2025 was yet another exceptional year for Veza Access Platform customers with delivery of a plethora of innovative new offerings, customer-requested feature enhancements, powerful integrations, and improved ways to help our customers to achieve true “permission-level” visibility across all their applications and systems in their drive to lead their organizations to true least privilege. Here’s Veza’s 2025 round-up of major new features and capabilities across the Access Platform:
Identities for All Enterprises, Anywhere and Everywhere
1. 325+ out-of-the-box integrations: A significant expansion of Veza’s native integrations, such as AWS DocumentDB, AWS Bedrock, Google VertexAI, Splunk Enterprise, Microsoft Dynamics 365 ERP and Teams, Oracle EBS, SAP SuccessFactors, Coupa Contingent Workforce, DevRev and SharePoint On-Prem, enables faster onboarding of critical business systems without custom work.
2. Flexible integration methods for any application: Newly developed generic integration methods, including CSV upload, database, SCIM and LDAP connector, support the integration with a broad range of in-scope enterprise applications.
3. Expanded integration attributes for better visibility: Added properties and attributes for various applications to enrich identity context and surface risks, such as AWS root users, complete GCP IAM role permissions, GitHub Secrets, Snowflake Organization Accounts, and created-date and last-activity data for Salesforce objects.
4. Key cross-integration enhancements improve risk detection and remediation: Veza now supports bidirectional risk score synchronization with Crowdstrike, along with enhanced identity mapping such as AWS IAM role to local user identity, third-party IDPs to custom IDPs.
User Experience Enhancements for All
1. Access AI-Powered Queries and Review Explanation: Use natural language to create queries, explain access reviews, and provide decision-making context for individual review line items.
2. Universal Search: Discover Dashboards, Queries, and more across Veza and its products using a simple “Command-k” keystroke.
3. Improved Global Navigation: We made it easier to find Products, Features, Insights and Risks with fewer clicks through continued navigation updates.
4. Standard UI Components: We launched our new Design System, introducing common UI components across Veza’s products and improving usability for our customers.
Identity Governance with Access Graph
1. Introduced Access AuthZ to automate the “last mile” of identity governance: Intended for legacy IGA, ITSM, and custom applications, Access AuthZ extends automated access provisioning/deprovisioning across legacy, on-premises, cloud/SaaS, and custom-developed applications using SCIM v2 as well as Veza and customer-developed integrations providing one unified model integrated with Veza’s Access Graph.
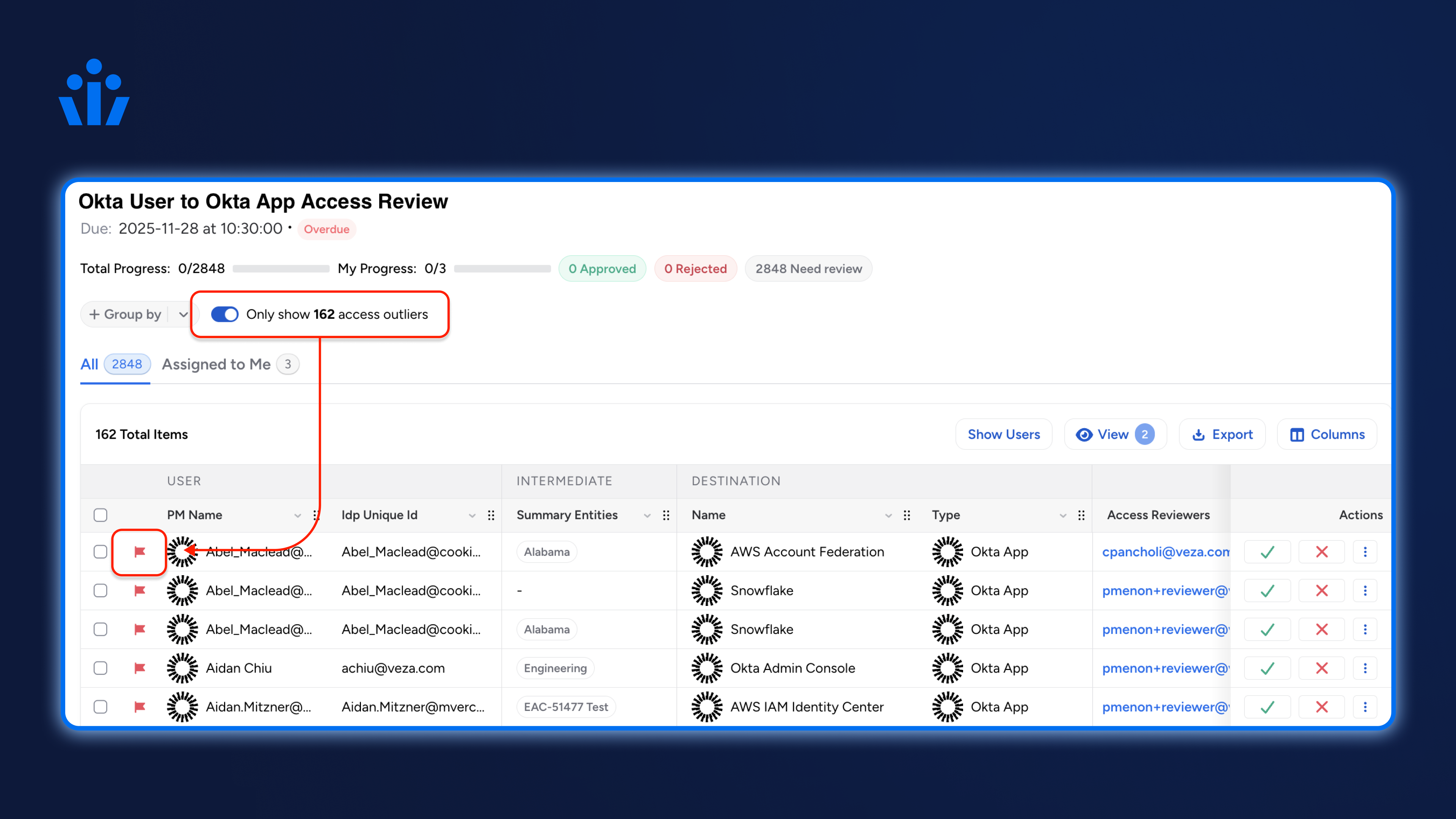
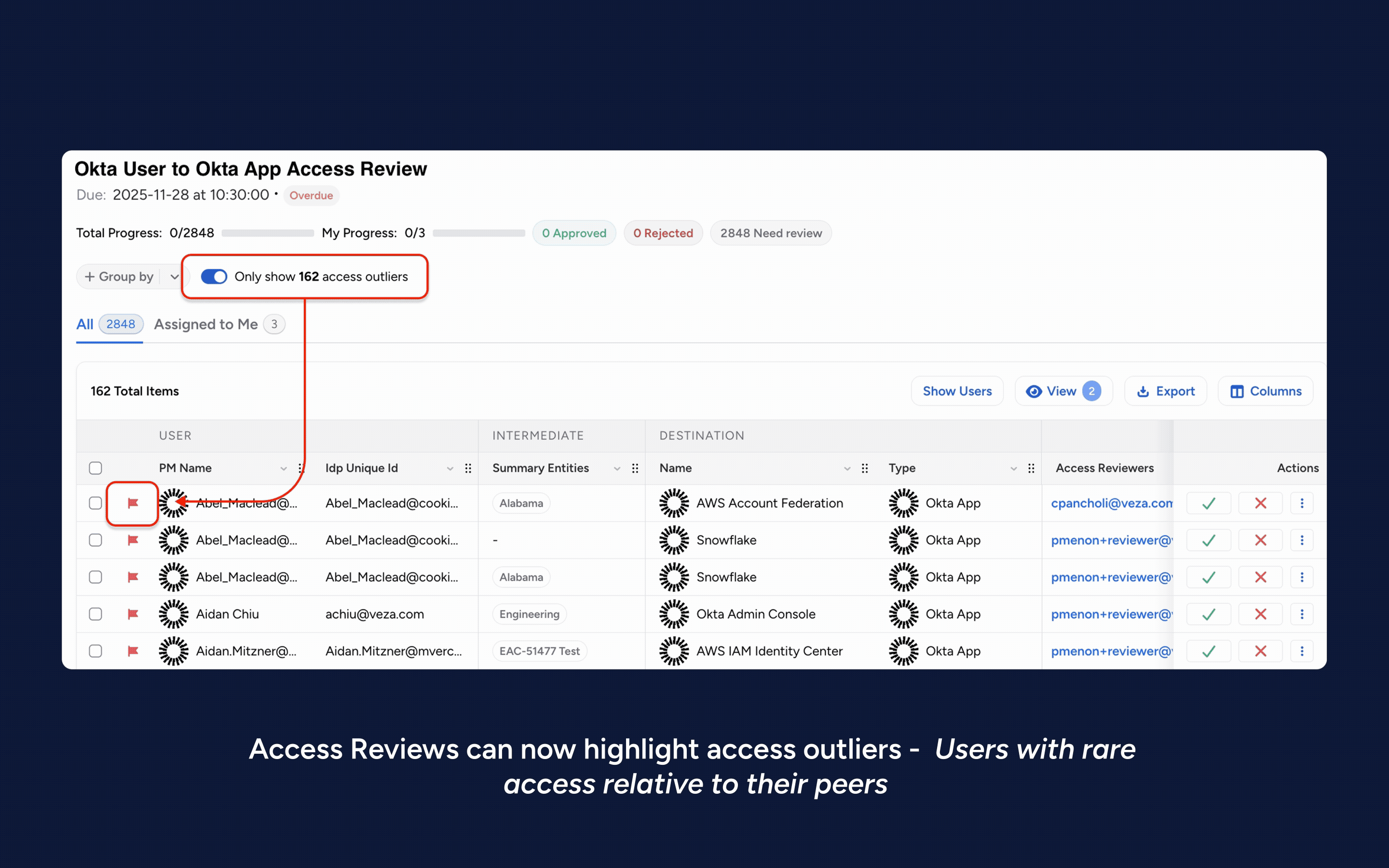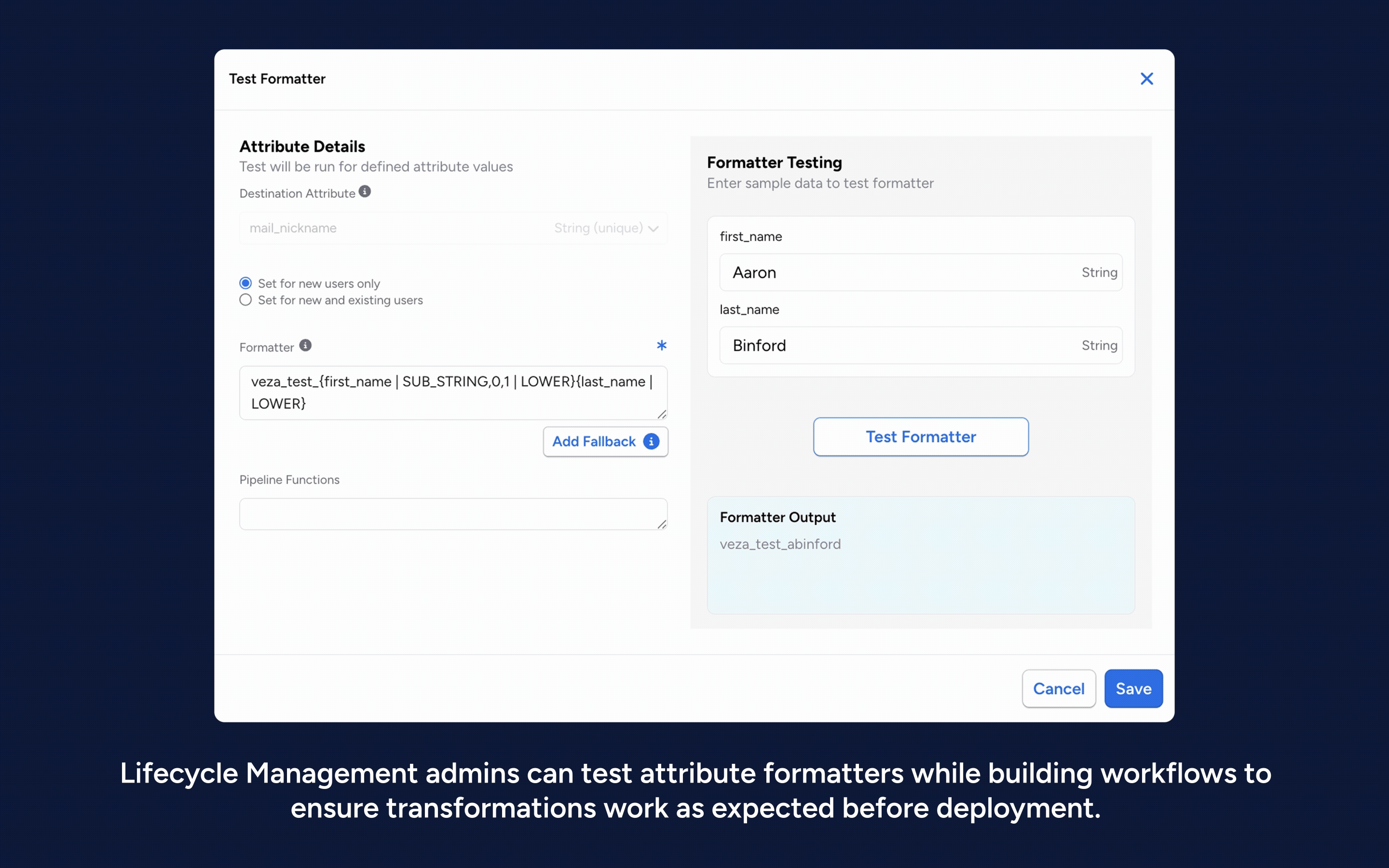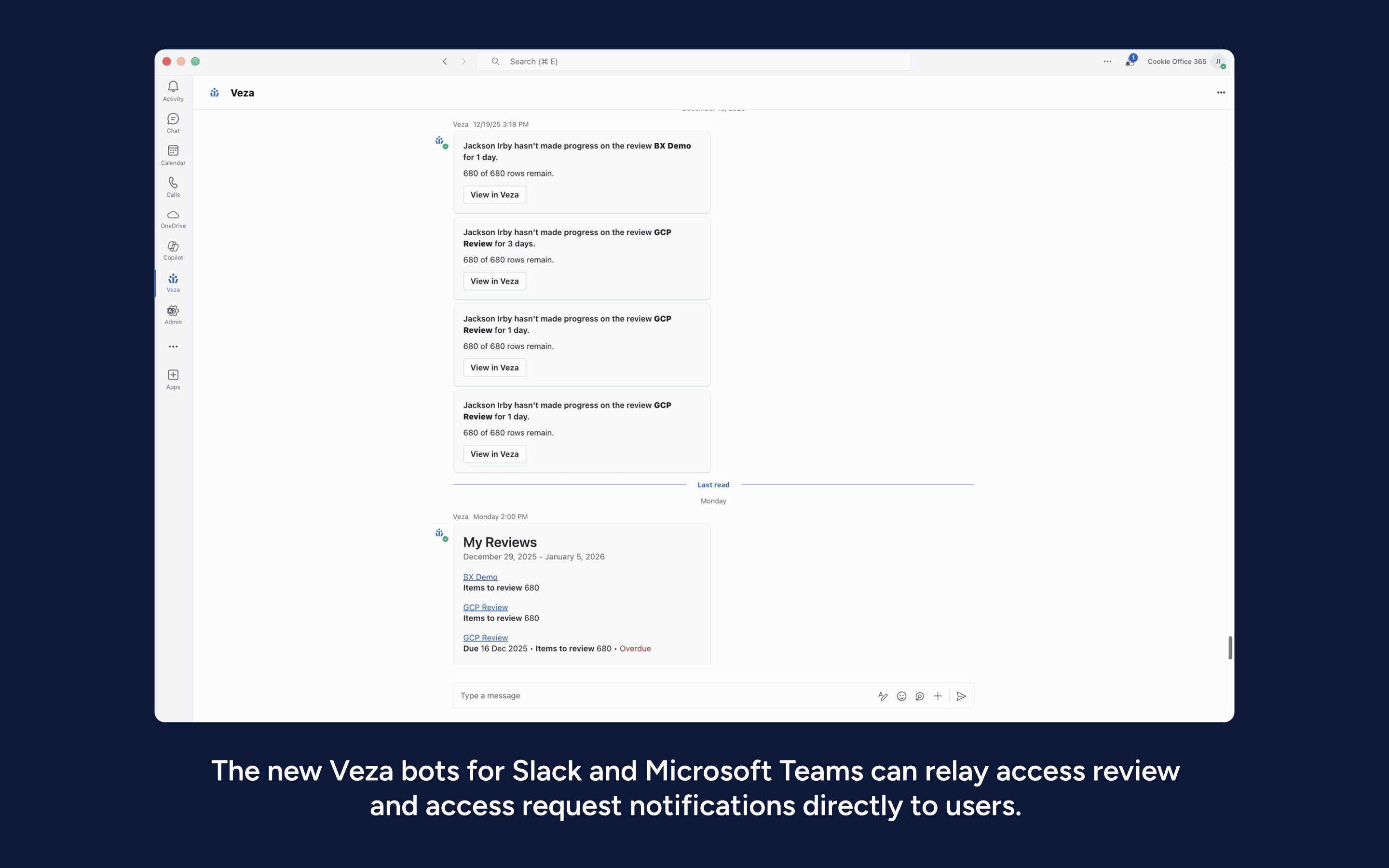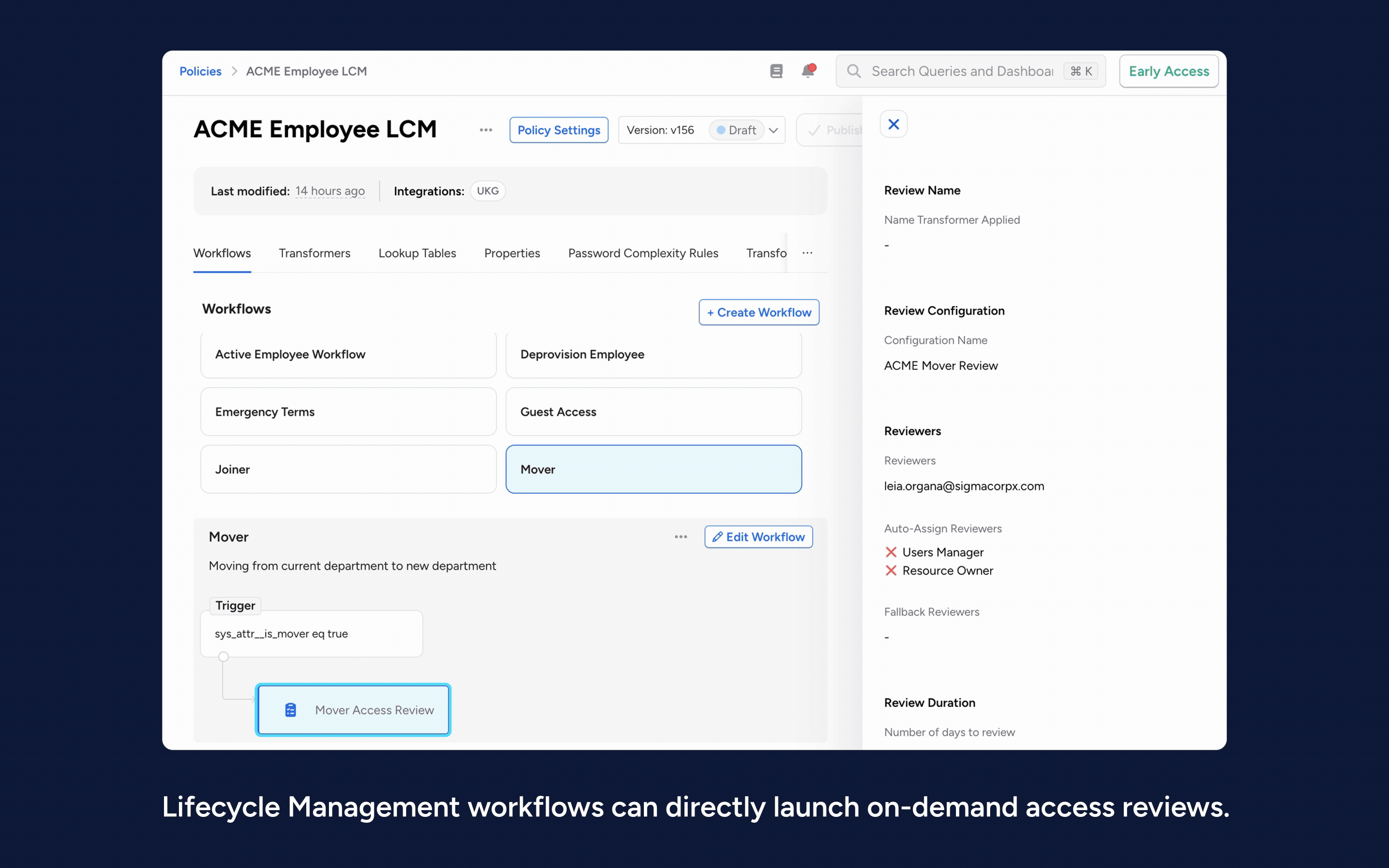
