Do you really know who has privileged access?
PAM tools leave you vulnerable to data breaches and insider threats.
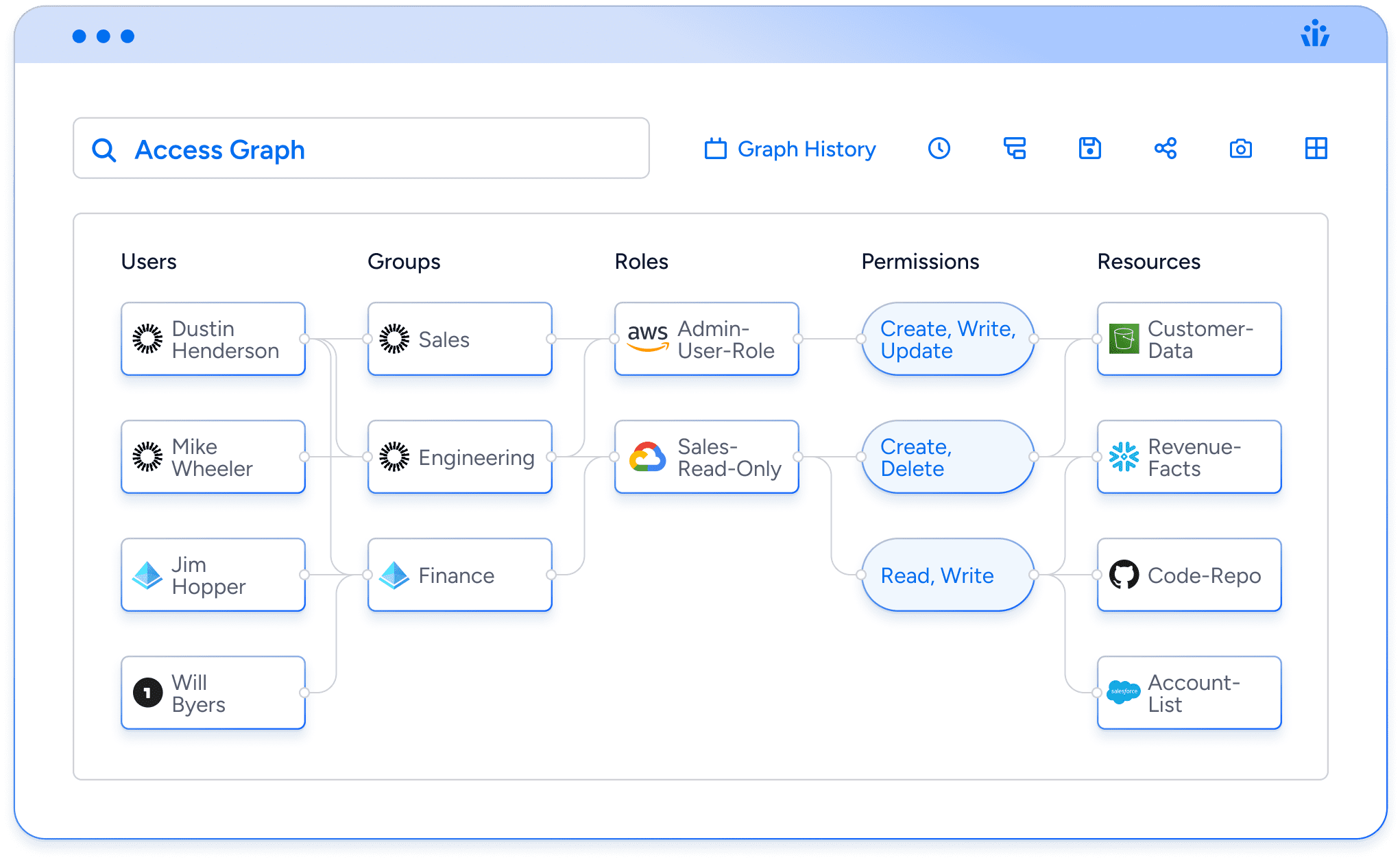
PAM tools (“privileged access management”) only manage highly privileged users and service accounts but have a blind spot when it comes to your full identity attack surface. While tools like Delinea, CyberArk, ARCON, and One Identity can monitor the accounts within their scope, they fail to catch privileged permissions across all identities. They won’t catch a role that is labeled “read-only” but for some reason allows overwriting Snowflake tables, or detect when the effective permissions for an overseas contractor inadvertently grant them access to sensitive files or PII.
Secure your data and prepare for audits with Veza
Download this whitepaper to discover how Veza automatically finds privilege violations by analyzing user permissions across all data systems, SaaS apps, and cloud services.
