Access Monitoring
Veza monitors activity by identities and roles on key resources to identify over-privileged permissions, right-size roles, and trim unneeded access and entitlements to sensitive resources.
How Blackstone uses Activity Monitoring to manage risk
“When you combine access with Access Monitoring you start to get into the question of whether an employee really needs the access they were given…Even if they’re entitled to that access, having the ability to see that they’re not using it enables us to make better decisions about the risks associated with keeping that access“
Adam Fletcher | Chief Security Officer
Why use Veza
Key Benefits
Track Activity to achieve Least Privilege: Know what resources users have actually accessed rather than just what they are entitled to access.
Identify Over-Permissioned Access Risks: Identify and focus on managing your most overprivileged users, roles, and resources.
Remove Unused Access: Identify and remove unnecessary or dormant access to resources.
Mitigate Permission Risk: Right-size permissions for users.
Save Cloud Costs: Remove access to resources which are never used.
Respond Rapidly: Speed up post-incident forensics by identifying what resources an attacker actually accessed.
Key Features
Monitor Activity: Collect and process audit logs data from Snowflake, AWS, Azure, and other services.
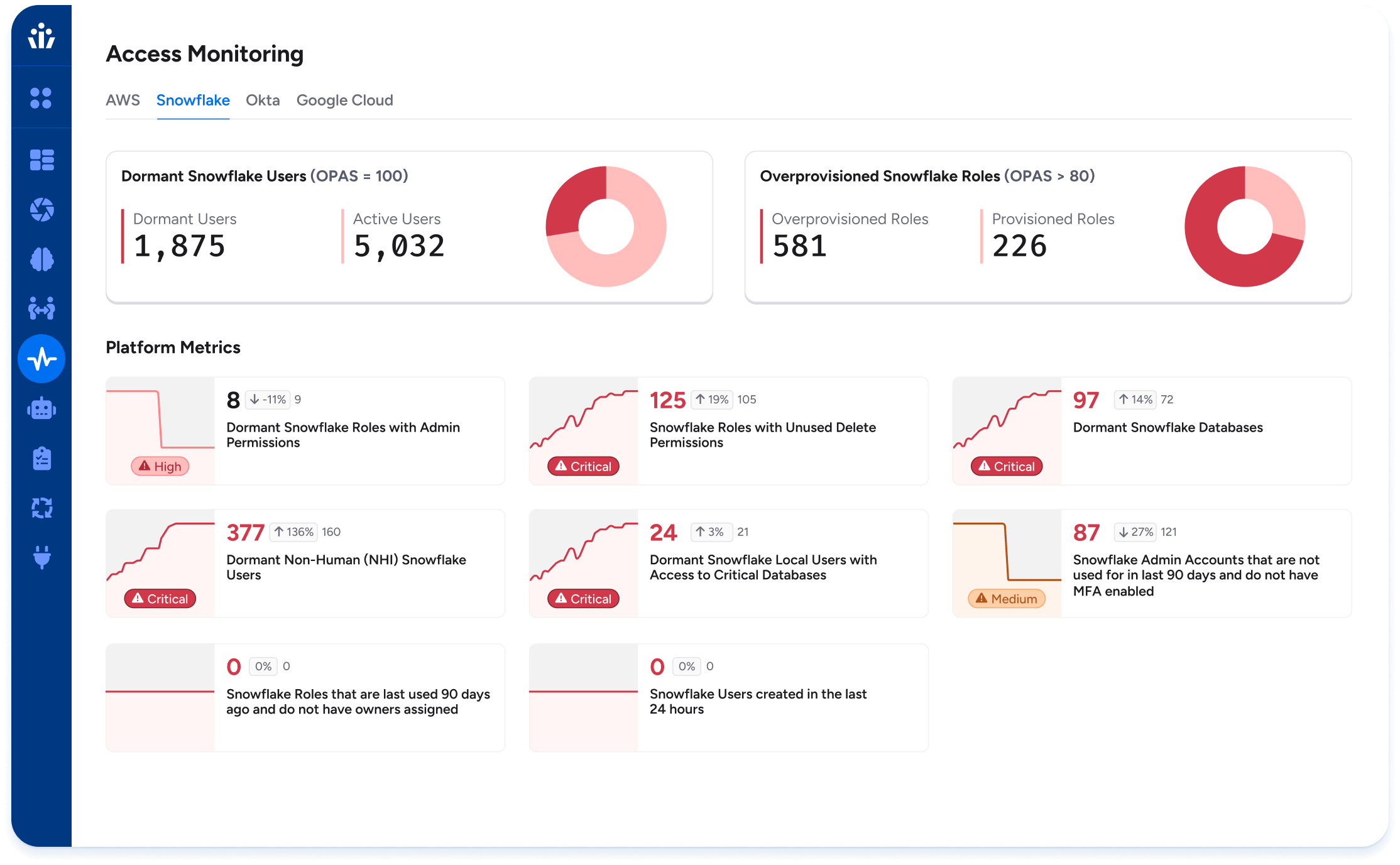
Over-Provisioned Access Score (OPAS): Synthesize different access operations (e.g. read, delete, update) across any set of resources into a single numeric activity score to help you compare levels of activity for roles and users.