2. Major risk-based review improvements: Now includes support for Veza’s new Risk Score 2.0 algorithm, drillable risk scores within access reviews allowing reviewers to see contributing access risk factors, and access outlier detection based on peer group analysis.
3. Auto-revocation of rejected access built into Access Reviews Advanced: Ability to automatically revoke rejected access in a review is now a built-in feature of Access Reviews Advanced.
4. Built-in revocation verification: Upon review completion, Access Reviews continuously checks the Access Graph to confirm that access associated with rejected line items have indeed been revoked—and automatically marks those items as “Fixed” when access revocation is detected.
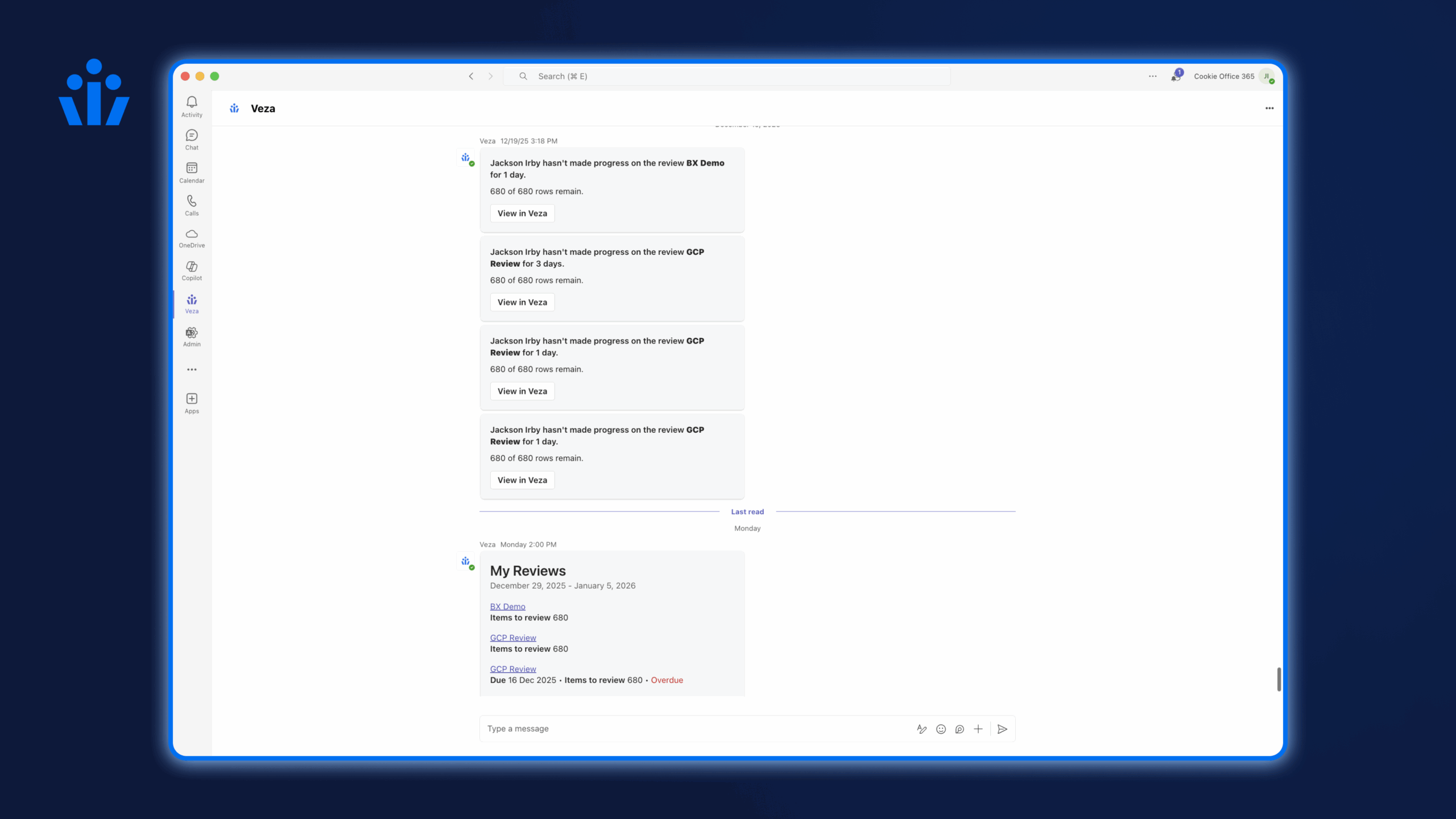
5. Slack-and Microsoft Teams-based notifications and alerts for Access Reviews and Access Requests: Two new Veza bots now integrate natively with Slack and Microsoft Teams allowing notifications and alerts related to pending access reviews and access requests to be sent directly to users on these modern messaging platforms; augments existing email notification capabilities.
6. Consolidated reporting and enhanced Excel-based reporting for access reviews: New Excel format reporting for Access Reviews provides rich, insightful metrics per review or per campaign; reports are generated quickly and effortlessly and are ready for both auditors and senior management; new export API supports programmatic access review exports and reports.
