
For decades, your security strategy has been about building strong walls to keep the adversaries out. However today, the adversary is already inside, as they prioritize access over exploits. Ransomware accounted for 58% of large claims, and 79% of attacks are now malware-free, as adversaries are relentlessly capitalizing on compromised credentials to simply log in to your network. Identity has become the new battleground, where adversaries exploit misconfigurations, dormant accounts, and over-permissioned roles. Hence, your identity security posture has a direct bearing on insurability as you must now provide verifiable proof to contain escalating premiums and to maintain coverage.
Why Shifting to Authorization-Focused Security Matters Now
Organizations have rightly invested in authentication, adopting MFA and anti-phishing controls that insurers now require. But authentication only verifies who you are—it doesn’t protect against attackers using stolen, valid credentials. With excessive permissions, adversaries can move laterally, escalate privileges, and remain undetected.
That’s why authorization, or what identities are allowed to do, must become central to identity security. Visibility into permissions and access rights exposes hidden risks across users, non-human identities, API keys, AI agents, and third-party vendors. As automation and AI expand the attack surface, authorization intelligence is the missing control to close today’s identity security gap.
The Four Key Authorization Blind Spots That Impact Insurability
When insurance brokers and underwriters assess your identity risk landscape, they look for clear evidence and data-driven answers that will eventually determine your insurability, coverage and premiums, across these four critical areas:
- Privileged Access and Dormant Accounts:
This goes beyond just having a PAM solution. You have to demonstrate to the underwriters that you have a full inventory of all privileges, visibility into dormant/unused privilege permissions, and prove that you enforce the principle of least privilege across your entire organization. - Non-Human Identities (NHIs):
One of the most critical blind spots in any organization is visibility into Non-Human Identities (NHIs) and the risks they present. Insurers and underwriters want to get a clear picture of your NHI landscape, including shadow NHIs. You have to demonstrate that you have complete NHI accountability that shows all assigned human owners, along with evidence of your NHI and AI governance processes, proving that you have complete control over all NHIs.
- Third-Party and Supply Chain Risks:
Managing access for your vendors, contractors, and software supply chain is a crucial part of your identity strategy. Insurers and underwriters demand to know precisely how you manage, audit and limit the access granted to these external identities.
- Toxic Combinations and SoD Risks: A more common, but invisible identity security risk is from the intersection of access permissions across different applications and systems. Underwriters need proof that you have processes in place to check internal fraud and data misuse arising from toxic combinations, and to detect separation of duties (SoD) violations in real time, in addition to demonstrating an auditable policy enforcement trail.
Power Cyber Insurability With Veza
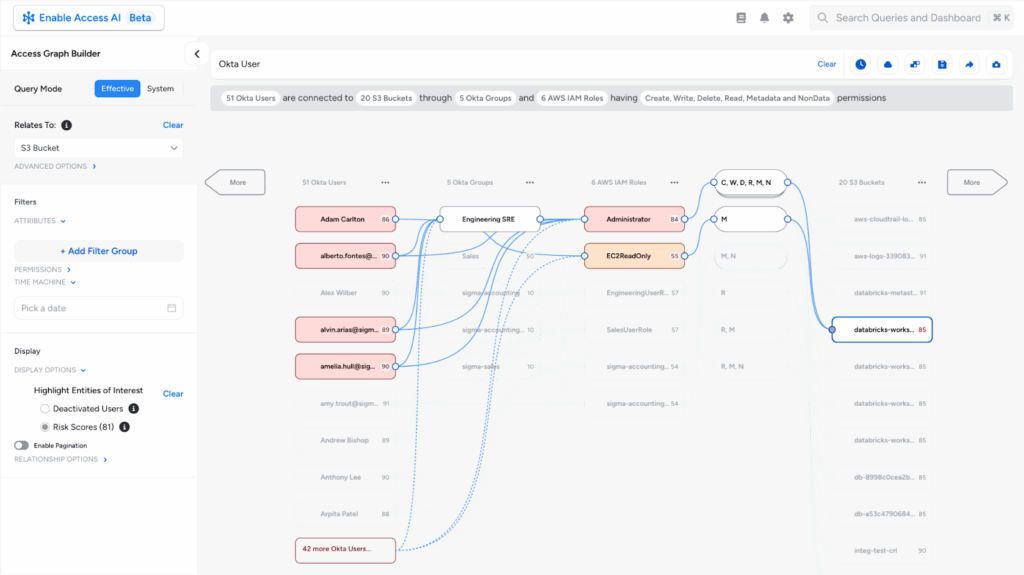
To become and stay insurable, and to optimize premiums with better coverage, you must shift your focus from authentication to authorization. Veza provides you with the single source of truth to continuously visualize, understand and control access permissions for all identities, and eventually prove to underwriters that you have a mature identity security program. With Veza:
- Map your entire identity landscape: The Veza Access Graph creates a unified map of who can take what action and on what data, by continuously correlating authorization metadata from 300+ enterprise systems. This gives you the visibility and intelligence needed to find and fix access risks before they can be exploited.
- Get proactive access intelligence: Veza Access Intelligence helps you instantly surface privileged users, dormant permissions, and policy violations with 2000+ pre-built queries. This proactive intelligence is the foundation of a resilient and insurable security program.
- Effortlessly realize least privilege access: Veza Access Monitoring enables you to quickly identify and remove unnecessary permissions and right-size roles to align with the principle of least privilege (PoLP), with instant visibility into both who can access what and who has accessed what.
- Continuously score all identity risks: Veza’s risk engine provides measurable data on your identity security posture in real time. This provides the hard data required to prove to underwriters that your security strategy is dynamic and robust, while automated workflows help you manage access reviews and lifecycle management.
Provide the Right Answers to Insurers, Everytime
Veza helps you shift to a proactive approach to meet the dynamic demands of the cyber insurance market that sees identity as the single biggest component determining insurability.
“Ransomware groups are using credentials obtained via phishing attacks or stolen in cyber-attacks, including those targeting IT suppliers, and sold on the dark net. Using credentials is easier than hacking. Once they get the ‘keys to the kingdom’ hackers can quickly access a system, elevate their access privileges and then move through the system.” – Cyber security resilience 2025, ALLIANZ COMMERCIAL
Instead of reacting to questionnaires, it’s time to proactively manage the identity risks that determine your coverage, providing underwriters with hard, verifiable evidence of your identity security controls.
Prove Your Insurability. Cut the Noise. Act.
- Download the white paper: A CxO’s Guide to Proving Insurability with Authorization Data
- See the use case: How Veza operationalizes authorization data for cyber insurance
- Request a demo: Get a live readout of your identity risk posture





