taking systems offline. Either way, companies end up paying users to stand or sit around waiting to get back online.
- Costs to remediate: This includes the initial full-court press it takes for IT to remediate and recover from an attack, and the inevitable forensics and increased investment to create stronger defenses that follow.
- Reputation: Last but never least, your organization’s reputations may suffer a serious hit, followed by a costly dip in brand loyalty and sharp rise in cyber insurance premiums and potential fines for breaching compliance. This is especially true for organizations that are entrusted with sensitive customer data, where a significant breach could lead to a fatal loss of confidence.
“Don’t pay the ransom”
The FBI and virtually all cybersecurity thought leaders advise against paying the ransom to keep from encouraging attacks. And, sad to say, there’s no guarantee cybercriminals will give back your files even if you do pay. Some companies obviously agree to pay, often out of fear of having breaches become public.
The typical ransomware response
Dealing with ransomware can be summed up in two short words: not fun. Once that lock screen message pops up—and the clock starts running—responders’ first goal is to contain the threat by:
- Identifying and isolating infected systems. Ransomware spreads fast so this may mean powering down or taking devices and systems offline.
- Removing the malware from the network by removing infected devices from the network and shutting down external access.
- Recovery efforts focused on restoring data from backups if available.
It’s not like we’re not trying. Ransomware continues to grow in severity despite global cybersecurity spending expected to reach $1.75 trillion from 2021–2025.
Yet, because the response is so predictable and hasn’t done much to stop attacks from evolving, most studies reach the same conclusion: it’s better — and cheaper — to prevent ransomware from happening in the first place than to control the damage after the fact. We agree: to reverse the tide, our focus needs to shift to prevention.
5 ways to avoid ransomware attacks
Most experts discussions agree ransomware prevention starts with these ongoing best practices:
- Educating all users to the dangers and how to recognize sophisticated phishing and other tactics used to distribute and activate malware
- Backing up important data where it won’t be impacted if threat actors gain the network
- Maintaining the strongest possible cybersecurity posture, from user devices to servers to hybrid networks and clouds. Critical places to bolster defenses across the attack kill chain include:
- Antivirus / anti-malware solutions that screen and quarantine suspect software.
- Email protection gateways, sometimes considered the first line of defense against phishing, business email compromise (BEC), and related attacks.
- Endpoint detection and response (EDR) products and service.
- Multi-factor authentication (MFA) used to verify identity, establish trust, and keep the wrong people from accessing assets.
- Identity security software that detects abnormal user behavior
- Secure web gateways (SWGs) that can identify malicious web ads used to misdirect users to sites that distribute ransomware
- Network monitoring and network detection and response (NDR) that flag unusual file access, C&C traffic, and lateral movement following initial access
- Practicing vigilant vulnerability management with reliable threat intelligence and automation to prioritize patching effort based on risk to your individual organization
- Leveraging authorization to apply least privilege access: While organizations invest heavily in all of the above, cyber defenses are only as strong as their weakest link. Most companies overlook a critical element of their ransomware risk: the permissions they grant users.
The role of identity and authorization in stopping ransomware attacks
Since pouring budget and analyst cycles into stopping ransomware from entering your environment may be a losing battle, consider this simple point: in order for attacks to succeed, a threat actor needs a compromised user account to move through the network.
In 2022, the Verizon DBIR cited privilege abuse as the #1 form of misuse leading to breaches. Verizon defines privilege misuse as:
. . . the pattern where people use the legitimate access granted to them as employees to steal data. Often, they act alone, but they sometimes act in concert with others. Either way, you have a data breach and must deal with the fallout.”
Without this access, the attempted extortion falls flat. So, why don’t defenders use authorization to their advantage?
One reason: they have no easy way to manage it. Most businesses lack visibility into the effective permissions of identities, and find it virtually impossible to enforce the principle of least privilege — a critical element of ransomware protection.
What is least privilege access?
A least privilege security posture means ensuring each identity has only the minimum privileges on data — create, read, update, or delete — required to do its job. Maintaining this advanced level of control requires complete, automated visibility and actionable insight, but that doesn’t mean it needs to be hard.
How to prevent ransomware attacks with Veza
With the right strategy for managing authorization, companies gain complete visibility into their identity-to-data relationships so they can prevent the misuse of privileges. Best-practice authorization management entails understanding which identities can take what actions across your entire data stack, on-prem and in the cloud.
The Veza platform closes the authorization gap so organizations can answer the vital question, “who can and should take what action, on what data?” Veza extracts system-specific authorization metadata from identity providers, cloud IAM, apps, and data systems, and creates a single control plane for authorization.
Identity management professionals can see the full chain of authorization for every identity, human or machine. Accurate mapping of identity to authorization makes it easy for admins to prioritize and implement protections to enable least privilege access to data to reduce risk.