7. Broad application provisioning/deprovisioning support for both birthright and just-in-time access: OAA Write “Framework” and custom REST API actions further extends Veza’s universe of supported applications for provisioning/deprovisioning to custom, homegrown, and legacy applications; augments existing support for thousands of standards-based SCIM-enabled applications and native support for market-leading enterprise applications and platforms.
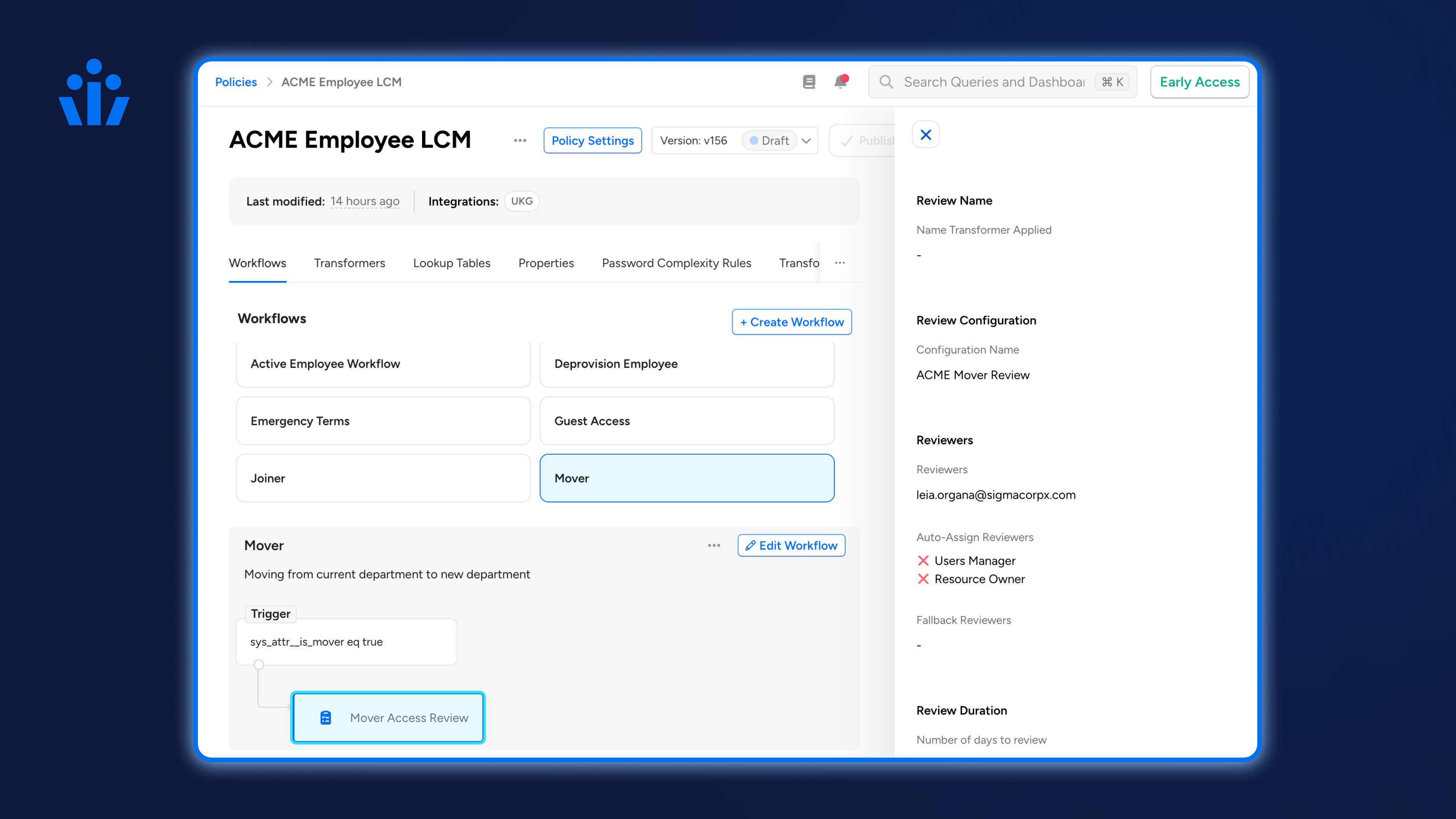
8. Ability to launch on-demand access reviews as part of Lifecycle Management workflows or ad-hoc from Access Intelligence, Separation of Duties, and NHI Security: Admins of these products can launch of user access reviews targeted on joiners, movers, or leavers (Lifecycle Management), risky and/or highly privileged entities (Access Intelligence and NHI Security), or users violating SoD policies (Separation of Duties).
9. Usability enhancements to Lifecycle Management policy and workflow management: Improvements include enhanced autocomplete functionality, ability to pause workflows and actions, and an easier drag-and-drop workflow builder
10. Configurable password complexity settings in Lifecycle Management: Ability to enforce complexity policies for system-generated passwords for Active Directory
11. Custom email notification templates for Lifecycle Management: Allows Lifecycle Management notifications to incorporate company branding and configurable messaging, such messages sent to new hires
12. Dynamic Access Profile assignments: Allows flexible RBAC/ABAC rule setting for assigning application entitlements
13. Advanced deployment guardrails for Lifecycle Management & Access Requests:
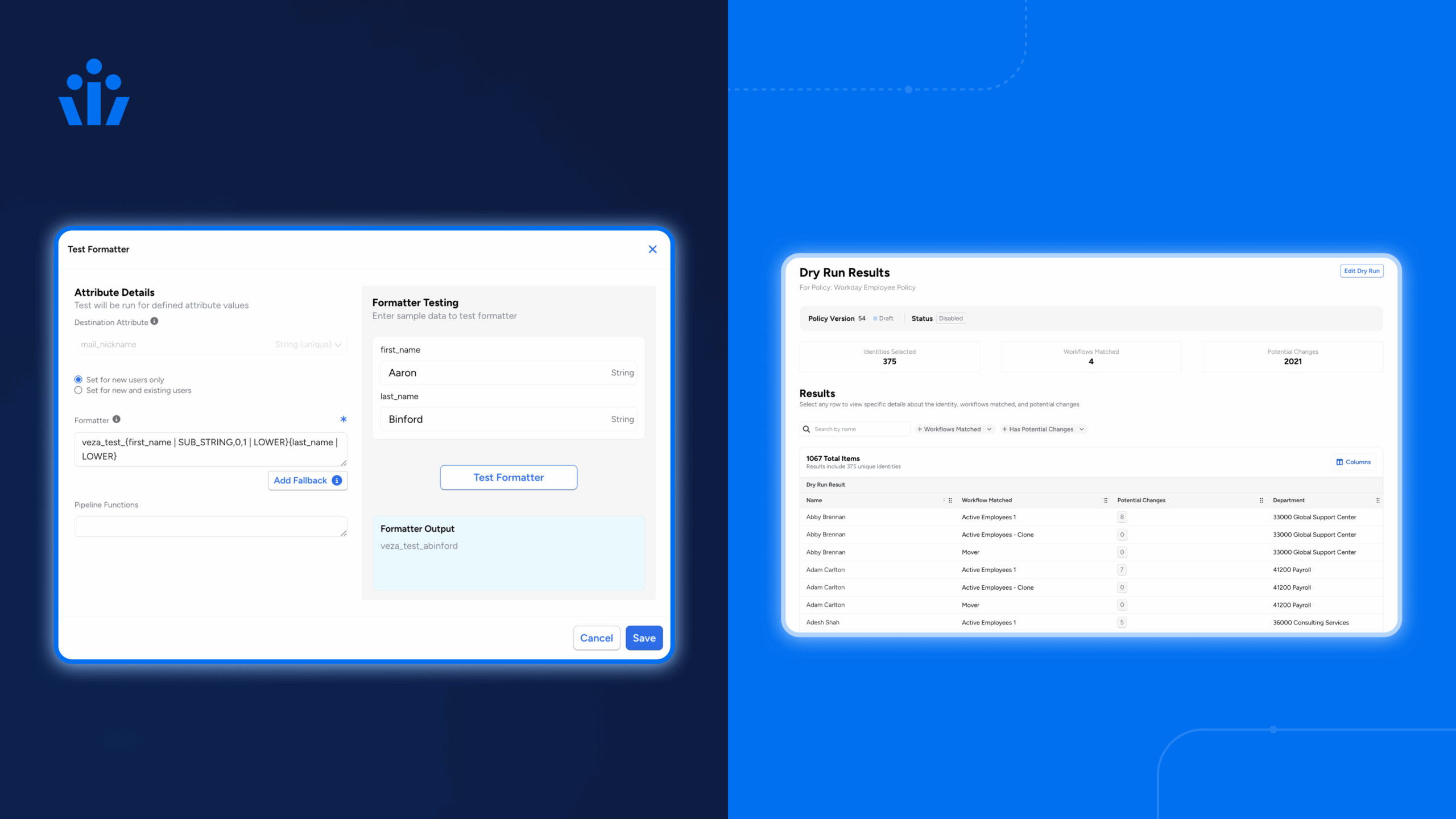
- Enhanced dry run to allow admins to see what happens all or a select group of users are simultaneously “run” through joiner, mover, and leaver workflows.
