Blog
-
 Identity Security
Identity SecurityUnderstanding ISPM: Closing the Identity Gap with Identity Security Posture Management
ISPM is a new category of identity security designed to help organizations continuously monitor and manage identity risk across cloud, SaaS, and hybrid environments. Learn how Identity Security Posture Management works, why it matters, and how Veza enables it. -
 AI
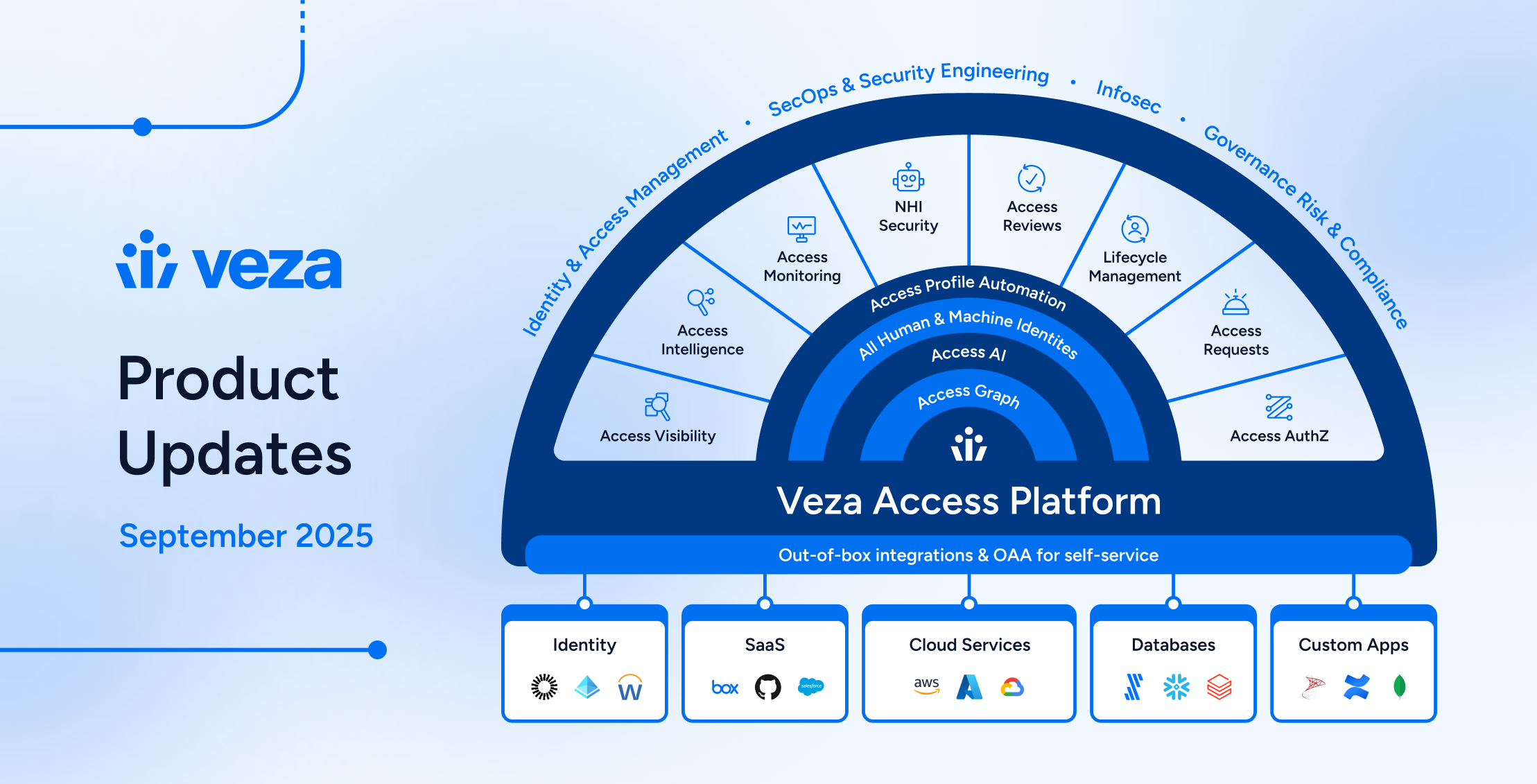
AIVeza Access AI – Applications of Gen AI for Identity Security Use Cases
Veza Access AI transforms identity security by enabling natural language queries to navigate complex access landscapes, empowering organizations to achieve least privilege effectively.
Explore our posts
-
Ransomware Isn’t Just Malware Anymore – It’s an Identity Problem
Learn more -

