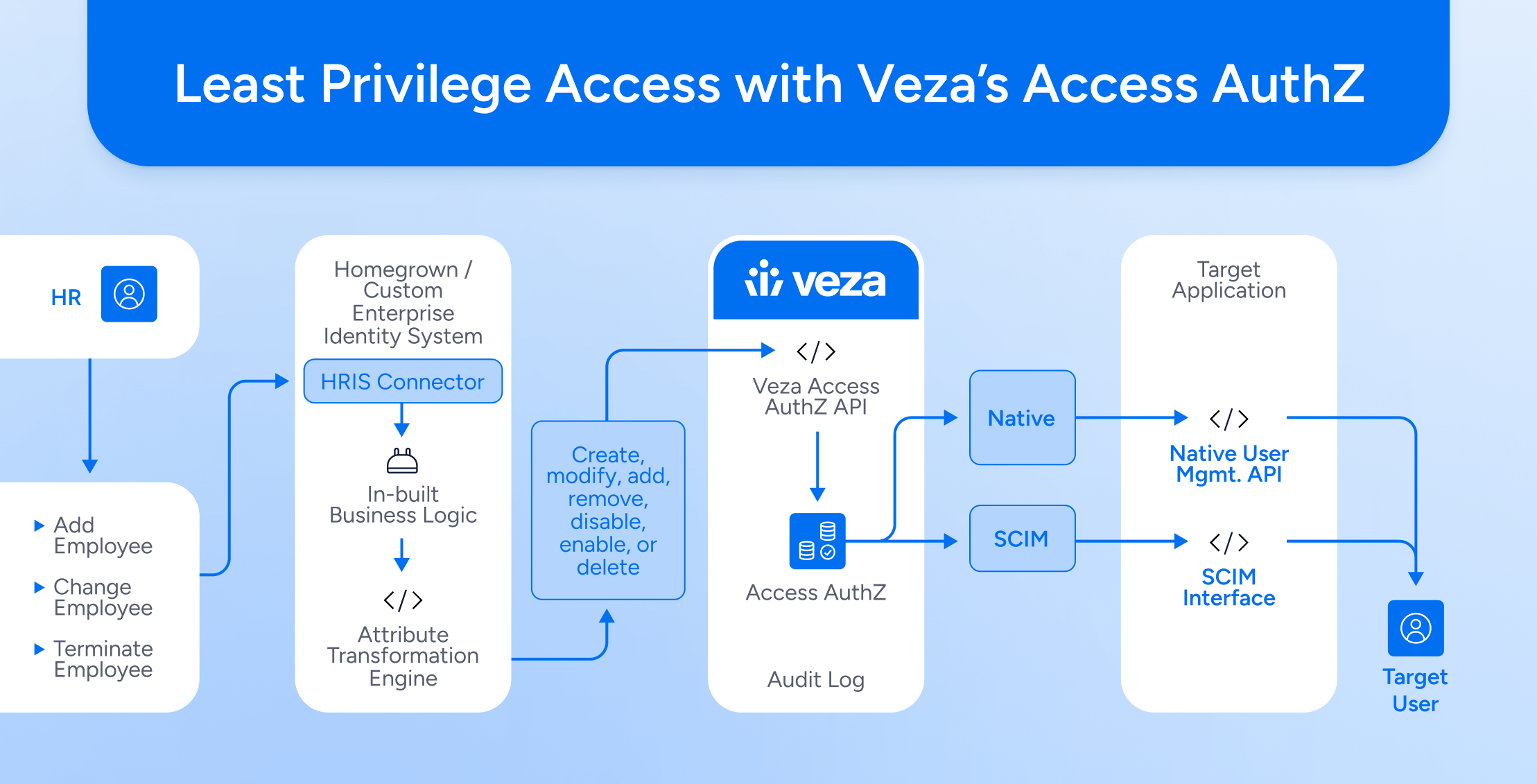
As the average enterprise utilizes hundreds of applications, effective provisioning and deprovisioning demand robust integrations between identity sources and target systems. Many enterprises invested heavily in legacy IGA solutions, ITSM platforms, or even cobbled together homegrown tools or scripts over time. Unfortunately, this has proven to be a difficult, expensive, and never-ending endeavor. Notwithstanding the fact that most organizations lack staff with the necessary technical skills, building and maintaining integrations for provisioning and deprovisioning across hundreds of applications is tedious, error-prone, unscalable, and shockingly expensive to maintain.
