Blog
-
 Company
CompanyAnnouncing Veza’s Series D: Securing Identities through Achieving Least Privilege
How do you achieve the principle of least privilege? One access permission at a time. Today, I am thrilled to share a significant milestone in Veza’s journey: we have raised $108 million dollars in Series D funding, led by New Enterprise Associates (NEA) with participation from all our existing investors—including Accel, GV (Google Ventures), True […] -
 Identity Security
Identity SecurityVeza Access AI – Applications of Gen AI for Identity Security Use Cases
Veza Access AI transforms identity security by enabling natural language queries to navigate complex access landscapes, empowering organizations to achieve least privilege effectively.
Explore our posts
-
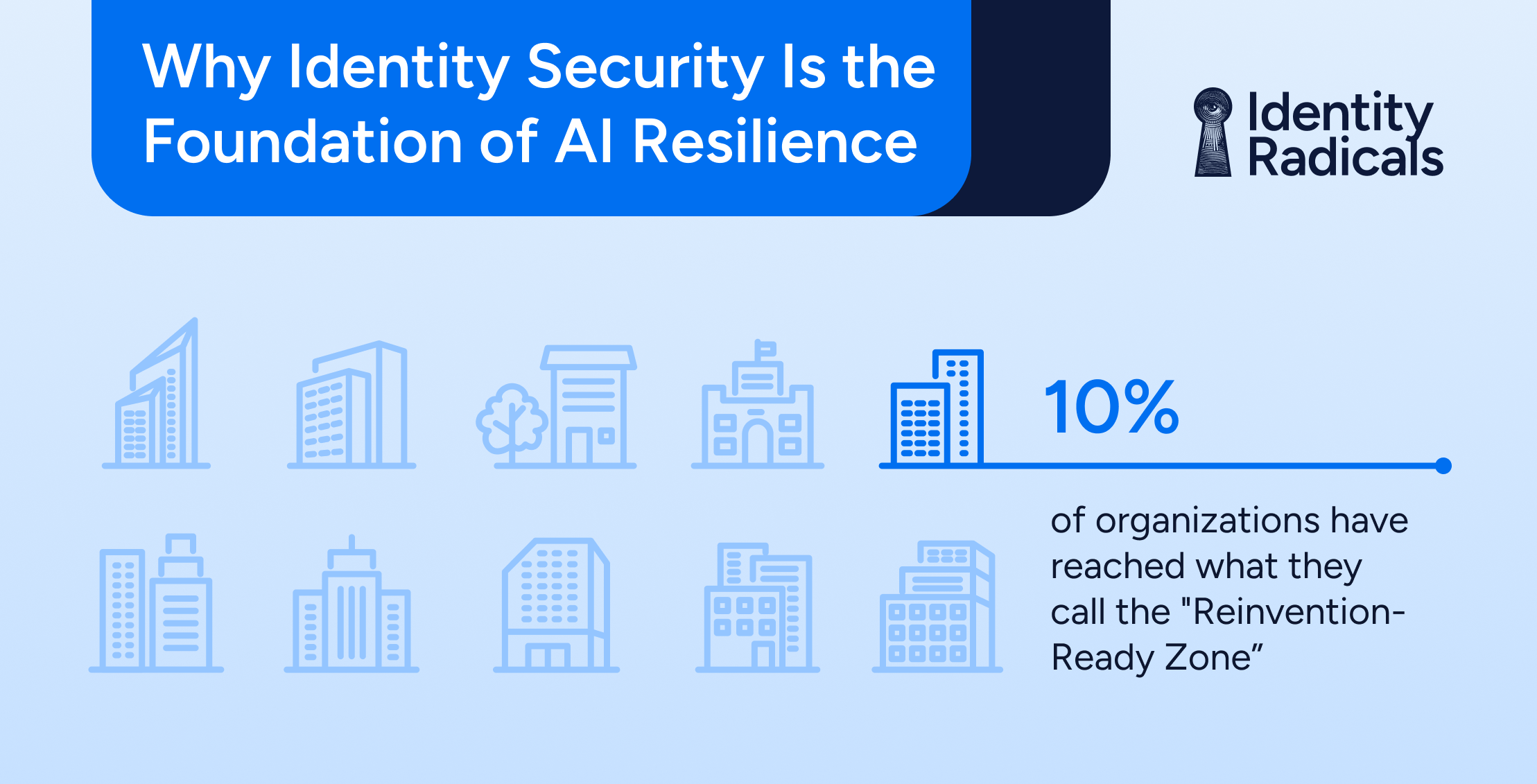
From Exposed to Reinvention-Ready: Why Identity Security Is the Foundation of AI Resilience
Learn more -

