Introduction
Veza Access Reviews enable critical business processes for examining and validating access rights on your organization’s applications, systems, and resources. The types of users who interact with Access Reviews vary by organizational structure and business processes.
Moreover, some organizations are structured as a collection of independent operating entities – this means that access control must address two things at once: (1) what each type of user (i.e. persona) is allowed to do and (2) how review data stays isolated by entity. This matters because access reviews turn decisions into an enforced control with evidence. Done well, they help maintain least privilege on crown-jewel systems; produce defendable evidence for SOX, SOC 1 Type 2, SOC 2 Type 2, ISO/IEC 27001, GDPR, HIPAA, and PCI DSS; and help lean GRC and identity teams to focus on the access that affects risk, not volume. In short, it’s not only about who can do what; it’s also about keeping each entity’s review data strictly segregated. As a result, access control also needs to extend beyond just what users of different roles can perform, but also how to keep review data from one operating entity separate from another.
Within a typical access review program, there are multiple personas that play different parts tied to their job function, including:
- Access review program managers – these individuals are responsible for running the organization’s access review program; they often need to coordinate across all the persona’s listed below and have oversight across all review campaigns
- Assigned reviewers – these individuals are assigned line items in specific reviews to determine if a user’s access is still needed and justified; typically these individuals are people managers, application owners, entitlement owners, business process owners, etc.; reviewers should only see assigned line items – nothing more
- Coordinators/monitors – these are individuals embedded in business units within the organization that help coordinate the review and ensure reviewers are completing their assigned line items in a timely manner; they only need visibility into review campaigns relevant to their business unit
- Auditors – this may encompass both internal and external audits within the organization; auditors ultimately certify completed reviews
- Application owners – these individuals are responsible for in-scope applications; in some organizations, it may be their responsibility to ensure that their application data is correctly and accurately reflected in the Veza platform; they only need visibility into review campaigns relevant to their application
- Operators and administrators of the Veza platform – these are the individuals who are responsible for administering and operating the Veza platform; depending on the organization, they may or may not be directly involved in the access review program
This results in each of these personas requiring different levels of access to the reviews – and not necessarily visibility to all reviews.
Veza provides a comprehensive set of role-based and permission-based access controls to help customers effortlessly achieve their access requirements, always ensuring that permissions are sufficiently fine-grained to support the principle of least privilege for the different stakeholders and across operating entities during the entire access review process.
How Personas Collaborate Before, During, and After an Access Review Campaign
A successful review campaign requires participation and close cooperation across the different user personas. That collaboration is what turns policy into an enforced control with evidence.
Before the campaign. You need someone to administer the campaign – typically the access review program manager(s), but in smaller organizations, this could also include operators and administrators of the Veza platform with less specialization. This function involves setting up and creating the configurations and access reviews, requiring knowledge of what applications, identity providers, users, entitlements, and resources are in scope and therefore need to be included as part of the review campaign. They may also need some awareness about how this data is captured in the Veza Access Graph in order to properly scope the application-specific reviews. Once they have finalized the list of applications required for the access review campaign as well as defined the scope, they need to create the access review, set the cadence for recurrence, assign specific line items to the appropriate reviewers, and configure other settings such as downstream actions/workflows, review due dates, and notifications. Good scoping isn’t just housekeeping; it keeps reviewers focused on the rows that move risk.
During the campaign. Reviewers perform the review and recertification task. Reviewers need to be able to view the line items they’ve been assigned, take action to approve (maintain access) or reject (revoke access), and sign off to confirm their decisions. Reviewers are the largest and most diverse stakeholders in the process, by far, and they carry the most consequential workload. Where access is privileged or SOX-relevant, many teams add a second set of eyes so sensitive decisions aren’t made in a vacuum, and keeping reviewers informed without burying them is part of the job, and intelligent notifications help teams maintain momentum and accountability across the campaign..
After and between campaigns. Coordinators and monitors track progress, guide reviewers, and remove roadblocks so work keeps moving. Auditors, internal and external, certify that completed reviews meet policy and compliance requirements. Application owners ensure the campaign reflects how access actually works in their systems and support any technical steps to keep data accurate. Many teams also run small, targeted checks when risk changes instead of waiting for the calendar. For a practical pattern, check out this blog about on-demand reviews, useful for joiner, mover, leaver events, privilege escalation, or ownership changes.
The Veza Access Control Model for Access Reviews
Veza provides two dimensions of access control – what a user can see and what operations a user can perform. Access is controlled through a combination of assigned user roles, permissions on reviews and review configurations, row assignments in reviews, and settings.
User role assignment controls what actions users can perform on reviews and review configurations as well as on tenant-level configurations and settings.
Review configurations also maintain their own access control lists (called the “Limit Access” list) to determine which specific users in the tenant can read, update, or manage specific reviews.
Row assignment controls whether a reviewer can see assigned rows in a review as well as grants decision-making privilege.
Settings control review behavior, such as whether to allow reviewers to be able to export reviews.