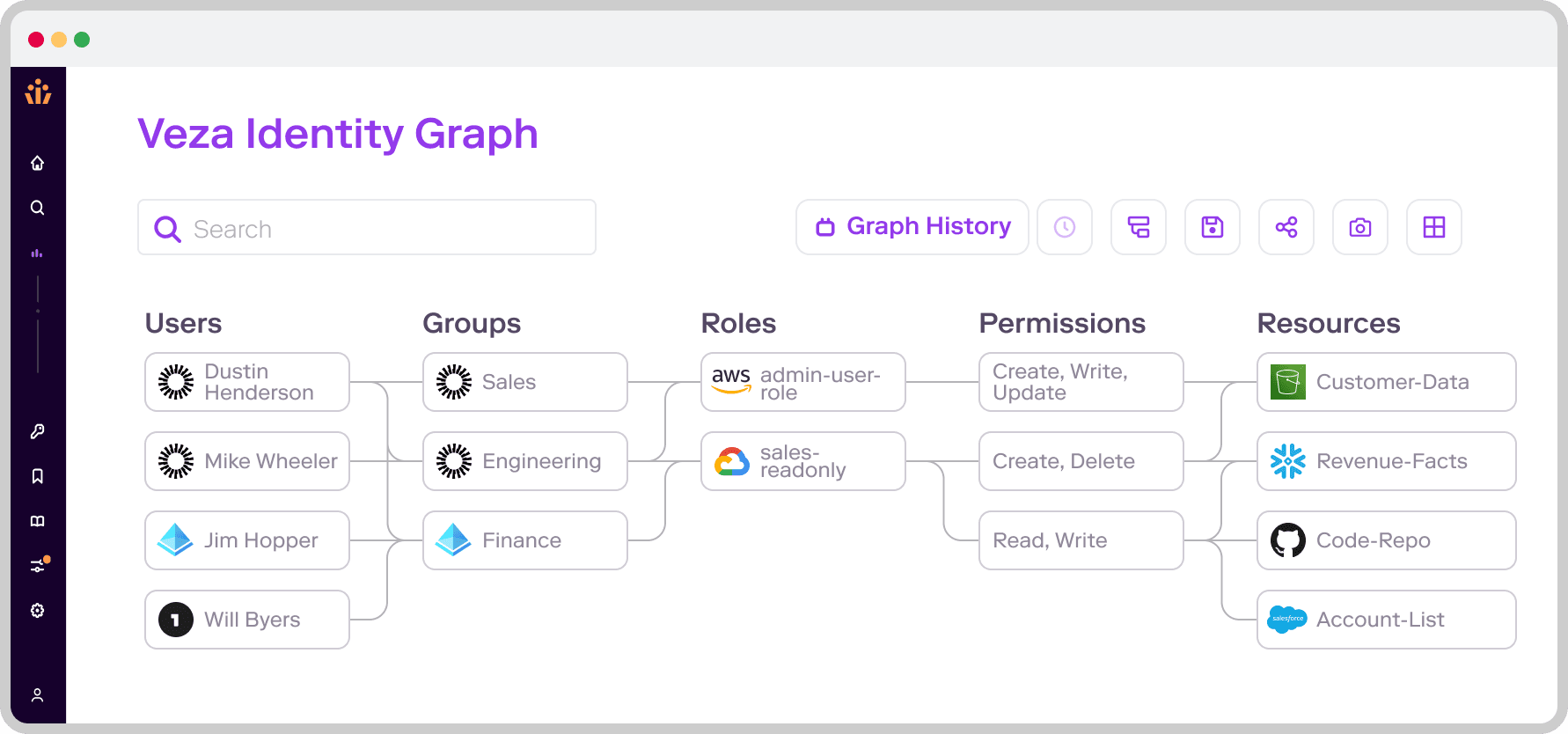
The platform also provides recommendations on how to remediate access violations, including specific steps for specific systems. As an example, companies can flag users with high-risk permissions such as programmatic access to services, or AWS roles with AssumeRole lateral movement. Veza users can also identify undersecured data stores such as S3 buckets that are unencrypted or allow public access.
A new front line of defense against ransomware
Ransomware attacks enjoy steady success because organizations aren’t focusing their security strategy on the real target of ransomware attacks – data. For these attacks to succeed, attackers must both access and encrypt data, which means compromised users and devices need the permissions to do so.
What organizations miss
If the compromised account doesn’t have the necessary privileges to access and encrypt sensitive information, or to leverage lateral movement/privilege escalation, the attack fails. If you’re adhering to the principles of Zero Trust, the permission to encrypt data should only be granted to a small subset of privileged accounts.
If organizations can’t easily tell which individual identities have access to what data, they’re unable to manage and apply least privilege effectively. To impose control, best-practice authentication management equips a business to:
- Gain visibility into identity-to-data relationships
- Apply least privilege across all human and machine identities
- Identify and eliminate cloud IAM and data store misconfigurations that lead to access via roles/permissions/policies
Veza plays a critical role in protecting against ransomware by detecting excess privileges your employees and services have on data systems and identifying those with privilege permissions to databases. By continually monitoring the state of authorization and automating remediation of least privilege violations, organizations can fully leverage their data without undermining security or compliance
To learn more, read the solution brief, Authorization – The Missing Piece of Ransomware Protection, or contact us to arrange a demo.