What is Third Party Risk Management (TRPM)?
Learn more -

Better Together: Augmenting SailPoint with Full-Stack Access Visibility
Learn more -

17 Best data governance tools [2025 review]
Learn more -

12 Best Identity Security Software [2025]
Learn more
-
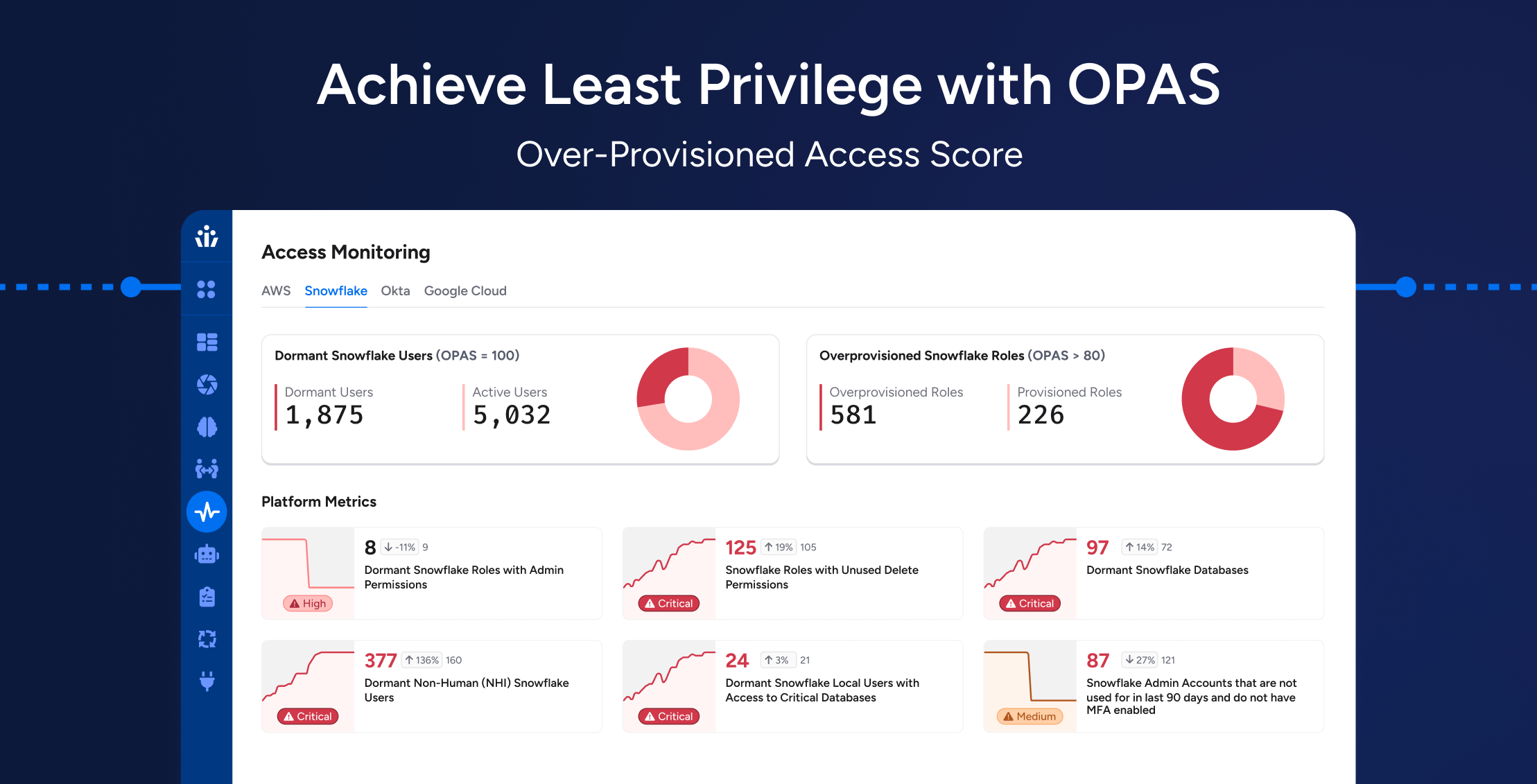