Roles
The Veza platform has a number of out-of-the-box roles that Access Reviews customers can assign to users, based on their persona and function. These are split mainly into 3 categories – Admin/Operator, Reviewer, and Other (that perform supporting tasks related to reviews). More specifically, here’s the set of out-of-the-box roles supporting Access Reviews as well as their specific level of privilege as it relates to acting on rows in reviews, managing reviews and review configuration, managing application settings, and managing Veza Groups.
| Role | Configuration Permissions | Review Permissions | Actions on Rows | Settings | Veza Group Permissions |
| Admin | CRUD (all reviews) | CRUD (all reviews) | Full, all rows (all reviews) | Full across the entire tenant | CRUD |
| Access Reviews Admin | CRUD (all reviews) | CRUD (all reviews) | Full, all rows (all reviews) | Full (Access Reviews only) | R |
| Operator | CRUD (accessible reviews only) | CRUD (accessible reviews only) | Full, all rows (accessible reviews only) | None | R |
| Access Reviews Monitor | R (accessible reviews only) | CRUD (accessible reviews only) | Reassign only (accessible reviews only) | None | None |
| Reassigner | None | R (accessible reviews only) | Reassign only (accessible reviews only) | None | None |
| Watcher | None | R (accessible reviews only) | Read only (accessible reviews only) | None | None |
| Access Reviewer | None | R (assigned reviews only) | Full (assigned reviews only) | None | None |
Amongst the roles for access review campaigns:
- Admin: Can manage all settings, users, and has all privileges across the Veza platform including user management, system configuration, and complete platform administration.
- Access Reviews Admin: Can manage all settings, review configurations, reviews, and has full administrators privileges within Access Reviews. Outside of Access Review, has no administrative privileges.
- Operator: Can create reviews and review configurations, but visibility to other reviews and review configurations must be explicitly granted. Typically assigned to individuals who are responsible for creating and managing access reviews as part of a certification campaign.
- Access Review Monitor: Can view review configurations (when explicitly granted visibility), progress metrics, and completion status across all reviews derived from those configurations. Can instantiate reviews from a granted review configuration, but cannot create or modify review configurations. Typically assigned to individuals who are responsible for launching and monitoring review campaigns as well as tracking their progress.
- Access Reviewer: Limited role for users assigned to reviews. Reviewers can only see assigned reviews and act only on assigned rows.
- Reassigner: Specialized role with the ability to reassign any row in a review, but otherwise no ability to administer or manipulate reviews.
- Watcher: Can view reviews and applied decisions, but otherwise cannot make changes.
When a single user needs to maintain different personas, they can be assigned multiple roles simultaneously. In this case, they end up with the union of privileges for each assigned role.
The role assigned to a user dictates the default user interface that the user sees when they log into the Veza platform. For example, users with Admin, Operator, or Access Review Monitor roles land in the Veza administrative interface whereas users with the Reviewer, Watcher, and Reassigner roles land in the Access Hub – tailored to just the limited set of actions and tasks they’re able to perform against access reviews.
Limiting Access to Reviews
As established earlier, there is often a need to support diverse organizational structures for review campaigns that dictate a flexible access control model. This is common when compliance-specific campaigns are spread across different departments or operating entities within an organization and each needs to restrict access for their specific reviews. When this happens, operators and other stakeholders need to have a narrower scope by being granted access to only a subset of configurations and reviews. This separation of access can be achieved by the Limit Access capability in Veza Access Reviews, which is effectively an access control list applied to review configurations and inherited by reviews.
Note: By default, Limit Access functionality is disabled on customer Veza tenants, though the functionality can be enabled upon request to Veza Technical Support or Customer Success.
Veza Groups
Veza Groups are identity containers that help organize common users with similar permissions for scaling access management. Groups aggregate users to allow for collectively assigned permissions making it easier to manage access control at scale.
Veza Groups contain multiple users as members – including both local Veza users as well as SSO users. Users can also belong to multiple groups simultaneously.
Some of the key capabilities of Veza Groups include:
- Can be granted access to reviews and review configurations through the Limit Access list
- Can be designated for entity ownership
- Can be designated for ownership of Access Profiles and integrations
- Can serve as approvers in access request workflows
There are two types of Veza Group, including:
- Customer-managed (created in Veza), and
- SCIM-managed (provisioned from identity providers)
SCIM-managed Veza Groups can be automatically synchronized from external identity providers via inbound SCIM provisioning.
Additional Capabilities
Veza makes it easy for users assigned the Access Reviewer role to see exactly what they need to work on so they aren’t spending time looking for their assigned reviews. For instance, users only assigned the Access Reviewer role will only see reviewers where the user has assigned rows. Similarly, when the reviewer opens a review, they only see the uncompleted rows assigned to them – nothing more; nothing less.
For users assigned the Access Reviewer role as well as another administrative role, the main reviews list page adapts. A new filter card entitled “Needs My Review” lets the user, as a reviewer, quickly filter the view to only include the reviews that have rows assigned to them.
