Blog
-
 AI
AIVeza – The Enterprise Agent Identity Control Plane
Veza’s 2026 State of Identity and Access Report found that in a typical enterprise, an average worker holds 96,000 entitlements, 38% of IdP accounts are dormant and only 55% of permissions are safe and compliant. The volume and complexity of identity-based attacks is exacerbated by the explosion of AI agents and non-human identities (NHIs). In […] -
 Company
CompanyServiceNow + Veza: A new chapter in identity security
Today marks a pivotal moment—not just for Veza, but for the entire identity security industry. I’m deeply proud to share that ServiceNow has signed a definitive agreement to acquire Veza. Together, we will accelerate the mission to secure identity across the modern enterprise as organizations transition into the era of agentic identities. When Maohua, Rob, […]
Explore our posts
-

Taming the M&A Chaos: How Veza Addresses Identity Security Risks During Mergers, Acquisitions, and Divestitures
Learn more -

Automating Veza Access Requests for the Enterprise: Integrating Veza with ServiceNow
Learn more -

Forrester Recognizes Veza for IGA, ISPM, and NHI/AI Identity Management
Learn more -
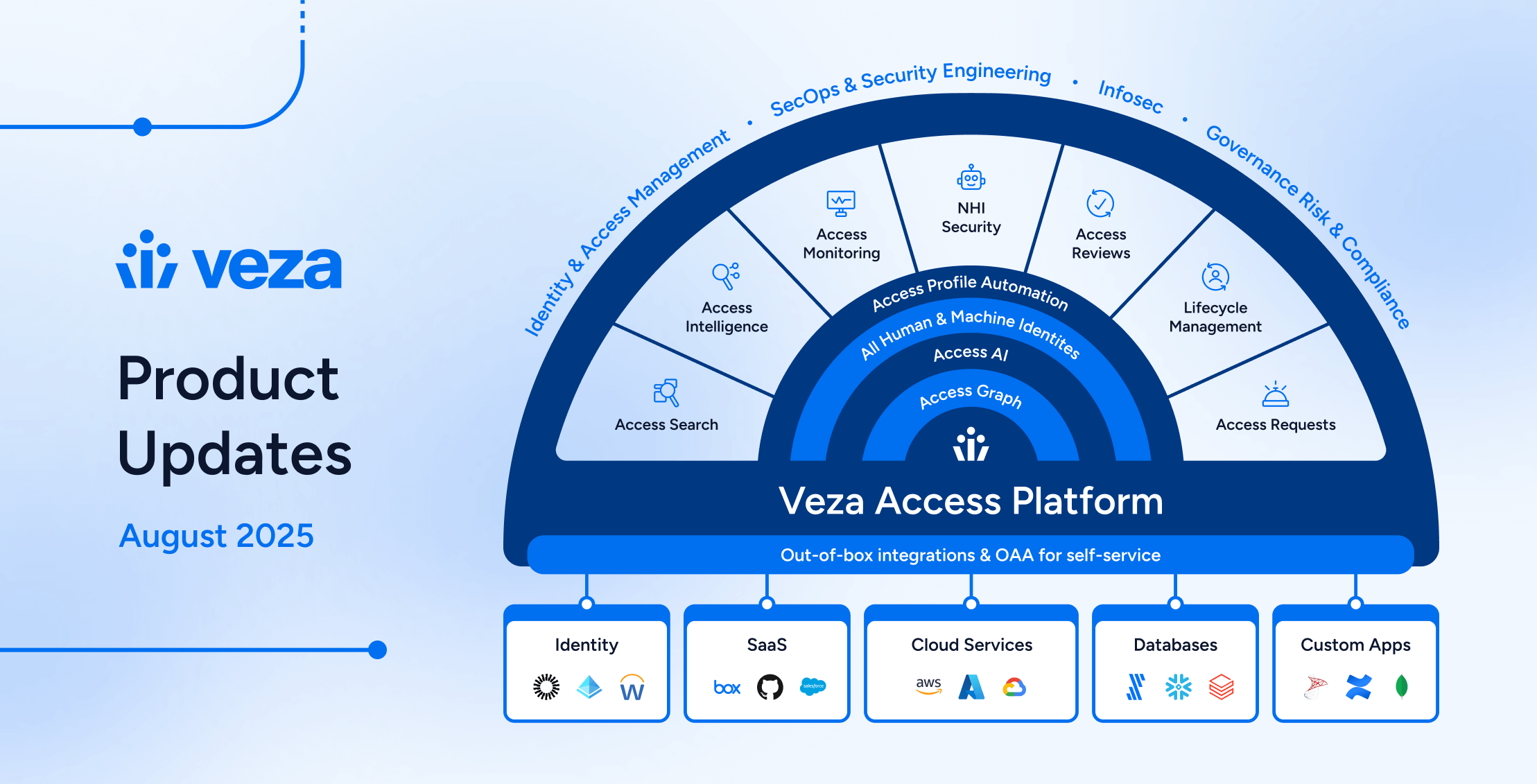
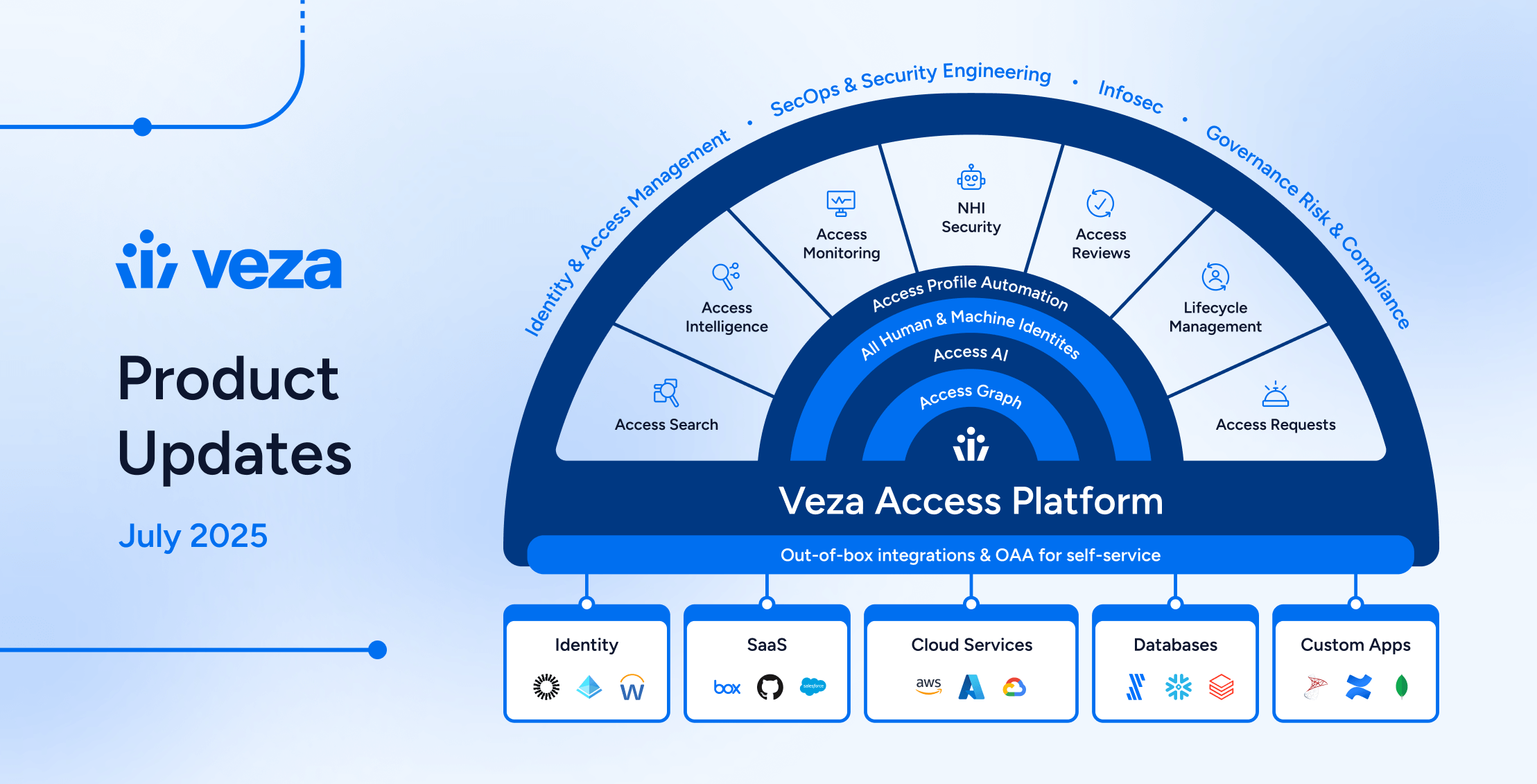
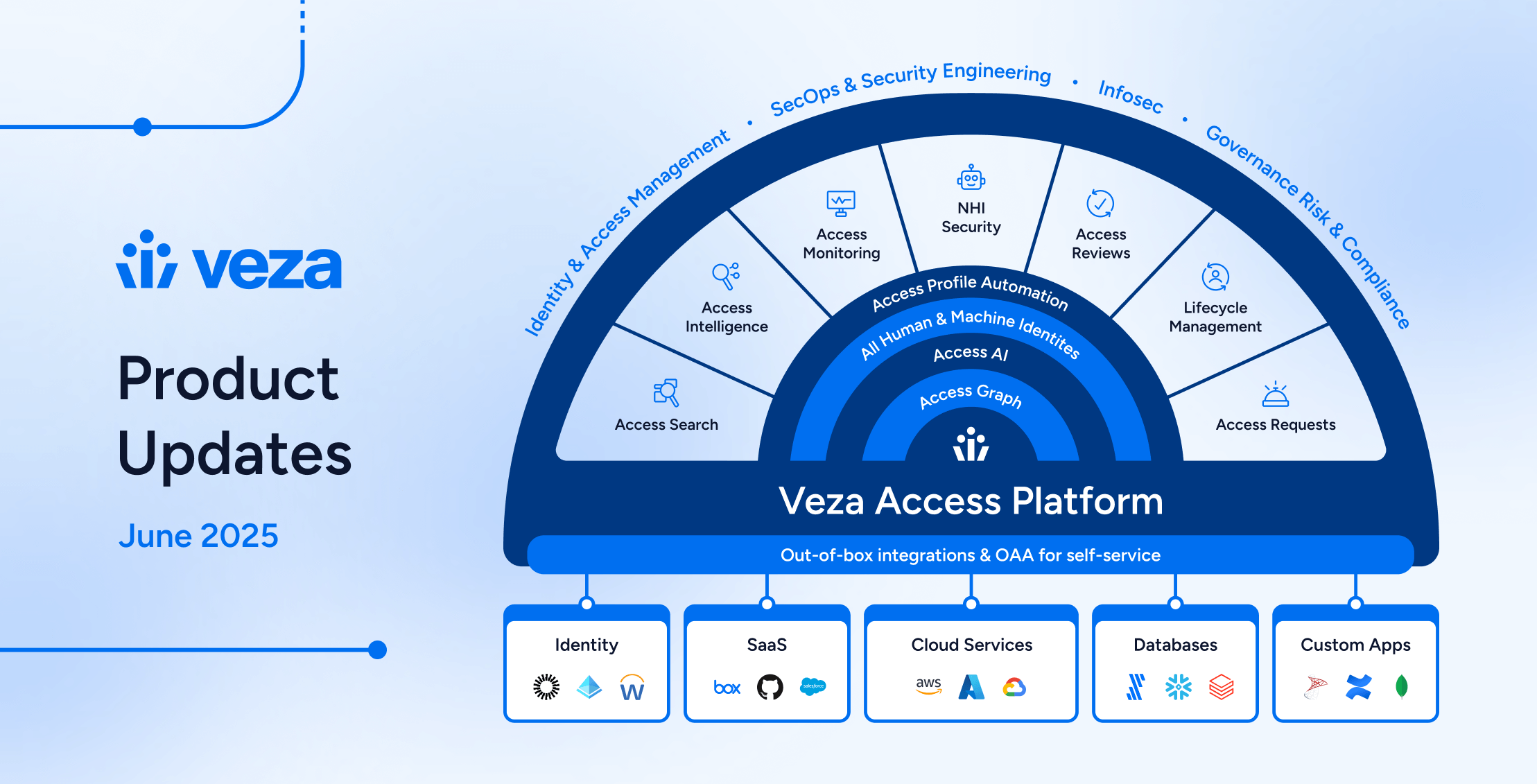
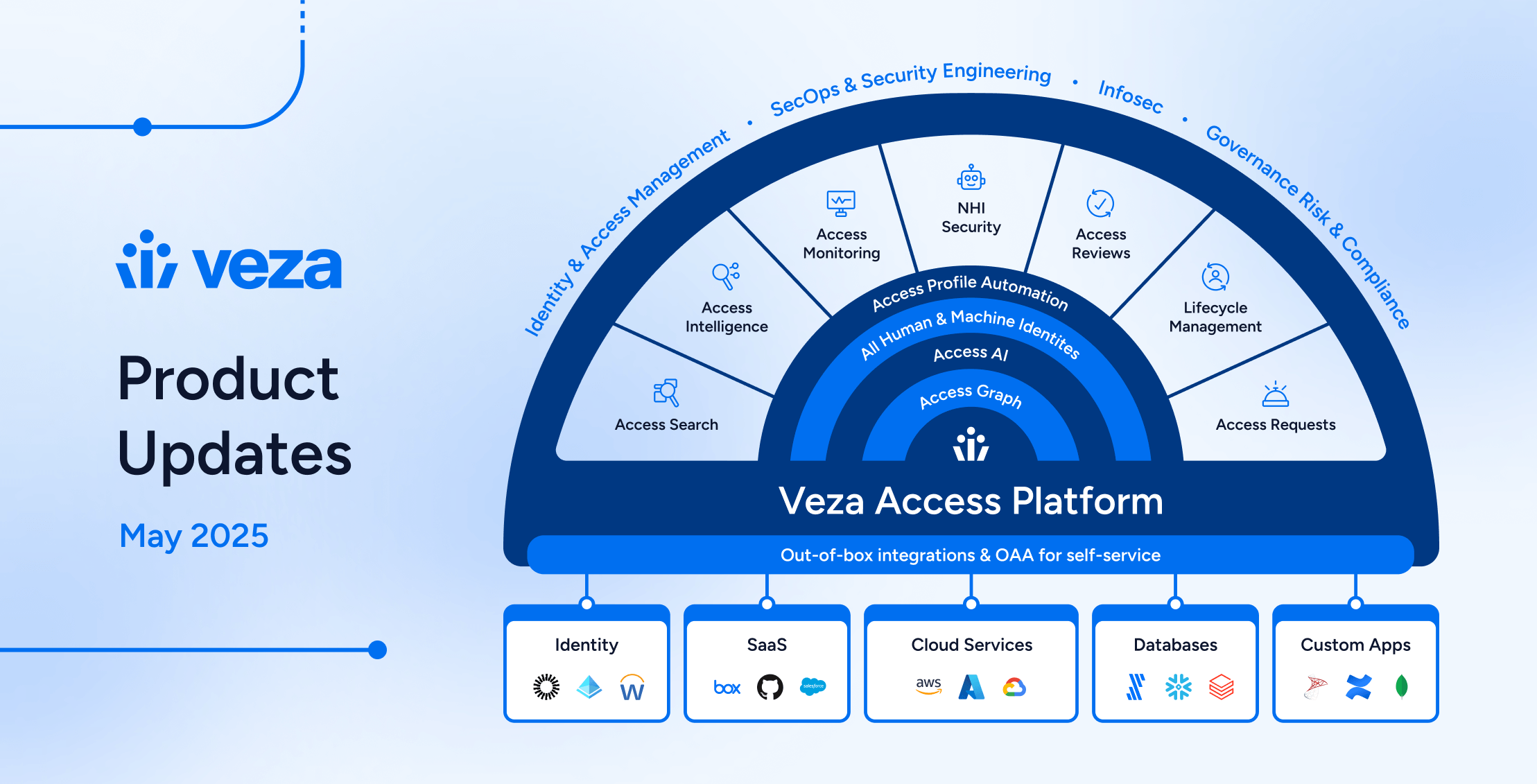
2025: The Year of Product Innovation