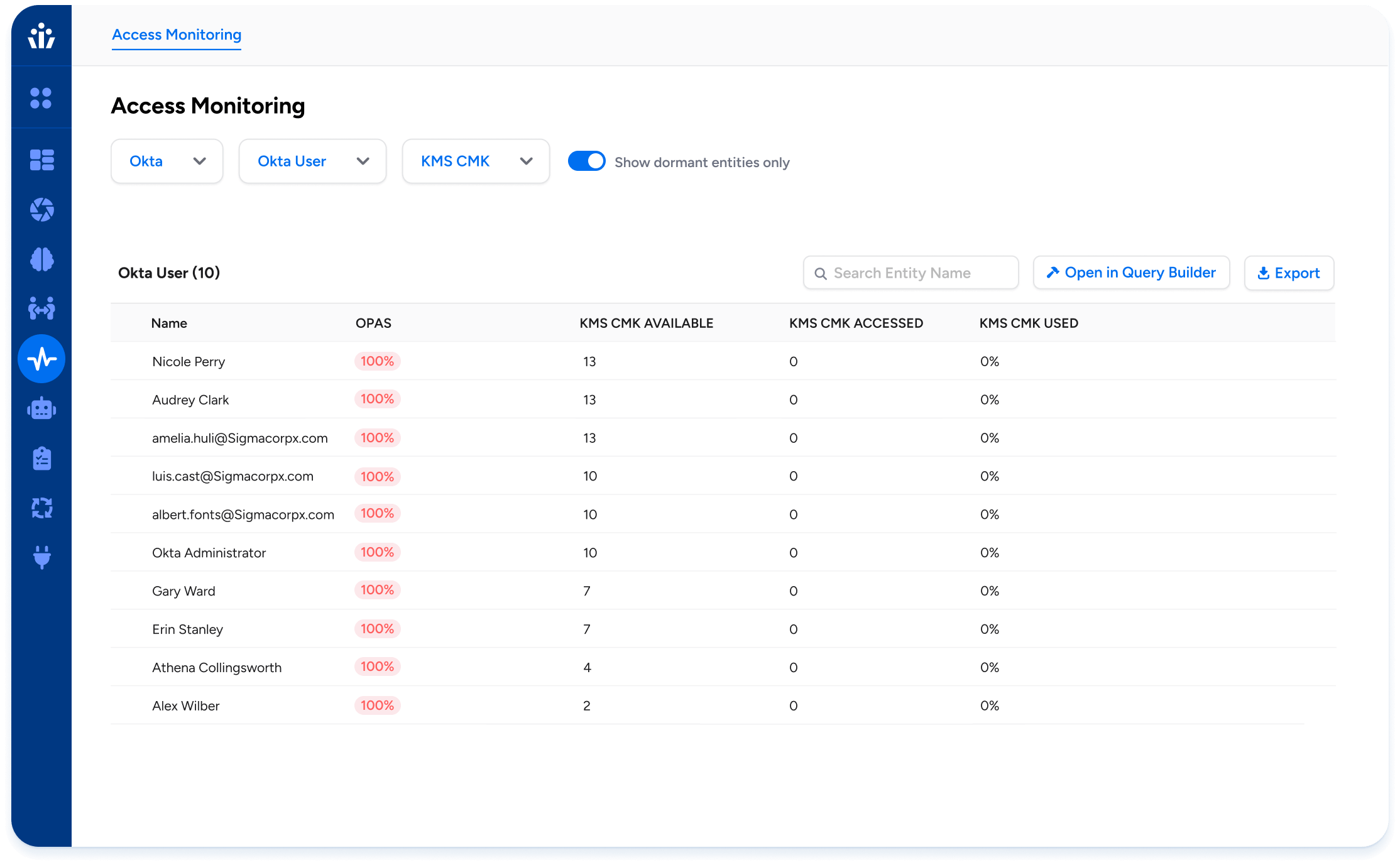
Access Stats: Show if, and exactly how many times, an identity has accessed a resource, and the exact time of the most recent access.