How to Govern OpenAI Access While Enforcing Least Privilege: Three Enterprise Perspectives
Learn more -

The SharePoint Blind Spot: How Legacy IGA Failed to Stop Volt Typhoon
Learn more -
DOJ’s Bulk Data Transfer Rule: Why Identity Visibility is Now a Compliance Requirement
Learn more -
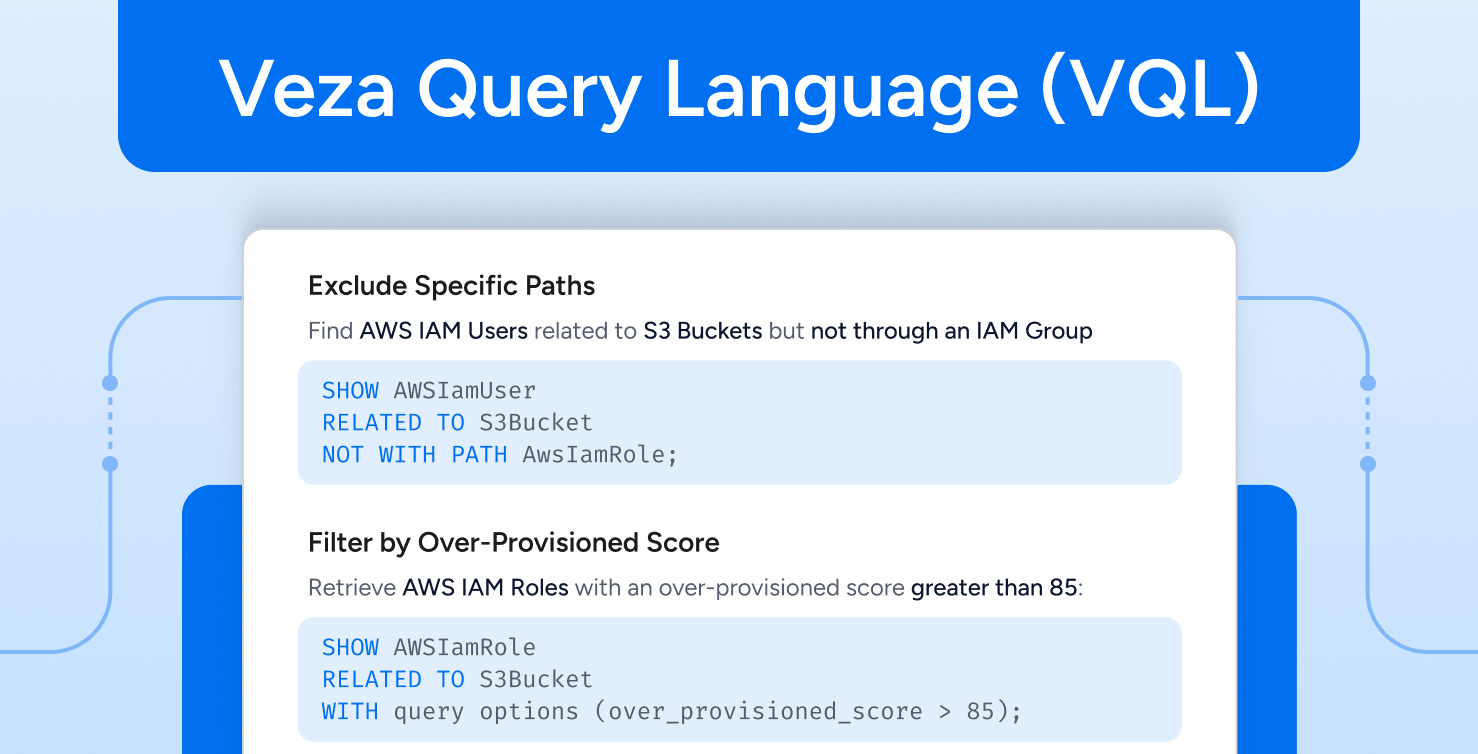
Introducing VQL – Veza Query Language
Learn more -