Learn more
-
How To Choose the Right Data Governance Tools [2025]
Learn more -
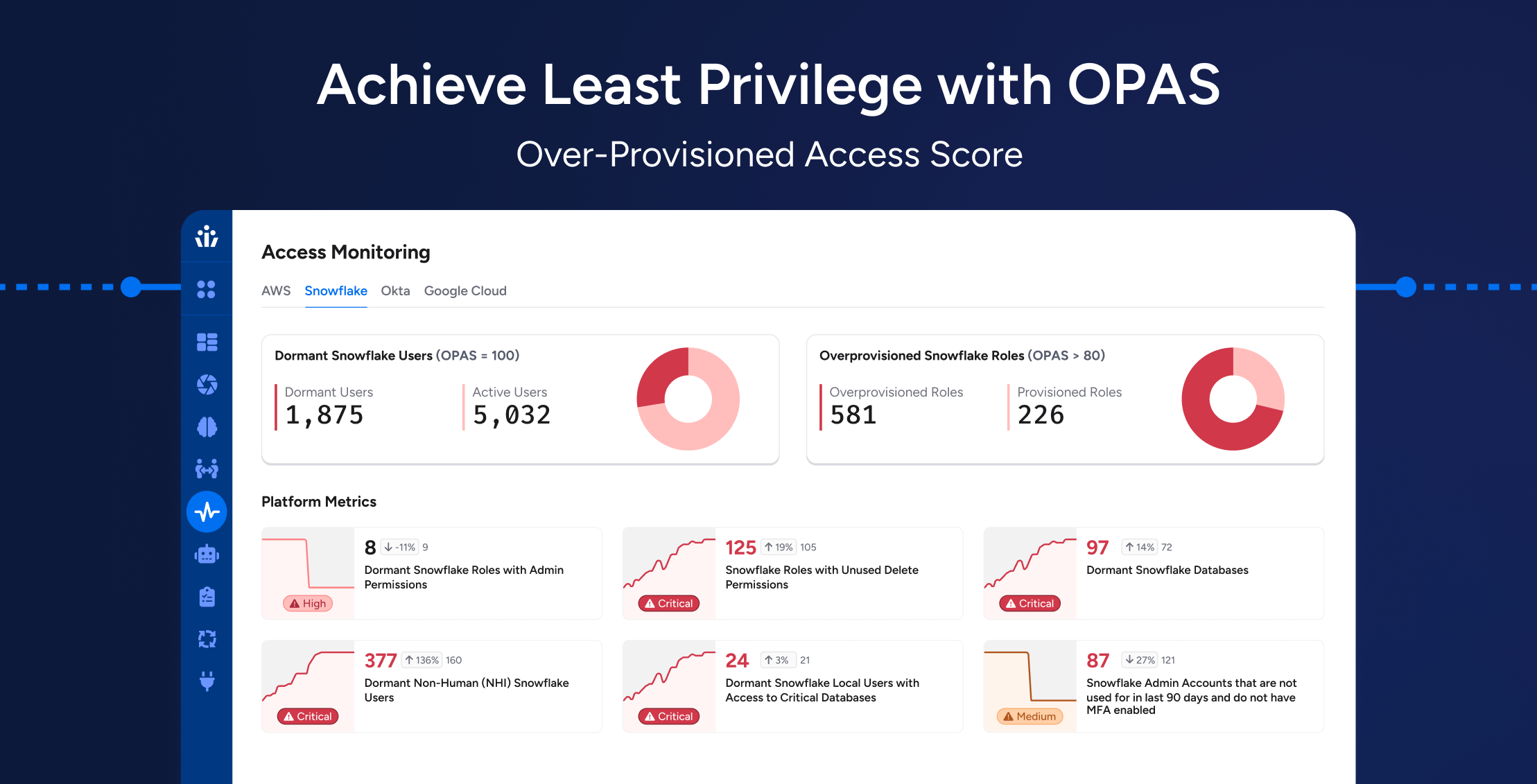
Achieving Least Privilege at Scale: How OPAS Helps Enterprises Reduce Hidden Access Risks
Learn more -
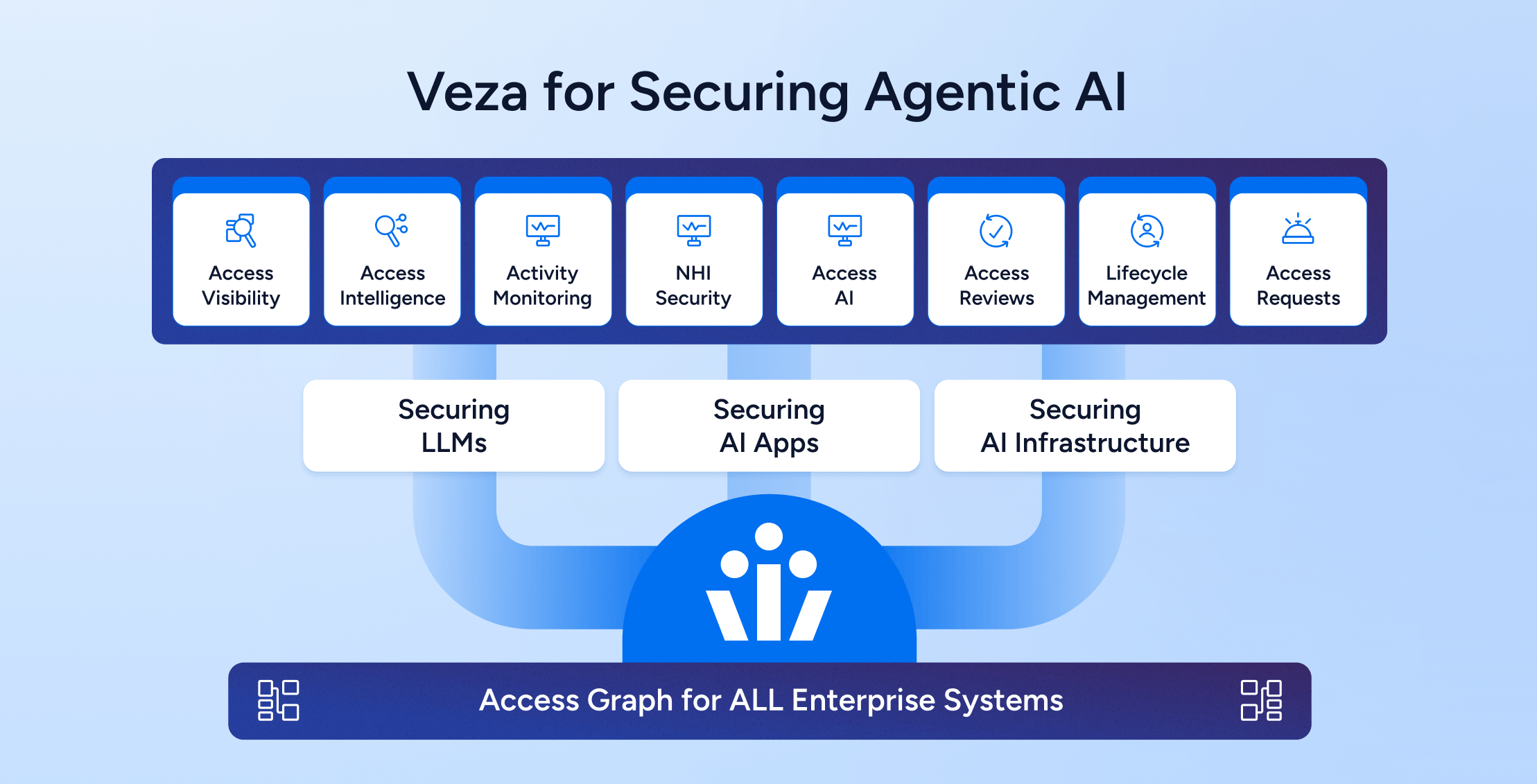