Achieving Least Privilege at Scale: How OPAS Helps Enterprises Reduce Hidden Access Risks
Learn more -
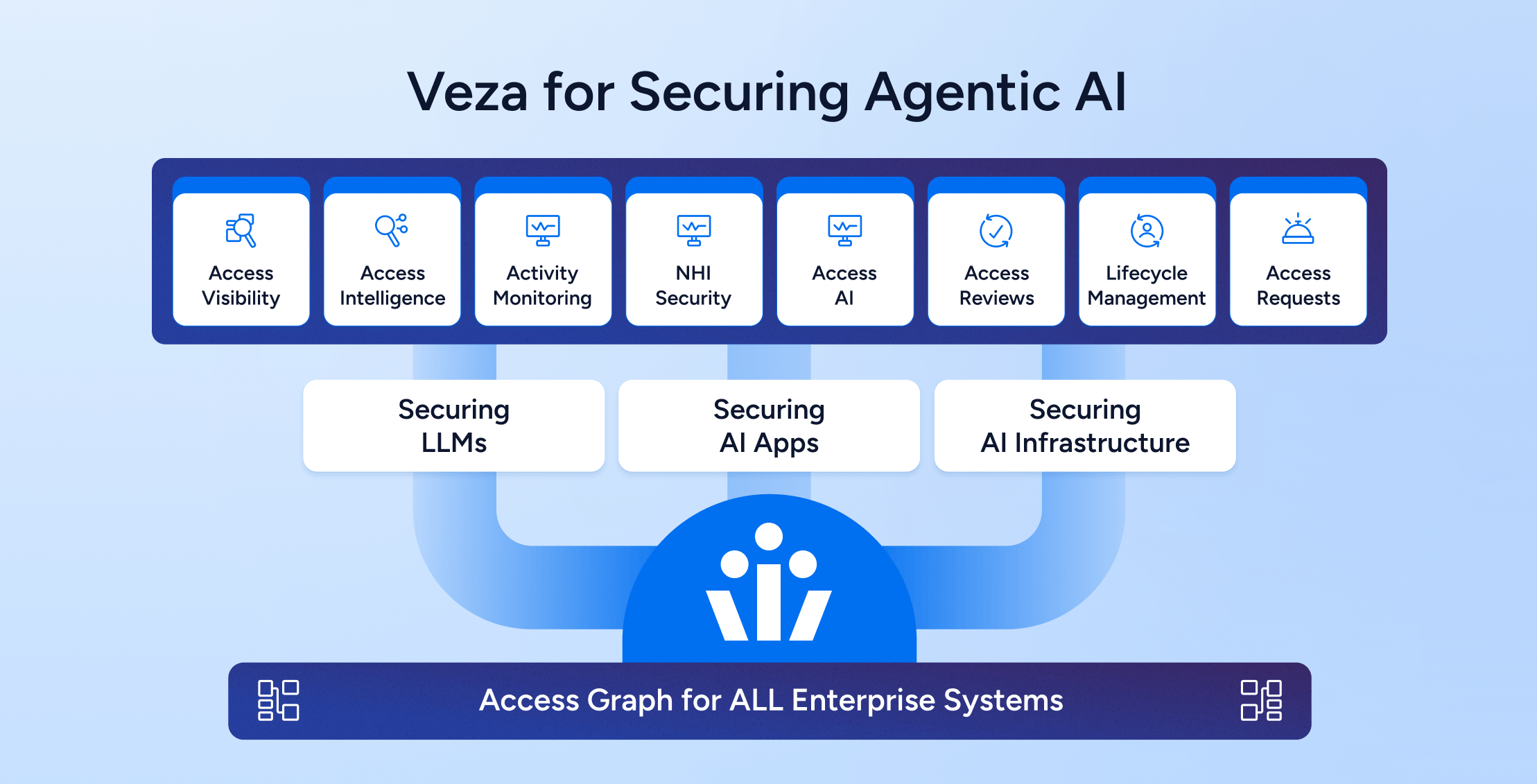
Trust as the Foundation for Agentic AI Architecture: Securing Access to all the AI layers – Models, Infra, AI Applications