Overcoming Identity Silos: Toward Unified Identity Security
Learn more
-
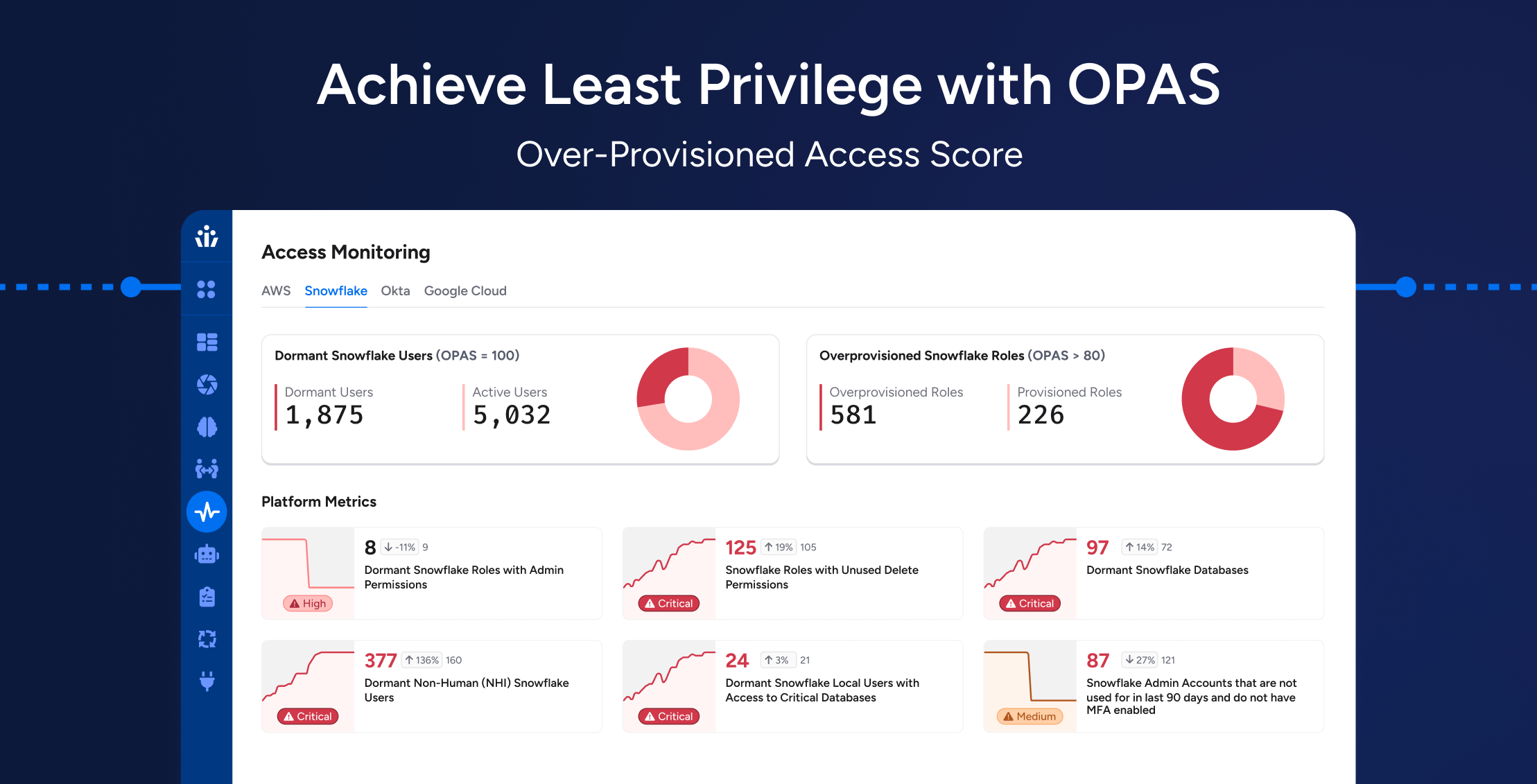
Achieving Least Privilege at Scale: How OPAS Helps Enterprises Reduce Hidden Access Risks
Learn more -
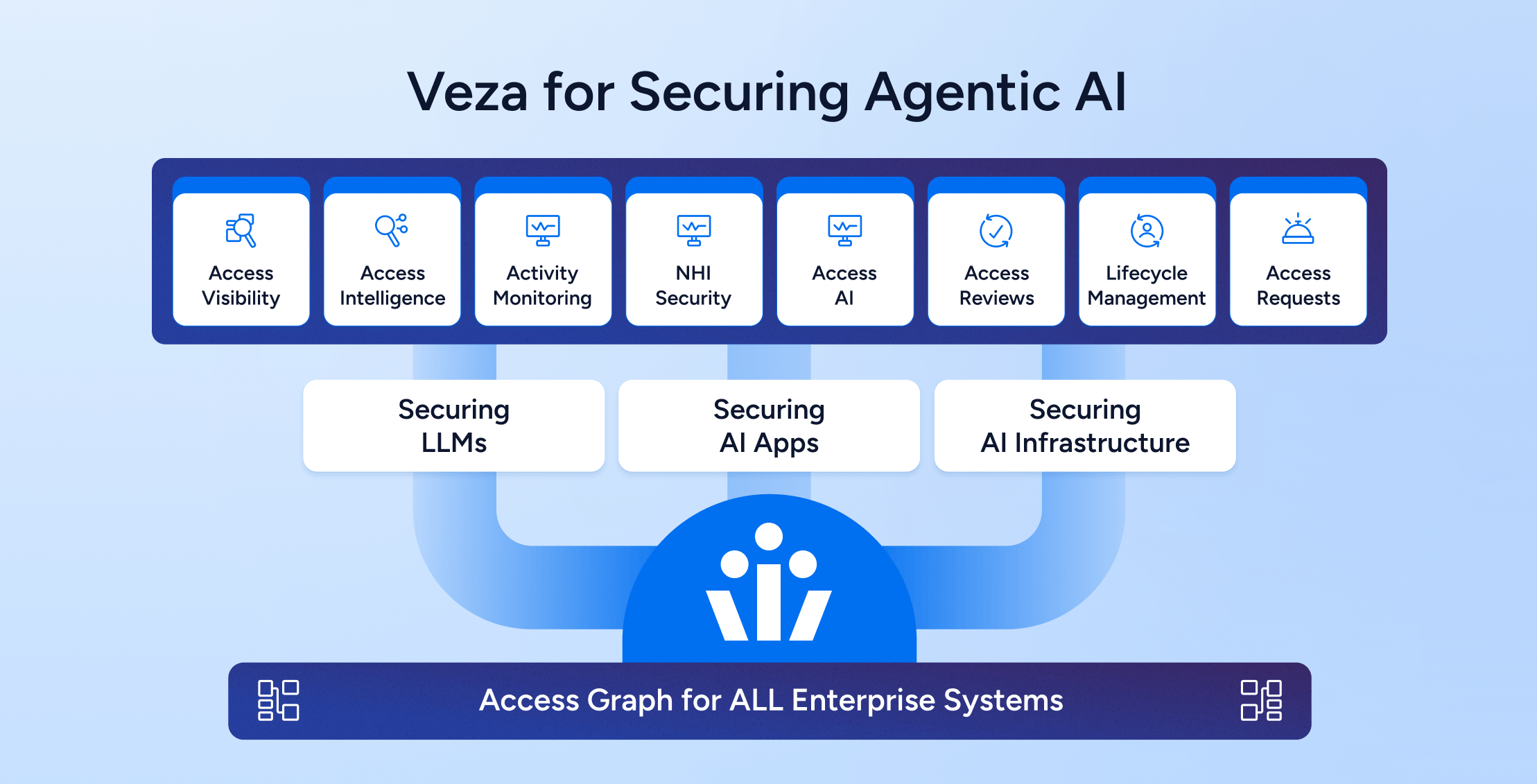
Trust as the Foundation for Agentic AI Architecture: Securing Access to all the AI layers – Models, Infra, AI Applications
Learn more -