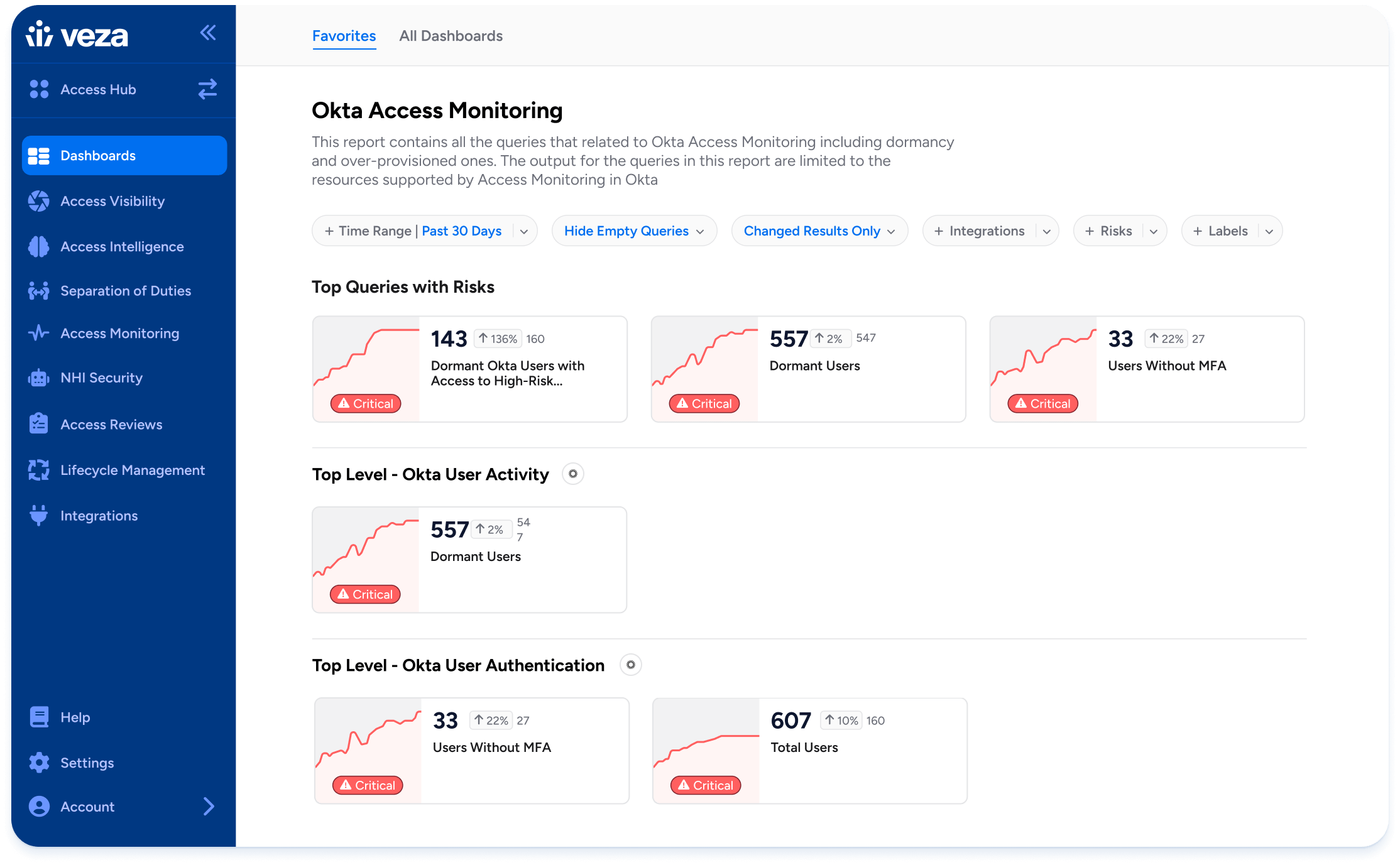
Access Intelligence: Power rules and alerts with activity scores. For example: automatically create a workflow whenever Veza detects a new over-privileged user.