Trust as the Foundation for Agentic AI Architecture: Securing Access to all the AI layers – Models, Infra, AI Applications
Learn more -
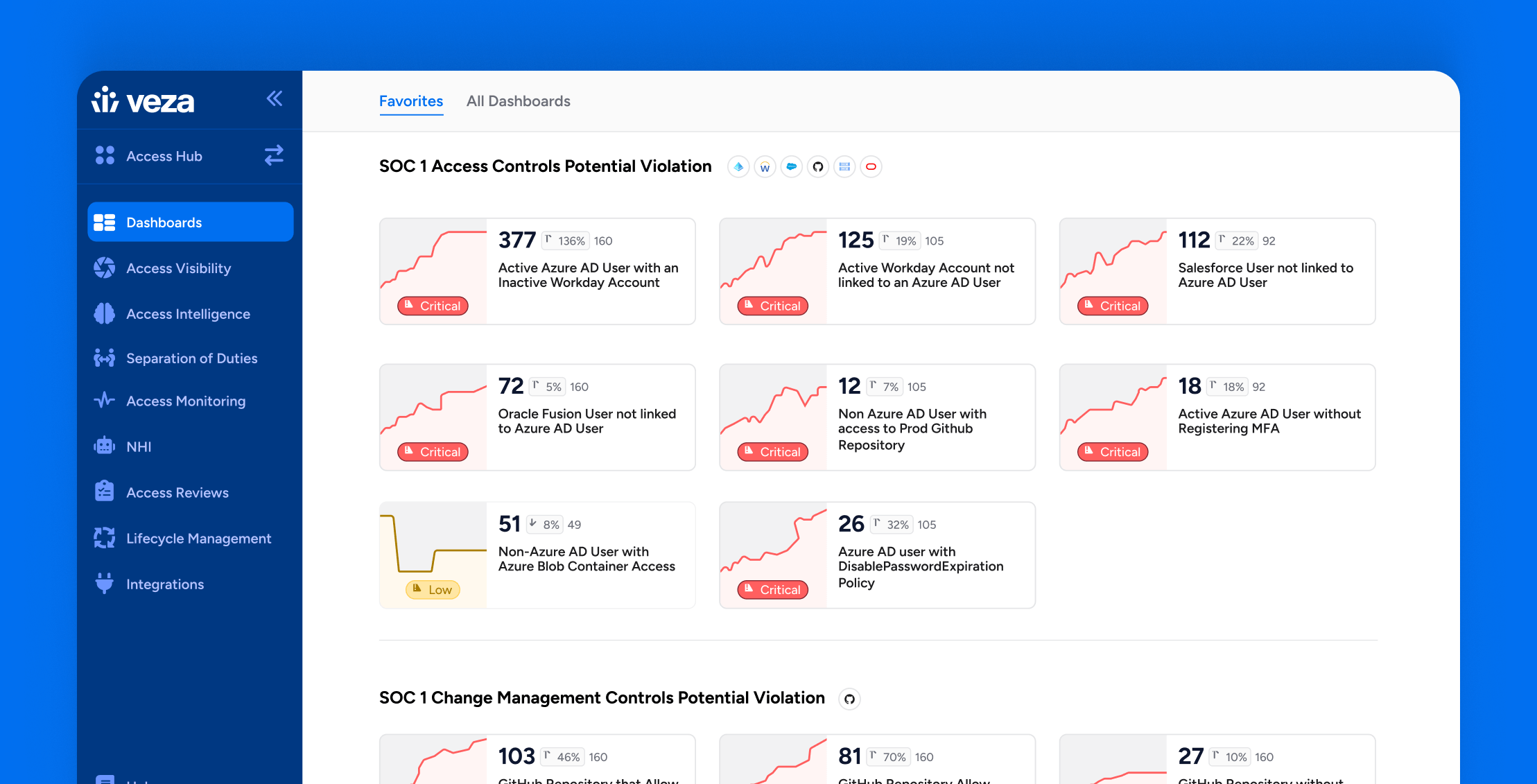
How Veza Strengthens SOC 1 Compliance: Common Control Failures & How to Fix Them
Learn more
-