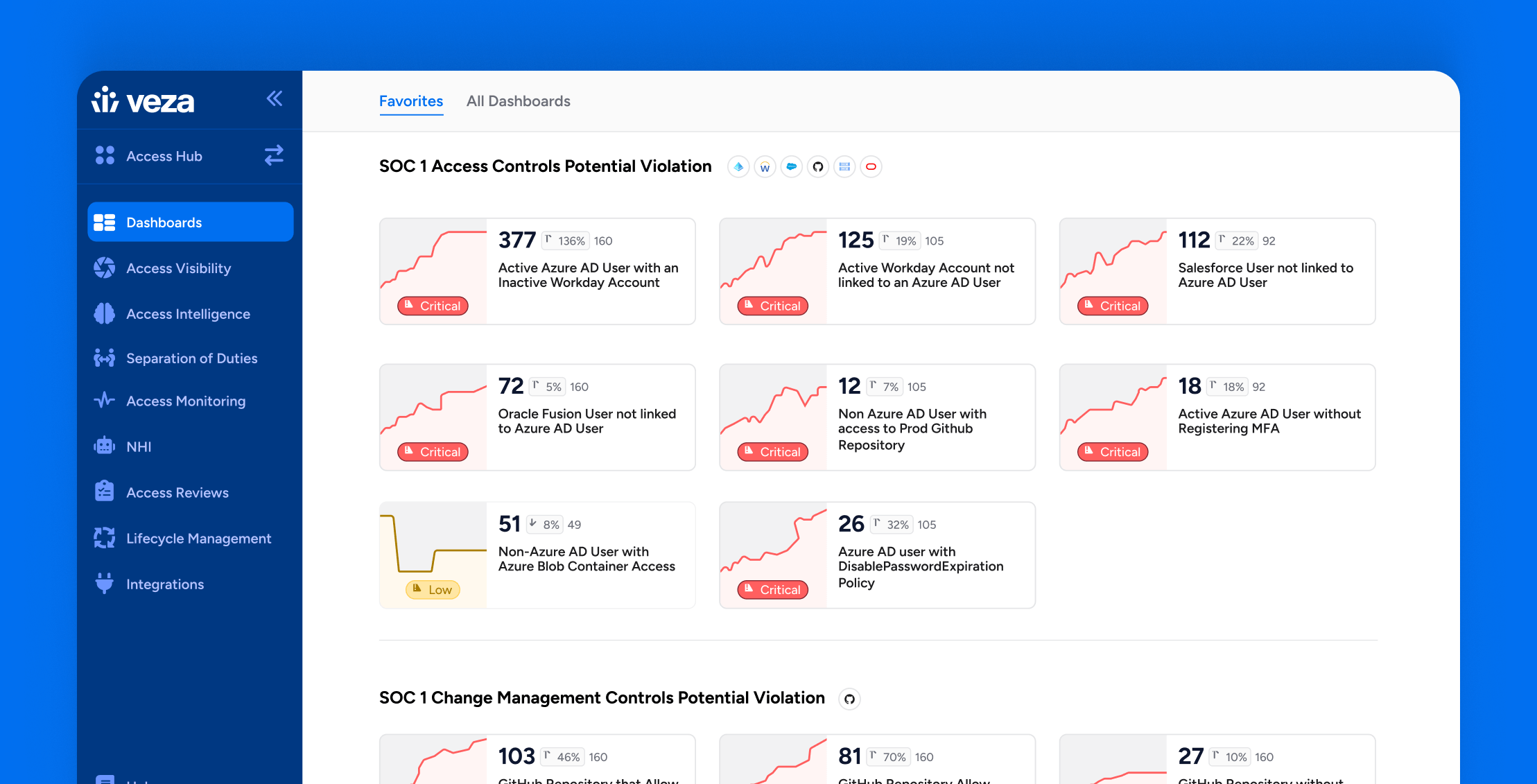
How Veza Strengthens SOC 1 Compliance: Common Control Failures & How to Fix Them
Learn more -
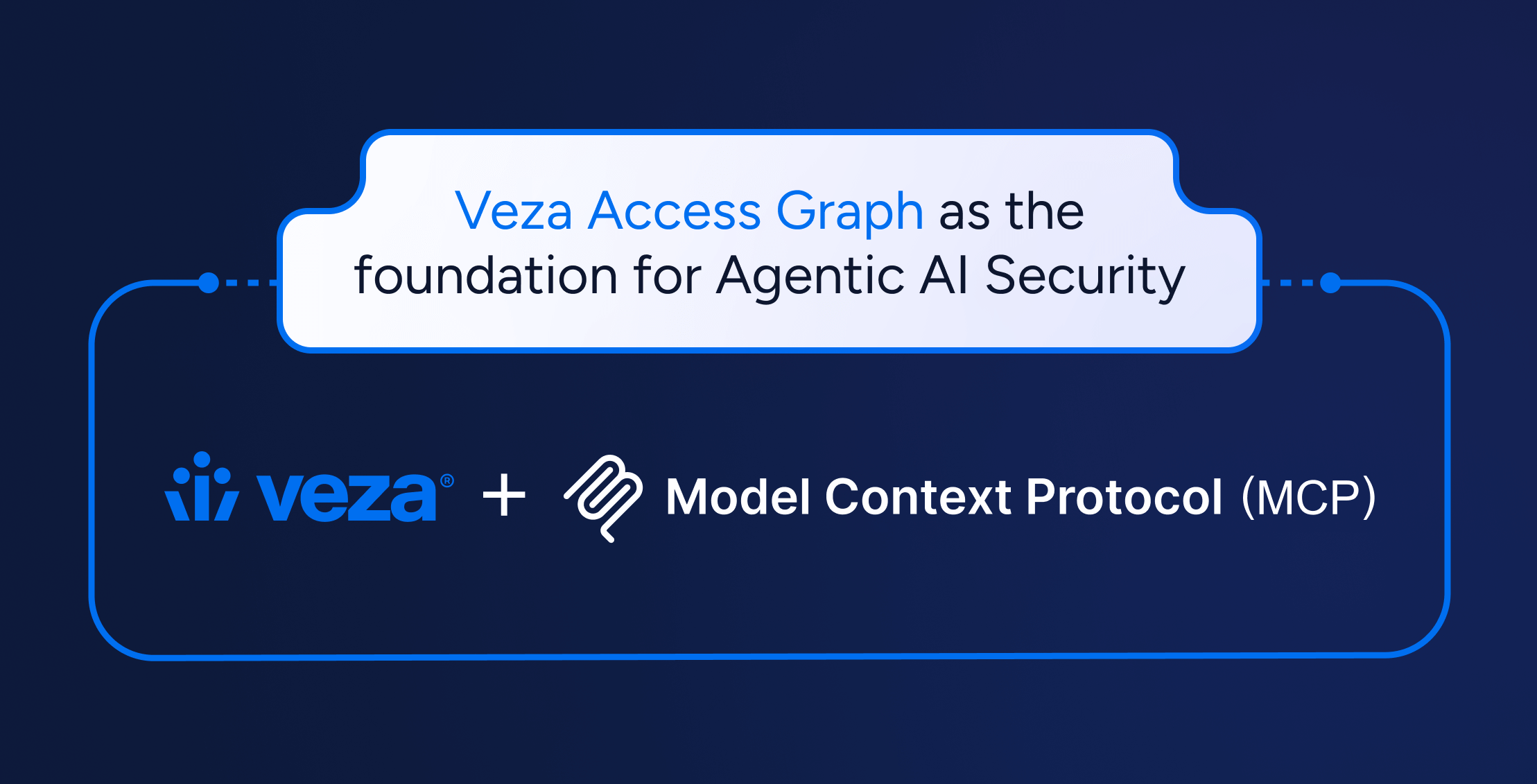
Model Context Protocol (MCP): Implications on identity security and access risks for modern AI-powered apps
Learn more
-

The SharePoint Blind Spot: How Legacy IGA Failed to Stop Volt Typhoon
Learn more -

Overcoming Identity Silos: Toward Unified Identity Security
Learn more -
The Security Paradox of Data and Digital Transformation
Learn more -
How AI Is Reshaping Identity Security: Opportunities and New Threats
Learn more -
The Hidden Cost of Over-Provisioned Access: Identity’s Role in Cloud Optimization
Learn more -

Identity is the New Security Perimeter
Learn more
-

I Attended the Verizon Data Breach Session at RSA So You Don’t Have To:
Learn more -

Reflections from Gartner IAM London: Visibility Leads to Observability
Learn more -

Achieving DORA Compliance: A Practical Guide for Financial Organizations
Learn more -

Join us at Black Hat USA August 3 – 8, 2024
Learn more -

Join us at RSAC May 6-9, 2024
Learn more -

Veza @ AWS re:Invent
Learn more