Learn more -
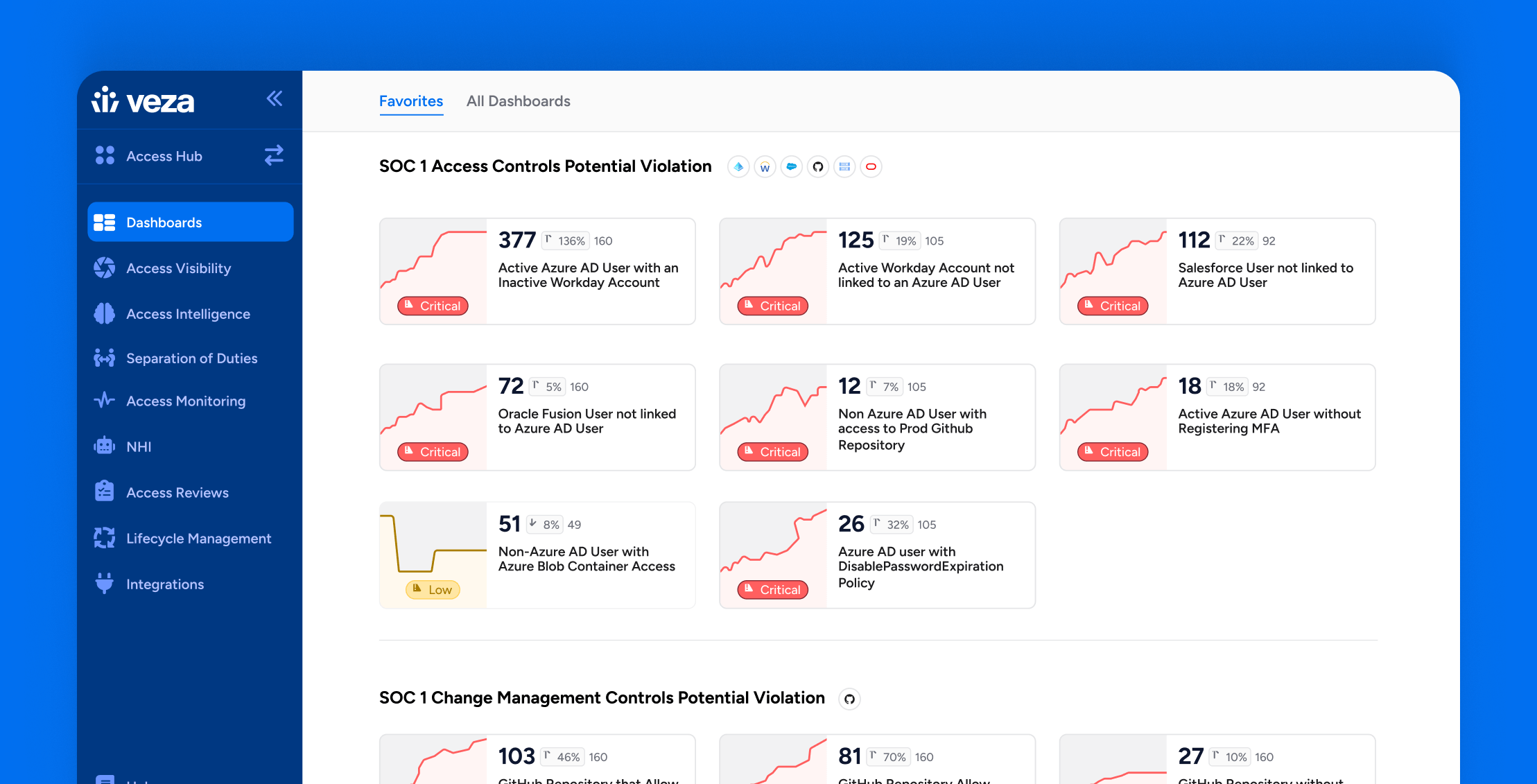
How Veza Strengthens SOC 1 Compliance: Common Control Failures & How to Fix Them
Learn more -
Model Context Protocol (MCP): Implications on identity security and access risks for modern AI-powered apps
Learn more
-