- Configurable “safety limits” that govern the maximum number of users operations allowed to ensure unexpected or erroneous HR system updates don’t trigger undesired downstream user account changes.
- In-line testing for data transformers to accelerate workflow build-out and prevent unintended changes to target applications.
- Versioning & rollback – Versioning and rollback of Lifecycle Management policies and Access Profiles ensures that any changes can be traced and, if necessary, rolled back to the last known working version.
14. Just-in-Time (JIT) access policies: Individual access requests can be governed by JIT policies that dictate the appropriate duration of access to be granted, time-to-live for individual access requests, approval workflows (with support for multiple levels of approval), and exception rules for non-responsive or inactive approvers.
15. Cross-application SoD violation detection (now with support for NHIs and AI agents): Beyond human users, admins can now identify NHIs and AI agents assigned conflicting roles and permissions across disparate applications that violate SoD policies.
Automation for Operationalization
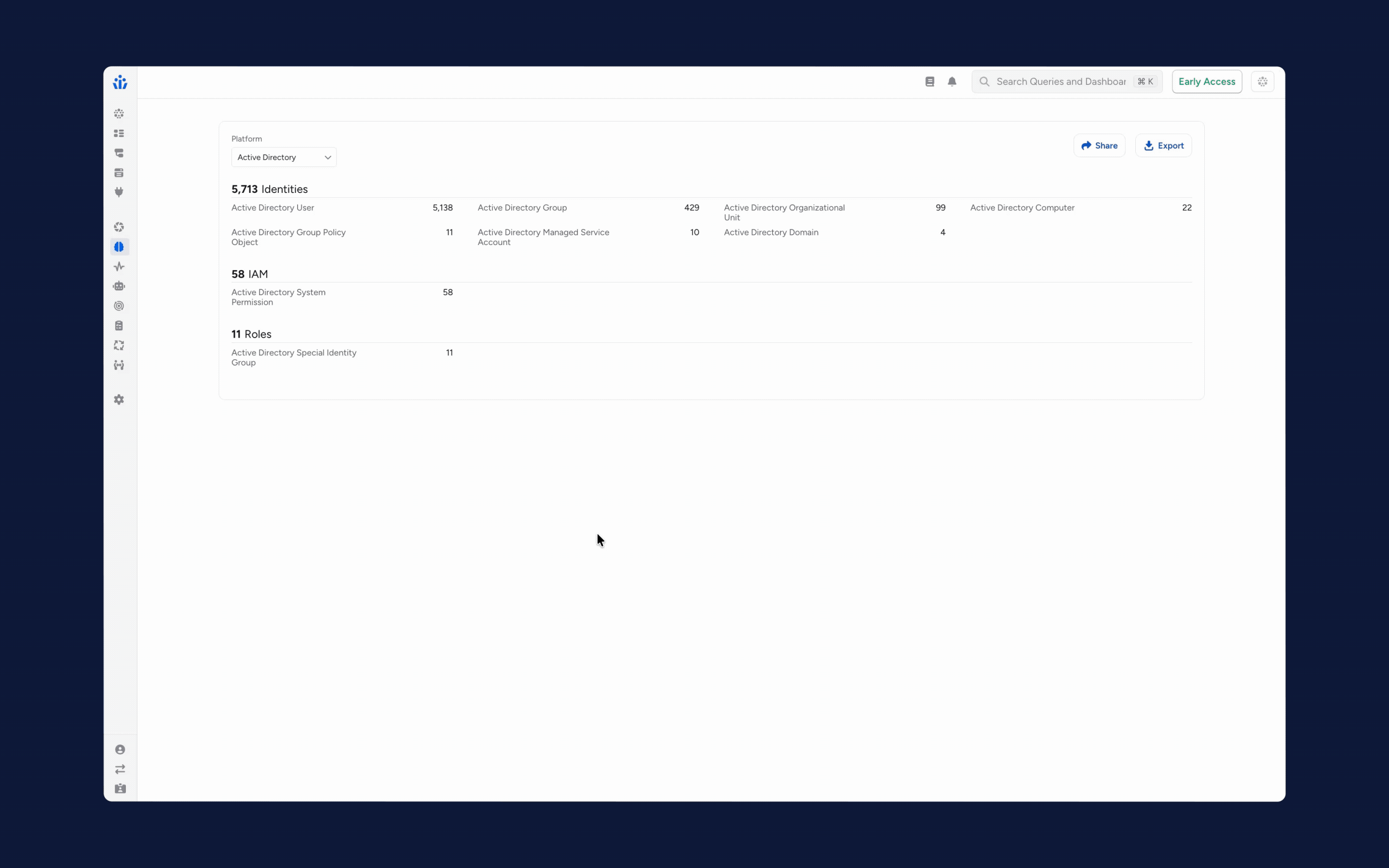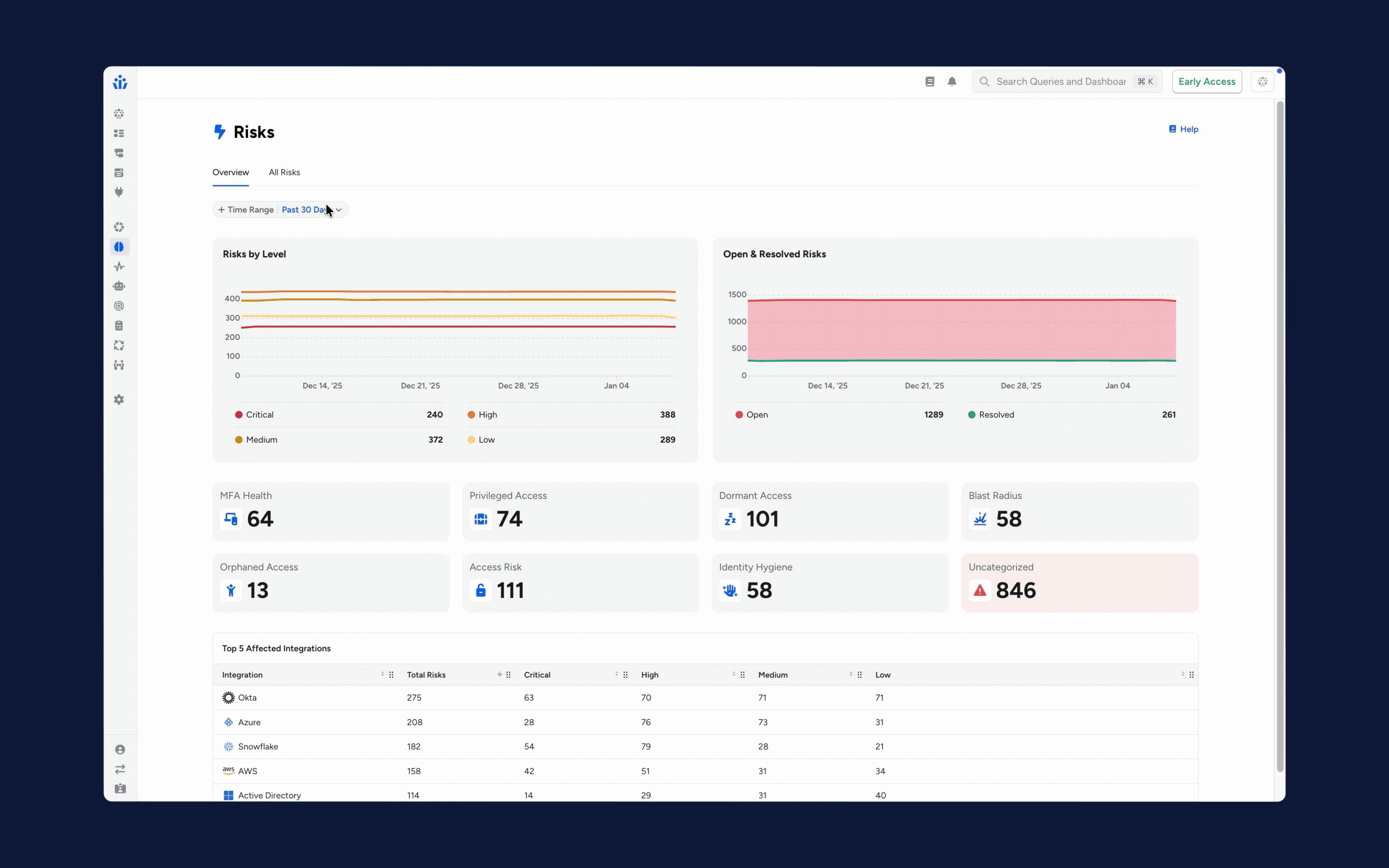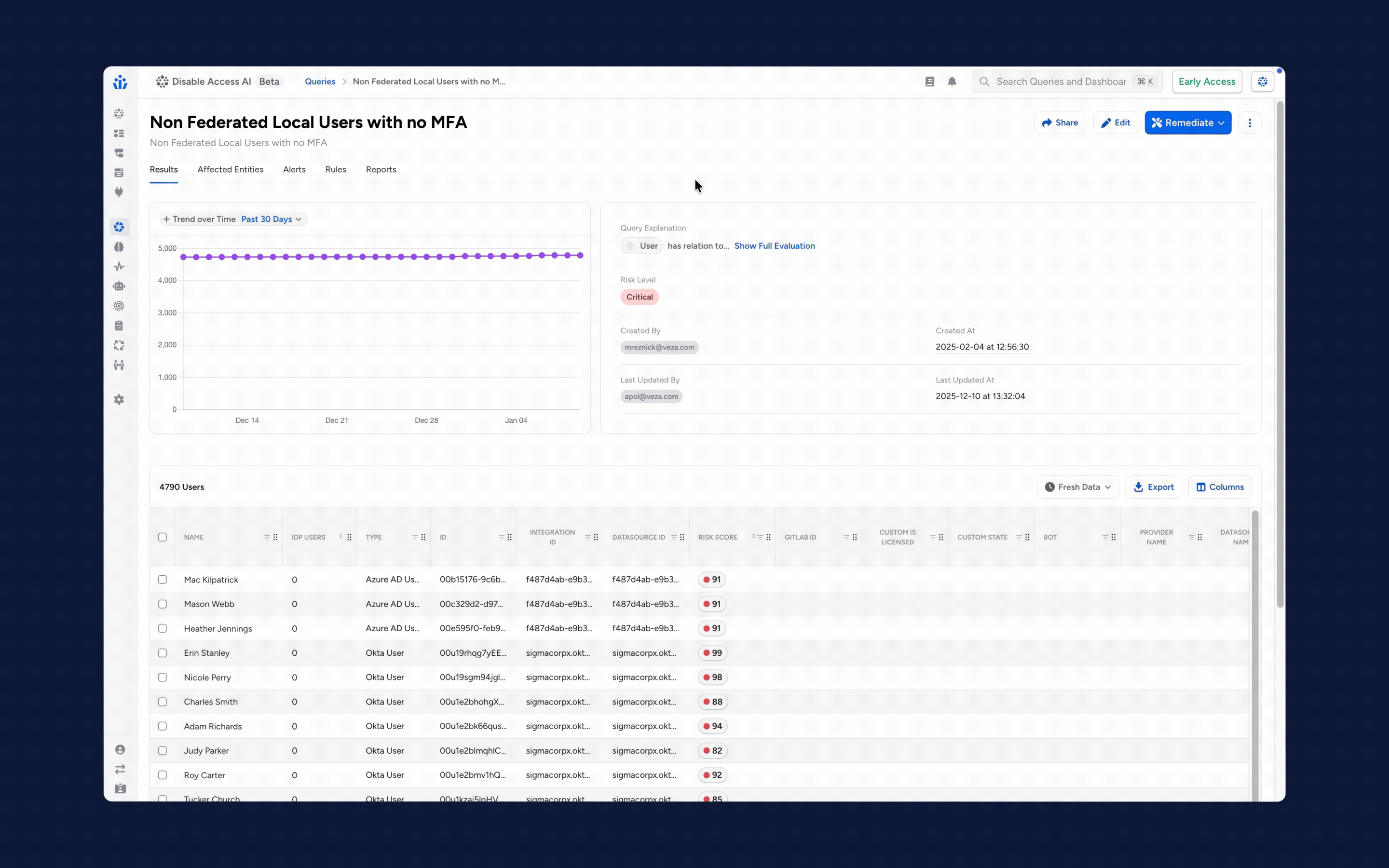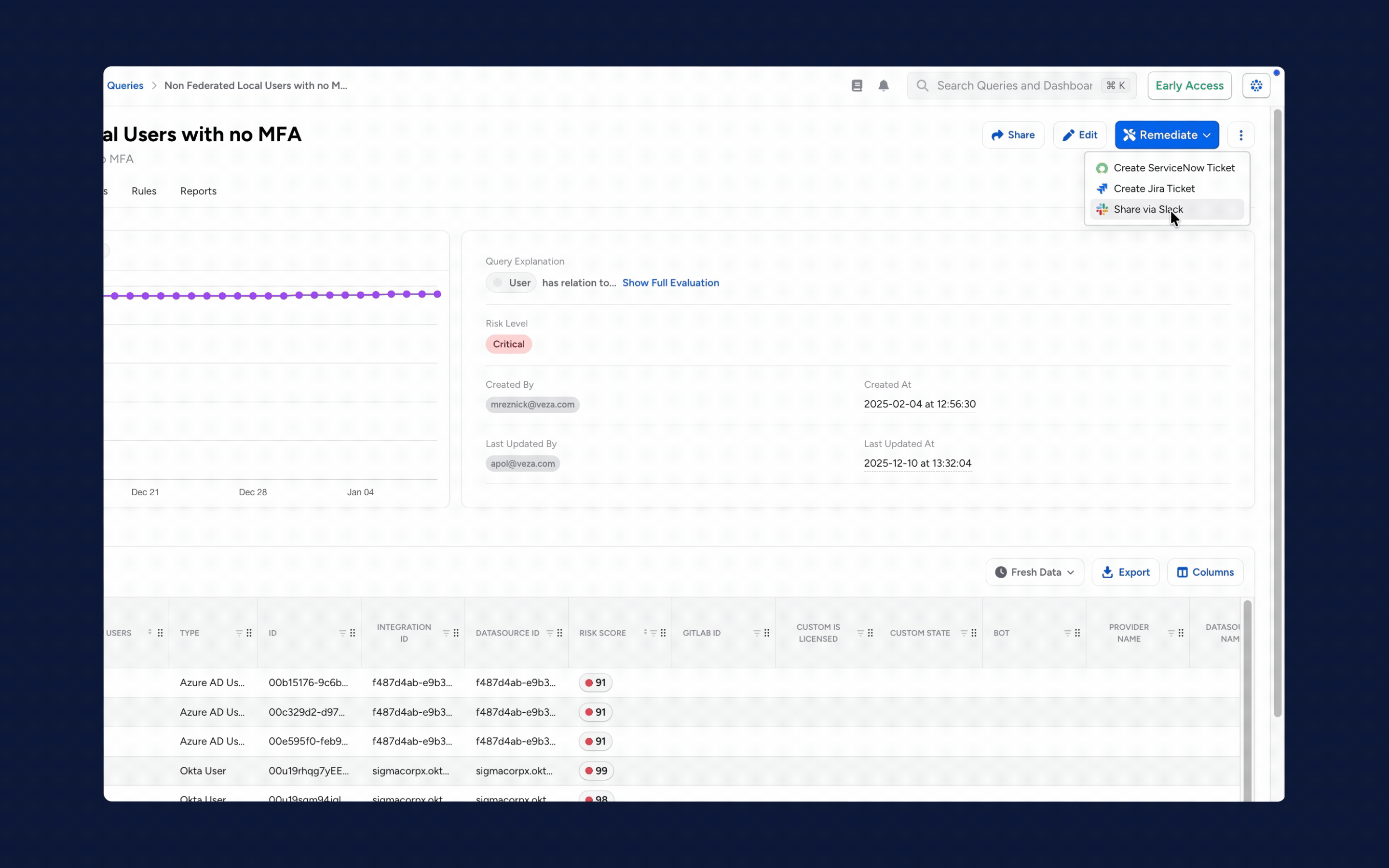
1. From Risk Visibility to Immediate Resolution: We’ve updated our risk engine with smarter scoring and risk profiles to help you find, prioritize and categorize findings. The redesigned Risks page makes it easy to see these findings at a glance, organized by level or status. You can now go beyond visibility and take action by opening Jira or ServiceNow tickets and alerting your team via Slack or email.
2. Fast, accurate access using intelligent role engineering: Leverage your existing user, application, and entitlement data in the Access Graph to automatically generate roles and define birthright access. This ensures the principle of least privilege access is enforced by design, which minimizes access drift and enhances overall security posture.
3. Activity Monitoring for BigQuery and Azure: Veza added activity monitoring for Google BigQuery and Azure services, including Service Principals and Keys. You can now see exactly how permissions are being used to help you spot and fix over-privileged accounts. It’s a simple way to make sure everyone has just the right amount of access they need and nothing more.
Next-generation Identity Access for NHI & AI Governance
In 2025, Veza redefined the boundaries of identity security by launching purpose-built solutions for the fastest-growing risks in the enterprise: Non-Human Identities (NHI) and autonomous AI Agents. By unifying these under our Access Graph, we moved beyond basic labeling into a complete governance framework for the AI era.