The SharePoint Blind Spot: How Legacy IGA Failed to Stop Volt Typhoon
Learn more -
Overcoming Identity Silos: Toward Unified Identity Security
Learn more -
The Security Paradox of Data and Digital Transformation
Learn more -
How AI Is Reshaping Identity Security: Opportunities and New Threats
Learn more -
The Hidden Cost of Over-Provisioned Access: Identity’s Role in Cloud Optimization
Learn more -

Identity is the New Security Perimeter
Learn more
-

I Attended the Verizon Data Breach Session at RSA So You Don’t Have To:
Learn more -

Reflections from Gartner IAM London: Visibility Leads to Observability
Learn more -

Achieving DORA Compliance: A Practical Guide for Financial Organizations
Learn more -

Join us at Black Hat USA August 3 – 8, 2024
Learn more -

Join us at RSAC May 6-9, 2024
Learn more -

Veza @ AWS re:Invent
Learn more
-

10 top privileged access management (PAM) software solutions for 2025
Learn more -
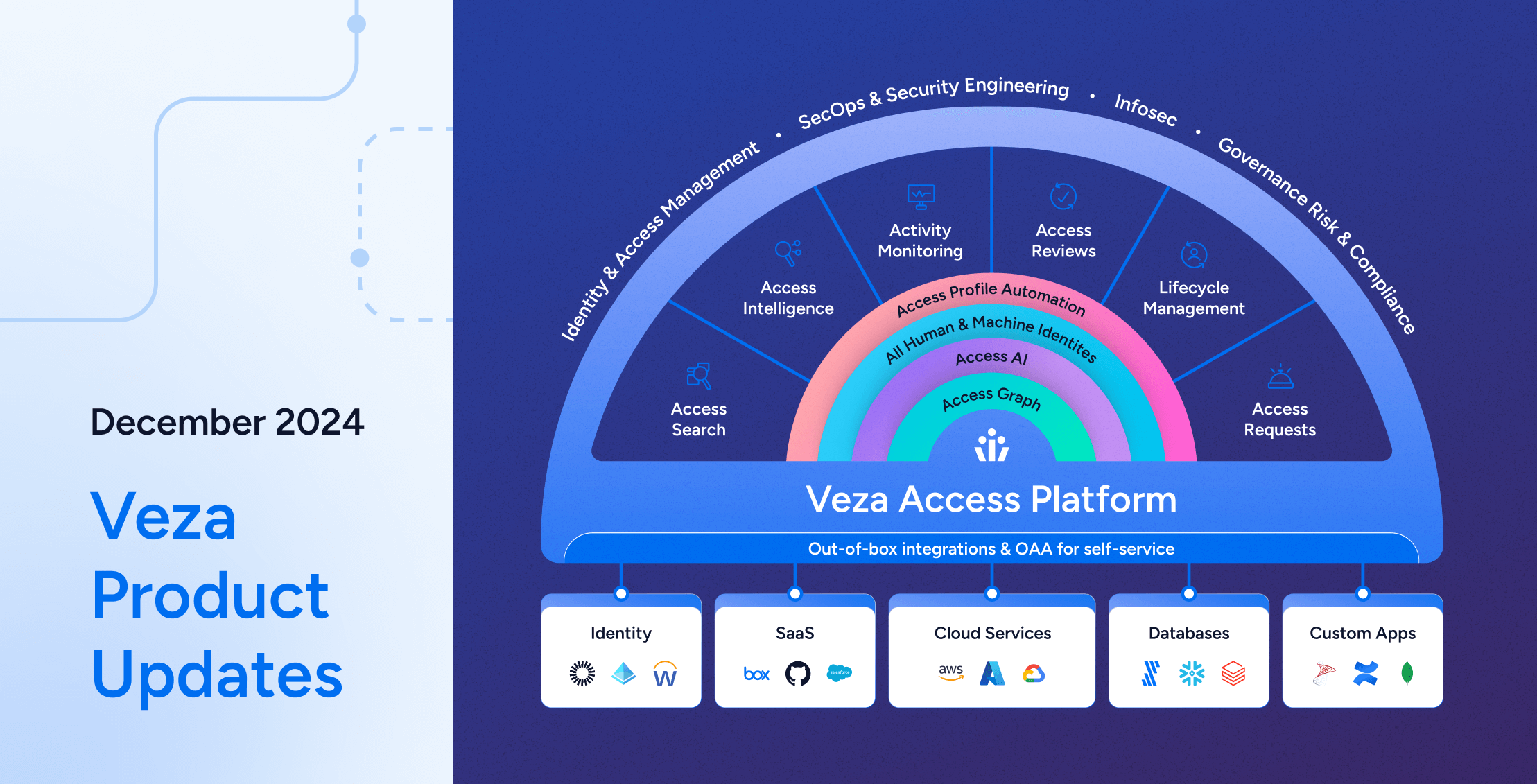
Veza Product Updates – December 2024
Learn more -

Demonstrating PCI DSS 4.0 Compliance with Veza’s Identity Security Platform
Learn more -

Complete SailPoint Review & Top Alternatives [2024]
Learn more -

Posture of Access, 3 Pillars of Least Privilege
Learn more