Cloud Entitlements Dashboard: New dashboard for Security Engineering and Security Operations teams on most active users, dormant users, dormant roles, and more.
Learn more about Access Monitoring
-
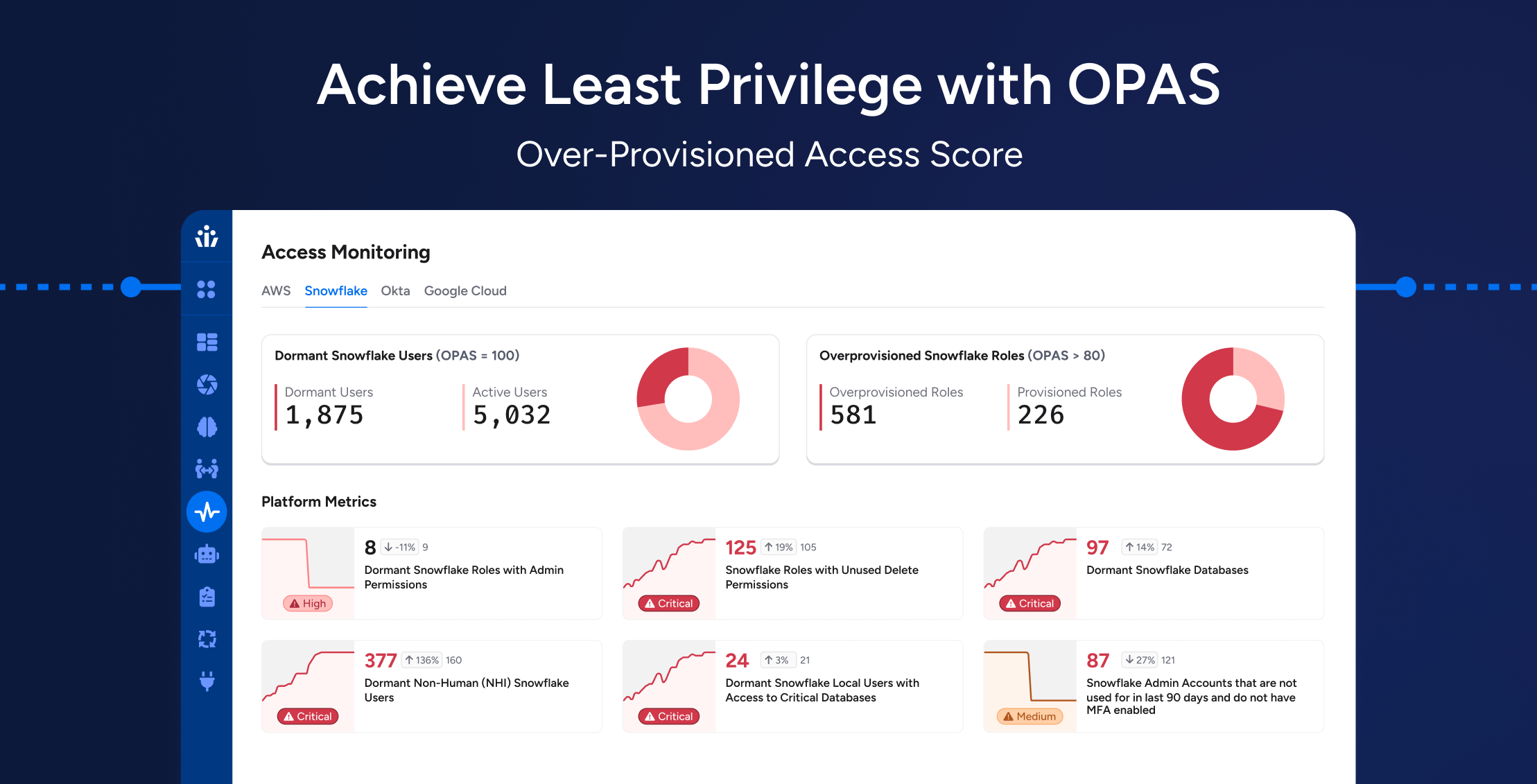
Achieving Least Privilege at Scale: How OPAS Helps Enterprises Reduce Hidden Access Risks