Once the user opens a specific review, they will see 2 tabs entitled “All” and “Assigned to Me”. These allow the user to quickly filter the review to show only the rows they need to make decisions on (“Assigned to Me”) vs. “All” rows. This combination of navigational aids greatly helps in surfacing what’s most pertinent and immediately actionable for a reviewer to address as soon as they log in to Veza.
Conclusion: Essential Control for Compliance
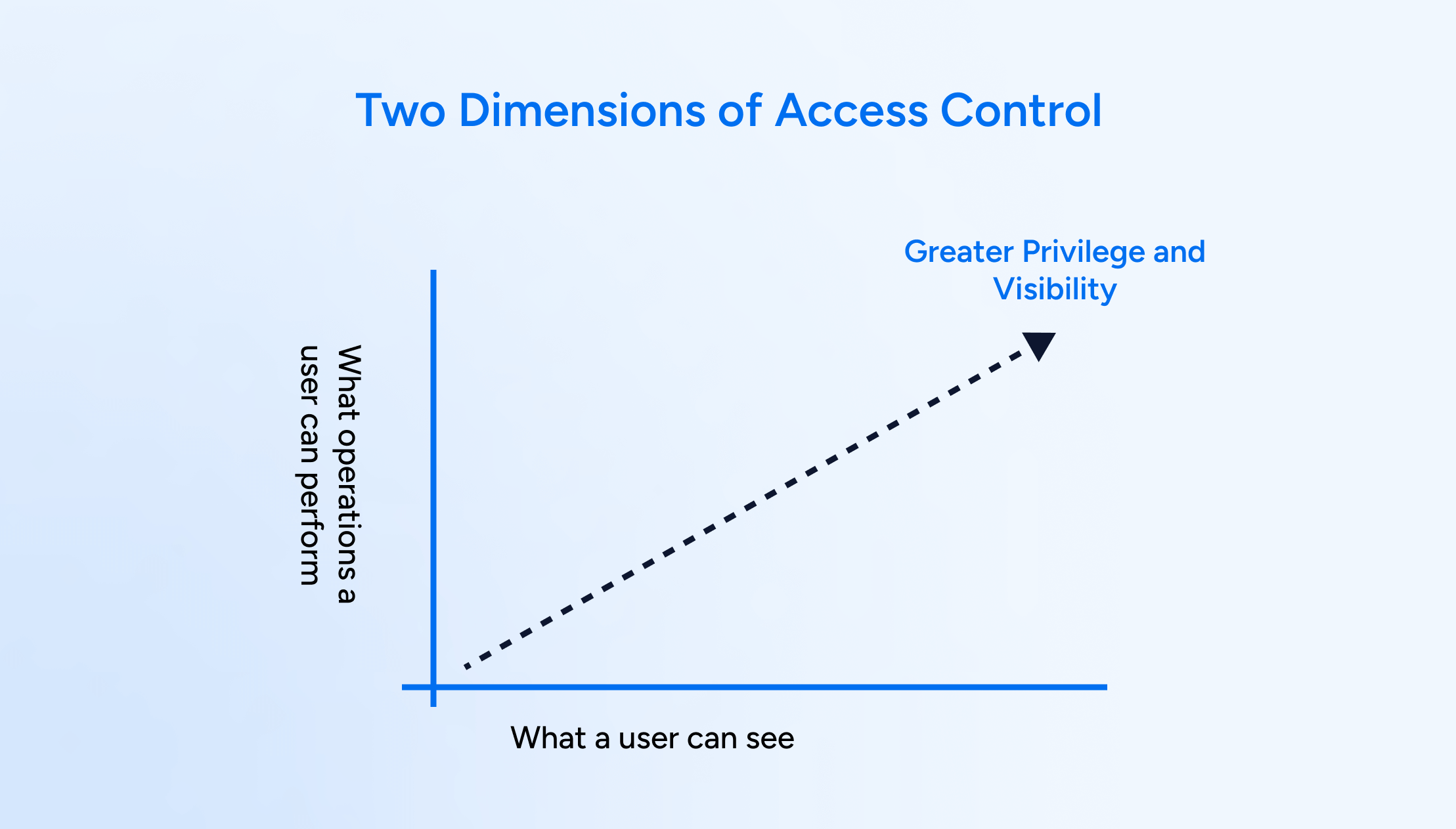
Veza Access Reviews provides powerful, granular access control demanded by modern enterprises that need to adhere to the principle of least privilege within their IGA platform. The core is a two-dimensional access model – controlling visibility (“what a user can see”) and operational actions (“what operations a user can perform”).
Access is enforced by the assigned user role and row assignment as well as the Limit Access list. Features like Veza Groups enable permission management at scale whilst Limit Access provides flexible scoping for review campaigns across departments. Ultimately, Veza’s comprehensive access controls help organizations efficiently enforce their security requirements and meet rigorous compliance demands.
Next steps
Learn the practice
The Definitive Checklist for User Access Reviews
See it in action
Modernizing User Access Reviews (webinar)
Talk with us
Request a Demo