12 Best Identity Security Software [2025]
Learn more -
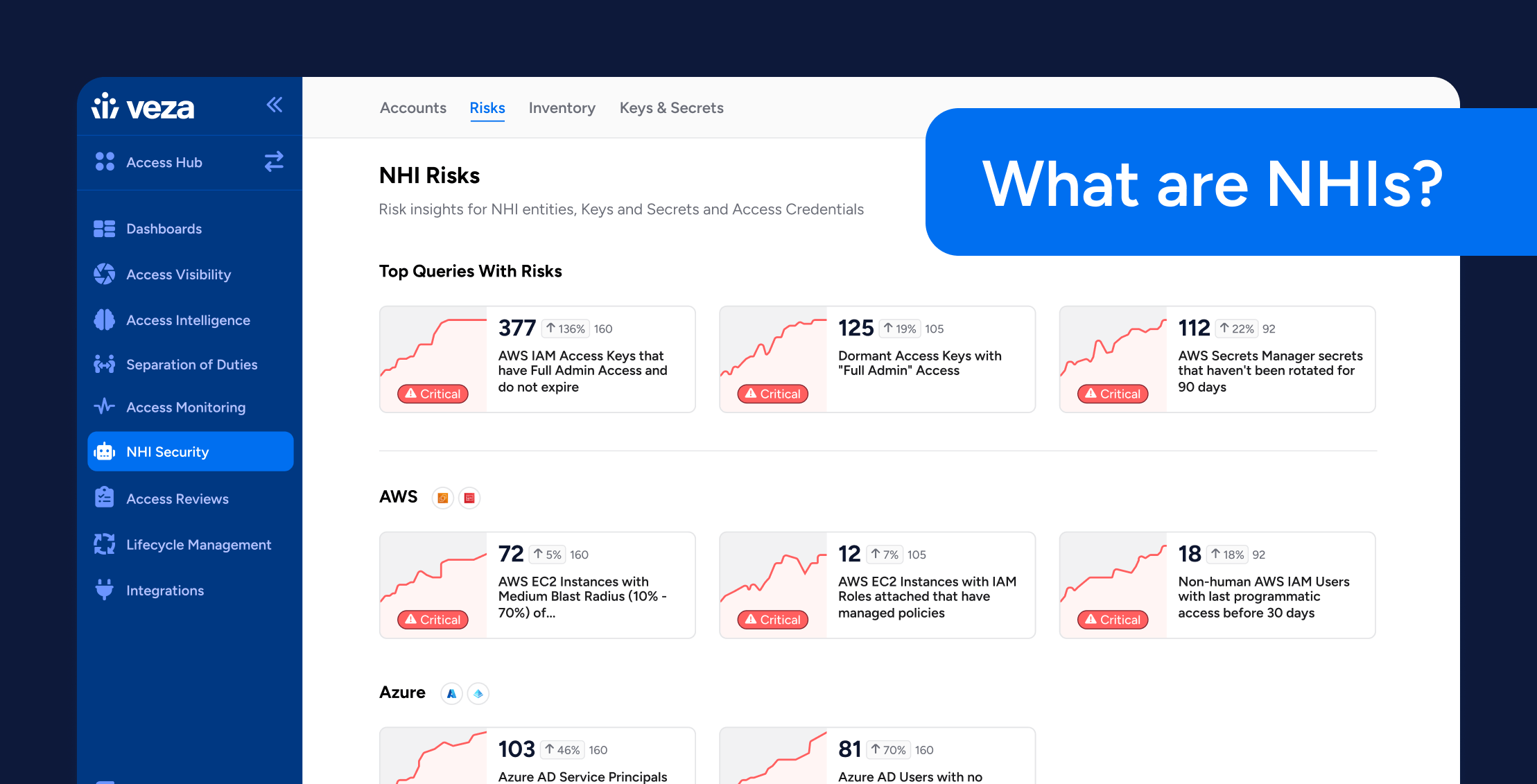
What Are Non-Human Identities?
Learn more -
Identity is Eating Security: Why Access Is the New Perimeter
Learn more -

Achieving Least Privilege at Scale: How OPAS Helps Enterprises Reduce Hidden Access Risks
Learn more -

Achieving DORA Compliance: A Practical Guide for Financial Organizations
Learn more
-

From Exposed to Reinvention-Ready: Why Identity Security Is the Foundation of AI Resilience
Learn more -

Identity Crisis: The Rise of Machines
Learn more -

Identity is Eating Security: Why Access Is the New Perimeter
Learn more -

When Logging In Is the New Hacking: Nicole Perlroth on the Evolving Cyber Threat Landscape
Learn more
-

I Attended the Verizon Data Breach Session at RSA So You Don’t Have To:
Learn more -

Reflections from Gartner IAM London: Visibility Leads to Observability
Learn more -

Achieving DORA Compliance: A Practical Guide for Financial Organizations
Learn more -

Join us at Black Hat USA August 3 – 8, 2024
Learn more -

Join us at RSAC May 6-9, 2024
Learn more -

Veza @ AWS re:Invent
Learn more