Learn more -
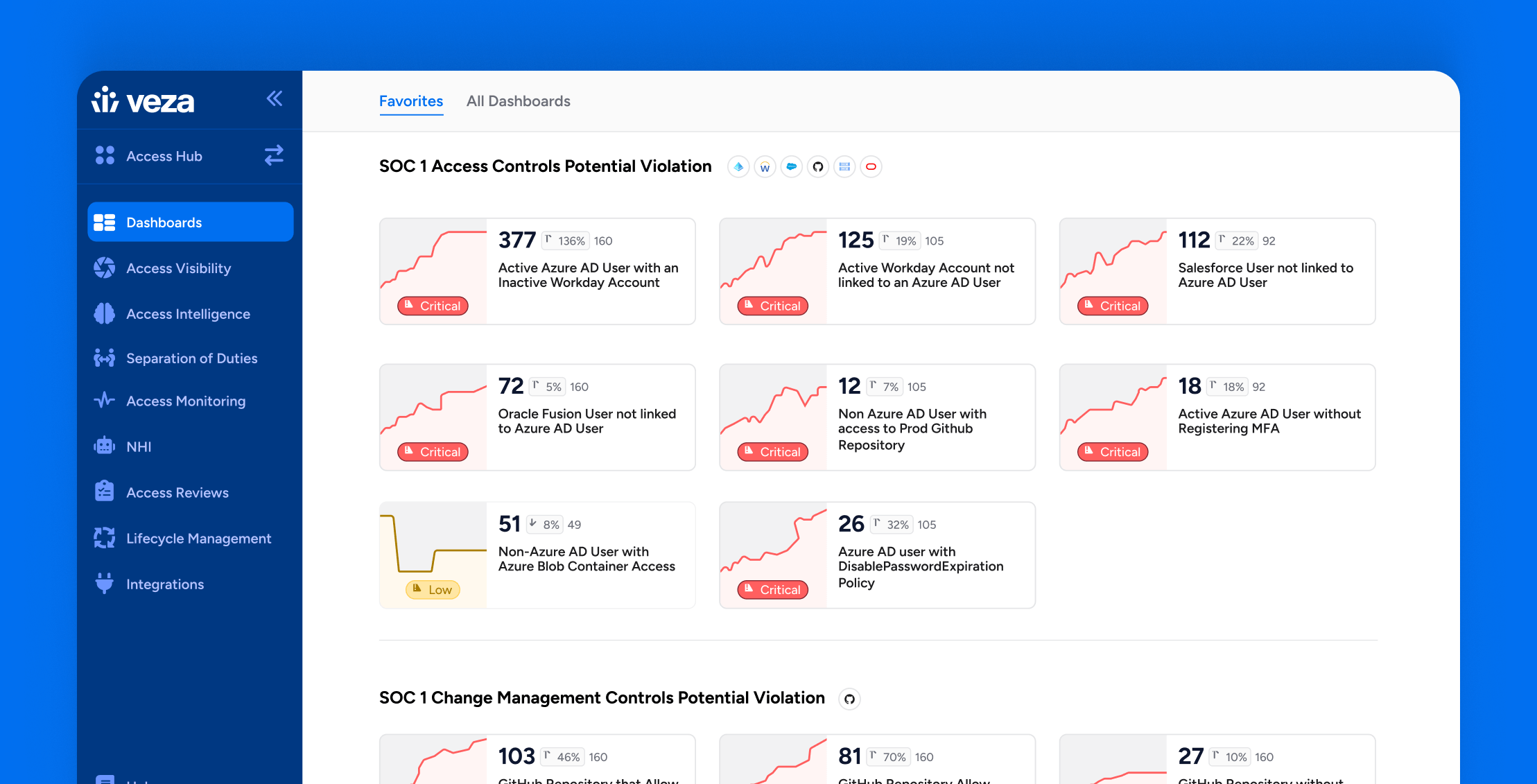
How Veza Strengthens SOC 1 Compliance: Common Control Failures & How to Fix Them
Learn more -
From Access Oversights to Audit Excellence: How Veza and Legacy IGA Secure SharePoint Environments
Learn more