Pass SOX, ISO 27001, and SOC 2 audits by mapping out access permissions and enforcing data governance policies for users and service accounts across cloud, hybrid, and on-premise systems.
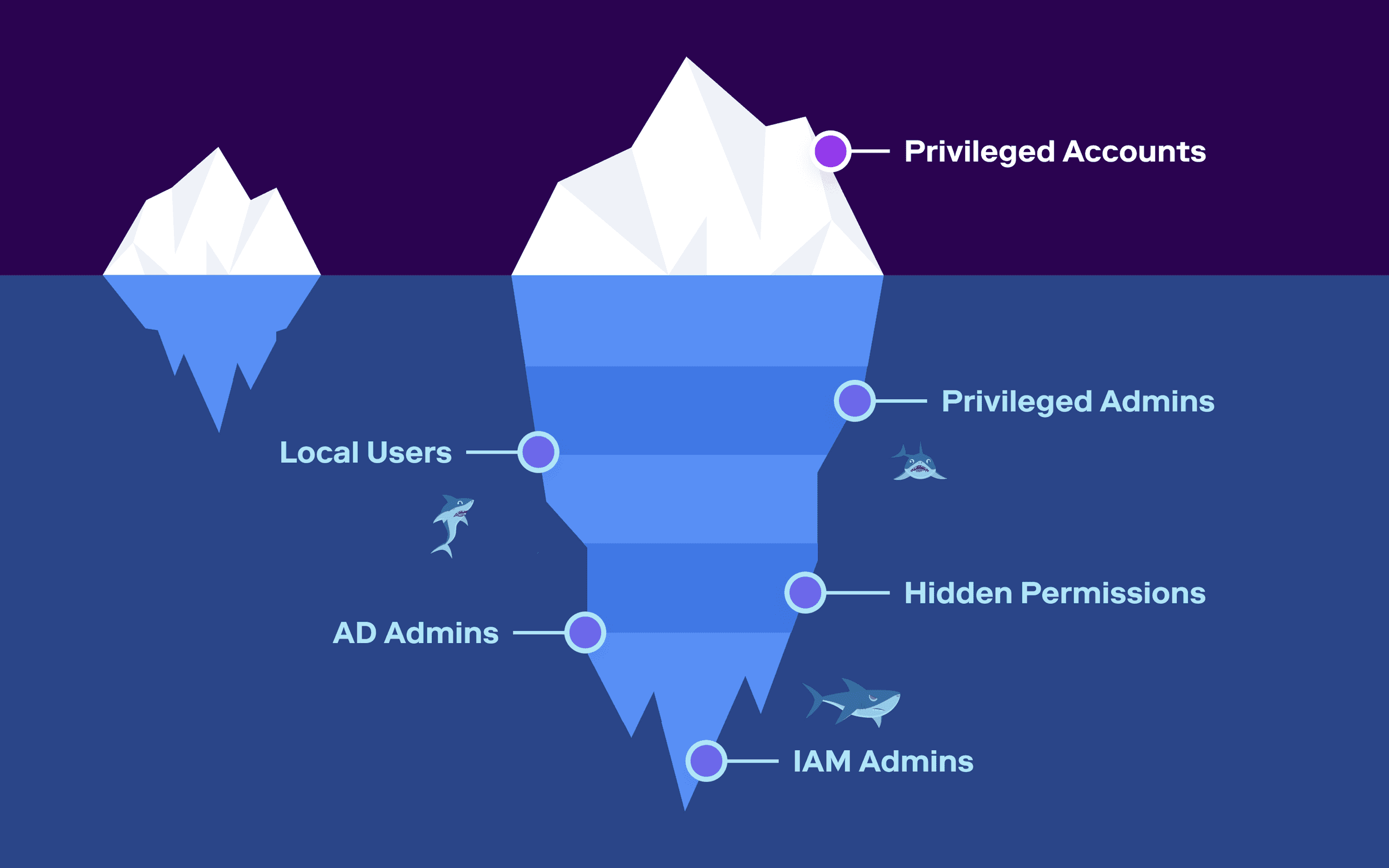
PAM tools fail to see:
- Users in non-admin roles who have admin-type privileges
- Local users or admins who aren’t managed by security tools like SSO and IGA
- Guest users who haven’t been properly restricted in their access.
- Business users who have inappropriate and unnecessary permissions to read, modify, or delete data.
- Privileged users who have inadequate authentication security (e.g. an account with read/write access to critical data but without multi-factor authentication turned on)
- Dormant accounts and inactive 3rd-party integrations that create opportunities for threat actors.