Identity as the New Security Perimeter
It’s been well-established that identity is the new security perimeter, meaning that organizations must rapidly achieve true least-privilege access across all systems and data. This means ensuring every user, application, service, and system only has the minimum necessary access for its job. This drastically reduces the likelihood and impact of security breaches by limiting an attacker’s lateral movement in the case of account compromise. Enforcing least privilege also helps minimize the likelihood and impact of data breaches, ransomware attacks, and other types of widespread disruption or mayhem.
Two of the cornerstones of capabilities to reach “true” least privilege are:
- Complete visibility and risk assessment for all users, entitlements, resources, and permissions across all applications
- An ability to rapidly provision and deprovision users with appropriate access to/from those applications
It was with these outcomes in mind that Veza married its Access Graph-based visibility and risk analytics capabilities (Veza Access Visibility and Veza Access Intelligence) with its innovative birthright entitlement provisioning and just-in-time access request capabilities (Veza Lifecycle Management and Veza Access Requests). The results were numerous:
- Day 1 Productivity: New employees became productive immediately since proper birthright entitlements could be provisioned by Day 1.
- No Entitlement Accumulation: Employees, contractors, and guest workers who changed roles or positions with the organization no longer accumulated unnecessary access privileges over time since policy-based deprovisioning could now automate access removal. This ensured true least privileged access was being maintained.
- Elimination of Orphaned, Abandoned, and Other Risky Accounts: Orphaned, abandoned, non-compliant accounts tied to terminated employees, and other risky accounts with residual amounts of access could now be quickly identified and actively remedied. In particular, access for terminated employees was now eliminated as fast as former employees could be walked out the door.
Still, many organizations face a number of different challenges.
First, some organizations had legacy IGA or homegrown systems in place. Original aspirations for these systems may have been ambitious, but the reality was that many of these systems never got too far off the ground – only integrating with a very small proportion of the critical systems and applications originally envisioned. At the same time, these systems – even in their limited state – have become too entrenched in employee onboarding/offboarding processes to rip out. The result? A stalemate.
What is the way out? Gartner’s VIA (Visibility, Intelligence, and Automation) model describes how modern identity programs can break this stalemate by first achieving full visibility into who has access to what, applying intelligence to analyze and prioritize risks, and finally implementing automation to continuously enforce least privilege at scale.
Other organizations have increasingly started deploying more homegrown access request systems using their enterprise ITSM platform to begin a transition toward more just-in-time access. While these organizations may have found it easy to create online forms and marry them to an approval workflow, actually plumbing the request and approval process into access provisioning and deprovisioning has been daunting – different APIs for different applications, different access granting models, challenges achieving consistent deprovisioning, etc.
What all these organizations need is a single, universal interface to extend last-mile provisioning and deprovisioning capabilities to their legacy IGA, ITSM, SOAR, and custom applications, such that those applications could consistently provision and deprovision user access across a diverse set of applications, platforms, systems, and databases. This was the genesis behind Veza Access AuthZ.
Introducing Veza Access AuthZ
Veza’s Access AuthZ offers a secure and seamless way to manage user access programmatically for applications across cloud, SaaS, and on-premise environments (including legacy and custom applications), helping you ensure both Day 1 productivity and true least privilege access.
Delivered as an API, Access AuthZ can be easily integrated with existing legacy IGA, ITSM, and SOAR systems as well as custom applications, facilitating secure and seamless last-mile provisioning and deprovisioning for target applications. This eliminates the need for enterprises to develop integrations one at a time between their systems and target applications. By seamlessly integrating a modern, unified provisioning/deprovisioning API with their legacy IGA, ITSM, SOAR or homegrown systems, enterprises can achieve rapid time to value and reduce their total cost of ownership (TCO) compared to alternatives – namely point-to-point integrations developed one target system at a time.
Veza Access AuthZ provides comprehensive application support
- Veza Access AuthZ supports secure last-mile provisioning and deprovisioning actions for a range of leading target applications (platforms, systems, databases, and applications) supporting critical business functions to ensure seamless business continuity. Veza natively supports leading applications, databases, and platforms from Microsoft, Google, AWS, Salesforce, SAP, Oracle, GitLabs, Okta, Snowflake, PostgreSQL, Atlassian, Splunk, and more.
- Veza Access AuthZ also supports the SCIMv2 protocol, so the entire universe of SCIM-enabled applications is also fully supported.
- Veza Access AuthZ is flexible. Beyond native application integrations and SCIM support, Veza Access AuthZ really shines in its potential to support custom and legacy applications using Veza’s unique Open Authorization API (OAA) Write framework. With OAA Writes, Access AuthZ can be used to provision and deprovision users and modify their access across custom applications powered by OAA, increasing the utility of Access AuthZ in achieving true least privilege. The same framework can also be used to provide the Veza platform with visibility into the applications – crucial for monitoring, alerting, risk analytics, and more.