Discovery & Integration
1. Unified NHI & AI Agent Inventory: Launched two new product modules providing a centralized management interface for all machine identities (AWS, Azure, GCP, Entra ID, Okta, Salesforce, HashiCorp) and autonomous AI agents.
2. Multi-Platform Agent Discovery: Integrated deep visibility for agents and bots across major AI ecosystems including Microsoft Copilot, Salesforce Agentforce, AWS Bedrock, and Google Vertex AI.
3. Public MCP Server Discovery: Added the ability to surface which public Model Context Protocol (MCP) servers (such as Google Search or GitHub) are being accessed by agents, exposing potential data leak paths.
4. Automated Identity Classification: Enhanced logic to automatically identify and classify “Non-Human” identities and AI agents based on metadata.
5. Cloud Secrets & Keys Deep-Dive: Expanded discovery for GitHub Secrets and provided deeper metadata insights for AWS KMS Keys, including key origin and rotation status.
Visibility
1. AI Blast Radius Visualization: Leveraged the Access Graph to provide detailed views of exactly what sensitive databases and files an AI agent or NHI can access, including the foundation models they are utilizing.
2. Cross-Organization Impersonation (GCP): Enhanced visibility into Google Cloud to track machine accounts impersonating identities across different organizational boundaries.
3. NHI Risk Dashboards: Pre-built, customizable dashboards that highlight critical risks like dormant keys, unrotated secrets, and overly permissive service accounts.
4. OWASP for LLM Compliance: Pre-built reporting aligned with the OWASP Top 10 for LLMs to satisfy AI safety audits and regulatory requirements.
Operationalization & Action
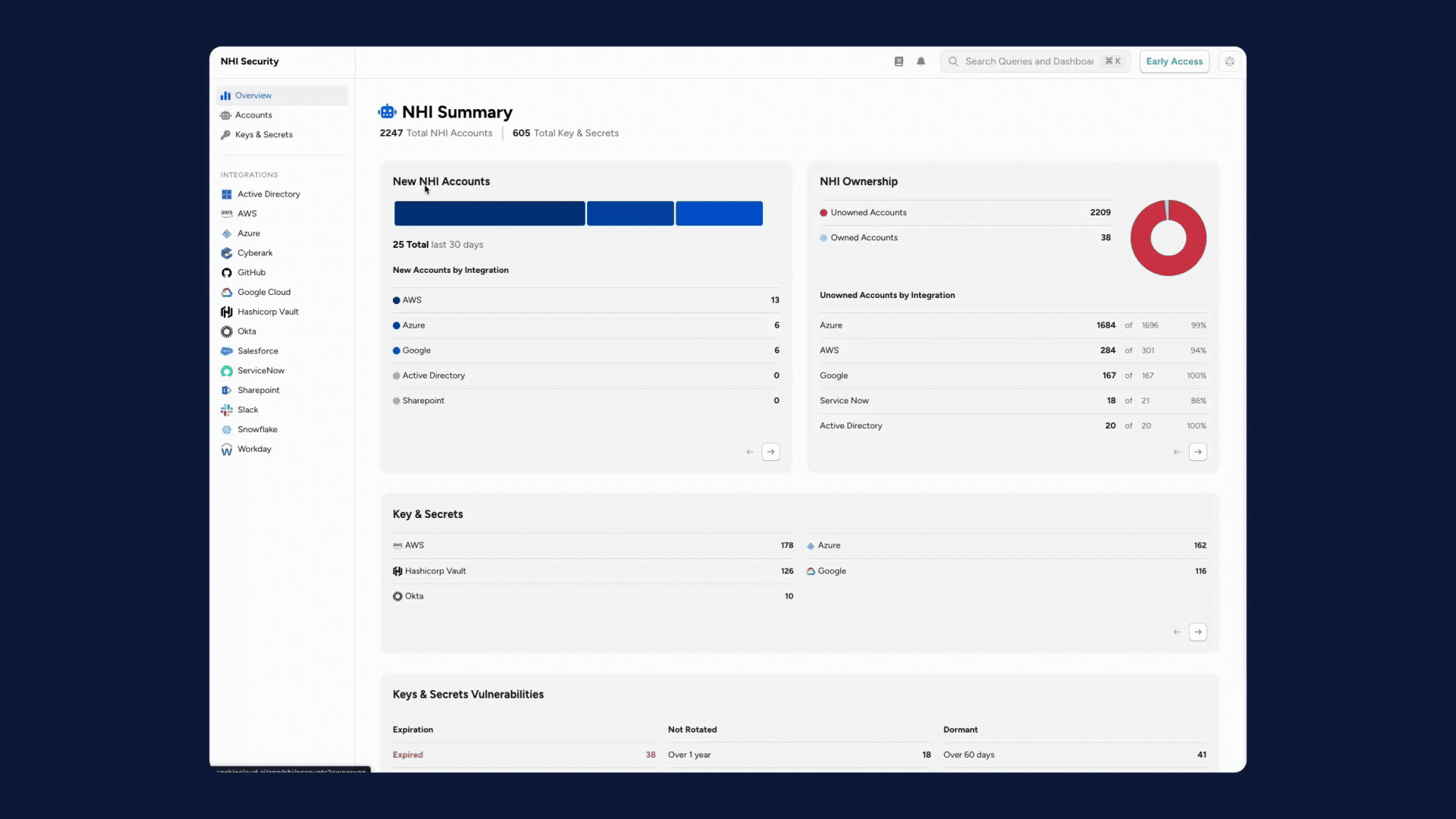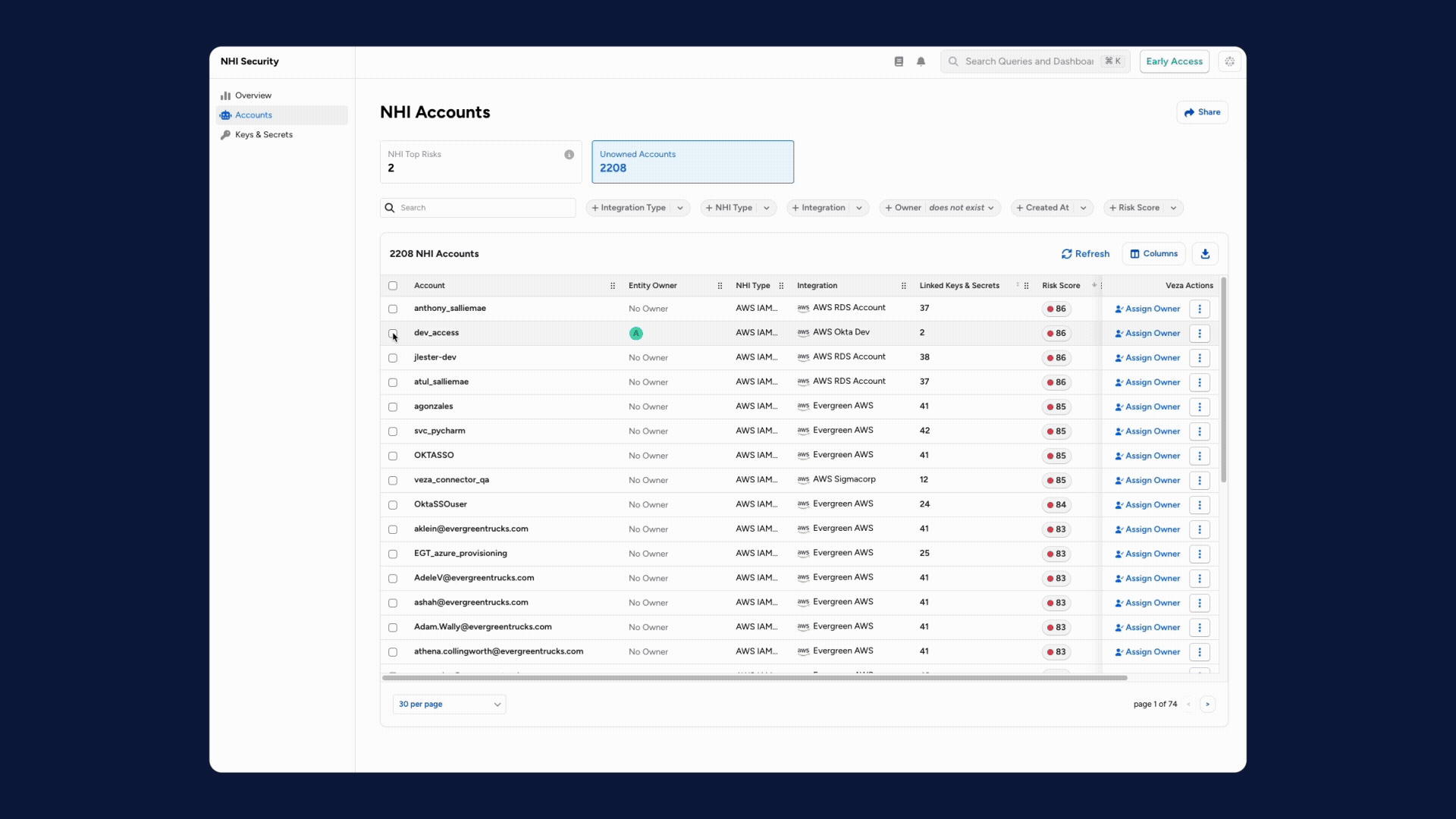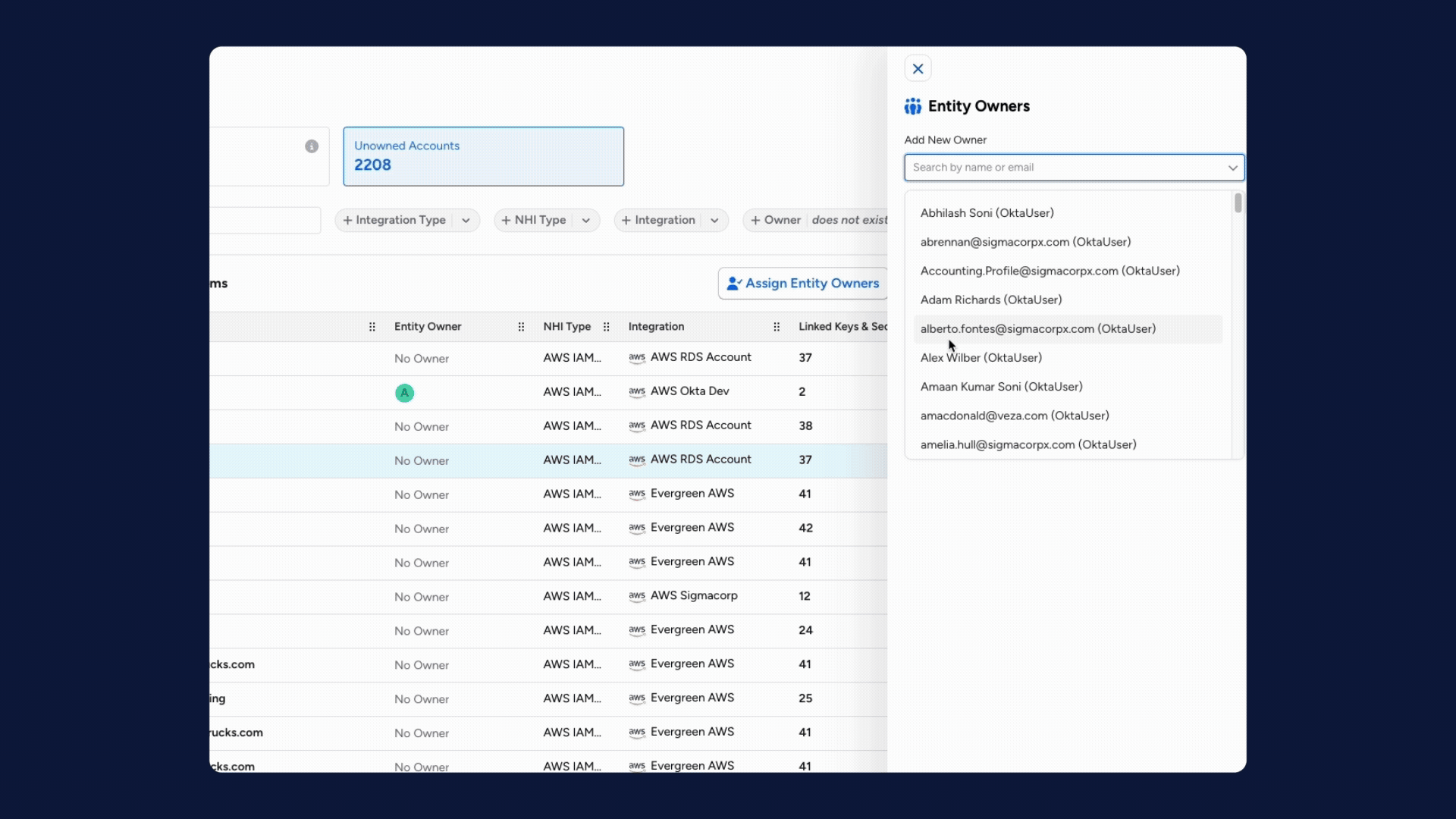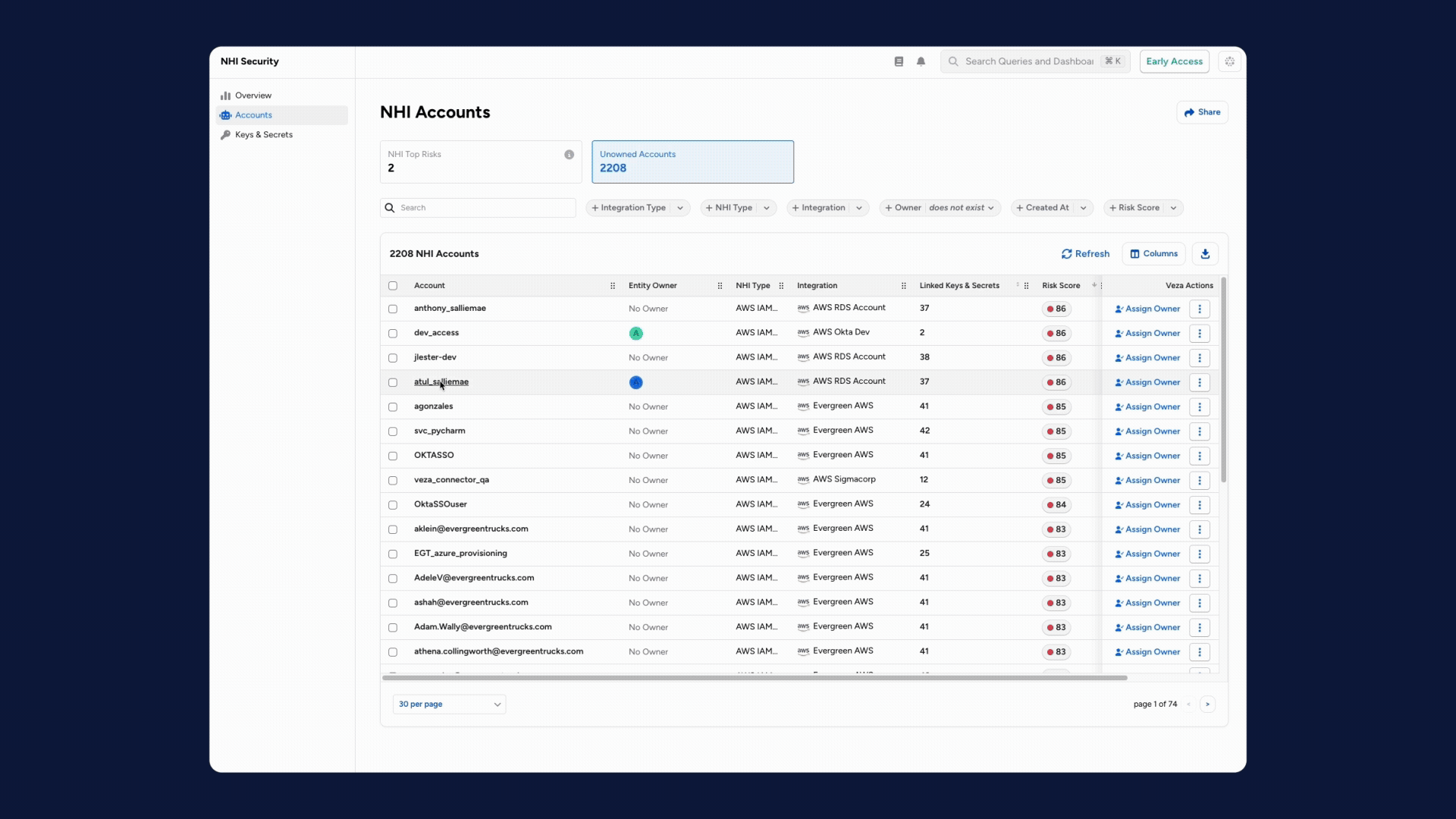
1. Agent-to-Human Ownership Mapping: Established a critical governance layer that links every autonomous agent and NHI to a responsible human owner.
2. Enforcing Least Privilege for NHIs: Integrated NHI and AI agent capabilities into Access Reviews, enabling owners to systematically surface and revoke excessive permissions to enforce the Principle of Least Privilege (PoLP).
3. Orphaned Identity Alerts: Introduced real-time alerts for machine identities that lose their assigned human owner, triggering automated reassignment to prevent unmanaged “orphaned” access.