Secure Provisioning and Deprovisioning using Veza Access AuthZ
Supporting multiple target systems is crucial, but it’s equally important to comprehensively address provisioning and deprovisioning across critical systems. Veza Access AuthZ offers a complete suite of user and entitlement management actions to facilitate mission-critical provisioning and deprovisioning scenarios. This can help ensure true least privilege as well as help remediate identity-related vulnerabilities, such as dormant accounts, non-compliant accounts, entitlement accumulation, and more. These actions include:
| API Method | Description |
|---|---|
| Create User | Creates a local user account in an integrated target system |
| Update User | Updates a local user account in an integrated target system |
| Disable User | Disables a local user account in an integrated target system |
| Enable User | Enables a disabled local user account in an integrated target system |
| Delete User | Deletes a local user account in an integrated target system |
| Add User to Group/Role | Adds a local user account to a group or role in an integrated target system |
| Remove User from Group/Role | Removes a local user account from a group or role in an integrated target system |
Importantly, this is a single interface to support all applications – the same interface for user and entitlements management operations from Active Directory to Oracle; from Snowflake to Atlassian Cloud; and beyond.
Benefits of Veza Access AuthZ
Broad applications support on Day One
- SCIMv2 support for user provisioning and deprovisioning enables out-of-the-box support for literally thousands of applications and platforms that natively support SCIM.
- Native support for leading applications, databases, and platforms from Microsoft, Google, AWS, Salesforce, SAP, Oracle, GitLab, Okta, Snowflake, PostgreSQL, Atlassian, Splunk, and more.
- Veza’s unique OAA Write framework allows customers, third-party ISVs, and integrators to add support for legacy and custom applications.
- All integrations simultaneously support both visibility in Veza’s Access Graph as well as user provisioning/deprovisioning.
Enhanced Security
- Automating provisioning and deprovisioning reduces the likelihood of manual errors and the risk of unauthorized access, ensuring that identities are provisioned and deprovisioned accurately and promptly – minimizing the attack surface and strengthening overall identity security.
Backed by Veza’s standardized REST API endpoint:
- Enterprises can leverage a common REST API endpoint for all user provisioning/deprovisioning operations across a diverse set of target applications
- Developers can get started fast without mandating the need to learn a new API for every new application, platform, or database that they need to integrate
Operation Efficiency:
- Streamlined access provisioning and deprovisioning significantly improve efficiency by reducing the time and resources traditionally spent on manual identity lifecycle management.
- Simplification frees up IT and security teams to focus on more strategic initiatives.
No Connectors to Manage; No Service Desk Tickets
- As a SaaS, Veza maintains the application connectors, including all updates, bug fixes, and security patches. Nothing to upgrade – even to receive updates and enhanced functionality
- Since Access AuthZ is performing the actual user and entitlement management operation on the target applications in an automated manner, there are no service desk tickets flying around, forcing application owners to take manual action. This dramatically reduces Mean Time to Provision/Deprovision – the core metric for any mature identity program
Rapid Time to Value:
- Easy to integrate Access AuthZ with its flexible, powerful API with external systems, such as legacy IAM, ITSM, SOAR, and custom applications, reducing total cost of ownership (TCO) and accelerating time to value.
Compliance and Audit-Ready:
- Robust auditing and reporting capabilities enable organizations to maintain clear records of access provisioning/deprovisioning operations. This is crucial for meeting regulatory compliance requirements and demonstrating a strong security posture during audits.
Navigating the complex landscape of identity threats requires enterprises to strike a delicate balance between productivity and security. Traditional IGA and ITSM tools often rely on costly custom integrations, thus escalating the total cost of ownership (TCO) with the need for continuous maintenance and constant monitoring. Veza’s Access AuthZ automates critical provisioning and deprovisioning operations across an extensive range of SaaS, cloud, and on-prem applications, databases, systems, and platforms (along with support for custom and homegrown applications), offering broad application coverage on Day 1 and delivering rapid time to value. This approach enables security and identity teams to operate at the speed of innovation without sacrificing security or compliance.
Next Steps
Start here: Automated Access Revocation & Access Remediation — why deprovisioning is the bottleneck, patterns to kill standing access, and how to measure MTTP/MTTR impact.
Go deeper: Modernizing Identity with Just-in-Time Access — On-Demand Webinar — how to wire JIT approvals to policy-driven enforcement and extend control into legacy and custom apps with OAA.
See it in action (BOF): Request a demo — live walkthrough of Access AuthZ driving adds, changes, and revokes across AD, SaaS, cloud, data, and legacy systems to slash mean time to provision/deprovision.





